Understand the LogRhythm Architecture
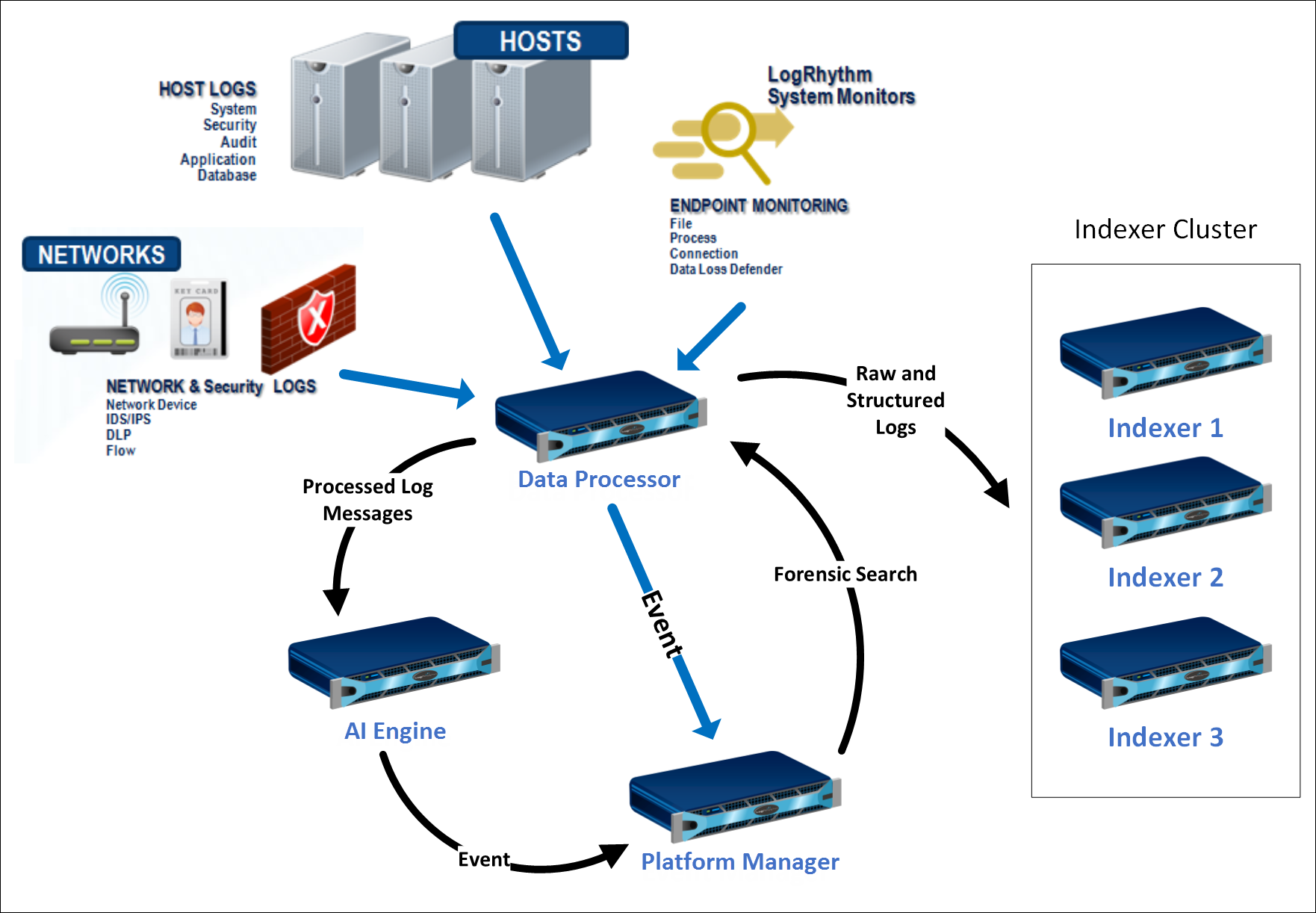
LogRhythm has been designed with a highly flexible modular architecture. Each key LogRhythm function exists in a separate software program, or service.
A multitude of devices are generating thousands of raw logs in your network at every moment. These devices can include servers, firewalls, routers, network services, applications, and email systems. Depending on the device, the logs are generated in a wide variety of formats and can include information related to system health, user interaction with an application, and so on. All of this log data has varying degrees of importance, from mundane activity to a potential security compromise.
LogRhythm SIEM is a fully integrated Security Information and Event Management (SIEM) solution that processes this raw log data to make information available to you in a meaningful and uniform context. The following diagram shows the key LogRhythm components for collecting and processing logs: the Agents, the Data Processor, the AI Engine, and the Platform Manager.
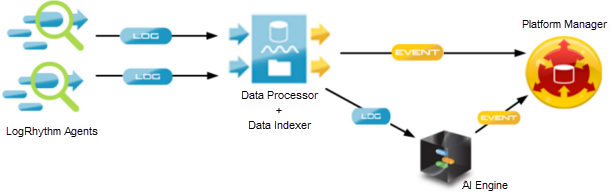
The individual services are installed on hosts to create the overall LogRhythm solution. All LogRhythm services can be installed on a single server providing all LogRhythm capabilities or the services can be installed on separate servers in high performance and redundant configurations.
Changing the default SQL Server Collation from “SQL_Latin1_General_CP1_CI_AS” is not supported and can leave your deployment in a non-working state.
General Guidelines for Deployment Architecture
A minimal deployment of LogRhythm consists of:
- One Platform Manager
- One Data Processor
- One Data Indexer
- One System Monitor
The modular nature of LogRhythm's components allows the Platform Manager, Data Processor, and Data Indexer to reside on the same server for low-volume deployments, or on dedicated servers for high-volume deployments. The following general guidelines apply to any LogRhythm deployment, large or small:
- The Platform Manager and its associated database contain the record of events generated by LogRhythm as well as all the LogRhythm configuration data. It is important that the Platform Manager always be placed in a secure internal network.
- The Platform Manager is a Windows server running SQL Server 2016 Standard SP1 or higher and should be deployed accordingly.
- The Data Processor forwards Agent log data to the Data Indexer. It is the recommended practice to deploy Data Processors and Data Indexers in a secure internal network. However, in some scenarios it may be advisable to place the Data Processor in a DMZ when Agents will be used to collect from Remote Sites.
- The Data Processor is a Windows server. The Data Indexer is a Windows or Linux server, and it should be protected with strict access controls placed on devices that can connect to the log repository if deployed in a DMZ or an untrusted environment.
- Communications to DMZ or remotely deployed Data Processors, from Platform Managers and Consoles, can be encrypted to provide secure log delivery.
- The System Monitor, which collects log data and forwards it to a Data Processor, can:
- be deployed on supported Windows, Linux, or UNIX systems in an internal DMZ or on remote network hosts.
- encrypt collected log data before forwarding it across untrusted networks (for example, the Internet).
- read collected log data before forwarding it across untrusted networks (for example, flat files).
- read local Windows Event Logs (the Windows System Monitor).
- read Windows Event Logs residing on remote systems (the Windows System Monitor).
- have an integrated Syslog server for collection of Syslog data.
- have an integrated NetFlow server (the Windows System Monitor) for collecting NetFlow/J-Flow data from Cisco devices.
- have an integrated sFlow server for collecting Flow data from network devices.
- have an integrated SNMP trap receiver.
- collect the following logs:
- Check Point Firewall logs
- Cisco IDS logs
- Logs residing in database tables
- Qualys, Nessus, and other vulnerability scanners