CCF Deployment Guide – Configure the Compliance Module
LogRhythm requires you to configure some objects included in the CCF Compliance Automation Suite. This section describes the steps you must perform.
- Population of Lists
- Activation and Configuration of AIE Rules & Alarms
Populate Log Source Lists
Follow the instructions below to populate the Log Source List.
- Open the LogRhythm Console and click List Manager on the main toolbar.
- Right-click the list name of a CCF Log Source Lists, and then click Properties.
- To view the log sources selector, click Add Item.
- Search for and select all log sources that you want, and then click OK.
- To save the list, click OK.
- Repeat this process (steps 1-5) for all CCF Log Source Lists.
Populate Hosts Lists
Follow the instructions below to populate Hosts Lists with existing hosts via entity.
- Open the LogRhythm Console and click List Manager on the main toolbar.
- Right-click the list name for a CCF framework-specific Host List, and then click Properties.
- Select the Hostname for the Item Type.
- Select the Add Item field.
- Select the entity name in the Entity Filter to add the hosts within.
- Repeat steps 4-5 for all hosts in separate entities that you want.
- To save the list, click OK.
- Repeat this process (steps 1-7) for all CCF framework specific Host Lists.
Follow the instructions below to populate Hosts Lists with existing hosts via import.
- Open the LogRhythm Console and click List Manager on the main toolbar.
- Right-click the list name for a CCF framework specific Host List, and then click Properties.
- Select the Hostname for the Item Type.
- Select the Import Items… field.
- Select the Import Text File… or Import Clipboard Text depending on your preferred file format.
- Select the file containing the host names to be added to the list and select Open.
- To save the list, click OK.
- Repeat this process (steps 1-7) for all CCF framework specific Host Lists.
Populate Users Lists
Follow the instructions below to populate User Lists.
- Open the LogRhythm Console and click List Manager on the main toolbar.
- Right-click the list name for a CCF Users List, and then click Properties.
- Select the Username for the Item Type.
- Type in the username in the Add Item field.
- Click the Add Item button to add the username.
- Repeat steps 4-5 for all usernames that you want.
- To save the list, click OK.
- Repeat this process (steps 1-7) for all CCF Users Lists.
Active Directory Sync – User Access Management
CCF: User lists can align with periodic reviews of access (User Access Management) and can be integrated with Active Directory Sync (AD Sync) functions. For further discussion of this functionality and other use cases around AD Sync, see the LogRhythm Community. User and group definitions within your Active Directory can be easily reflected and synchronized to ensure the structure is with your SIEM lists.
Populate Location Lists
Follow the instructions below to populate Network Lists.
- Open the LogRhythm Console and click List Manager on the main toolbar.
- Right-click on the list name for a CCF Location List, and then click Properties.
- Select the List Item and Add Item.
- Determine the level of location setting: Country or Region recommended.
- Type in the Country or Region Name in the Location Selector screen.
- To save the list, click OK.
- Repeat steps 4-5 to for all locations that you want.
- To save the list, click OK.
- Repeat this process (steps 1-7) for all CCF Location Lists.
Create Restricted User Profiles
Follow the instructions below to create Restricted User Profiles. This is a critical step to implement with the CCF module deployment.
- Open the LogRhythm Console and click Deployment Manager on the main toolbar.
- On the Tools menu, click Administration, and then User Profile Manager.
- To create a new user profile, click New.
There are various configuration options, but note that there are options for Restricted User and Restricted Admin, as well as tabs for applying restrictions for Entities and Log Source Access Rights. - Either apply restrictions to the User Profile based on CCF-focused Entity structures for a lower maintenance deployment or apply the CCF: All Log Sources list to be more granular with the configuration of the CCF scope.
- To apply a restricted User Profile, return to the Deployment Manager and select the People tab.
- Create a new user account or update an existing account with the new profile by right-clicking the profile and then clicking User Account Properties.
The User Profile drop-down selection includes any new profiles created. - To apply a new profile to the user account immediately, click Apply or OK.
The drop-down option is greyed out if the user is logged into the account he or she is attempting to modify.
Validate Ingested Log Data and Apply Data Masking Rules
Previous sections in this guide discussed the use of restricted profiles to limit who can see certain log data based on defined compliance scope through Entity & Log Sources. However, data protection within the SIEM can be taken a step further. Consider adjusting MPE Rules and Data Masking Rules to fine-tune logs ingested into the SIEM.
