7.16.0 GA Release Notes - 1 April 2024
LogRhythm 7.16 introduces configuration options that help analysts tune out unnecessary diagnostic events to save disk space and processing time. This release features case separation based on Entity and RBAC controls, so administrators can ensure multitenant customers and individual business units can only access data assigned to them. In addition, LogRhythm 7.16 simplifies the process to retire Open Collectors, Beats, and log sources in LogRhythm SIEM, reducing administrative overhead.
What’s new in SIEM 7.16:
Maintenance
Diagnostic Event Filtering
Diagnostic events that originate from the SIEM often take up valuable disk space from your organization. The reality is some of those events are purely informational and not needed for your team to do their jobs.
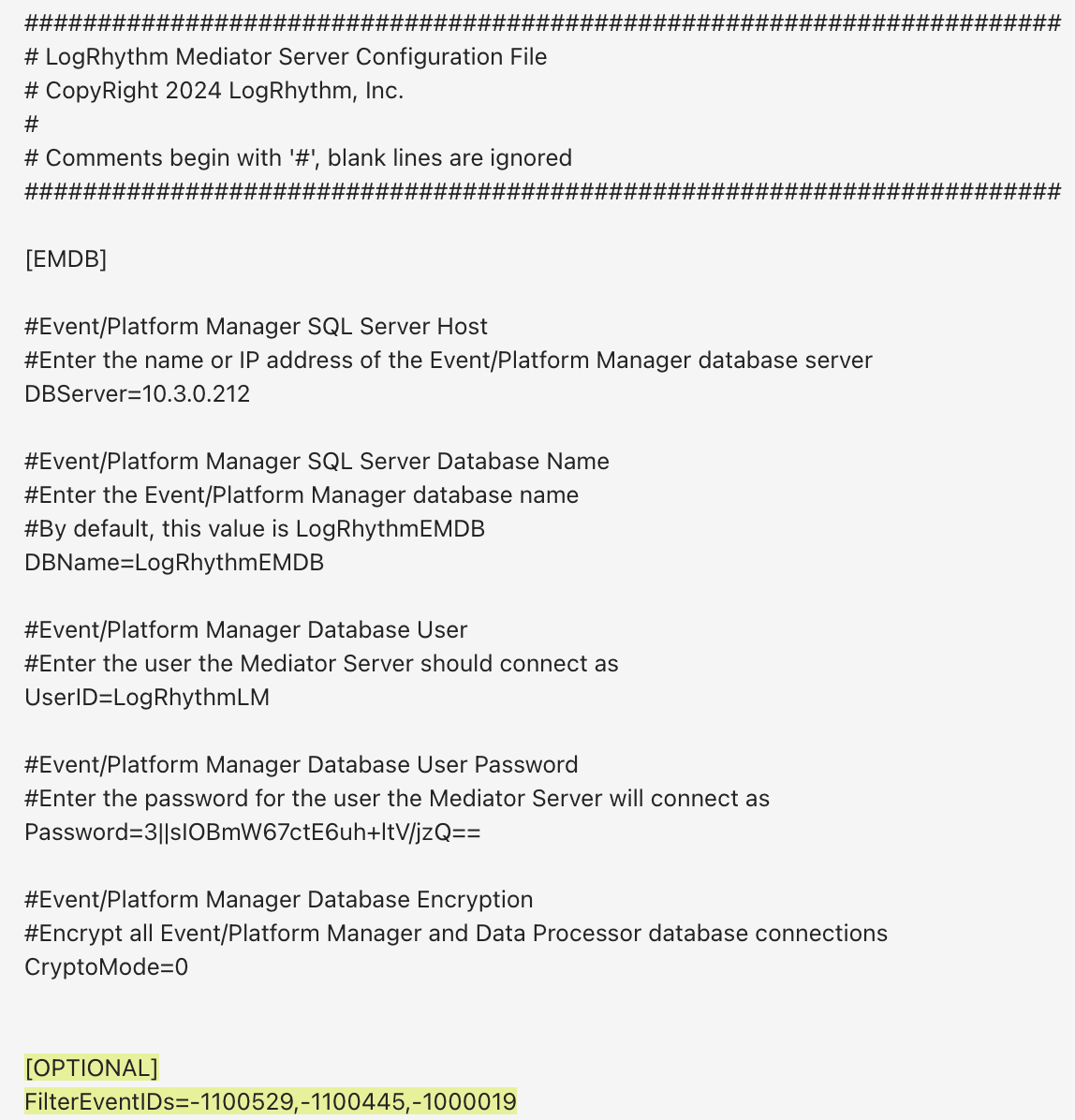
LogRhythm 7.16 now gives administrators the ability to tune out the noise, helping them focus on what matters. When you want to filter out an event, simply edit the Mediator configuration file, add the Event ID, and select the events you want to filter out. This will prevent non-critical events from being added to the Events Database, saving you disk space and processing time in the SIEM and Mediator. The benefit? The less you index in the Events Database, the fewer resources your system uses, maximizing its efficiency.
