7.18.0 GA Release Notes - 1 October 2024
LogRhythm 7.18 introduces LogRhythm Intelligence - a seamless integration of LogRhythm SIEM and Exabeam UEBA. Now you can get actionable AI-powered behavioral detections right in the SIEM!
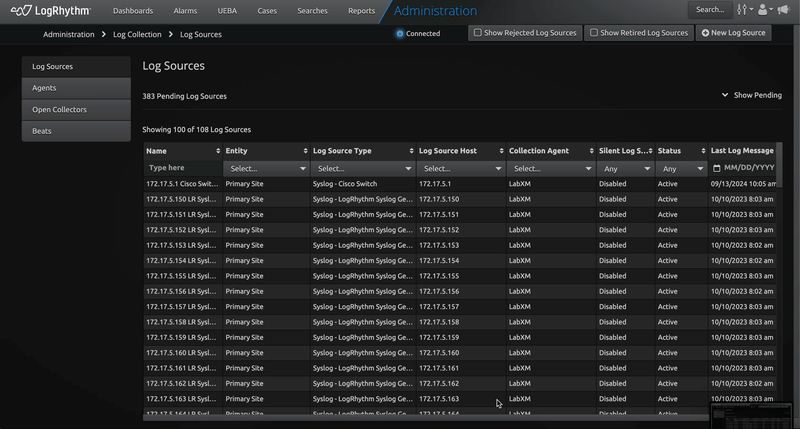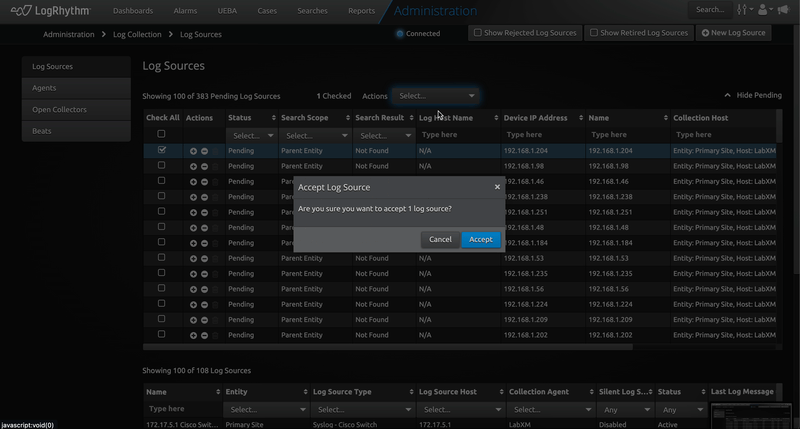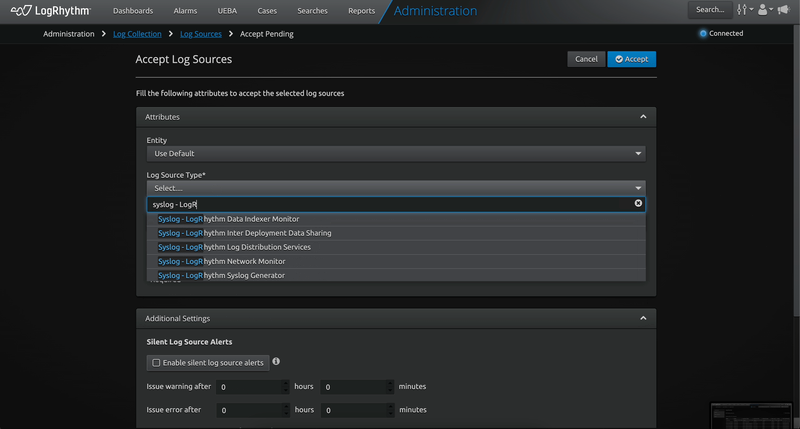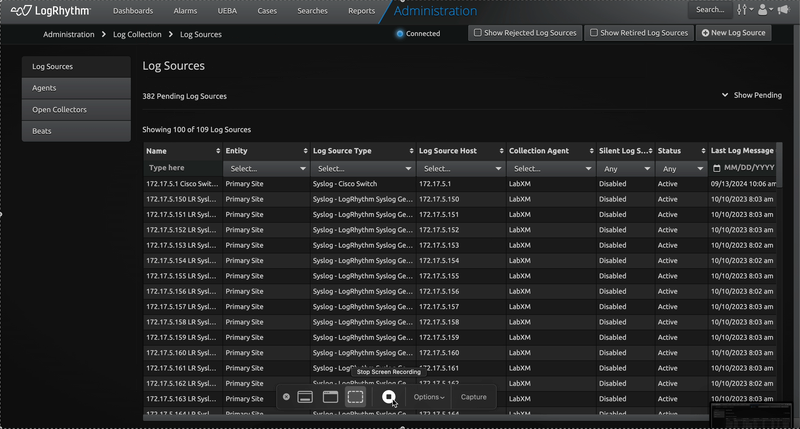
With LogRhythm 7.18, onboarding pending log sources is a breeze. Accept, reject, and delete pending sources all from within the Web Console! With these new features, security analysts can get a better view across the organization. Collecting mission critical log sources has never been easier!
