Axon 2023.01 Release Notes
Welcome to the January 2023 release of LogRhythm Axon. There are many updates in this version that we hope you'll like. Brief explanations of the updates are grouped into the following sections:
- Security Analytics and Detections
- Analyst and Administrator Experience
- Data Collection
- Platform Improvements
Key highlights include:
- Security Analytics Rule Authoring - Create custom analytics rules
- Common Event Assignment - Plain English description of log data
Security Analytics and Detections
Security Analytics Rule Management
Administrators now have enhanced controls for managing analytics rules.
- Enable or disable analytics rules authored by LogRhythm. By default, all out-of-the-box rules are disabled.
- Import or export custom analytics rules. Exported rules can be moved to other Axon deployments or shared with the LogRhythm Axon community.
- Edit existing analytics rules.
Controls on each rule also allow Administrators to show output, which executes a search that returns occurrences of the rule firing. For more information, see Rules.
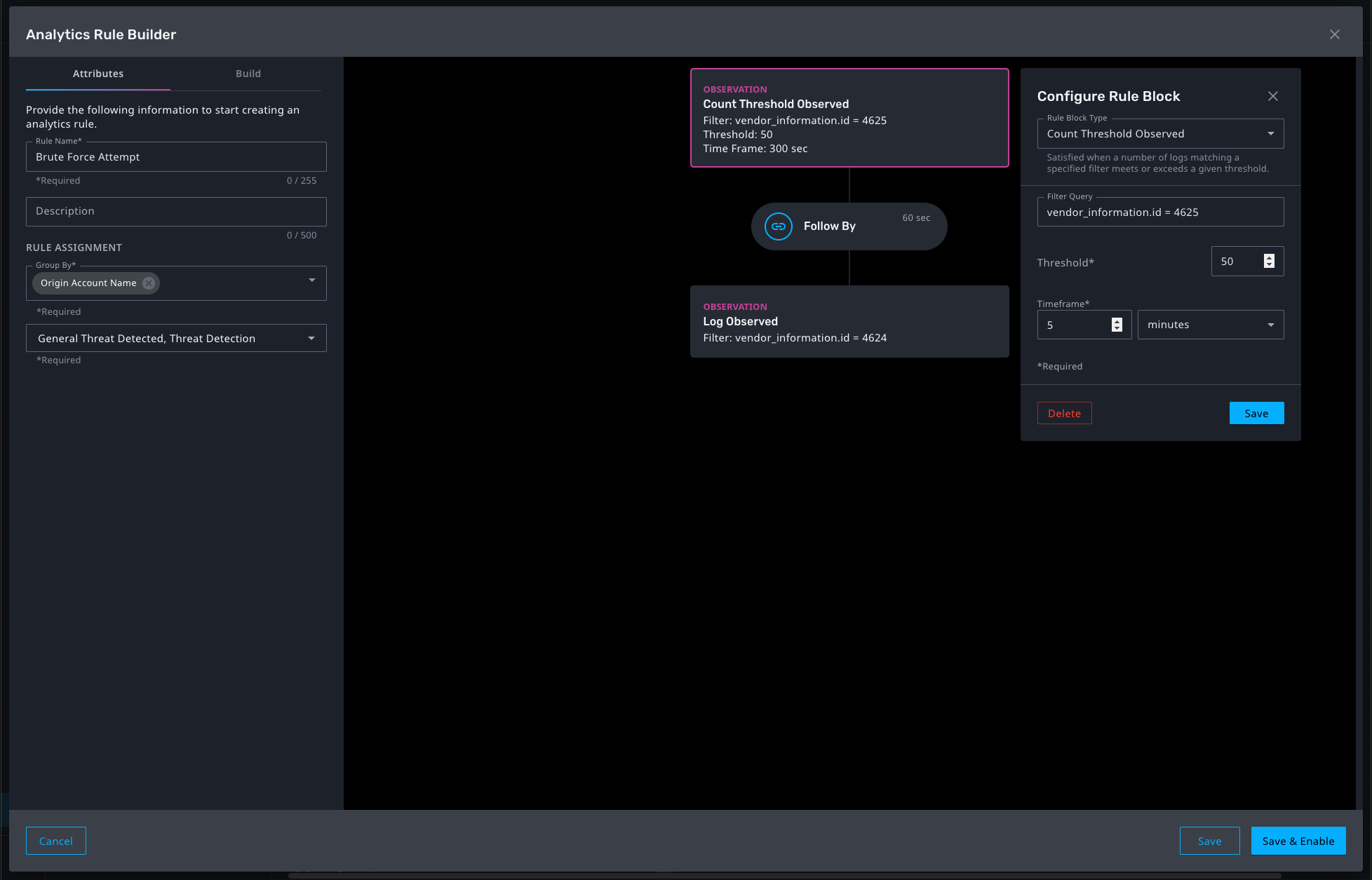
Security Analytics Rule Builder
Administrators can now author security analytics rules to support custom detection use cases. They can compose the following types of filter blocks:
- Log Observed
- Count Threshold Observed
Blocks contain a filter using the same filter language as the search workflow. Multiple blocks can be chained with customizable linking criteria. For more information, see Rule Builder.
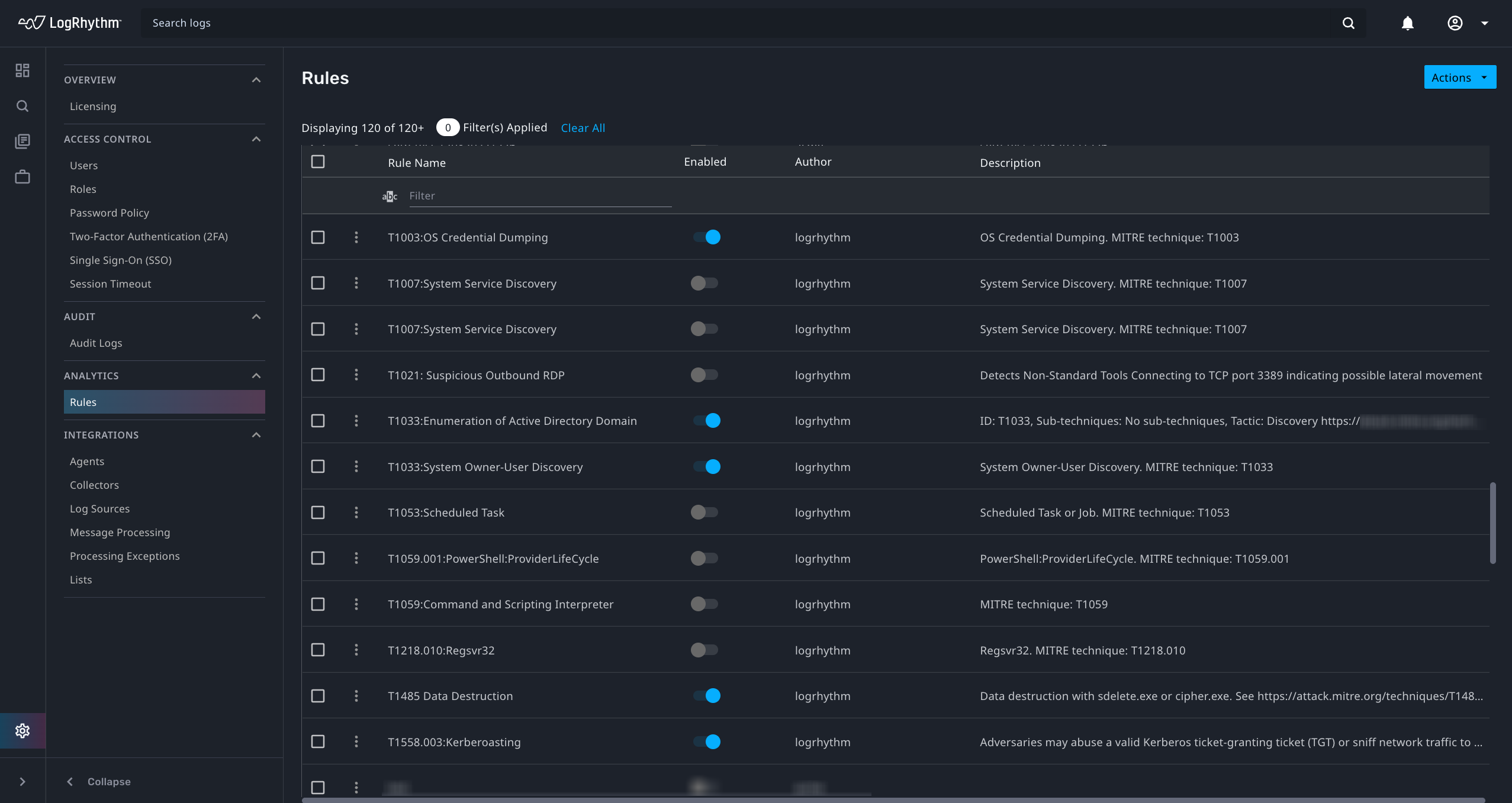
MITRE ATT&CK Content
Threat detection rules provide your team with an additional resource for threat research and dashboard configuration. The preconfigured rules deliver out-of-the-box content aligned to MITRE ATT&CK for rapid time-to-value. For more information, see Threat Detection Rules.