Most control objectives supported through SIEM can be executed without ingesting log data containing sensitive information. It is important to understand whether sensitive personal information (for example, social security numbers) and in the case of CCF, Controlled Unclassified Information (CUI), is being ingested by the SIEM. To manage the scope expansion of control assignment within the SIEM, LogRhythm offers Data Masking rules that look for sensitive information within log data and scrub data from the logs before entering LogRhythm SIEM.
As part of the CCF requirements for Data Classification activities, this effort should be translated into the SIEM to ensure sensitive data is not unnecessarily ingested into the SIEM. In addition, risk classifications can be adjusted at the entity and log source level to prioritize at-risk environments, such as those storing CUI.
Data masking rules can be established in the LogRhythm Consoles as shown below. For additional instructions on establishing data masking rules, please refer to the Data Masking section of the LogRhythm SIEM Help, available under Documentation & Downloads on the LogRhythm Community.
Add New Data Masking Rules
New Data Masking Rules can be created, but rules can be imported or exported as well. For more information on Importing and Exporting Data Masking Rules, search the LogRhythm Community.
You must be logged in as a Global Administrator to add new Data Masking Rules.
- On the main toolbar, click Deployment Manager.
- On the Tools menu, click Administration, and then click Data Masking Rule Manager.
The Data Masking Rule Manager appears. - On the menu bar, click New (the green plus icon).
The Data Masking Rule Properties window appears. - Enter a Name.
- Enter a Description.
- Select the Scope.
- If the rule applies to all Message Source Types, select Global.
- If the rule applies to a specific Message Source Type, click the Browse button and select the applicable Message Source Type.
- To enable the rule, select the Enable Data Masking Rule check box.
- Type the match regex.
If left blank, the transformation find/replace pairs are applied to all logs in the specified scope.
- Add a find/replace pair.
- Click Add New.
The Find/Replace Properties window appears. - In the Find Regex box, type the expression you want to transform.
- In the Replacement String box, enter text you want to replace the expression with.
Enter <hash_string> to generate a consistent hash where the same input value always results in the same output value. If blank, the matching text is replaced by a blank message. - Click OK.
- (Optional) Add additional pairs.
- Click Add New.
- If necessary, use the Up and Down arrows to reorder the Find/Replace pairs. The transformations are applied in the order listed.
- Type a Log Sample. When text is entered into the Log Sample text box, the Test button is enabled.
- Click Test to validate the regex. The Match Regex and Find/Replace pairs are run against the Log Sample. A result dialogue box appears and indicates either:
- Match Regex Success
The Match Regex matched the log sample. - Match Regex Failure
- Match Regex Success
Activate and Configure AIE Rules
All AIE Rules included in the CCF Compliance Automation Suite are disabled by default.
To enable the CCF AIE Rules
- Open the LogRhythm Console and click Deployment Manager on the main toolbar.
- Click the AI Engine tab.
- Select all the CCF AIE rules.
- Right-click the AI Engine Rule Manager, click Actions, and then click Enable.
All alarming AIE Rules included in the CCF Compliance Automation Suite have alarmingly disabled by default.
To enable alarming on the alarming AIE Rules
- Open the LogRhythm Console and click Deployment Manager on the main toolbar.
- Click the AI Engine tab.
- Select all the CCF AIE Rules that are configured to alarm (see Table 13: AIE Rules and Alarms).
- Right-click the AI Engine Rule Manager, click Actions, click Batch Enable Alarms, and then click Enable Alarms.
All alarming AIE Rules included in the CCF Compliance Automation Suite must be configured for notifications.
To configure notifications on the alarming AIE Rules
- Open the LogRhythm Console and click Deployment Manager on the main toolbar.
- Click the AI Engine tab.
- Select each of the CCF: AIE Rules that are configured to alarm and notify (see Table 13: AIE Rules and Alarms).
- Right-click the AI Engine Rule Manager, click Actions, and then click Batch Notification Editor.
- Select all the roles, individuals, or groups to be notified, and then click OK to save the notifications.
- Repeat Steps 2-5 for all alarming CCF AIE Rules that share notification personnel.
- At the top of the AI Engine Rule Manager, click Restart AIE Engine Servers.
