Configure the Azure Event Hub Beat
Configure Diagnostic Log Settings
If you collect a type of Diagnostic log and find the parsing is incomplete, see this Community Thread for details on how to submit feedback.
Each resource diagnostics log (for example, an individual Network Security Group) must be enabled individually.
- In your Azure Portal, select the Diagnostic settings option from Azure Services.
- In the grid, select the resource you want.
- (Optional) If the resource offers you the option to view the legacy experience, select it to disable legacy collection of activity logs. Otherwise, you will have duplication of data.
To disable this collection:- On the Log Analytics workspaces menu in the Azure portal, select the workspace to collect the Activity Log.
- In the Workspace Data Sources section in the menu on the left, select Azure Activity log.
- Click the subscription you want to disconnect.
- Click Disconnect, and then Yes to confirm.
- Select Add diagnostic setting.
- Type a name for the diagnostic setting.
- Select Stream to an event hub.
- Click Configure, and then select a Subscription, event hub namespace, and event hub policy name.
- Click Ok.
When you stream activity logs from any resource, activity logs from all resource groups within the same subscription are streamed to the chosen event hub.
Configure Microsoft Defender Log Settings
- You can Configure Microsoft Defender portal events logs to your Azure eventhub.
Configure AD Password Protection Log Settings
You can Configure AD Password Protection events logs to your Azure eventhub. First you can enable Password Protection on the cloud Environment.
- To enable the custom banned password list and add entries to it, complete the following steps:
- Sign in to the Azure portal using an account with global administrator permissions.
- Search for and select Azure Active Directory, then choose Security from the menu on the left-hand side.
- Under the Manage menu header, select Authentication methods, then Password protection.
- Set the option for Enforce custom list to Yes.
- Add strings to the Custom banned password list, one string per line. The following considerations and limitations apply to the custom banned password list:
- The custom banned password list can contain up to 1000 terms.
- The custom banned password list is case-insensitive.
- The custom banned password list considers common character substitution, such as "o" and "0", or "a" and "@".
- The minimum string length is four characters, and the maximum is 16 characters.
- Specify your own custom passwords to ban, as shown in the following example
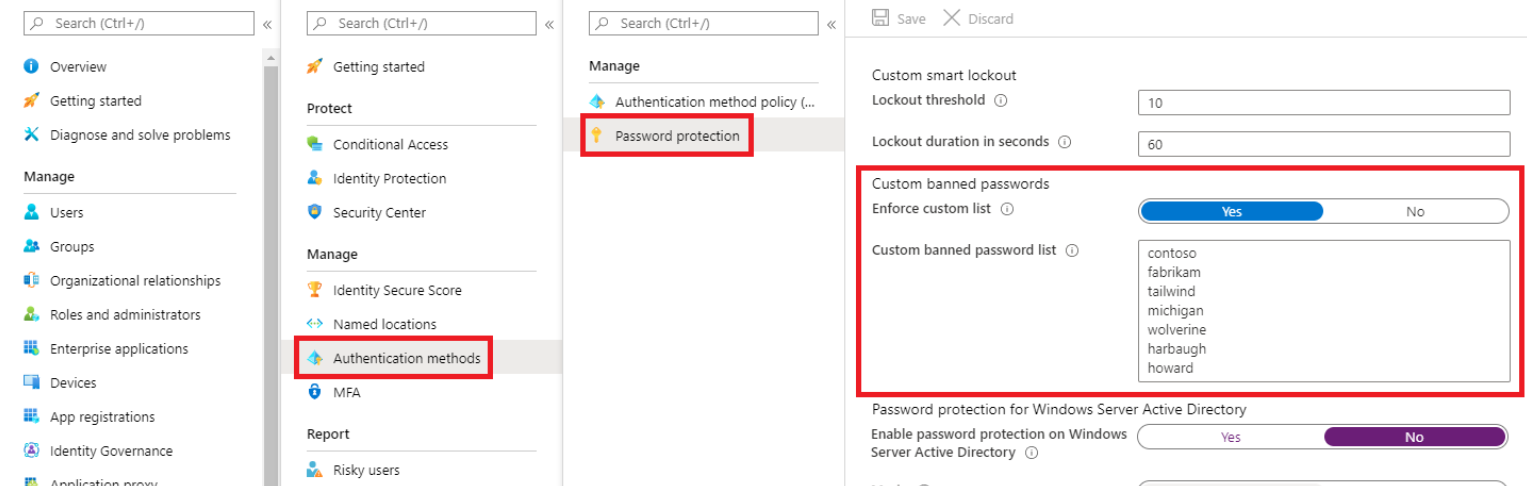
- Mode of operations - There are two option that APP allowed on the portal to apply as shown in above snapshot are described below:-
- Audit Mode - Audit mode is intended as a way to run the software in a "what if" mode. Each Azure AD Password Protection DC agent service evaluates an incoming password according to the currently active policy.