Rule Name | MITRE ATT&CK URL |
|---|---|
| T1003: OS Credential Dumping | https://attack.mitre.org/techniques/T1003/ |
| T1007: System Service Discovery | https://attack.mitre.org/techniques/T1007/ |
| T1012:Query Registry | https://attack.mitre.org/techniques/T1012/ |
| T1016: System Network Configuration Discovery | https://attack.mitre.org/techniques/T1016/ |
| T1018: Remote System Discovery | https://attack.mitre.org/techniques/T1018/ |
| T1033: System Owner/User Discovery | https://attack.mitre.org/techniques/T1033/ |
| T1053: Scheduled Task | https://attack.mitre.org/techniques/T1053/ |
T1059: Command and Scripting Interpreter | https://attack.mitre.org/techniques/T1059/ |
| T1543.003: Windows Service | https://attack.mitre.org/techniques/T1543/003/ |
| T1550.002: Pass the Hash | https://attack.mitre.org/techniques/T1550/002/ |
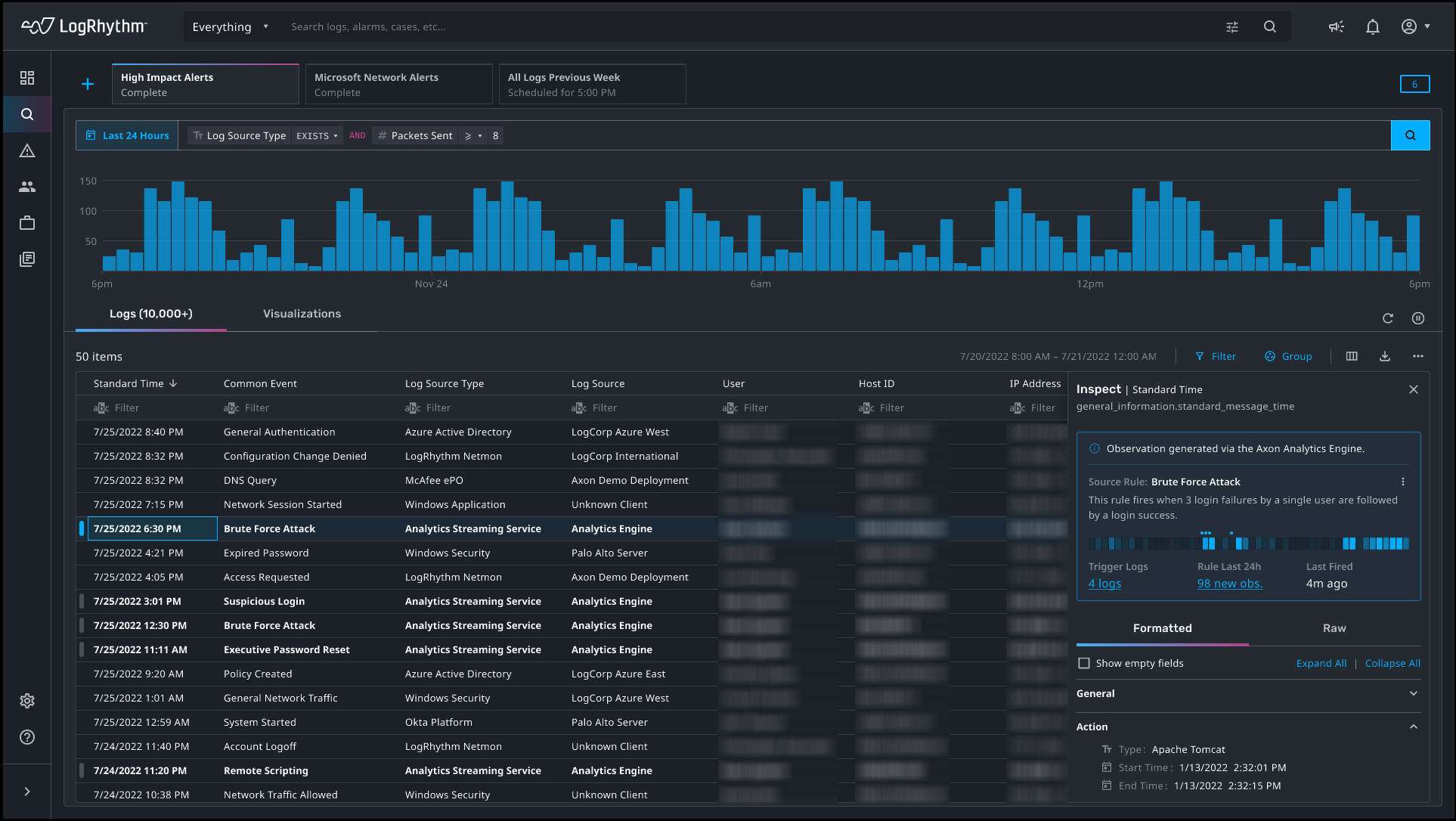