Use LogRhythm Network Monitor for TLS/SSL Auditing
LogRhythm Network Monitor is capable of translating TLS and SSL traffic for review and analysis. With CCF having control requirements for security by design and default, there are AIE rules, investigations and reports designed to augment the support of these articles. The Network Monitor sends data to LogRhythm via Syslog, which can be reviewed and is utilized with the automation suite’s evaluation objects.
AIE's activity threshold rules capture bundles of general TLS/SSL activity logs within the drill down of their AIE events. These activity rules are oriented toward pairing these drill-downs with dashboards to make the collection of TLS/SSL Case Management evidence easier. Since CCF no longer allows new implementations of TLS/SSL under most circumstances (as of October 31, 2016), the Potential New TLS/SSL Implementation rule is designed to flag activity on systems that have not been running TLS/SSL (the default evaluation period for this is set for two weeks, since systems running TLS/SSL are going to otherwise show that level of activity regularly). Another alarm is structured to flag early TLS or SSL if they show up in the environment.
AIE Rules | Notification Area | Corresponding Investigation |
|---|---|---|
CCF: Early TLS/SSL Alarm | Security: Activity | N/A |
As for the Investigation, it is configured to generate an overview of all TLS/SSL activity. Because there are AIE rules that can be used as Investigations for drill-downs, granular searches are more easily done with AIE drill-downs than with Investigations.
Since this rule requires LogRhythm’s Network Monitor to send TLS and SSL activity to the SIEM, a paid Network Monitor license is needed with syslog configured to be received by a LogRhythm System Monitor Agent. Professional Services and Support Services can assist with advanced configurations; otherwise, see the Network Monitor configuration guides under Documentation & Downloads on the LogRhythm Community.
The SIEM reflects TLS and SSL-relevant data under the “Version” metadata field. The ProtocolVersion metadata field on the Network Monitor side is where it can be determined whether TLS or SSL activity is showing up directly on LogRhythm’s Network Monitor, as well. The graphic below shows what to expect when trying to verify if TLS or SSL data is showing up on the SIEM.
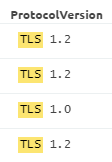
When looking over an entire packet, this activity shows up as seen in the following graphic:
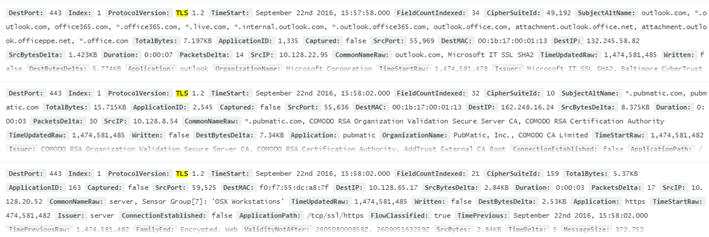
Direct Network Monitor searches can be performed under “ProtocolVersion” as well.
As noted earlier, after this data is sent to LogRhythm’s SIEM via Syslog, TLS and SSL activity is reflected under the Version metadata field. This data is utilized by the TLS and SSL-specific rule within the CCF Compliance Automation Suite. For more information on using the LogRhythm Network Monitor, there are various guides that can be used for reference, including but not limited to documents and videos on its capabilities uses and features. This content is available under Documentation & Downloads on the LogRhythm Community.
LogRhythm Advanced Capabilities
Use of LogRhythm Network Monitor
Network Monitor is a key aspect of LogRhythm to help mature the organization into a stronger security position. Rich context can be added to log data including the use of GeoLocation, deep packet inspection, and so much more. Our modules are designed to incorporate more enhanced tools within LogRhythm SIEM, thus providing a roadmap to bridge the gap between compliance and security objectives. For more information, see the Network Monitor information on the LogRhythm Community.
Use of LogRhythm Data Loss Defender
As CCF and many other compliance frameworks require monitoring of devices connected to the network, specifically USBs, LogRhythm’s Data Loss Defender (DLD) can be easily configured to facilitate this level of monitoring. This feature of the Windows System Monitor Agent independently monitors and logs the connection and disconnection of external data devices to the host computer where the Agent is running. It also monitors and logs the transmission of files to an external storage device. Further configuration may also help protect against external device connections by ejecting specified devices upon detection.
