Configure Sophos Central
This guide outlines the steps required to configure the Sophos Web Console in preparation for starting the Sophos Central Beat.
Generate the Client ID and Client Secret
The following information is required to configure Sophos Central for Beats:
- Client ID
Client Secret
These configuration keys are created in the API Credential Managment section of the Sophos Central web console.
The steps outlined in this guide describe the process to obtain a Client ID and Client Secret, which are needed to configure Sophos Central Beats for version 7.0.0 and later. If you are currently using Sophos Central Beat version 6.0.3 or earlier, upgrade to Sophos Central Beat version 7.0.0 (or later), along with LRCTL version 6.6.0 (or later).
When upgrading to Sophos Central Beat version 7.0.0 or later, ensure all existing instances are closed before launching a new one. Note that versions 7.0.0 and above are not backward compatible with the 6.x.x series.
- Open the Sophos Central web console: https://central.sophos.com/manage/dashboard
- Click on the General Settings icon on top right-hand side and then click on API Credentials Management.
- On the API Credential Management Page, click Add Credential.
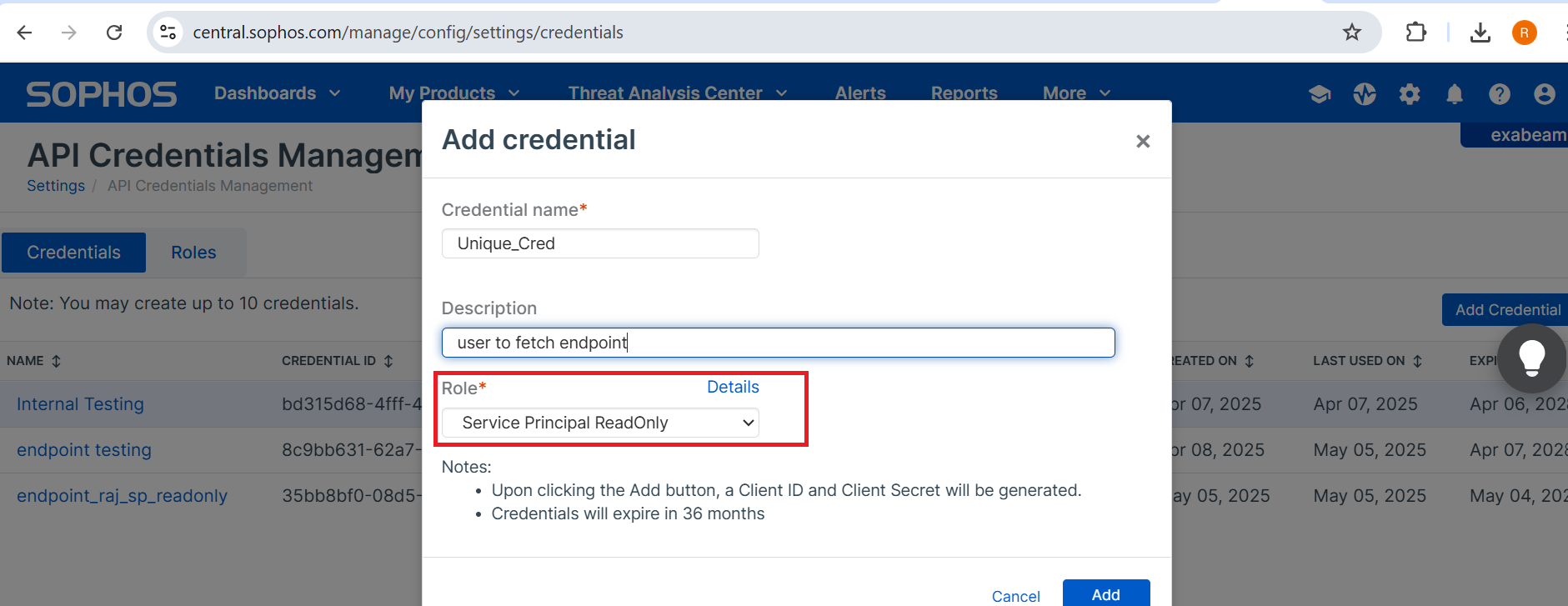
- Enter a unique Credential name, and an optional description.
- From the Role drop-list, select Service Principal ReadOnly.

- Click Add.