Case Management Data Separation
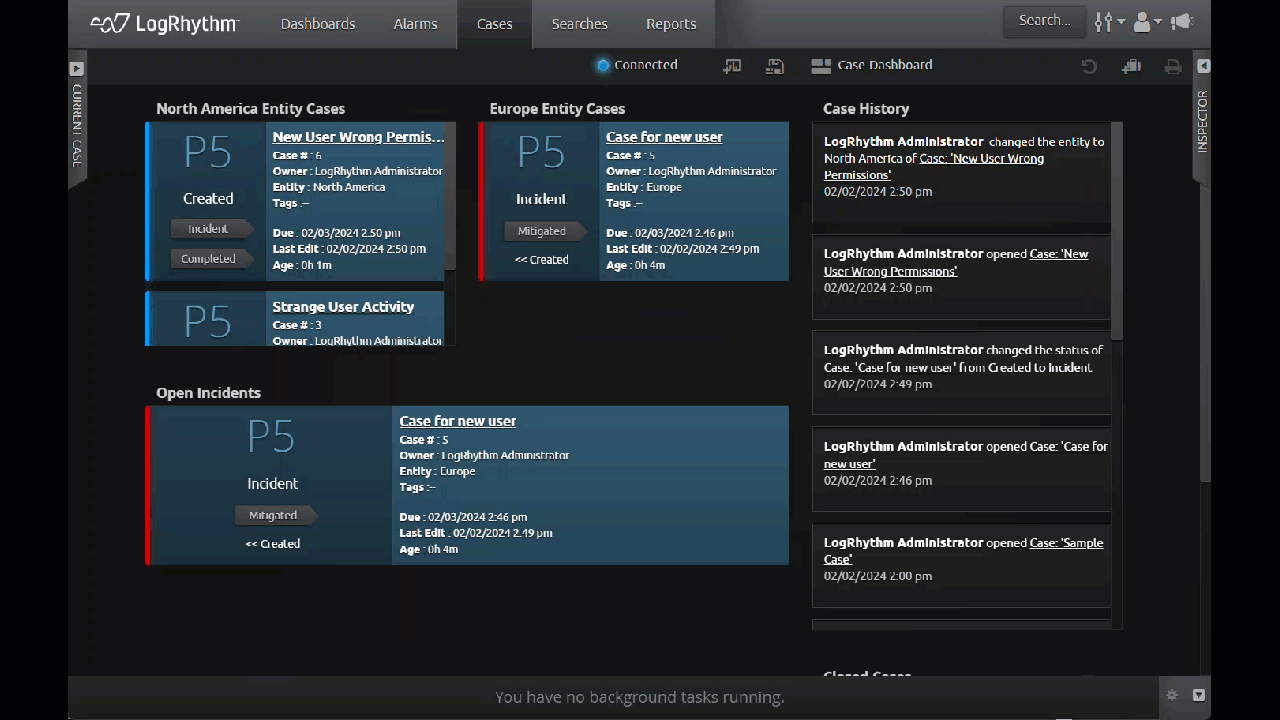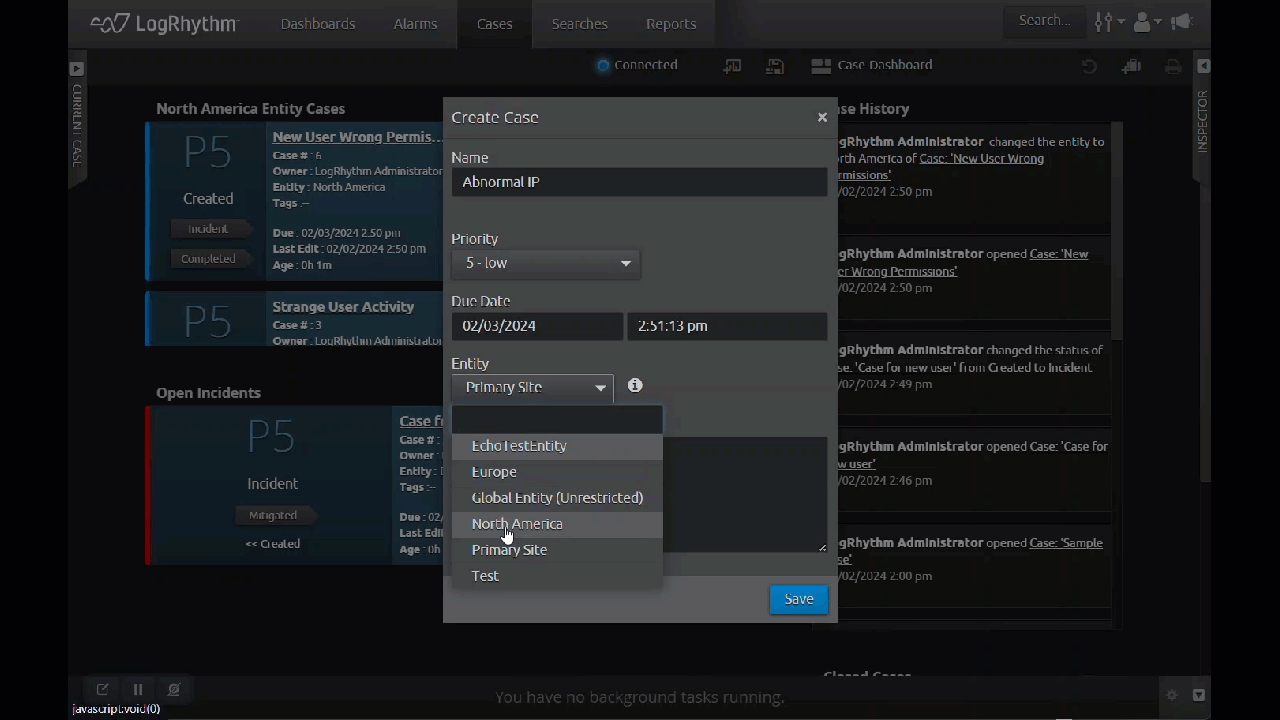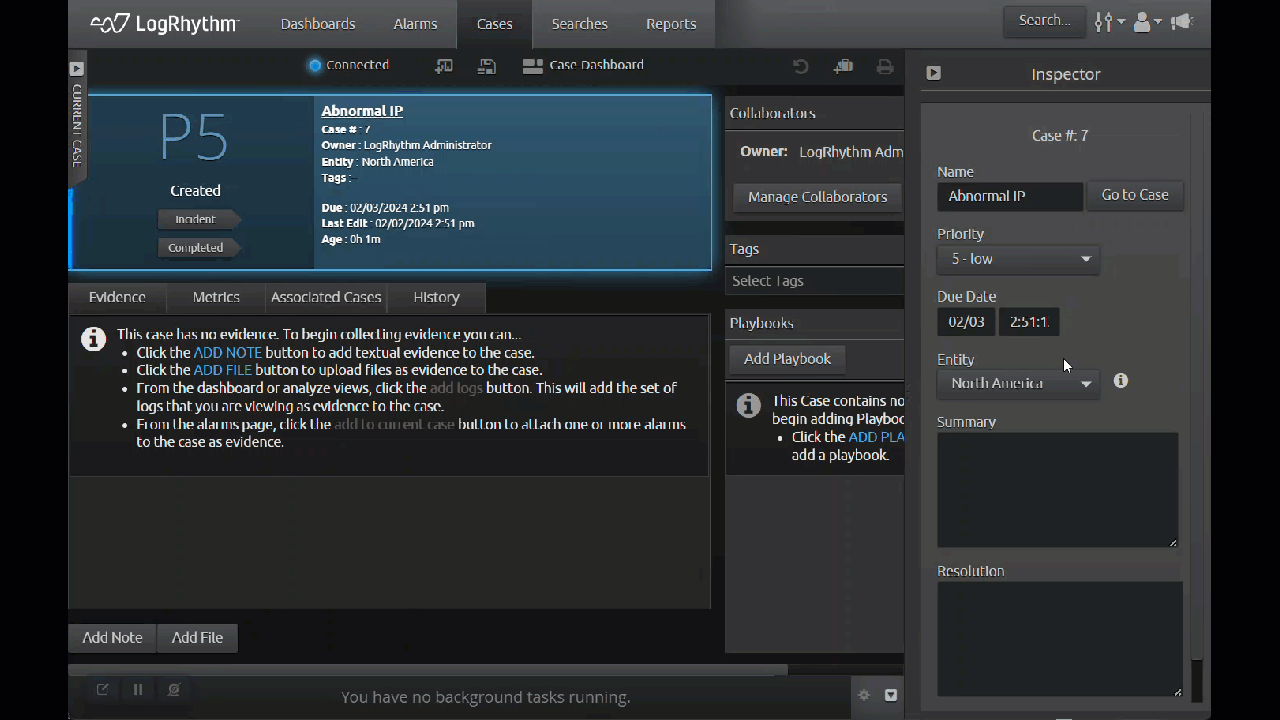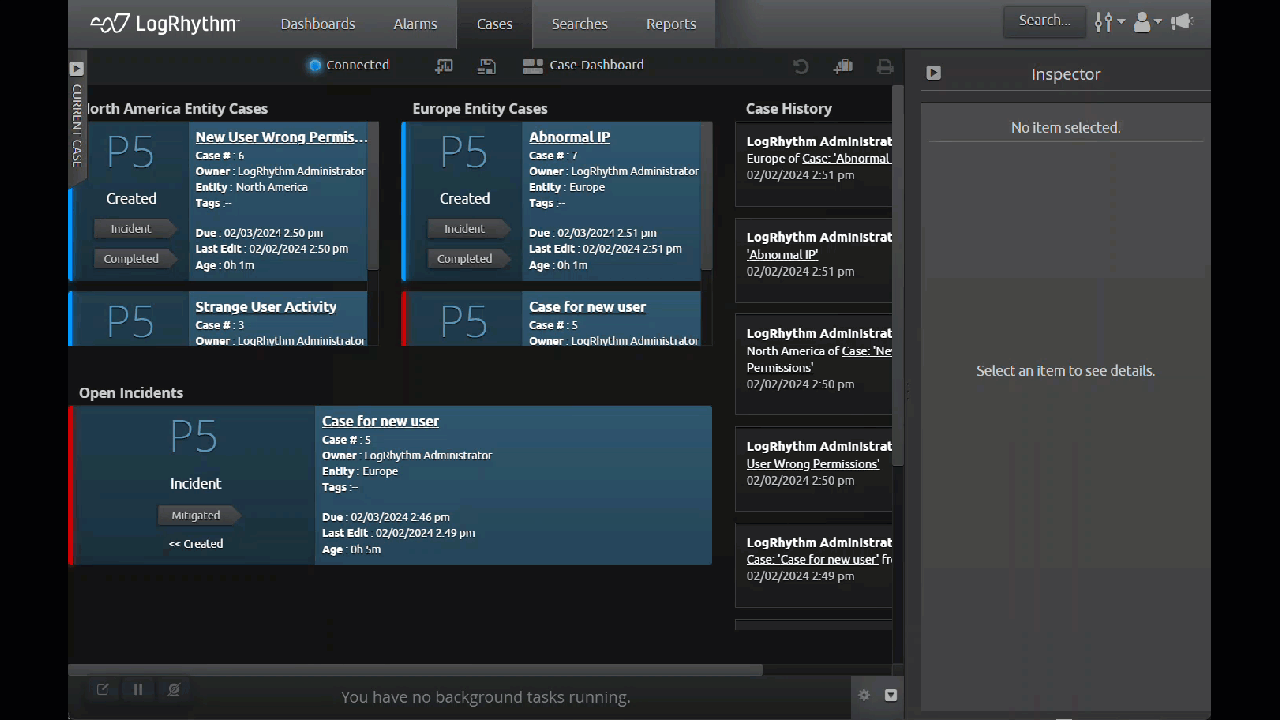
Business units and mulitenant environments can logically separate and secure data within the SIEM by using separate Entities. To streamline the workflow in the SIEM, LogRhythm 7.16 enables users to separate Cases based on Entity.