Analytic Observations Workflow
The Observations enhancement helps users quickly understand and investigate activity that triggered analytics rules. When an analytics rule is triggered, Axon creates an observation and attaches additional data to logs in table views and search results. Records containing observations are easily identifiable through bold text and a marker on the left side of the table. For more information, see Observations.
Analyst and Administrator Experience
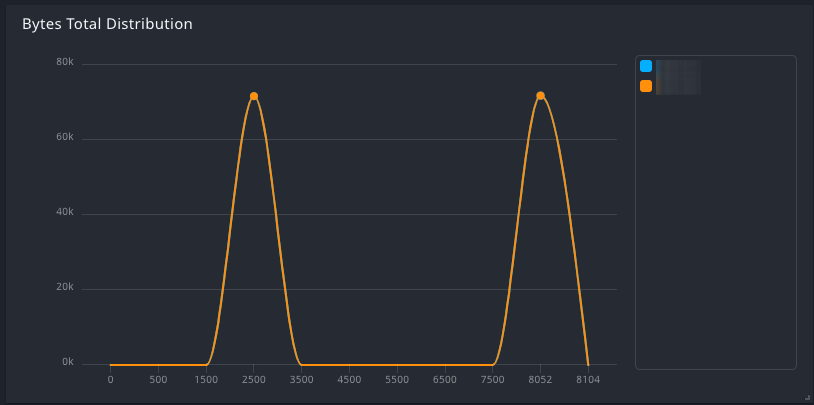
Histogram Widget
Histogram widgets can be used to display a distribution of customized numerical data directly on the dashboard or as a visualization in search results. An analyst might use the histogram widget to view the distribution of:
- Log message size by log source type
- Traffic by user or host
- Network activity by port number
For more information, see Histogram Widget.