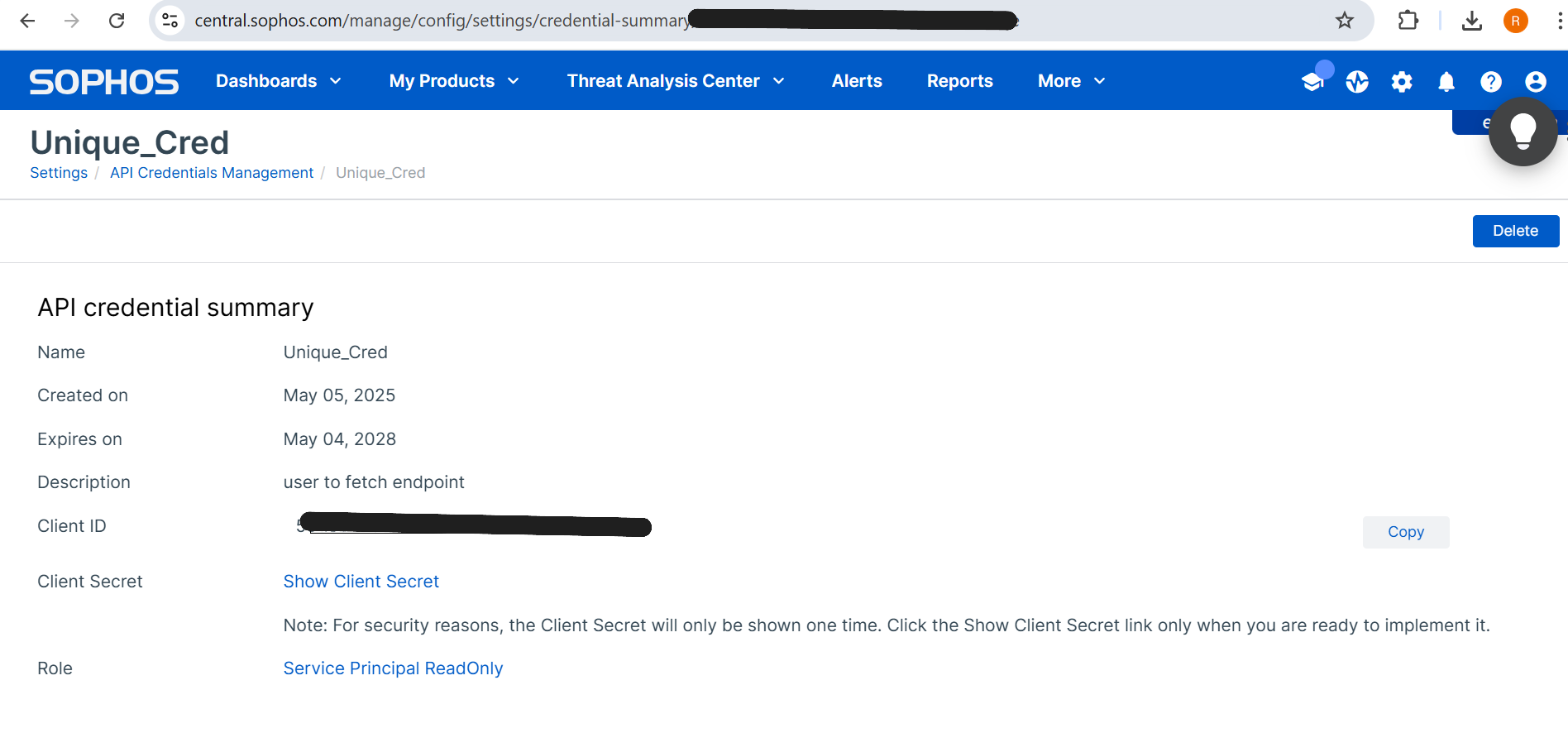
The Client ID and Client Secret are displayed. Copy the Client ID and Client Secret to a secure location.
These credentials will not be viewable again, so ensure they are copied at this time.
The Client Secret is hidden by default; click Show Client Secret to display it.
Configure a System on Sophos Central
The following installation takes 10–15 minutes.
- From the Sophos web console, in the menu on the left, select Protect Devices.
- In the center pane, click Choose Components.
The Component Installation Options dialog box appears. - From the list of products provided, select the products you want your installer to register for, and then click Download Installer.
After the installer is downloaded, double click the executable to install Sophos Central on your machine.
In some cases, you will be prompted to restart your system. Installation resumes automatically after your system restarts.- To verify the installation and registration in Sophos Central, from the menu on the left, select Endpoint Protection.
- Select the name of the product installer you downloaded, and from the menu on the left, select Computers.
The list of systems registered appears.
Generate Logs
Logs are generated when a user visits a malicious link.
A Sophos Alert notification appears on screen, blocks access to the link, and generates a log in Sophos Central.
View and Export Logs
To view and export logs from the Sophos web console:
- In the menu on the left, select Endpoint Protection, and then select Computers.
The list of registered systems appears in the center pane. - Select the system you want.
- On the Summary Tab, click View More.
- To view a detailed list of logs, click View Events Report.
A list of logs for the selected system appears. - Use the filters at the top of the center pane to configure the log set for export.
- To Export logs, on the bottom of the screen on the right, click Export.
- Select the report format, and the logs export begins.