This release also includes new versions of Elasticsearch and the Advanced Intelligence Engine service, make security analytics more powerful and enabling greater efficiency with quicker and more accurate TDIR. Platform improvements include:
Up to 80% decrease in DX heap consumption.
Up to 50% improvement in detection pipeline throughput.
Up to 10x improvement in processing of pattern matching rules.
Up to 87% faster loading of log sources in the client console.
And don’t miss out on over 60 new and enhanced log sources, including Rubrik, Anomali, and Akamai, added to over 1,000 existing out-of-the-box log sources as a continued commitment to provide customers accurate and modern TDIR.
What’s new in SIEM 7.18:
Maintenance
LogRhythm Intelligence
We are excited to announce LogRhythm Intelligence!
LogRhythm Intelligence introduces a cutting-edge AI-powered add-on that integrates behavioral detections into the LogRhythm Machine Data Intelligence (MDI) Fabric. This enhancement aims to escalate anomalous activities performed by users and hosts into the LogRhythm SIEM user interface. Leveraging insights from 795 behavioral models and 1,800 fact-based rules, you can now create searches, dashboards, reports, and implement security orchestration and automated response (SOAR) functionalities directly within LogRhythm SIEM. This advancement provides enhanced visibility into advanced cyber threats and tactics, including malicious insiders, compromised credentials, and lateral movement. With the help of LogRhythm Intelligence, you can achieve quicker and more precise Threat Detection and Incident Response (TDIR) outcomes.
Syslog Log Source Acceptance in Web Console
Expanding on the Open Collector and Beat management features added to the web console in previous versions, LogRhythm 7.18 introduces the ability to accept pending syslog log sources within the web console! This new workflow allows for a faster and more streamlined onboarding of pending syslog log sources all within the web console. LogRhythm Administrators will find this workflow allows for easier batch operations, and options such as the Processing Policy are pre-selected, saving you time and confusion when accepting new syslog log sources.
For more information, refer to the Manage Pending Log Sources documentation.
Exabeam Case Beat
Alert by Exabeam is a cloud application that categorizes, aggregates, and enriches security alerts for analysts. With the Exabeam Case Beat, you can collect those alerts using the LogRhythm Open Collector.
Setup is as easy as configuring a new API key within the Exabeam Security Operations Platform and then configuring the Exabeam Case Beat using JSON Parsing. This beat is also compatible with Beat Configuration in the Web Console. For more information on this new beat, refer to the Exabeam Case Beat documentation.
Log Source Additions and Improvements
As part of the bi-weekly LogRhythm SIEM Knowledge Base updates over the last quarter, nearly 50 log sources have been updated and/or improved, and 12 new log sources have been added, allowing for customers to increase their security footprint with log visibility within the LogRhythm SIEM.
New Log Sources | Updated or Improved Log Sources | ||
|---|---|---|---|
|
|
|
|
Enhancements & Resolved Issues
Data Indexer Elasticsearch Update to 7.10.2 OSS
The Data Indexer (for both Windows and Linux) has been upgraded from Elasticsearch 6.8.23 to 7.10.2 OSS. Elasticsearch version 7.10.2 is the latest OSS release, offering many new features and improvements, including:
An increase in usable Hot TTL per Elasticsearch node through the reduction in Segment Terms Heap memory consumption for online indexes;
An adaptive Replica Selection for faster search results across the cluster;
Improved data compression as part of Lucene 8.7;
Support for updated Kibana 7.10.2 OSS version; and
Improved indexing performance.