Notes Widget
Notes widgets can be used to add contextual information to a page. This dashboard and report widget can display user-configured text and images. An analyst might use the notes widget to explain:
- What the user should look for in a graph
- The significance of certain search results
- What data is found in a subsequent chart on a report
For more information, see Notes Widget.
Data Collection
New Log Source Types
This release introduces support for the following log source types:
- Amazon AppFlow
- Amazon OpenSearch Service
- AWS Cloud Map
- AWS DataSync
- AWS IAM Identity Center
- AWS Lambda
- AWS License Manager
- AWS MongoDB
- AWS Relational Database Service
- AWS Simple Email Service
- AWS Storage Gateway
- AWS Transit Gateway
- AWS Web Application Firewall
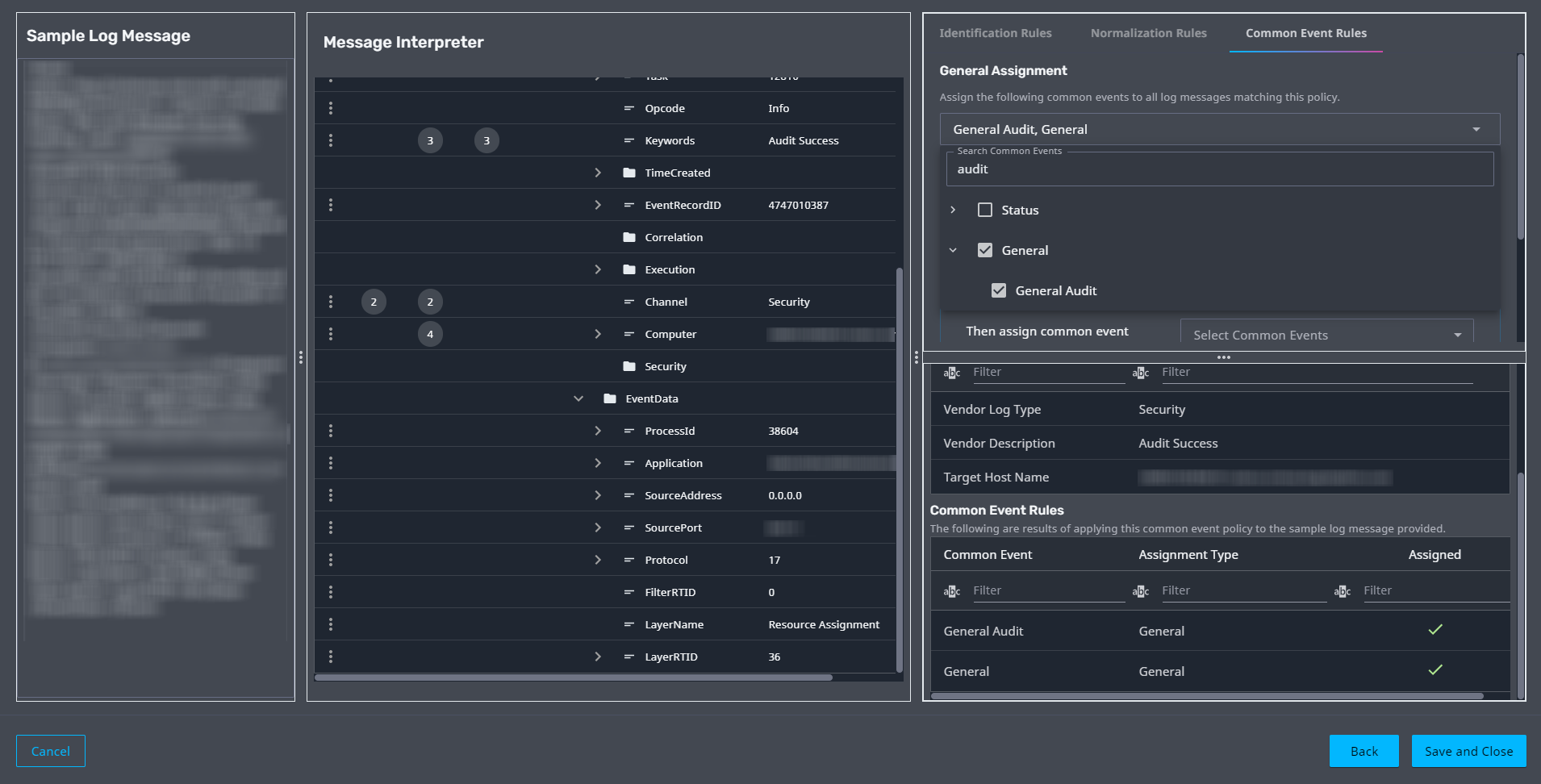