With the latest update, you can select an Entity when you create a new Case, and that Case will only be visible to people with access to that Entity. This gives administrators more control, ensuring that individual business units and multitenant customers only access data that is assigned to them through Entity separation and role-based access control (RBAC).
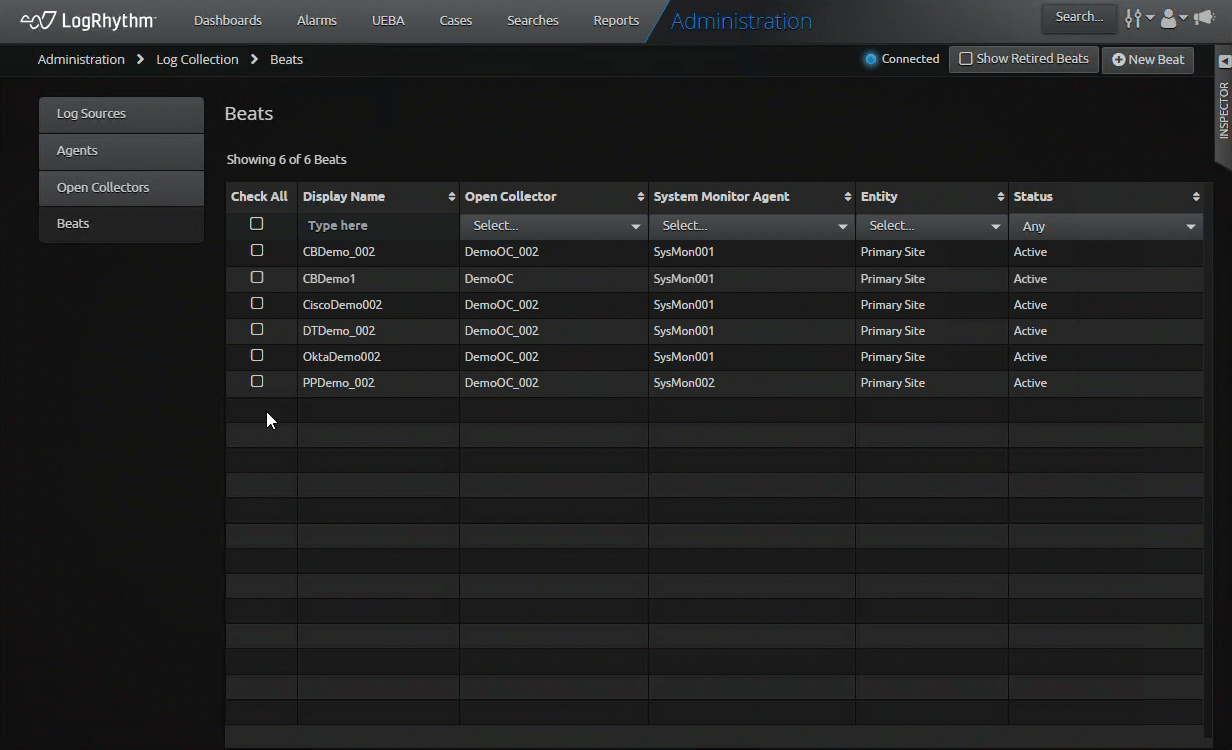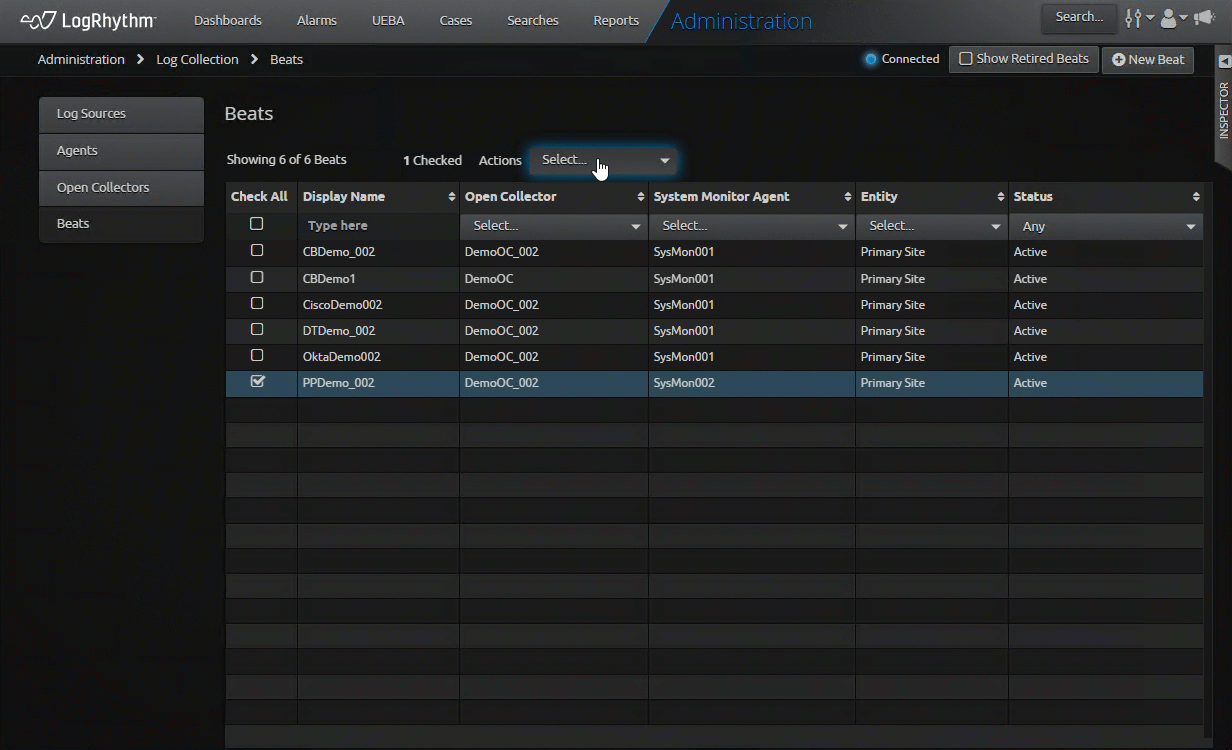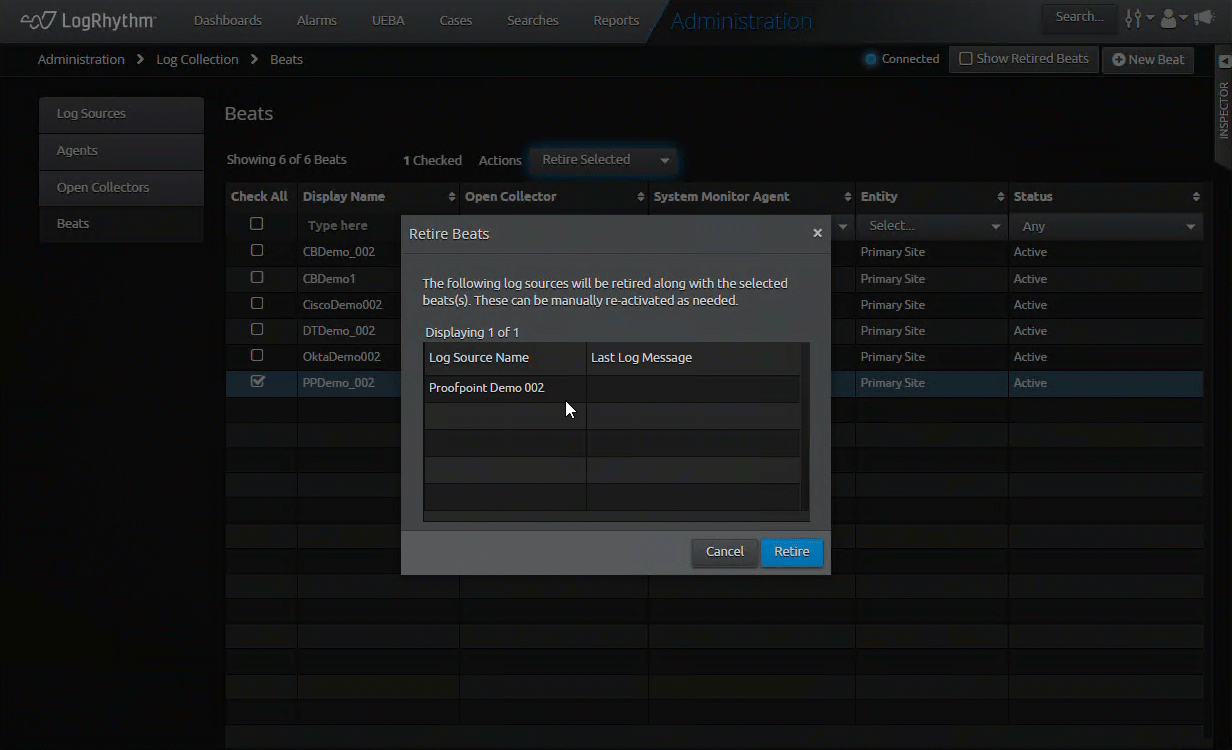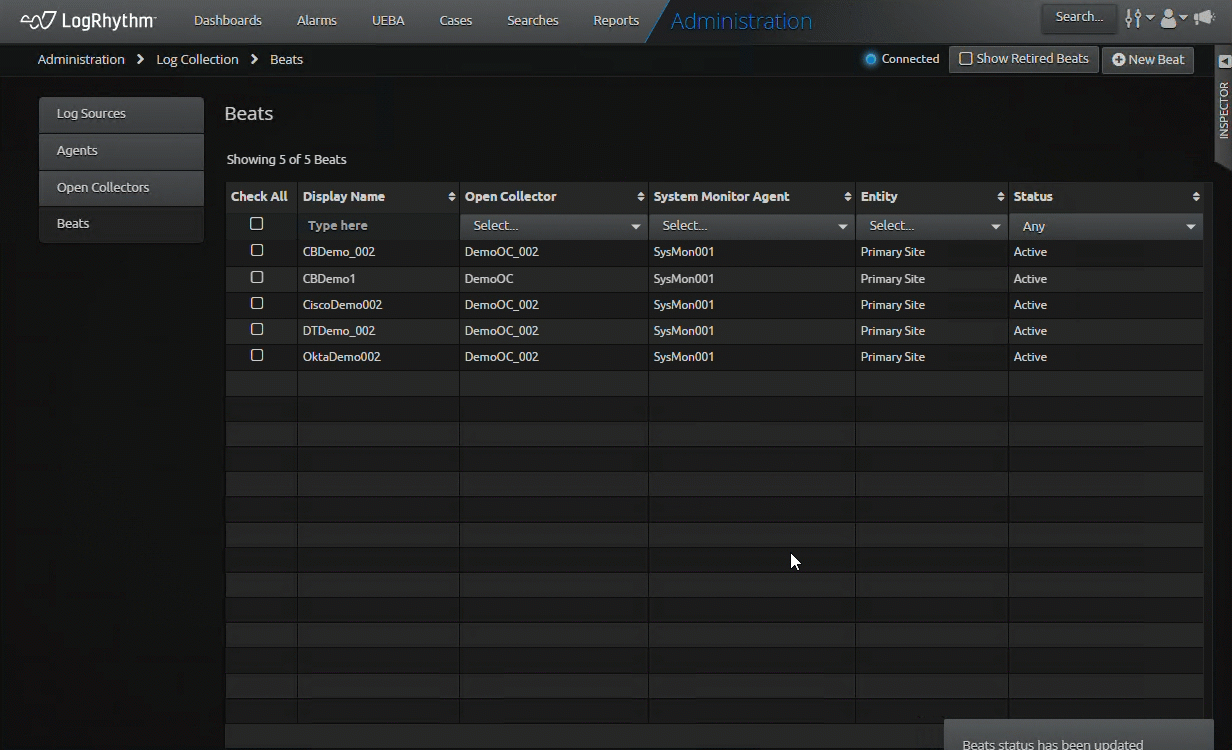
Streamlined Open Collector and Beat Retirement
What used to require numerous commands and regular references to our documentation is now streamlined in our Web Console. Building on the features we introduced in LogRhythm 7.14, this release takes the vision of Open Collector to the next level with a simplified and intuitive workflow in the Web Console.
As part of our effort to improve workflows for our customers, we are introducing more administration in the Web Console, re-imagining workflows to increase speed and performance. In LogRhythm 7.16, we improve the process to retire a Beat or Open Collector. You no longer need to go to another section of the SIEM to retire associated log sources when retiring a Beat or Open Collector. The latest SIEM update automatically retires them for you.
This feature enables the SIEM to simplify and automate previously manual tasks, allowing users more time to focus on security rather than SIEM administration. By automating log source retirement, you can reduce the number of clicks by at least 50 percent. This enables you to configure and update numerous log sources, reducing your administrative overhead.