- Enforced Mode - Enforced mode is intended as the final configuration. Like when in audit mode, each Azure AD Password Protection DC agent service evaluates incoming passwords according to the currently active policy. When enforced mode is enabled though, a password that's considered insecure according to the policy is rejected.
- Log Generation
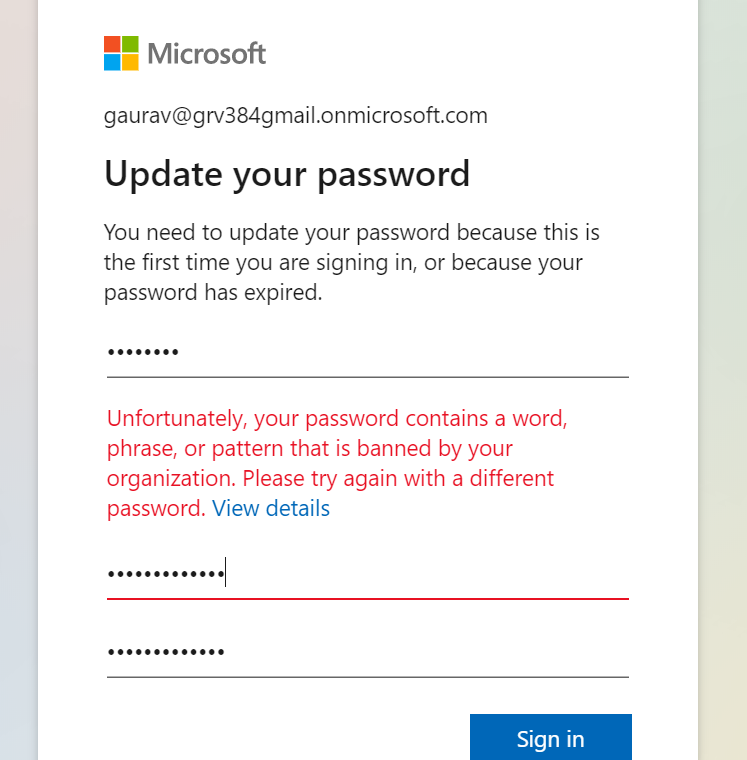
- After implementing all the step APP is applied on the all cloud user listed in azure directory. So whenever the user is tried to login or access the Enterprise application with banned password they are not allowed to login, as shown in the following example
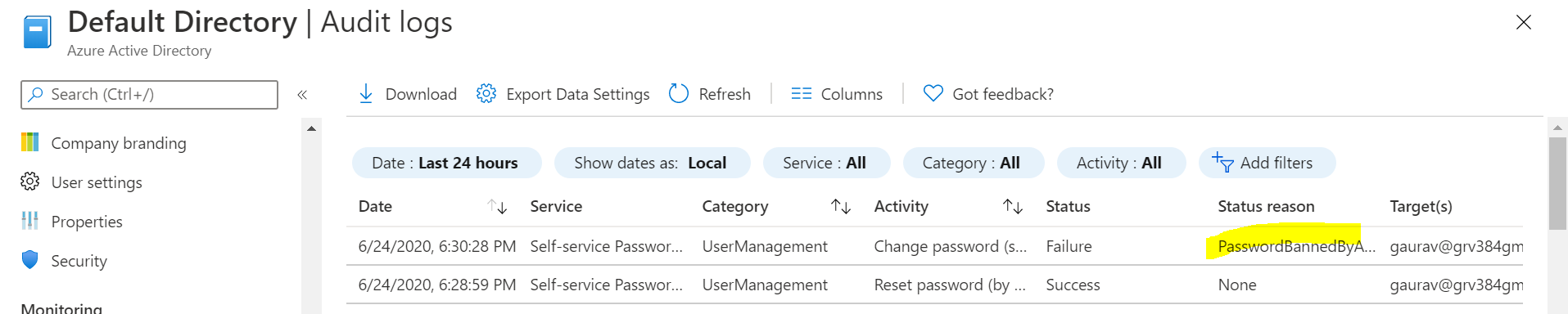
- After completing the above activity, we can observe that these event logs are getting generate in audit logs and further we can route this to the event hub by using the diagnostic setting. below is screenshot for the same:-
- Streaming to Event Hub
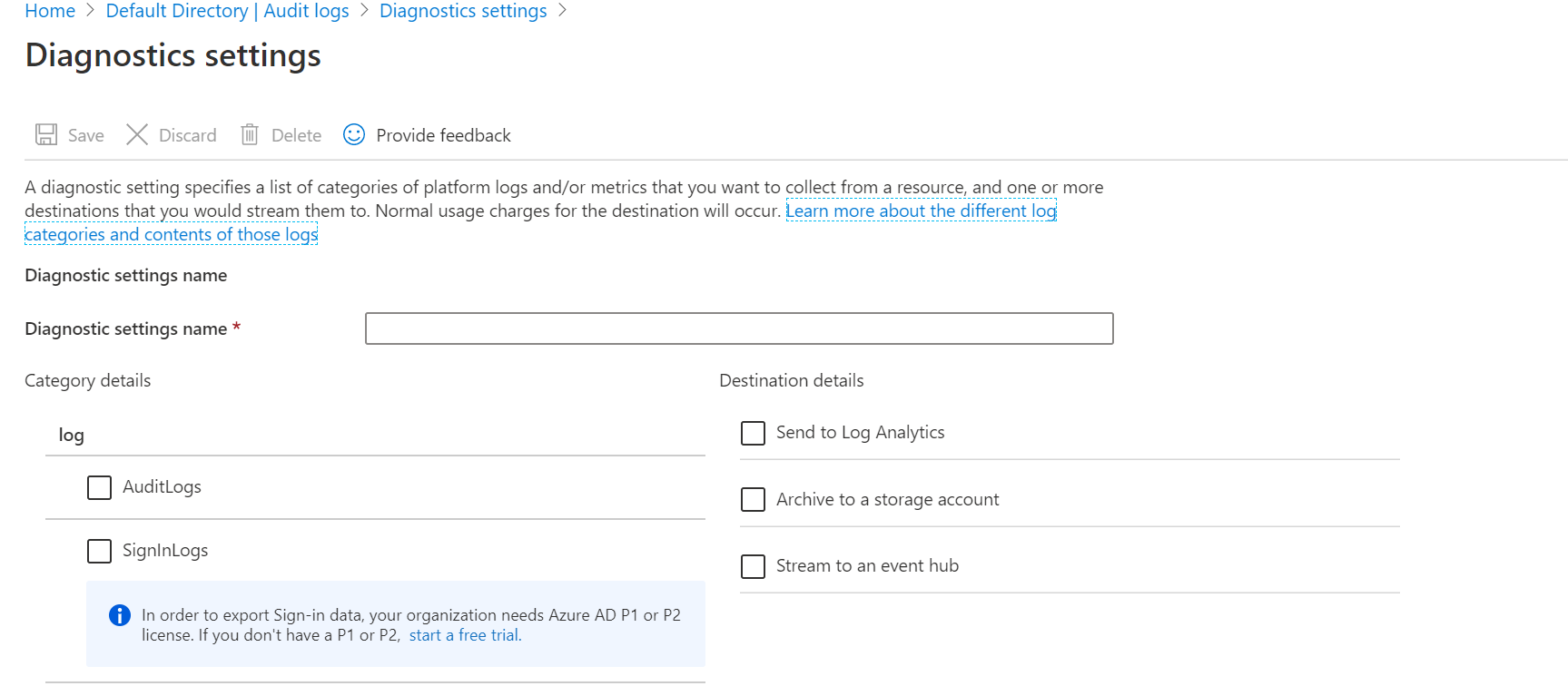
Audit logs can be route to Event hub by configuring the Diagnostic setting. Steps are given below:-
- Go to the Active Directory and select the audit log under monitoring
- Click on Add diagnostic setting
Now select audit log and click on stream to event hub option as shown in the below snapshot
- After implementing all the step APP is applied on the all cloud user listed in azure directory. So whenever the user is tried to login or access the Enterprise application with banned password they are not allowed to login, as shown in the following example
Configure the Event Hub Beat and Open Collector
Below are the two approaches through which you can run the Event Hub Beat.
- Connection Strings. Use the Event Hub Beat Using Connection Strings instructions to complete.
- Azure Auth (Through MSI). Use the Event Hub Beat Using Azure Auth (MSI) instructions to complete.
Event Hub values are stored in encrypted format in the beat configuration. When upgrading to the most recent Event Hub beat version, you must reconfigure the beat to properly store the configuration values as encrypted, and then restart the beat.
