Create Client and Server Certificates
This topic provides information about creating client and server certificates. Please note the following:
- For SQL Server server certificates, the Subject name must be the FQDN of the host machine — IP addresses are not allowed.
- For LogRhythm client and server certificates, the Subject name can be the FQDN of the host machine or its IP address.
- Be sure to put a ‘CN=’ before the FQDN or IP address of the Subject for all certificates (SQL Server and LogRhythm client/server).
- Ensure there are no spaces surrounding or in between the ‘CN’ and ‘=’ and the Subject (FQDN/IP).
- Ensure that the client and server certificates have their signing certificate — the Root CA of the certificate — in the Trusted Root Certification Authorities store.
If the LogRhythm TrueIdentity Sync Client is on a remote host, you must generate and trust custom or self-signed certificates on the PM before continuing with configuration.
If you are using the self-signed certificates located in C:\Program Files\LogRhythm\LogRhythm Common\LogRhythm API Gateway\tls, follow instructions to trust the certificates. Note that it is recommended you create custom certificates.
The instructions below are examples using openSSL to create certifications in a Windows command prompt.
- Log onto the machine where your LogRhythm Platform Manager is installed.
Go to C:\Program Files\LogRhythm\LogRhythm Infrastructure Installer\ssl, and copy the openssl.cfg to this directory.
The openssl.cfg can be found here openssl.cfg.
- Open a command prompt from this location and complete the following:
To create CSR, run
CODEopenssl req -out CSR.csr -new -newkey rsa:2048 -nodes -sha256 -keyout privateKey.key -config openssl.cfgTo create a public certificate from CSR and a private certificate, run
CODEopenssl x509 -req -days 365 -in CSR.csr -signkey privateKey.key -out LogRhythmSSL.crt -extensions extended -extfile openssl.cfgTo create PFX from the public and private certificates, run
CODEopenssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in LogRhythmSSL.crtTo export the two certificates from PFX, run
CODEopenssl pkcs12 -in <certname>.pfx -nocerts -out privateKey.key -nodes openssl pkcs12 -in <certname>.pfx -nokeys -out LogRhythmSSL.crtTo remove the passphrase from the private key, run
CODEopenssl rsa -in privateKey.key -out LogRhythmSSL.pemTo convert p7b format to the certificate, run
CODEopenssl pkcs7 -inform (DER|PEM) -print_certs –in <pkcs7_certname>.p7b -out LogRhythmSSL.crtRun the following to ensure all MD5 checksums match
CODEopenssl rsa -noout -modulus -in privateKey.key | openssl md5 openssl x509 -noout -modulus -in LogRhythmSSL.crt | openssl md5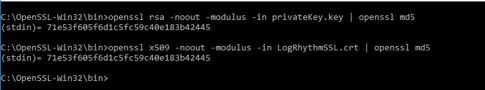
- The new certificates are generated.