Configure Windows Event Log XML Filters with the Admin API
Configured logging levels can often be more granular than you need, creating clutter in Windows Event Logs and using up precious processing cycles and space in your SIEM. And filtering out these messages at the agent would require regex, as well as local processing cycles. That’s why version 7.9 introduced the ability to use Windows XML query format to target and collect only the specified types of Windows Event logs you need.
With LogRhythm 7.16, we expand this capability into the REST API, updating log source management endpoints to include XML filter configuration options. Now administrators can reduce admin overhead by programmatically configuring and updating Windows Event log sources through the API.
New and Updated Log Sources
As part of LogRhythm 7.16, we are excited to introduce a new Linux Host log source. This new log source combats some of the challenges we have seen over the years with a growing number of log sources being combined into a single log source type. In the latest release, we are separating Syslog Linux to specifically support OS level logging.
To improve management, performance, and reliability, LogRhythm is working on a multi-quarter project to divide the Linux Host log source and others in future releases into separate log source types that can be leveraged using Log Source Virtualization. This will ensure customers can minimize the extra rules of tools or components that are not in use, and instead ensure maximum performance on the components in use.
To support our ongoing commitment to you, we continually update and improve Message Processor Engine (MPE) rules. As such, a crucial step in maintaining a healthy security posture is to normalize log messages. This helps ensure that you get more value out of the log data LogRhythm ingests and the security insight power of LogRhythm’s Machine Data Intelligence (MDI) Fabric.
A few of the highlights released over the last three months include:
Firewall security – The insight provided from firewalls is critical for protecting organizations. This quarter, LogRhythm released improvements for firewalls such as: Palo Alto Networks, Fortinet FortiGate, Forcepoint Stonesoft, Check Point, and Juniper Networks firewalls. With these improvements, LogRhythm customers will find greater value in the log enrichment and can better defend against threats.
Cloud Security – Protecting cloud resources is more critical today than ever before. That’s why we made improvements to cloud log sources. This quarter, LogRhythm improved: Azure Event Hub, AWS CloudTrail, and Gmail Message Tracking. These improvements ensure organizations that use these cloud solutions have effective visibility in their SIEM to detect, respond, and prevent threats.
Endpoint – Regardless of whether you are protecting end users or servers, to effectively monitor endpoints, it’s crucial be aware of new and emerging threats. With LogRhythm SIEM 7.16, LogRhythm’s improved CrowdStrike, Kaspersky, Windows Event logging, Linux, and AIX normalization rules ensure you get the most accurate information out of the logs to maximize your security awareness.
And those are just the highlights! LogRhythm updated more than 30 log sources over the last quarter, and we will continue to update more as part of our commitment to our customers’ successful security practices.