For DLD to work, you must configure the DLD Policy Properties and System Monitor Agent DLD Properties according to your needs. These settings can be found by clicking Deployment Manager on the main toolbar, the Tools menu, and then Administration. New monitoring policies can be established, or existing policies can be edited.
The following objects have been included within the CCF Compliance Automation Suite to leverage the LogRhythm DLD policies:
AIE Rules | Notification Area | Corresponding Investigation |
|---|---|---|
CCF: Data Loss Prevention | Operations: Information | CCF: LogRhythm Data Loss Defender Log Inv |
Summary Report | Report Class | Description |
|---|---|---|
CCF: LogRhythm Data Loss Defender Log Summary | Operations | This report provides summary information on data generated by the LogRhythm Data Loss Defender. Data is grouped by Entity, Impacted Host, Common Event, and Object with a count of how many times that condition has been experienced within the reporting period. |
Use of LogRhythm True Identity
User access management, including access provisioning and account activity, are crucial to any compliance program. LogRhythm offers a road map within SIEM to utilize additional features which provide powerful context to log data within this scope. Content within the CCF Compliance Automation Suite will initially point to criteria of User Origin & Impacted but can be adjusted after True Identity has been established and synced with your AD through existing application programming interfaces (APIs).
TrueIdentity is useful because the solution lets you add multiple identifiers to a single user’s identity. As the organization matures the overall UAM, including account classification and determining associated accounts to a given user, TrueIdentity can be leveraged as a powerful tool to supplement UAM objectives. This solution help adds significant context to user activity within in-scope environments. All this information can be built out in LogRhythm’s TrueIdentity, as shown in the example below:
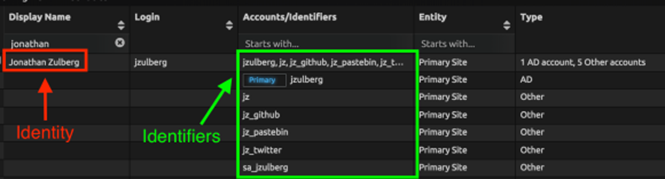
Use of LogRhythm Honeypot Integration Module
Honeypots are directly called out in CCF objectives [SC-26 & SC-35] and are an advanced way to progressively learn and understand attacks against your environment. Honeypots are an often overlooked and undervalued asset to a security team’s arsenal. These decoy systems can be configured to attract and trap anyone who attempts to penetrate a company’s network. By implementing the LogRhythm Honeypot Integration Module (KB Module #42) with your own honeypot system, you can gather incredibly valuable information for your organization. This module works with three of the most common honeypot solutions: Kippo, PhpMyAdmin, and WordPot. For more information, see the Honeypot Module guides available under Documentation & Downloads on the LogRhythm Community.
Use of LogRhythm GeoLocation Settings
With an organization’s increased globalization of information technology or customer interactions, adding geographic context can help enrich log data. As it applies to CCF, this geographic context can be leveraged at the country level to enrich inbound and outbound traffic to identify when data may be entering your environment from a country with strict data security and privacy regulations.
Knowing whether an event within your environment involves one of these countries can facilitate the application of policies around obtaining consent and other time-sensitive, regulatory requirements. Further, enriching data to include geolocation can also assist with preventing unauthorized access or enforcing access control.
To prevent your SIEM from being overwhelmed, it is recommended to set the Geographic IP (GeoIP) location level to Country. This can be established within the GeoIPResolutionMode property in the Data Processor Advanced Properties. If GeoIPResolutionMode is set to None (default), then GeoIP location cannot be resolved for logs or used for Network Visualization. For more information, see the LogRhythm SIEM Help, available under Documentation & Downloads on the LogRhythm Community.
The following objects have been included within the CCF Compliance Automation Suite to leverage the GeoIPResolution setting of Country:
AIE Rules | Notification Area | Corresponding Investigation |
|---|---|---|
CCF: GeoIP Blacklisted Region Activity | Security: Suspicious | CCF: GeoIP Inv |
CCF: GeoIP General Activity | Security: Suspicious | CCF: GeoIP Inv |
Summary Report | Report Class | Description |
|---|---|---|
CCF: GeoIP Summary | Security | This report summarizes GeoIP activity that is associated with AI Engine GeoIP rules, in the CCF compliance automation suite. |
