Carbon Black Cloud Beat
Version 6.0.8
The Carbon Black Cloud Beat currently supports log collection via the Alerts API only (i.e. CB Analytics alerts and Watchlists alerts).
Alerts API
VMware Carbon Black Cloud extends the capabilities of the Alerts API by improving the methods of retrieving alerts, and adds functionality to manage the workflow by updating the alert status. This allows you to more efficiently call an API by providing a wider range of filterable fields, including creation time, category, type, status, tag and more, as well as the ability to dismiss alerts.
Carbon Black Beat supports log collection through the Alerts API:
- CB Analytics Alert - CB Analytic alerts are created from the Endpoint Standard NGAV offering. Log in JSON Format.
- Watchlist Alert - Watchlist alerts are created from alert enabled watchlists in Enterprise EDR.
- Device Control Alert - Device Control alerts are created when an endpoint attempts to access a blocked USB device.
Devices API
VMware Carbon Black Cloud extends the capabilities of the Devices API by improving the methods of retrieving device information and adds functionality to perform actions. This allows you to more efficiently call an API by providing a wider range of filterable fields, including policy ID, status, operating system and more. You can also perform actions on individual devices such as quarantine/unquarantined, enable or disable bypass, or upgrade to a new sensor version.
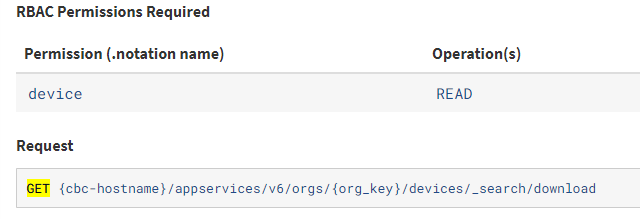
Export Devices (CSV)
Enriched Events Search API
The Enriched Events Search API lets you search through all data reported by your organization’s Endpoint Standard-enabled sensors to find one or more specific enriched events that match your search criteria.
You can:
- See tactics, techniques and procedures (TTPs) and the MITRE CVEs associated with potentially malicious activity.
- Get visibility into the cyber kill chain stage at which attacks were stopped.
- Identify the family and name of malware observed and stopped on your organization’s endpoints.
Requirements:
- Endpoint Standard product.
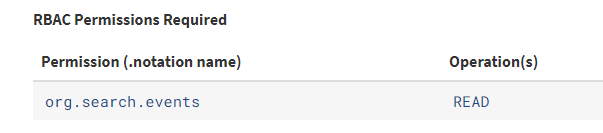
- The org.search.events CREATE permission is required to create a search.
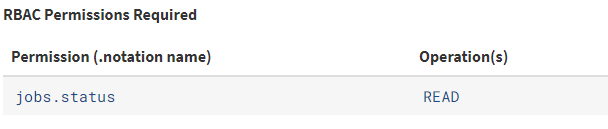
Job Service API
The Job Service API tracks the execution of long running tasks, making it easier to monitor the progress of asynchronous jobs. The API retrieve the jobs’ output once completed, and prevents important tasks from timing out mid execution. It can be used with other APIs, such as the Live Query REST API - Get Query Run Results, to asynchronously export large amounts of data.
Features of this API:
- Long running or slow jobs tracked through the jobs service will complete without timing out.
- Downloads can be repeated without having to run the underlying job multiple times.
- Jobs can only be seen by the connector or user who created them.
- Jobs are saved for 30 days.
Processes Search API
The Processes Search API lets you search through all the data that is reported by your organization’s sensors to find one or more processes based on specific criteria you set.
With visibility across your fleet of monitored endpoints, you can identify applications that are acting abnormally and, over time, cull the outliers from the total observed process activity, and retroactively identify the origination point for attacks that previously escaped notice.
You can:
- Test out a variety of approaches to querying your organization’s historical data before adding that query to a Watchlist.
- Get deep visibility into the security context of Windows processes including elevation, mandatory access control integrity level, and privileges.
- Search across all Enterprise EDR Watchlist-hitting activity in your organization, to hone in on patterns and outlier behavior.
Requirements:
- Endpoint Standard or Enterprise EDR product.
- The org.search.events CREATE permission is required to create a search.
- All API calls require an API key with appropriate permissions (see Authentication below).
API calls
The Processes Search API has three types of calls:
- Calls for Processes - searches process data.
- Calls for Events - searches event data.
- Calls for Enterprise EDR - scans for hits against watchlists and reports.