LogRhythm constantly reviews our supported log sources, and we make updates to strengthen our correlation and analysis. Some of our enhanced log sources for this quarter are:
Source | LogRhythm Enhancement |
|---|---|
Windows Event Log - Application | Added support for additional event IDs |
Windows Event Log - Security | Improved parsing of process names and their paths, as well as improved parsing of remote user account logon failed logs. |
Cisco FireSIGHT | Improved parsing to include session information as well as process and task information. |
F5 BIG-IP ASM | Improved support for multiple versions of the F5 product, also improved parsing of source IP, Authenticator and other logs. |
Juniper Firewall | Parsing for Dot1X and Kernel messages added and improved other parsing rules. |
Azure Event Hub | Improvements on bad token and sign-in failed logs |
SonicWall | Improved VPN log parsing |
Palo Alto Firewall | Corrections made for parsing Threat information as well as adding parsing for Application Characteristic |
CentOS to Rocky Linux Migration ISO
In our last quarterly release, LogRhythm created a detailed guide to help customers migrate to Rocky Linux. This quarter, LogRhythm introduces improved CentOS to Rocky upgrades by providing an ISO customers can mount. This helps customers perform upgrade steps faster, simplifying a complex migration and streamlining the process to upgrade to Rocky Linux. It might sound daunting, but we have worked hard to simplify the process for the migration. If you aren’t comfortable or able to manage this effort, reach out and get help from our Services team!
In-Platform Resource Center Tutorials
Building on our effort to enable customers, the LogRhythm Training and Enablement team added a new tutorial to the Resource Center. This guide focuses on the power of the Inspector window. Check out the Onboarding section of the Resource Center to see the tutorials included for free in the LogRhythm SIEM.
Enhancements & Resolved Issues
Bug # | Component | Description |
|---|---|---|
ENG-11118 | Web Console | The Web Console now displays all test results for filters by object, procedure name, or command metadata field using quoted filters. |
ENG-23752 | Web Console | When metadata contains double quotes, that data is now visible in the Analyzer page of the Web Console. |
ENG-24430 | Smart Response Plugin | Users can now successfully update the SmartResponse Plugin to the new version of the plugin. |
ENG-24994 | Smart Response Plugin | SmartResponse Plugins can process agent queries with values up to 5000 and effectively display all necessary data. |
ENG-32128 | Agents: Azure EventHub Log Collection | Added parsing support for Source IP, Destination IP Messages, and Actions on Azure Event Hubs Beat Logs. |
ENG-32134 | Agents: Azure EventHub Log Collection | Custom parsing is now enabled for Azure Eventhub Defender logs. |
ENG-33123 | Agents: AWS Guard Duty Log Collection | Additional parsing rules are now added for AWS Guard Duty Logs in the Open Collector JSON parsing engine for System Monitor. |
ENG-33633 | SysMon | All corresponding QIDs are now collected with the respective logs. |
ENG-35329 | Agents: Azure EventHub Log Collections | Token corruption in Eventhubbeat is now rectified by mapping SIPs correctly. |
ENG-40079 | Web Console | Warm index results are now included in the investigation of direct export. |
ENG-43218 | Configuration Manager | The “Database Connection Timeout” option has been added to Configuration Manager to allow users to configure the amount of time that must pass before a connection times out. |
ENG-47211 | Job Manager | As of the 7.16 Release, Job Manager has a new memory cache of identity display names and it will automatically refresh every 24 hours, or 1440 minutes. If needed, a new optional parameter in jobmgr.ini can be used to change this refresh interval. The smallest value it can have is 60 minutes. |
ENG-47312 | Web Console | Dashboard widget settings now persist and are no longer reset in certain circumstances. |
ENG-49007 | Agents: Windows | Windows Agents in the pending list are now accepted without generating errors in the System Monitor Policy Manager. |
ENG-49013 | Agents: Azure EventHub Log Collection | Additional parsing rules are now added for Azure Eventhub Defender logs in the Open Collector JSON parsing engine for System Monitor. |
ENG-49073 | SysMon | Logs received by the indexer are timestamped at the event, so the System Monitor JSON parser now accurately parses dates. |
ENG-49584 | SysMon | The Agent JSON parser now parses metadata fields one at a time instead of duplicates. |
ENG-49867 | Installation Components | Instead of generating a PowerShell error, reboots that are necessary during DR installations now proceed with the installation correctly. |
ENG-50481 | Web Console: UI | The old LR logo has been replaced with the new LR logo when opening a Case in the Web Console. |
ENG-50668 | Installation Components | An issue with installer pathing during a silent HA install/upgrade has been resolved. |
ENG-50692 | Infrastructure: Upgrade Scripts | 7.13 DB upgrade now successfully shows object reference set to an instance of an object when attaching a license in the check step before the upgrade. |
ENG-51997 | SIEM Core Services | Windows 2022 and Windows 11 are now available as OS options when creating a new Entity host. Additionally, it has been added to the Import Computers inside Windows Host Wizard. |
ENG-52000 | Reports |
|
ENG-52134 | SmartResponse Plugins | The contents of invalid SRP parameters are no longer stuck in an infinite loop when an AI alarm is triggered, but instead, it is retrieved twice. |
ENG-52387 | Package Manager | The upgrade .tar.gz package format has been fixed to conform to GNU for window applications that decompress and extract files. Now the package manager can upload the Suse package. |
ENG-52746 | Client Console | The Target Entity does not change automatically when enabling/disabling Automatic Log Source Approval Rules and importing the Knowledge Base File. |
ENG-52748 | Client Console | In the 7.16 Release, Client Console now can provide automatic access to newly created child entities to restricted admin if it has access to the root/parent entity. |
