7.17.0 GA Release Notes - 1 July 2024
LogRhythm 7.17 introduces the Open Collection Architecture and the JSON Policy Builder, making onboarding and parsing Logstash formatted JSON logs a breeze. With these new features, security analysts can get a better view across the organization. Collecting mission critical log sources has never been easier!
What’s new in SIEM 7.17:
Maintenance
Open Collection Architecture
Ingest and customize log sources faster than ever before. With LogRhythm 7.17, we’ve made it easy to bring JSON log sources into the LogRhythm SIEM. We’ve opened the System Monitor Agent, allowing it to accept JSON logs from sources that support the Lumberjack protocol. Now administrators can configure third-party JSON agents to supplement LogRhythm’s vast library of supported log sources.
And whether you need to tailor custom or out-of-the-box normalization rules, the Open Collection Architecture lets you edit, apply, and manage rules like a pro. The new custom policy folder on the System Monitor gives users a safe place to store custom or modified normalization rules without the risk of being overwritten or impacted during upgrades.
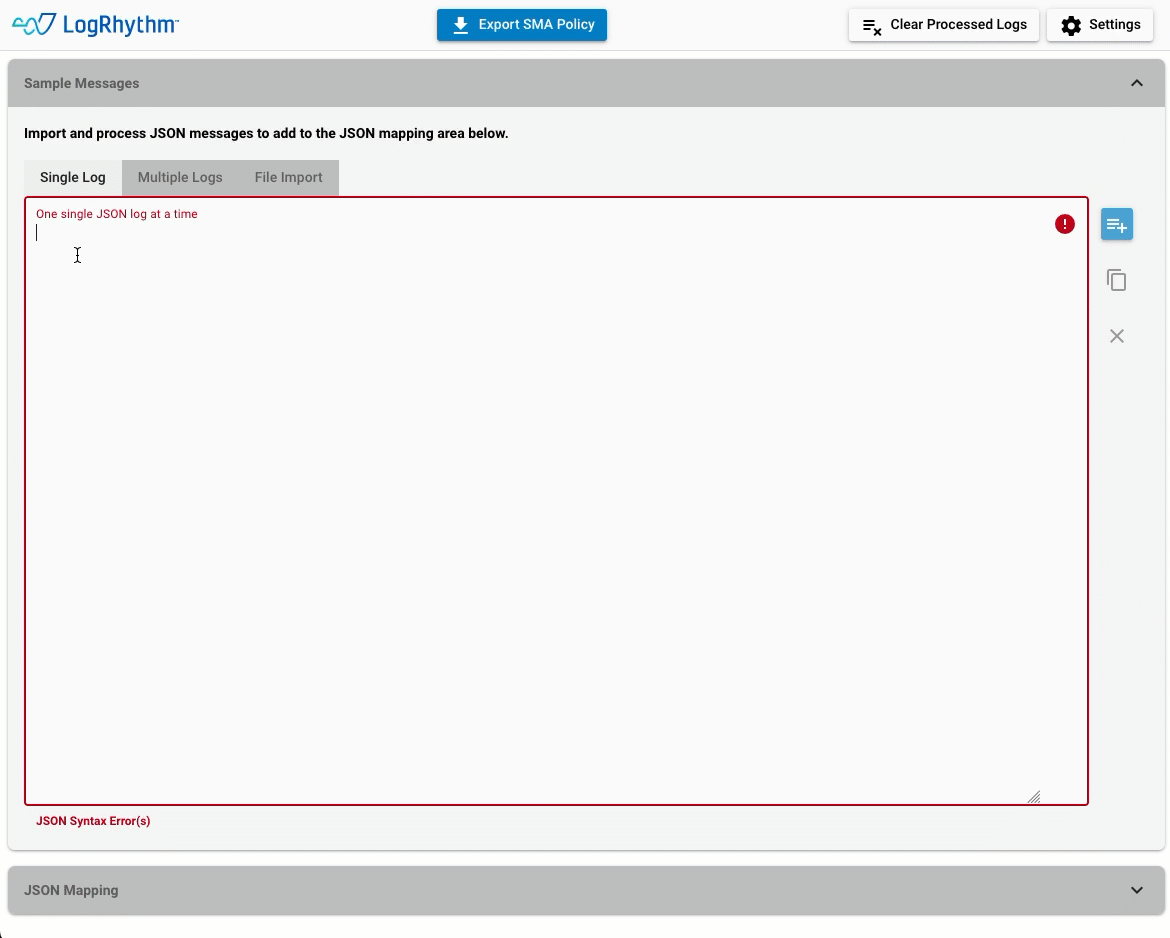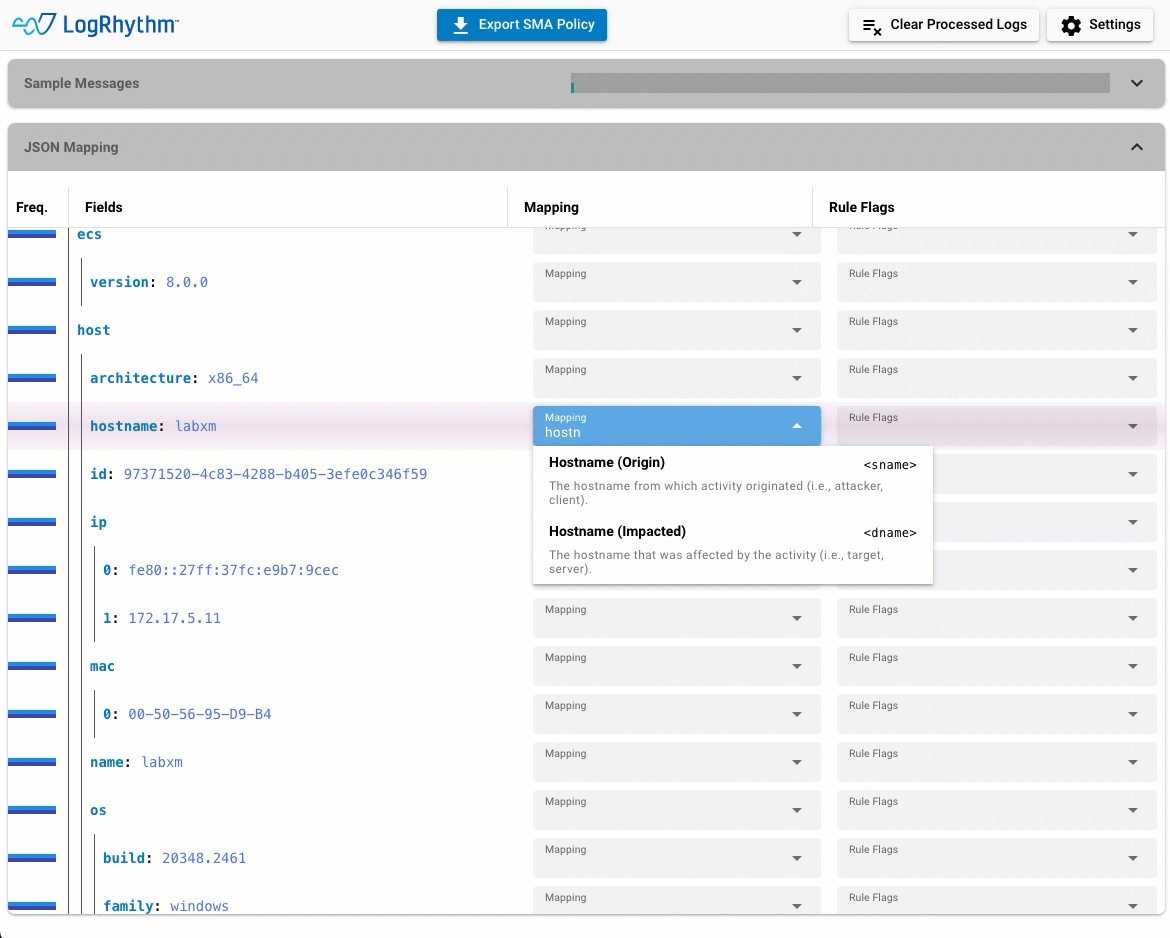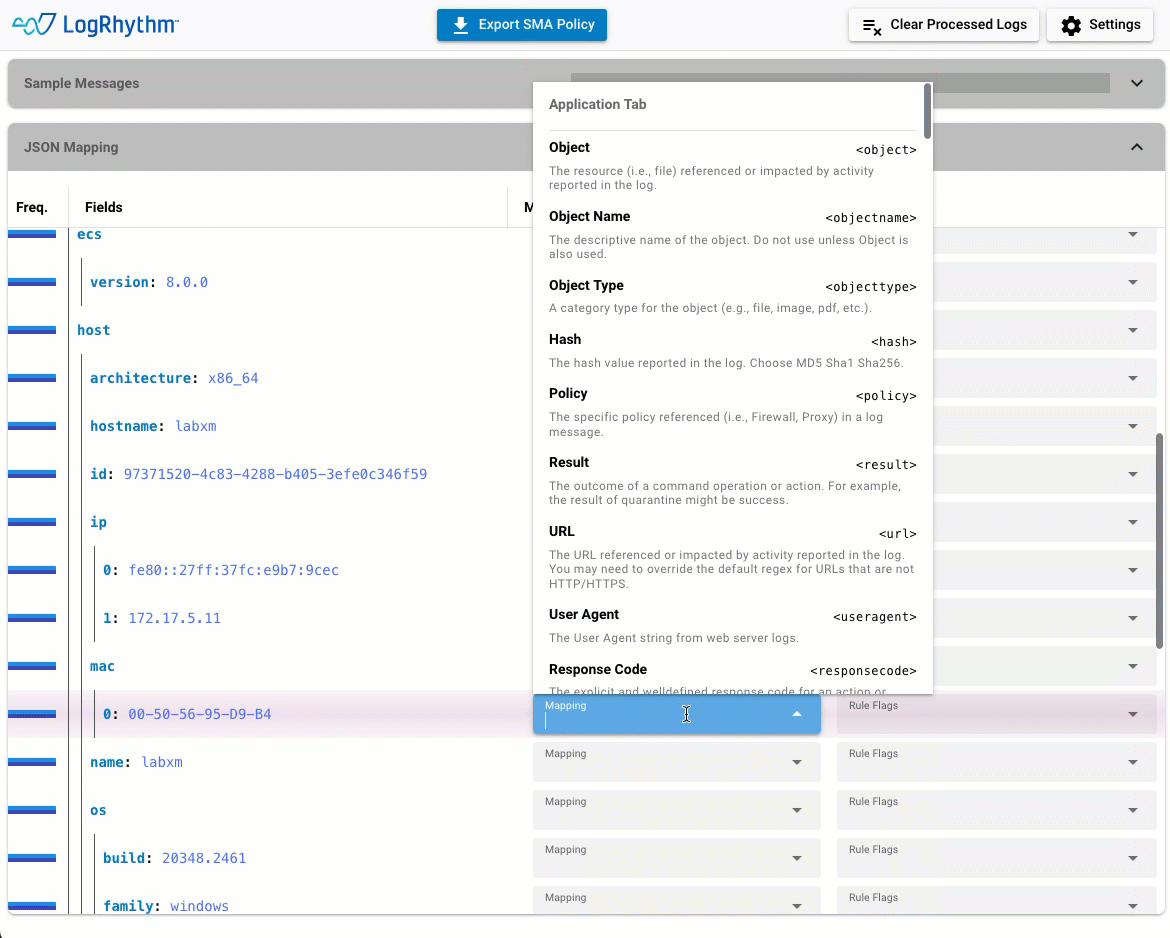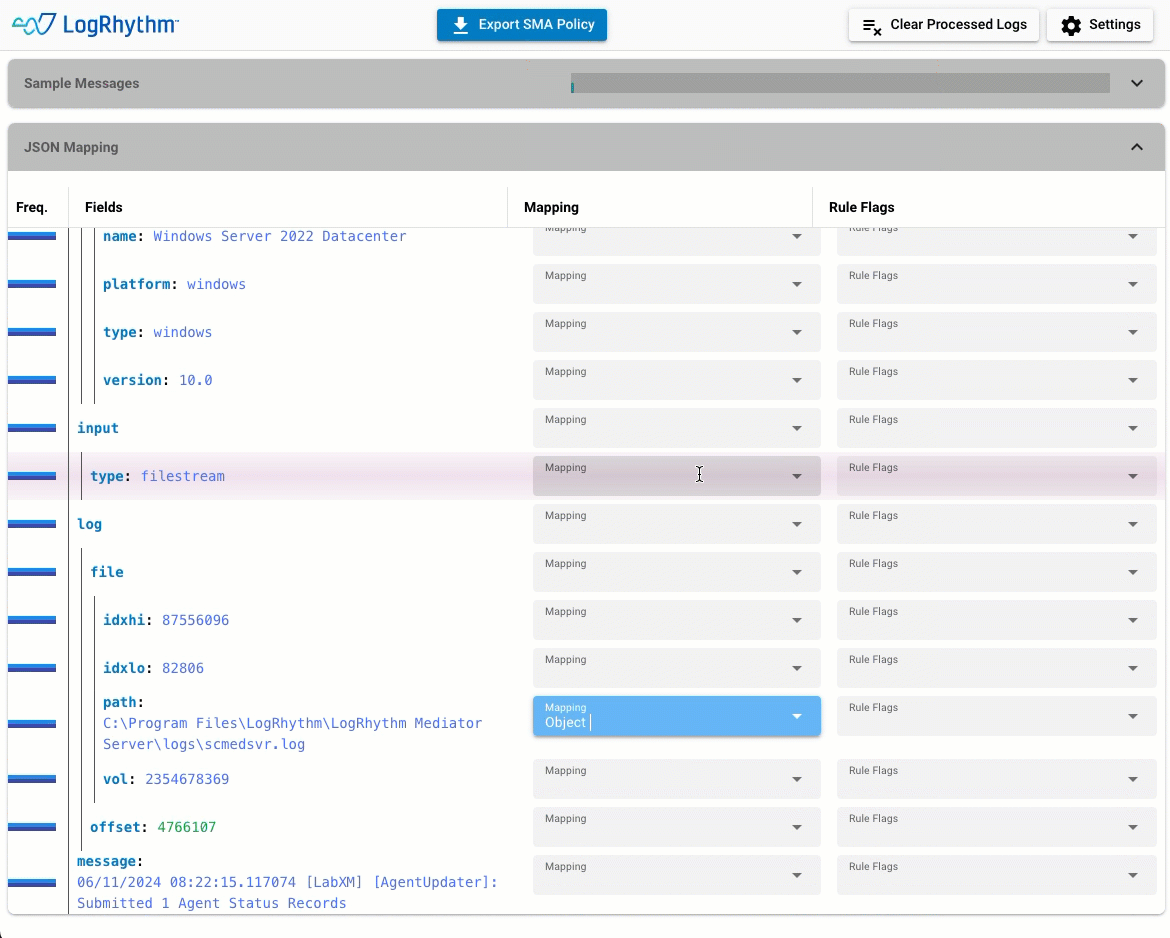
JSON Policy Builder
Map, export, apply. With the JSON Policy Builder, it’s that easy. The GUI-based wizard allows administrators to build policies and extract data from JSON log sources in minutes. No coding and no special training means that anyone can do it.
Data extracted from sample log messages is automatically extract by the wizard. Drop-down menus make it simple to map JSON values to the LogRhythm schema before exporting the policy file to the System Monitor Agent.
