Configure CustomObjectType in STIX/TAXII Feeds in TIS
For any custom STIX/TAXII (version 1 or 2) provider, the LogRhythm Threat Intelligence Service consumes email addresses, file hashes, and CustomObjectTypes in order to correlate them with log data. Select which fields are consumed by configuring the lrtfsvcconfig.json file. For more information about enabling CustomObjectTypes, see the following example for enabling Cisco CTA.
Enabling Cisco CTA
- Click Add Custom Source and add Cisco CTA on the Add STIX/TAXII Provider tab. For more information on completing the fields, see Add a Custom STIX/TAXII Provider.
- After you save the source, click Start Service on the Threat Intelligence Service Manager main page.
- Select the Cisco CTA provider from the options on the left, and select Enabled.
- Click Download Now.
- After the download completes, click the File menu and then click View Logs.
- Open the lrtfmgr.log and lrtfsvc.log in a text editor (e.g., Notepad), and look for
Provider Cisco CTA contains a CustomObjectType.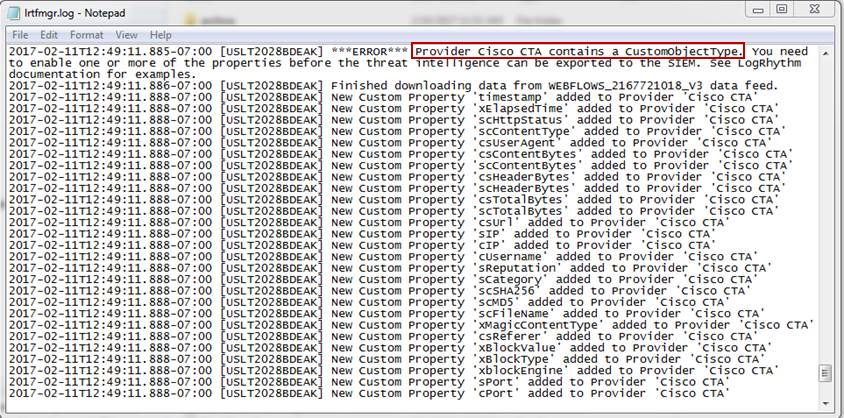
Stop the Threat Intelligence Service, and exit the Threat Intelligence Service Manager.
Open the lrtfsvnconfig.json file in a text editor (e.g., Notepad). The default path is C:\Program Files\LogRhythm\LogRhythm Threat Intelligence Service\config for the lrtfsvnconfig.json file.
Find the Cisco CTA provider you added.
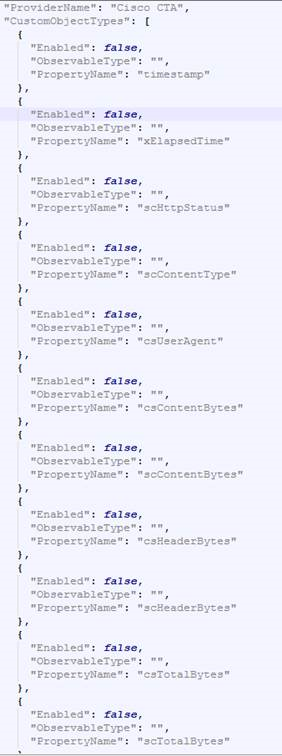
The CustomObjectType field contains the following fields:
- Enabled. Whether or not the field displays in the output. By default, this field is set to false.
- ObservableType. The type of field (Currently supported: URL, Domain, IP, FileHash, FilePath).
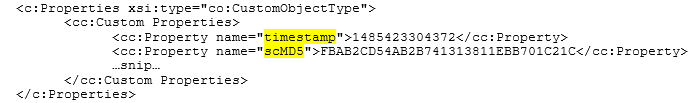
- PropertyName. The Name attribute of the field from the Provider (e.g., scMD5).
- The following are the recommended settings for Cisco CTA:
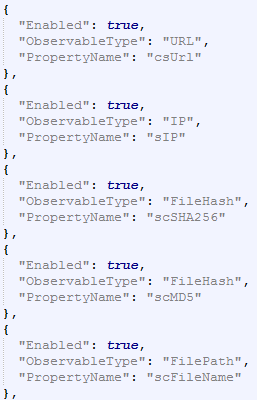
- Save the lrtfsvcconfig.json file.
- Open the Threat Intelligence Service Manager and Start the service.
Click Download Now for the Cisco CTA provider.
Cisco CTA only allows one download every 10 minutes.