As part of this upgrade, Elasticsearch 5 Indexes (LR 7.7 July 2021 or older) are no longer supported after upgrading to LogRhythm 7.18. If you believe you may have indexes older than July 2021 that have not aged out (archive restoration indexes), or you have recently upgraded from a LogRhythm version prior to 7.7, its strongly advised to check using the Upgrade Checker utility prior to upgrading your deployment. In the event that you have ES5 indexes, you can restore the data from Inactive Archives or wait for the data to age out before upgrading to LR 7.18.
For users with a Linux DX, when upgrading to 7.18+ it is strongly advised not to use the “--skip-upgrade-checker” command unless your cluster is down prior to the upgrade. The health checker contains very important validations which ensure that your cluster is “Upgrade Ready” prior to the upgrade. Running the Installer with the “--skip-upgrade-checker” option may render your cluster unable to start following the upgrade and require manual migration work. See the Post Upgrade section of the DX Upgrade Checker documentation for more information.
Customers using Kibana with LogRhythm will be required to upgrade Kibana to a matching version. For more information on this process, refer to the Using Kibana with LogRhythm SIEM topic.
AIE Update to .NET 8 Framework
The AI Engine service (AIE) has been migrated from .NET Framework 4.7 to the .NET Core 8. The .NET Core 8 code base has been optimized for modern operating systems and offers improvements in performance, compatibility and features. The .NET Core 8 AIE offers a number of performance improvements, including:
Better service memory management under duress, leading to increased stability;
Lower overall CPU resource consumption under identical load profiles;
Increased performance while processing regex/pattern based rule blocks;
Higher peak and sustained load handling on identical systems under identical rule configurations; and
Greater benefits on newer Windows Operating Systems (Server 2022).
This change introduces the requirement of .NET Core 8.0.3+ as part of the AI Engine service joining the Data Processor update from 7.17. Off-line installations may require downloading the .NET Core Windows Desktop Runtime here. .NET Core introduces new Environment Variables used for runtime configuration of .NET 8, these variables should not be modified except under the direction of support or engineering.
Client Console Improvements to Log Sources Grid
Loading of the Log Sources grid in the Client Console’s Deployment Manager has been optimized for loading a larger number of records. Log Source load times are now 87% faster.
Additionally, a new option has been added to the General tab of the My Preferences screen that allows you to disable auto-refresh of the Log Sources grid. When auto-refresh is enabled (default), the Log Sources grid will now only update when there are changes to the entities displayed in the grid, reducing the amount of time the screen spends reloading and in between states. With auto-refresh disabled, the grid will only refresh when you manually choose to refresh it.
Resolved Issues
Bug # | Component | Description |
|---|---|---|
ENG-11163 | Documentation: Search | The Basic Queries documentation has been updated to be clearer regarding Lucene filters. |
ENG-11184 | Smart Response Plugins | The CrowdStrike Smart Response Plugin (SRP) has been updated to resolve an error relating to the API base URL. |
ENG-24428 | Client Console: Log Sources Grid | The Log Sources grid has been enhanced in a number of ways to improve performance. Refer to the Client Console Improvements to Log Sources Grid section of the release notes for more information. |
ENG-36433 | Reporting | An issue with the “Case Details” report under the Case Management class of reports not providing results limited to the specified timeframe has been resolved. |
ENG-38427 | Client Console: Lists | When editing a list, the TTL Expiring Items option can now be unchecked as expected. |
ENG-39760 | APIs | The API workflow UI has been updated to be clearer regarding modification of the API key’s expiration date. |
ENG-50328 | APIs | The LR Metrics API Log Volume endpoint search now returns consistent and correct values. |
ENG-52744 | Metrics | The AIE Metrics Dashboard in Grafana now correctly auto-refreshes and updates when changing the Host value. |
ENG-53808 | User Profiles | Changes made in User Profile Manager now correctly update after a sync. |
ENG-53846 | AI Engine | An issue with the “Notify the following groups” section of the AIE Notify tab sending notifications regardless of whether the options “Is Silent” or “Can Batch” are checked has been resolved. |
ENG-54557 | Reporting | The “Normal Date” field can now correctly be saved as a top-level group field in a custom report template. |