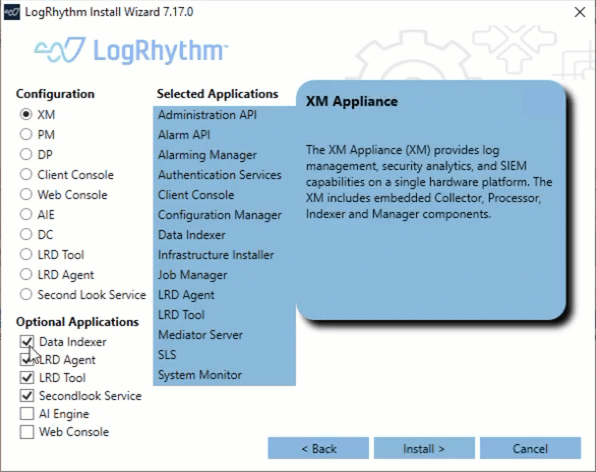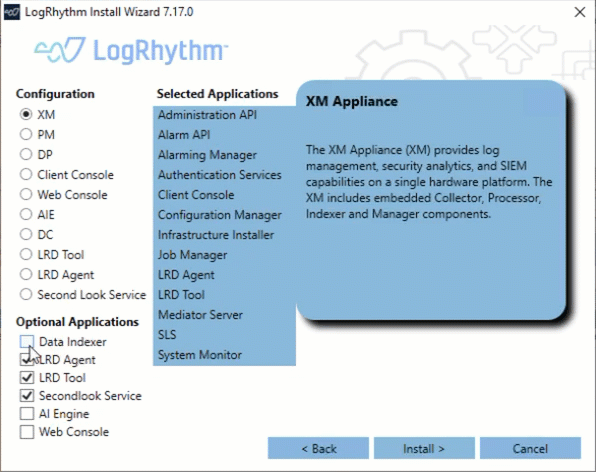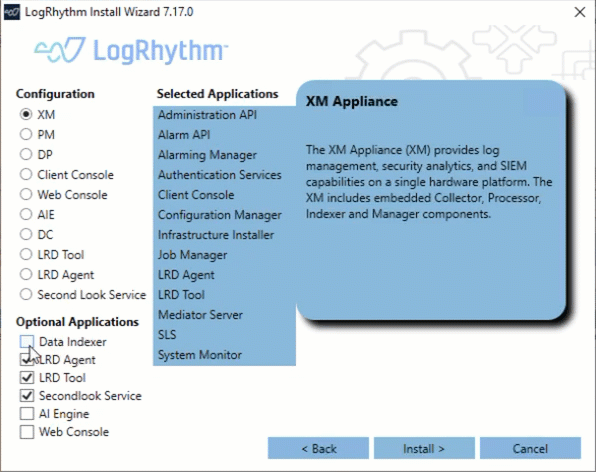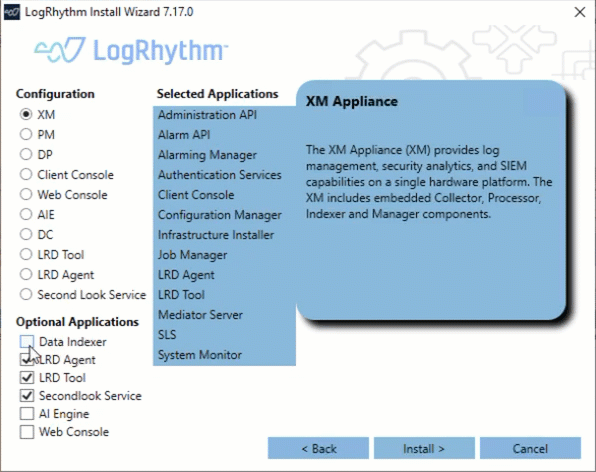
Install & Upgrade Improvements
LogRhythm’s flexible architecture makes it easy to expand and scale, and now the LogRhythm Install Wizard is just as flexible. The streamlined installer gives you greater control over which components are installed on a single box. Administrators can now opt out of installing the Data Indexer on the same hardware as the rest of the LogRhythm components. This streamlines your process, making your upgrade faster by removing the need to run the LogRhythm Install Wizard multiple times.
