Deployment Security
This section provides information about some of the security features in LogRhythm, including passwords and password encryption, support for Public Key Infrastructure (PKI), users and security roles, and user security permissions.
Authentication and Secure Message Transport Search
All login activity and services run by any user on the Client Console are secured by OAuth2. Services include searches performed with the following:
- Tail
- Investigation
- Personal Dashboard
- TopX
- Reports (when run as Investigations)
- SecondLook
To audit secure message transport search, you can review Console.log. You can find Console.log in the following location: %APPDATA%\LogRhythm\logs.
LogRhythm Password Encryption
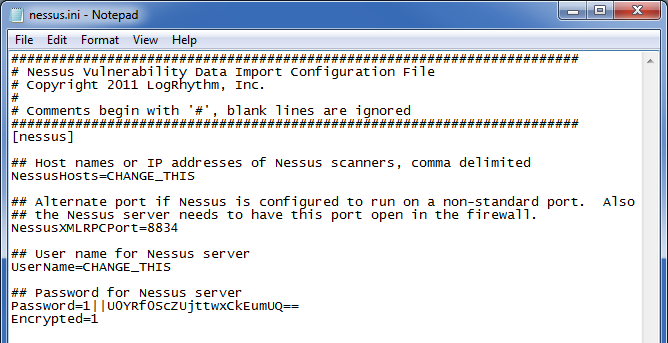
All passwords stored in configuration flat files, such as .ini files, or SQL Server database tables, such as SMTP server password in the EMDB.ARM table, are encrypted. All password entries in the Client Console are masked.
LogRhythm supports passwords up to 255 characters long for SIEM services and the Client Console.
Encryption Method:
- Generated key (64 bytes) is hashed (SHA1) into 20-byte array (256 bits)
- AES encryption: cipher mode is ECB and padding mode is PKCS7
Where passwords are stored and entered in a LogRhythm deployment:
- Configuration (.ini) files (scmedsvr, scarm, lrjobmgr, LRAIEEngine, sdee)
- Database Tables
- EMDB System Monitor
- EMDB ARM
- Client Console
- Login
- Log Exporter (SMTP)
- Automatic Log Source Configuration (SNMP Connections)
- Local Configuration Managers (LCM)
- AI Engine
- Data Processor
- Job Manager
- Platform Manager
- System Monitor Agent
The LogRhythm Encryption Utility does the following:
- Encrypts passwords and writes output to the Client Console.
- Encrypts Cisco IPS, Qualys, Nessus, NeXpose, Metasploit, Sourcefire, Retina, and eStreamer passwords used by the LogRhythm System Monitor for event and vulnerability collection. Encrypted passwords will be written to the value of the "Password=" parameter in the specified configuration (.ini) file — the configuration file must already exist.
- The lrcrypt.exe file is located in one of the following locations: C:\Program Files\LogRhythm\LogRhythm System Monitor\lrcrypt.exeC:\Program Files (x86)\LogRhythm\LogRhythm System Monitor\lrcrypt.exe
- Usage: lrcrypt [-e passwordtoencrypt] [path\inifile]
- For example, if the user runs lrcrypt -e password config\nessus.ini, the value specified by password is encrypted and written as the value for the Password parameter in the nessus.ini file.
To get encrypted values for other configuration file parameters — those other than Password — you must run lrcrypt without specifying the path to the .ini file.
For example: C:\Program Files\LogRhythm\LogRhythm System Monitor>lrcrypt -e mypassword
LogRhythm Password Encryption Utility
Encrypted password: 3||//y/XnKOyOls8HGOb6WaBw==
In this case, mark and copy the encrypted password value and manually paste it into the configuration file.
For security reasons, you should ensure that strong passwords are used and that all passwords are protected.
LogRhythm Users
A LogRhythm user is created within LogRhythm as a person record and user account. A person record doesn’t require a user account, but a user account requires a person record. A user account is also required to log in to the system. By default, a LogRhythm Administrator and LogRhythm Analyst user is created and available with a new LogRhythm Deployment. Each LogRhythm user is granted database access under a specific security role.
LogRhythm users access the LogRhythm solution via the LogRhythm Client Console by entering a user ID and password. As part of the login, all communications can be encrypted by selecting the Encrypt all communications check box from the Login window. Users can log in with a Windows Account or a specific user account. In either case, the record must exist as a person/user within the LogRhythm solution as created via the Client Console. If FIPS is enabled in the local security policy, Windows Authentication is required and therefore is the only method to log in to the Client Console.
Each LogRhythm user account must be assigned a User Profile. A User Profile is assigned one of the following Security Roles: Global Administrator, Restricted Administrator, Global Analyst, Restricted Analyst, or SOAP API Service Administrator.
The general permissions for each Security Role are described below.
Global Administrator
Full control of LogRhythm functionality
Never disable the LogRhythm Administrator role. Doing so will break your ability to perform other key functions in both the Client Console and the Web Console.
Global Analyst
- Has LogRhythm database permissions that are limited only to read-only functions (investigations, tails, alarms, and reports)
- Has no access to Deployment Manager to make configuration changes (LogRhythm enforced)
Restricted Administrator
- Has LogRhythm database permissions that permit configuration changes as well as read-only functions (investigations, tails, alarms and reports)
- Has specific permissions to view and modify host, SM Agent, and log source properties (SQL Server enforced, View). Also known as LogRhythm Discretionary Access Control. This access control is segregated by Entity.
Has limited access to Deployment Manager to make configuration changes to permitted resources (LogRhythm enforced)
A Restricted Administrator can be explicitly granted permission to perform almost all tasks a Global Administator can, on a task-by-task basis. For more information, see Modify User Profile Management Permissions.
Restricted Analyst
- Has LogRhythm database permissions that are limited only to read-only functions (investigations, tails, alarms and reports)
- Has specific permissions to view data from log sources, entities, and Data Processors (SQL Server enforced, View). Also known as LogRhythm Discretionary Access Control. This access control is primarily segregated by Entity, but can also be granted at a Data Processor and/or Log Source level.
- Has no access to Deployment Manager to make administrative changes (LogRhythm enforced)
SOAP API Service Administrator
- Full control of LogRhythm API functionality
For more information, see People and Users.