ENG-52992 | APIs | The Windows Authentication API and the Search API are two SecondLook APIs that now support the Windows account type for database authentication. The user can achieve this by modifying the DB Authentication strategy in Configuration Manager and adding Windows or domain account credentials to the Service Logon property. |
ENG-53096 | Job Manager | The customer can now successfully run the monthly Log Volume Report because the Scheduled Log Volume Report completes without a service restart and the Job Manager does not go to the old state. |
ENG-53484 | Data Processor | Windows remote log sources utilize pinned mode to collect logs when the agent switches from the secondary to the primary data processor. |
ENG-53564 | Agents: Windows, Beats Collection | For 7.13 and 7.14 Agents, after upgrading to 7.15, Beats collection works as expected without stopping or requiring manual restarts. |
ENG-53587 | Agents: Azure EventHub Log Collection | The latest update rectifies the misclassification of Azure Authentication Logs and introduces Eventhubbeat AADIAM log subrules to enhance the System Monitor JSON parser, thereby improving monitoring and classification accuracy. |
ENG-53588 | Agents: Gmail Message Tracking Log Collection | The latest Gmail Message Tracking Beat update adds subroutines to the System Monitor Agent's JSON parsing engine, improving accuracy and efficiency. |
ENG-53599 | Agents | The System Monitor Collector license type now allows the user to enable the IPFIC/NetFlow/J-Flow Server, sFlow Server, and sFlow Counter settings through the advanced properties of the collection agent type. |
ENG-53630 | SIEM Core Services | Now, the LogRhythm Service Registry ensures no extended undetected outages or server failover scenarios occur. The Consul update is now reliable for max_rejoin_age, even when a system is offline for an extended period or a failover occurs to another server. |
ENG-53724 | Open Collector/Beats | Open Collector GCP audit logs no longer cause errors in the SCSM.log file when using the JSON SMA parser. |
ENG-53728 | SysMon | The AIX SMA now is shipped with updated C++ runtime libs. |
ENG-53818 | Agents: Azure EventHub Log Collection | The JSON SMA parser now accepts AppServiceIPSecAuditLogs from OC Eventhubbeat Azure source, enabling full parsing of logs instead of receiving general classification. |
ENG-53829 | Client Console | Customers no longer receive an error when they try to import an AIE rule that contains a list with a high number of use contexts in their filter. |
ENG-53876 | Client Console | Customers can now delete entities without receiving errors. |
ENG-54002 | Agents: Beats Collection | Log collection works as expected without establishing multiple connections to each beat. |
ENG-54219 | True Identity | Fixed Okta login parsing in System Monitor's JSON parser, ensuring that Okta now correctly displays system logs with the user's display name or secondary ID (email). |
ENG-54464 | Agents: Azure EventHub Log Collection | Added sname parsing to Open Collector Azure Defender ATP logs to the JSON parser in System Monitor. |
ENG-54504 | Agents: Azure EventHub Log Collection | Login parsing does not convert identity to userPrincipalName. This has been changed to UserPrincipalName to be consistent with the rest of EventHub policy. |
ENG-54511 | Client Console | Customers can now view the Deployment Monitor window without encountering any errors. |
ENG-54747 | Documentation | The API Documentation has been updated with improvements. |
ENG-54806 | Search API | The Search API no longer generates an error when the ClientID is blank. |
ENG-55463 | Web Console | For deployments with a large number of entities, when searching or filtering for entities, all entities are now displayed in results. |
ENG-55616 | Data Indexer: Transporter | Adding truncation to the following new fields in 7.16 Release to prevent errors in the transporter: Reason, Session, ObjectName, Hash, VendorInfo, ParentProcessPath. Any content exceeding 32766 length will be truncated. |
ENG-55625 | Agents | Missing agent information in the mediator agent configuration cache no longer prevents connections to other agents. |
ENG-55897 | SysMon | Now, the agent can start collecting again the logs that were being collected before restarting/stopping the service. |
ENG-56251 | Web Console | For deployments with a large number of entities, when searching or filtering for entities, all entities are now displayed in results. |
ENG-56286 | Client Console | Customers can now delete entities without receiving errors. |
ENG-56764 | Documentation | Fixed links in API - Office 365 Management Activity Device Configuration Guide. |
Resolved Issues - Security
Security-related issues resolved with this release are available for customers to view in the Community.
Known Issues
The following issues have each been found and reported by multiple users.
Bug # | Found In Version | Components | Description | Release Notes |
|---|---|---|---|---|
ENG-43218 | N/A | Alarm API | When using the XSOAR integration with Alarm API, requests periodically return a 500 internal server error. | Expected Results: The integration should work without returning an error. Workaround: Retry the request until it succeeds. |
ENG-38849 | N/A | Knowledge Base | When parsing logs associated with Syslog Linux Host, the Mediator returns the following error message: “Regex rule match timed out.” | Expected Results: The regex rule should parse successfully without timing out. Workaround: There is currently no workaround for this issue. |
ENG-38594 | 7.11 | SmartResponse Plugins | When SmartResponse Plugin scripts are modified but not triggered for 7 days, the custom changes are deleted and the SRP reverts to default settings. | Expected Results: When SRP scripts are modified, the changes should be retained. Workaround: There is currently no workaround for this issue. |
ENG-41651 | 7.12 7.13 | Web Console | After upgrading to 7.12 or 7.13, the CAC authorization used to log in to the Web Console stops working. | Expected Results: The CAC authorization should work when logging in to the Web Console. Workaround: There is currently no workaround for this issue. |