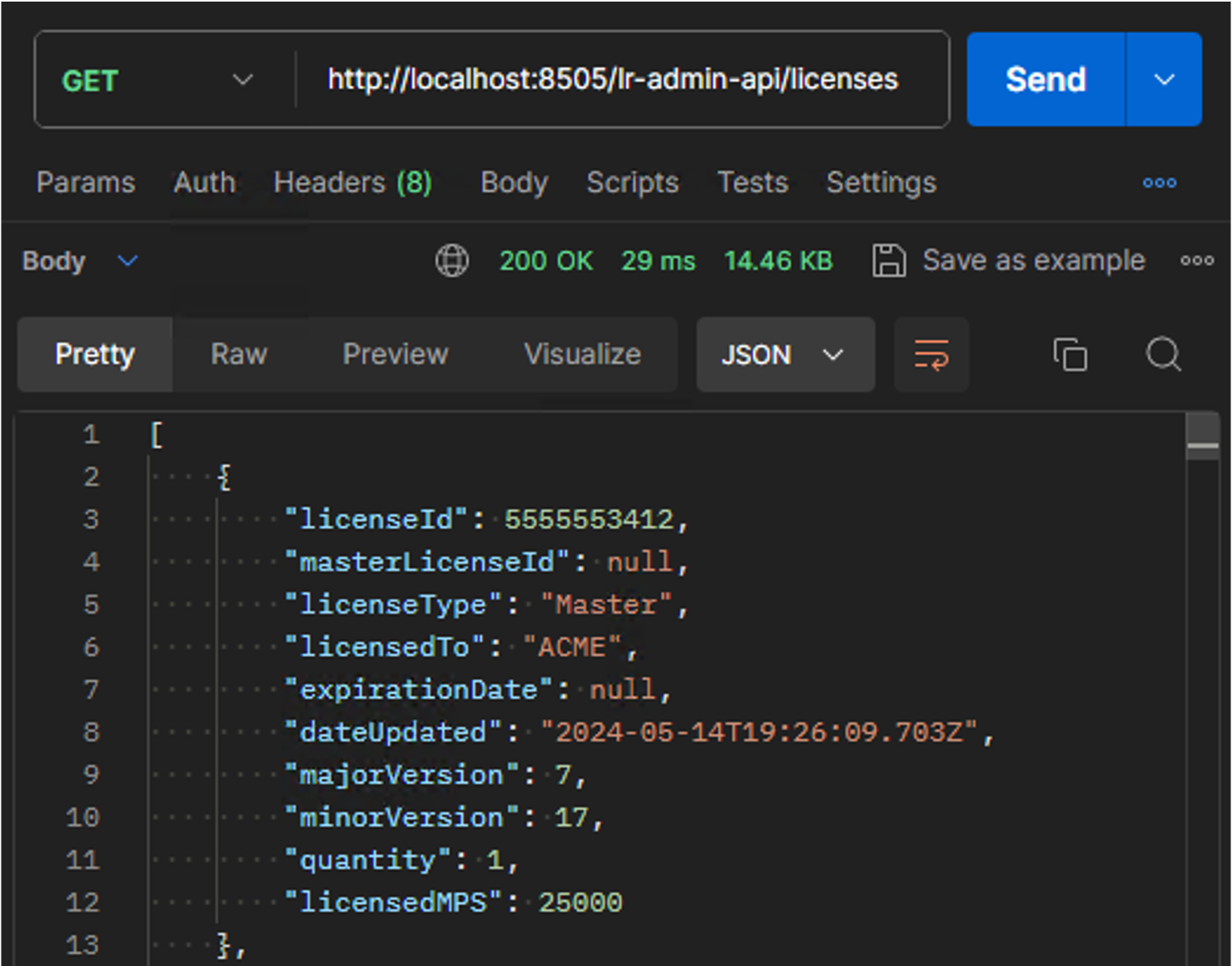
Licensing Details in the Admin API
Administrators can now programmatically obtain critical licensing information through the REST API. Manually logging into environments and the Client Console is no longer needed. Retrieve and monitor LogRhythm SIEM licensing and version details using the new licensing details endpoint in the Admin API. Combine with other LR API endpoints like the Metrics API to quickly compare and monitor licensed MPS vs current volume statistics. Reduce overhead and automate data retrieval across multiple environments.
Updated Log Sources
As part of LogRhythm 7.17, we are proud of our many updated log sources. This quarter we focused on improving what we already have. We carefully reviewed and refined over 70 log sources to improve the experience for LogRhythm Analysts. We believe this will deliver great value in terms of more reliable and stable log parsing rules which ensures that visualizations, reports and detection rules leverage accurate and improved data.
