Office 365 Management Activity API Collection
This document explains how to configure the collection from O365 management activity using the Web Console's cloud-to-cloud functionality. This feature is available only to LRCloud customers.
Prerequisites
Before configuring the collection from O365, do the following:
- Check if O365 is configured to send logs via Rest API (for more information, see Configure Office 365 Management Activity).
- Make sure that the customer is an LRCloud customer and has their environment hosted.
- Ensure that you have the required values for O365 Management Activity: Client Secret and Tenant Domain.
Initialize the Logs Source
- Log in to the Web Console as a Restricted Administrator User.
- On the top navigation bar, click the Administration icon and select Cloud Log Collection.
- At the top of the Cloud Log Collection page, click New Log Source.
The New cloud log collection dialog box appears. - Select the Office 365 Management Activity SYSMON AGENT tile.
The Add Office 365 Log Source window appears.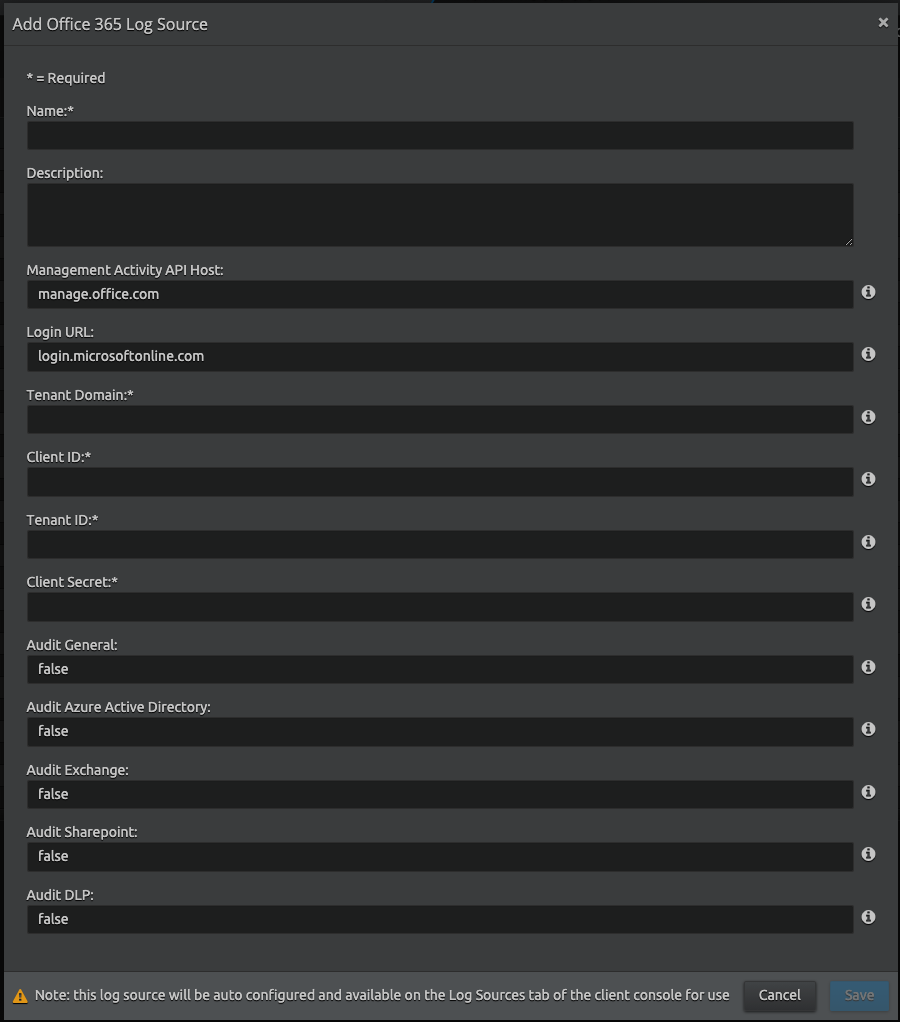
Enter the following details:
Setting Default Value Description Name Not Applicable Enter the name for this log source. Description (Optional) Not Applicable Enter a description for this log source. Management Activity API Host (Enterprise plan)
Host name of the Management Activity API. The default value is for Enterprise customers. The following table indicates values for government plans:
Government Plan Value GCC government manage-gcc.office.com GCC high government manage.office365.us DoD government manage.protection.apps.mil Login URL login.microsoftonline.com Enter the value based on your plan. Following are example values:
Plan Value Enterprise https://login.microsoftonline.com GCC high government https://login.microsoftonline.us Tenant Domain Not Applicable Specify your domain in the following format:
<YOUR_DOMAIN>.onmicrosoft.com
Client ID or Application ID Not Applicable Enter the Client ID (alternatively known as the Application ID). You can obtain the ClientID from the Azure AD portal. This can be found in your App Registration > Overview screen (for example, a0b2345c-1aa2-ab1c-ab34-abc12345acbe).
Tenant ID or Directory ID Not Applicable Enter the Tenant ID (alternatively known as the Directory ID). You can obtain the TenantID from the Azure AD portal. This can be found in your App Registration > Overview screen (for example, a0b2345c-1aa2-ab1c-ab34-abc12345acbe).
Client Secret Not Applicable Enter the client secret value that is generated from the Azure AD portal (for example, a0b2345c-1aa2-ab1c-ab34-abc12345a). For instructions on generating your client secret, see REST API - Obtaining your Client Secret. Audit General false Enable auditing of General events. Option of false or true. Audit Azure Active Directory false Enable auditing of Azure Active Directory Management events. Option of false or true. Audit Exchange false Enable auditing of Exchange Management events. Option of false or true. Audit Sharepoint false Enable auditing of Sharepoint events. Option of false or true. Audit DLP false Enable auditing of General events. Option of false or true. - Click Save.
- Click the System Monitors tab.
- Select the Action check box corresponding to the (customerid)-dpawc agent.
- Right-click the selection, click Actions and then click Service Restart.
A new active log source is created and accepted in the Client Console with the provided information. Collection should start automatically in few minutes.
The Platform Manager hosts all the log sources. It is recommended to create a new host entity and move the log source to the new host, which is done in the log source properties screen and not from the log source grid.
For security, the values entered are encrypted using LRCrypt.
Default Config Values for O365 Management Activity
| Setting | Default Value |
|---|---|
| Timeout | 300 |
| LogApiRequests | false |
| MaxBatchSize | 10 |
| StopCountFetchNewContentIds | 1000 |
| StopCountCacheFiles | 50 |
| NumOfBackMinutesData | 15 |
| CollectionDelay | 1 |
Recommendations
Create a Separate Log Source for each Office 365 Event Stream
The Office 365 Management Activity Log Source consists of multiple event streams from within the Office 365 environment. It is recommended to split these streams into separate log sources. This enables ease of analytics and increases log source throughput efficiency.
To create separate log sources, do the following:
- Create a different cloud-to-cloud configuration in the Web Console for each events stream within Office 365.
- In each configuration file, select one of the events streams to be true and all other events streams to be false. The possible events streams you can enable are:
- AuditAzureActiveDirectory
- AuditExchange
- AuditSharepoint
- DLPEvents
- AuditGeneral
Name each log source to correspond to the events stream you selected to be true in that configuration.
Example
Events stream: AuditAzureActiveDirectory
Configuration file settings:
- AuditAzureActiveDirectory=true
- AuditExchange=false
- AuditSharepoint=false
- DLPEvents=false
- AuditGeneral=false
Repeat this process to enable all the remaining events streams.
The log source type for all the events streams will be API - Office 365 Management Activity.