ENG-54671 | Reporting | When exporting the Investigation report to a .csv file, the “Direction” field now correctly displays “Unknown” instead of a blank field. |
ENG-58107 | Metrics | Grafana has been updated to version 10.3.7 for Centralized Metrics. |
ENG-58299 | APIs | The Admin API can now correctly be used to create new syslog log sources with virtual identifiers enabled and assigned. |
ENG-58413 | Log Parsing | The JSON System Monitor Agent Okta parser has been updated so that “alternateID” is used for account/login parsing instead of “id”. |
ENG-58812 | Web Console | Custom filters on a Web Console Dashboard are now correctly maintained when drilling down on a Dashboard item. |
ENG-59097 | AI Engine | Two new optional parameters have been added to the LRAIEngine.ini file that can control the processing of AIE Stats: DiagnosticsEngineStatsWritingInterval=1 [Default - 1, Min - 1, Max 60] |
ENG-59183 | Web Console | The Log Sources list now displays properly in the Web Console UI. |
ENG-59310 | Search | An issue where finding a log exception during a search caused the search to halt completely has been resolved. Now, the log exception is marked as missed and the search loop continues as expected. |
ENG-59388 | Log Parsing | Additional parsing fields have been added to the Cisco Duo log source type. |
ENG-59427 | AI Engine | AI Engine Data Provider statistics are now correctly logged in the lraiedp.log file. |
ENG-60405 | AI Engine | An issue with incorrect Data Provider values being displayed within the AIE Communication Manager has been resolved. |
ENG-60768 | Log Parsing | Additional parsing fields have been added to the Proofpoint log source type. |
ENG-61115 | Documentation: FIPS | The LogRhythm FIPS package located on the Community has been updated for versions 7.17 and 7.18, and the documentation for Configure LogRhythm DX has been updated with additional steps to ensure the FIPS package is successfully implemented. |
ENG-61136 | Reporting | The Log Volume by Day report now correctly gives consistent results, including no longer dropping days from selected timeframes. |
ENG-61182 | System Monitor: Mediator | The Mediator now reloads its System Monitor configuration cache once per minute as opposed to every time a System Monitor connects. This prevents the SQL server from being overwhelmed by config cache updates. |
ENG-61277 | Log Parsing | The JSON System Monitor MSGraphBeat parser has been updated with additional fields. |
ENG-61359 | Log Parsing | Resolves various parsing issues with the Data Processor parser. |
ENG-61401 | Documentation: APIs | The documentation for the LR Admin API endpoint UpdateLogSource has been updated to correctly state the required fields. |
ENG-61737 | Log Parsing | The JSON System Monitor Azure Event Hub parser has been updated with additional fields. |
Resolved Issues - Security
Security-related issues resolved with this release are available for customers to view in the Community.
Known Issues
The following issues have each been found and reported by multiple users.
Bug # | Found In Version | Components | Description | Notes |
|---|---|---|---|---|
ENG-41651 | 7.12 | Web Console | After upgrading to 7.12 or newer, the CAC authorization used to log in to the Web Console stops working. | Expected Results: The CAC authorization should work when logging in to the Web Console. Workaround: There is currently no workaround for this issue. |
ENG-62271 | 7.18 | Data Indexer | After upgrading to 7.18, LogRhythm has bundled an upgrade to Elasticsearch OSS 7.10.2 which uses log4J version 2.11.1 and may flag on scanners as being affected by a remote code execution vulnerability in the JNDI parser. | LogRhythm bundled in the jvm options of the 7.18 release mitigations for the log4J vulnerabilities by setting the “-Dlog4j2.formatMsgNoLookups=true”. This is present on both the Windows and Linux build of the Data Indexer. Scanner findings can be considered a false positive. The log4J version will be updated in a future release as part of the DX Update roadmap in 2025. |
ENG-62275 | 7.18 | Data Indexer | Searches containing more than 65k fields/terms in the query may fail. This includes searches using lists with >65k items in them. | Workaround:
Linux systems must update all nodes in the cluster - /usr/local/logrhythm/transporter/logs.json
After modification to the transporter template, restart the service. |
ENG-62332 | 7.18 | Data Indexer | Clusters Containing >600 days of Hot TTL fail to create new indexes due to Shards Per Node limit | Workaround:
|
ENG-62339 | 7.18 | Client Console | Some customers may experience issues with displaying “Last Log Messages” under the Deployment Manager > Log Sources tab. This appears to be isolated to conditions where the OS region does not match the region configured in client console, but the languages are the same. (OS = US/English, Client Console = Indonesia/English) | Workaround:
|