To support our ongoing commitment to you, we continually update and improve Message Processor Engine (MPE) rules. As such, a crucial step in maintaining a healthy security posture is to normalize log messages. This helps ensure that you get more value out of the log data LogRhythm ingests and the security insight power of LogRhythm’s Machine Data Intelligence (MDI) Fabric.
A few of the highlights released over the last three months include:
Firewall security – The insight provided from firewalls is critical for protecting organizations. This quarter, LogRhythm released improvements for firewalls such as: Palo Alto Networks, Fortinet FortiGate, Sophos XG and Cisco Firepower and Meraki. With these improvements, LogRhythm customers will find greater value in the log enrichment and can better defend against threats.
Applications – Key business applications have been updated this quarter: Oracle and Microsoft SQL have been updated for Databases, Apache access logs for web servers, Trend Micro Email Security and FortiMail for email solutions. These are just some of the business applications improved to give you more reliable insight.
Operation Systems – Many MPE rules improvements centered on Operations Systems, especially Windows Event logs. For non-Windows users, several Unix flavors have been updated also: AIX, HP-UX, IRIX, Solaris and Linux. Providing quality MPE rules for all of these Operations System log sources ensures security analysts have a clear and cohesive view of all the servers in an organization.
And these are just the highlights! LogRhythm updated more than 70 log sources over the last quarter, and we will continue to update more as part of our commitment to our customers’ successful security practices. For all of the release notes and changes review the Knowledge Base Release Notes on the Community.
Improved Log Sources:
API – Office 365 Management Activity | Syslog – Citrix NetScaler | Syslog – Linux Host |
|---|
Enhancements & Resolved Issues
Mediator Update to .NET 8 Framework
The Data Processor service (Mediator) has been migrated from .NET 4.7 to the .NET 8 framework. The .NET 8 code base has been optimized for modern operating systems and offers improvements in performance, compatibility and features. The .NET 8 Mediator offers a number of performance improvements:
Better service memory management under duress leading to increased stability
Lower overall CPU resource consumption under identical load profiles
Higher peak and sustained load handling on identical systems
Greatest benefits on newer Windows Operating Systems (Server 2022)
This change introduces the installation of .NET 8 as part of the Installation Wizard along with new Environment Variables used for runtime configuration of .NET 8. These variables should not be modified except under the direction of support or engineering.
Resolved Issues
Bug # | Component | Description |
|---|---|---|
ENG-11134 | Web Console: Services | The Web Console services now automatically restart or recheck the EMDB IP in the service registry if they cannot connect to the SQL server, ensuring continuous operation without manual intervention. |
ENG-11168 | Job Manager | The Job Manager now excludes disabled users from Scheduled Report Jobs, logs when no recipients are available, and displays recipient names in a new column in the Scheduled Report Job grid. |
ENG-11178 | Admin API | The Admin API now supports network transfers between entities with clear documentation. |
ENG-11187 | Client Console | The Case Details Report now successfully pulls data for the selected date range. |
ENG-24727 | Client Console Search | When searching Host records, the results now accurately omit Host Entities that no longer contain the search criteria in their properties. |
ENG-26079 | Reports | When running reports for the same time frame, Log Volume by Log Source Type and Log Volume by Log Source now show the same log count. |
ENG-26682 | System Monitory Package Manager | The System Monitor version number is no longer truncated in the System Monitor Package Manager. |
ENG-32013 | Client Console: User Profile Manager | Changing a User Profile without updating the password no longer causes login issues for that user account. |
ENG-33357 | Documentation | Documentation for Add Network Records from File now includes clarification regarding special characters and quotes in string fields. |
ENG-38594 | Smart Response Plugin | Custom modifications made to Smart Response plugin scripts are now retained indefinitely. |
ENG-40223 | Alarm API | The Alarm API now uses the following format for date time fields: yyyy-MM-ddTHH:mm:ss.fff |
ENG-51371 | Web Console | When entering the Trigger Time in the Web Console Alarms grid view, pressing the backspace key now deletes only one character at a time in decimal numbers. |
