Collect Non-Domain Logs Remotely
You can configure system monitors and remote hosts for remote log collection without the use of a domain account. This method of log collection is generally used when there is a remote host where log collection is required that is either on a separate domain or is a member of a workgroup. While its simpler to deploy a local agent on the non-domain host to perform log collection locally and forward logs to a data processor that may not be possible in some cases. The following process is a suitable alternative to that configuration and uses reliable RPC-based windows protocols for authentication and log collection.
Prerequisites
- These standard Windows RPC ports must be open between the monitoring system and the remote system:
- TCP 135
TCP 445
The default Dynamic Port Range is 49152–65535. These ports also need to be allowed on the remote machine. The Remote Event Log Management (RPC) Windows Firewall rule enables this dynamic range. It is not necessary to have all ports within this range open. Use your firewall to check which ports are being used.
- These port settings are valid for Windows Vista and later, as well as Windows Server 2008 and later.
The remote system must be running the RPC and Remote Registry services.
To enable these services on the remote machine, go to Control Panel, click Administrative Tools, and then click Services. Start the Remote Procedure Call (RPC) and Remote Registry services. Set the Startup Type for both to Automatic.- A valid network route (path) must exist between the monitoring system and the remote system.
- A service account with Administrative permissions or a member of the local "EventLogReaders" default group must be configured on the system that is to be collected
Setup
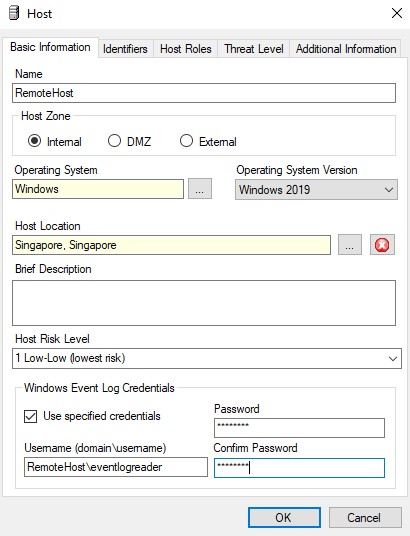
When configuring remote log collection with a non-domain or different-domain account from which the LogRhythm agent is running, you should specify the credentials in the LogRhythm console. When Entity Host credentials are configured in the LogRhythm Console, these will overwrite the account that the agent uses to perform remote log collection such that it will not use the account the agent is running under, but instead use the account configured for the specific entity host you want to collect logs from.
- Create a new account on each remote host which will be the target for remote Windows log collection.
- Add this new service account to the local system Administrators or Event Log Readers groups to allow remote Windows Event log collection.
- Open the LogRhythm Console, Deployment Manager, Entity tab and open the entity where your remote Windows log collection host needs to exist.
- If not already created, create a new entity host record for the host which needs to be collected:
- Select Windows for Operating System.
- Select the correct Operating System Version.
- Add at minimum an Identifier for Windows Name.
- Save the Entity Host record.
- Re-Open the Entity Host:
- Configure the Windows Event Log credentials.
- Valid formats for the Username include:
- hostname\username (if machine is non-domain this will use a local account)
- .\username
- domain\username (if machine is on a domain which is not part of a trust with the domain the LogRhythm Agent is running as)
- Configure the Log Sources for collection as per normal from the Log Sources tab in Deployment Manager.
