Public Key Infrastructure (PKI) Support
LogRhythm is Public Key Enabled (PKE) and supports Public Key Infrastructures (PKI). The application supports Common Access Cards (CAC) so users can log in to the LogRhythm Client Console using CAC windows credentials and run the LogRhythm services using CAC certificates for client/server TLS communications.
LogRhythm Component Mutual TLS Authentication
LogRhythm services can operate in several modes that allow for increasing levels of security. By default, the SIEM server services (for example, Mediator Server, AIE Communications Manager, SQL Server) use a self-generated server certificate to authenticate themselves to the client components that connect to them — System Monitors, AIE Data Providers, SQL Server clients). By default, the client components do not provide a client certificate to the servers – they are unauthenticated (one-way authentication). A better authentication method employs user-provided server certificates for these server services. The best authentication method employs user-provided server certificates AND user-provided client certificates for the client services — mutual authentication.
SIEM Component Default Behavior
Server services (LogRhythm and Microsoft SQL Server) use self-generated, self-signed server certificates:
- The Mediator service generates a self-signed server certificate at process start-up and uses that to establish TLS connections with System Monitor Agents. The key size depends on the value set for MinAgentSocketSecurity in the Data Processor Advanced Properties:
- 2048-bit key, if MinAgentSocketSecurity is set to TLS 1.2
- 1024-bit key, if MinAgentSocketSecurity is set to TLS 1.0
- The AIE Communication Manager service generates a self-signed server certificate at start-up and uses that to establish TLS connections with AIE Data Providers.
- The Web UI Server service generates a self-signed server certificate at start-up and uses that to establish TLS connections with web clients.
- The Common bundle generates a self-signed sever certificate at start-up for TLS connections with LR components.
- The SQL Server service generates a self-signed server certificate at process start-up and uses that to establish TLS connections with the LogRhythm components.
Client services (System Monitor, AIE Data Provider, SQL Server clients) do NOT present a client certificate when connecting to the server services.
User Certificate-based Mutual Authentication
- Support for user-specified TLS certificates for Windows/UNIX System Monitor Agent (client) and Mediator (server) communications (one- and two-way authentication).
- Support for user-specified TLS certificates for AIE Data Provider (client, in the Mediator) and AIE Communication Manager (server) communications (one- and two-way authentication).
- Support for user-specified TLS certificates for the Web UI Server (server, nginx) and web clients (browsers).
- Support for user-specified TLS certificates for the Data Indexer server.
- Support for user-specified TLS certificates for SQL Server (server). This certificate is used to authenticate and encrypt communications between SQL Server and the LogRhythm components: Client and Web Consoles, Mediator, ARM, Job Manager, and AIE Engine. Note that SQL Server does not support client certificates (one-way authentication only).
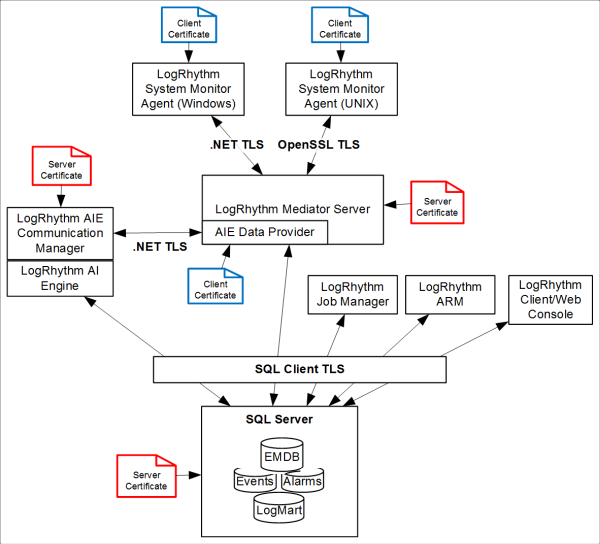
Red certificates are server certificates and blue certificates are client certificates.
Certificate Deployment Options for SIEM Service TLS Communications
| Software Component | Client/Server | No Certificate | Self-Generated Certificate | User Certificate |
|---|---|---|---|---|
| System Monitor Agent | Client | X | X | |
| Mediator Server | Server | X | X | |
| AI Engine Data Provider | Client | X | X | |
| AI Engine Communication Manager | Server | X | X | |
| SQL Server | Server | X | X | |
| Data Indexer Server | Server | X | X | |
| TrueIdentity Sync Client | Server/Client | X (Client) | X (server) |
The certificates need to use the same name as the default certificates.