ENG-52230 | Admin API | After upgrading and accepting a System Monitor Agent via the Admin API, the Deployment Manager now functions normally upon relaunch, with all IPs verified as valid and the NetMon tab building successfully. |
ENG-52775 | Message Processing | The relay regex now parses raw syslog log messages as expected. |
ENG-54023 | Admin API | The Admin API now accepts Linux System Monitor Agents without generating GUID validation errors. |
ENG-54204 | Log Sources | Log Message Processing Settings are no longer greyed out for custom log sources. |
ENG-54769 | Alarming and Reporting Manager (ARM) | Suppression settings configured in AIE rules and Alarm rules now work as expected. |
ENG-55596 | Web Console | The CSV export now includes all selected logs, regardless of applied filters, allowing users to export the entire set of selected logs, not just the filtered view. |
ENG-55821 | AI Engine: MPE Rules | The system no longer triggers alarms for MPE Null Log Sources. The new patch ensures proper log message handling, preventing the recurrence of the issue. |
ENG-55877 | Smart Response Plugin | Updated Smart Response scripts now include valid, non-expired certificates. This ensures proper execution in secured environments without errors. |
ENG-56056 | Web Console: SSO | Selecting “Continue with SSO” in the Web Console redirects to the SSO page for authentication, regardless of pre-filled username and password values. This ensures proper SSO authentication flow and security compliance. |
ENG-56298 | Error Messages | The SCMPE log now shows the raw log message in the regex rule matching time-out warning messages to aid in timeout troubleshooting. |
ENG-56487 | Agents | System now accepts pending System Monitor Agents with -1 set for the IP address. |
ENG-56799 | Web Console | The Drilldown on a Widget with a specific time range opens the Analyze Page displaying only the events within the Widget's time range settings. The Analyze Page shows the exact number of events matching those in the Widget's drilled-down data. |
ENG-57349 | Web Console | After upgrading to version 7.15, the contextualize panel auto-populates user account info in the contextualize field upon clicking the username in the Top User widget. |
ENG-57545 | Job Manager: Reports | Scheduled reports via Job Manager now correctly display the local time the report was run, matching the time set in the schedule. |
ENG-57598 | Agents: Gsuite Log Collection | The System Monitor JSON parser now accurately extracts and displays email addresses from LICENSES_SETTINGS type Gsuite logs. |
ENG-57599 | Agents: Gsuite Log Collection | This update adds group name parsing functionality for Gsuite logs in the Open Collector JSON parsing engine for System Monitor. |
ENG-57601 | Reports | Case management reports exported as CSVs maintain correct field alignment without shifting or inserting JSON fields incorrectly into columns. |
ENG-57808 ENG-58005 | System Monitor: AIX | The AIX System Monitor Agent build and package now allow successful installation of the 7.16 System Monitor Agent on AIX 7.2. |
ENG-57867 | Alarm API | In HA and DR environments, Alarm API calls are correctly routed without returning a 500 internal server error. |
ENG-57894 | Agents | Accepted System Monitor Agents no longer appear in the Pending Agents list. |
ENG-57961 | AIE Cache Drilldown API | The AIE Cache Drilldown API now functions correctly without requiring the Content-Type header, ensuring consistent behavior with other APIs. |
ENG-57994 | System Monitor | An issue with spelling errors in the System Monitor JSON parsing policy file has been resolved. |
ENG-58331 | Web Console | The Web Console display now correctly shows the entire search results bar without cutting off the bottom of the browser window. |
ENG-58639 | Agents: Azure EventHub Log Collection | Added parsing support for the riskEventTypes_v2 field for the Syslog - Open Collector - Azure Event Hub log source type. |
ENG-59026 | Agents: Cisco AMP Log Collection | Additional parsing rules are now added for Cisco AMP logs in the Open Collector JSON parsing engine for System Monitor. |
Resolved Issues - Security
Security-related issues resolved with this release are available for customers to view in the Community.
Known Issues
The following issues have each been found and reported by multiple users.
Bug # | Found In Version | Components | Description | Notes |
|---|---|---|---|---|
ENG-41651 | 7.12 7.13 | Web Console | After upgrading to 7.12 or 7.13, the CAC authorization used to log in to the Web Console stops working. | Expected Results: The CAC authorization should work when logging in to the Web Console. Workaround: There is currently no workaround for this issue. |