Common Events
Administrators can now assign Common Events Rules to their policies in the Policy Builder workflow. Common events allow you to:
- Quickly understand the meaning of a log message without requiring any special knowledge
- Build content that maps to a common taxonomy so that new data automatically works in existing rules, dashboards, and searches
For more information, see Message Interpreter.
Platform Improvements
Scalability and Stability
This release introduces a range of enhancements that make Axon even more stable and scalable. A more stable platform with improved performance provides an efficient and enjoyable user experience.
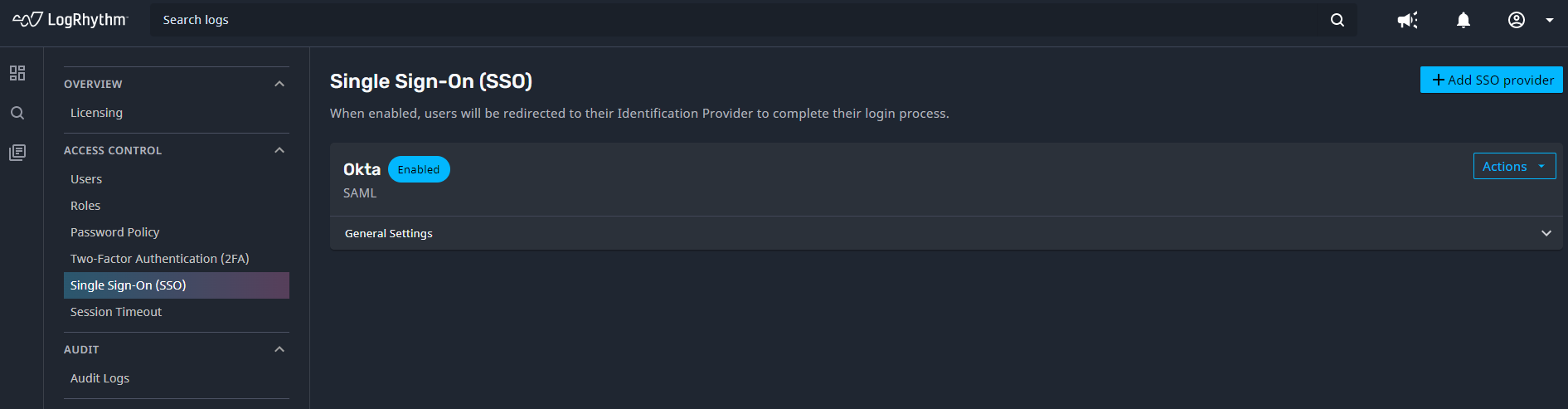
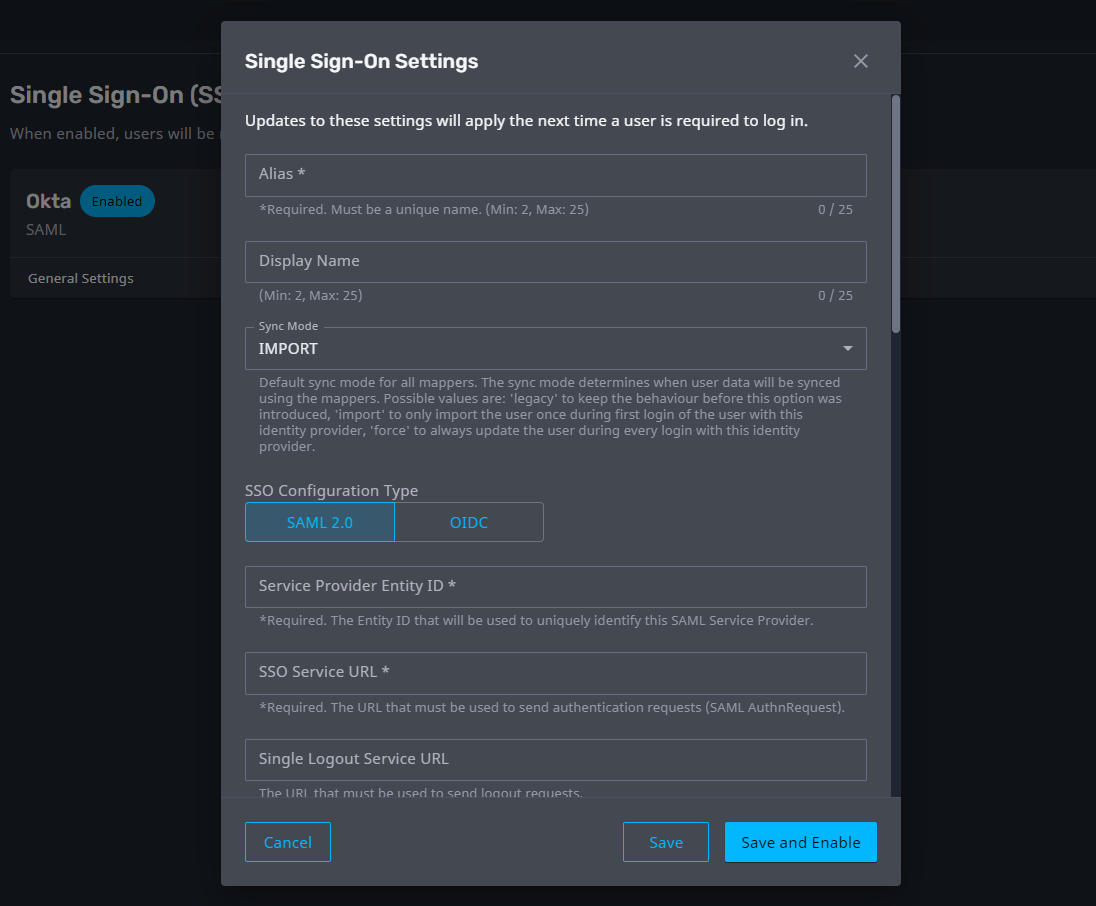
Single Sign-On
Single Sign-On (SSO) is an authentication method that allows users to securely log in to multiple independent systems using a single set of credentials. Administrators can now configure SSO for Axon via a SAML 2.0 or OIDC connection to third party IdP/IAM solutions such as Okta, Azure AD, or Sailpoint. This capability speeds up the user onboarding process by automatically granting access to a user the first time they login using SSO credentials.
Axon SSO is flexible enough to accommodate different authentication strategies. Administrators can configure connections to multiple SSO providers, and users can merge local accounts with their SSO accounts so they can access Axon using either local or SSO credentials.
For more information, see Single Sign-On (SSO).
Resolved Issues - Security
Security-related issues resolved with this release are available for customers to view on the Community.
