Alarms
What is an Alarm?
An alarm is a record of an event, or series of events, that triggered an alarm rule. In LogRhythm SIEM, alarm rules watch for certain conditions such as attacks on the network, compliance issues, system errors, and so on. For example, if log data reveals that a Trojan attempted to enter the network, an alarm rule such as "Alarm on Malware" is triggered that notifies administrators. The alarm rule can also trigger remediation (SmartResponse) actions, such as scripts for disabling an Active Directory account or killing a running process.
LogRhythm SIEM provides a wide variety of predefined rules, which administrators can load through the Knowledge Base Import process. Alarm rules are configured and managed in the Client Console. For more information, see Alarm Rules in the Client Console (Administrator's Guide).
How Alarms are Triggered
An alarm can be triggered in LogRhythm SIEM, as follows:
The Data Processor receives logs from Agents. The log processing engine, called the Message Processing Engine (MPE), then processes log data and classifies a subset as MPE Events. For more details, see the LogRhythm Architecture.
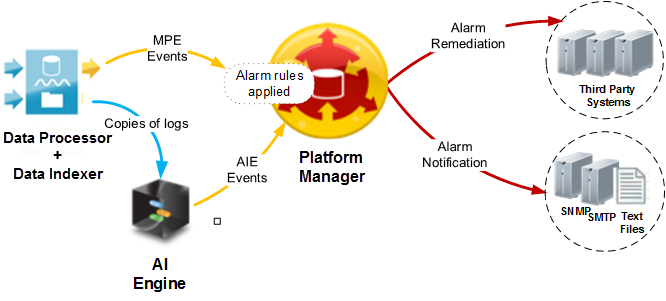
- The Data Processor forwards MPE events to the Platform Manager. If the Advanced Intelligence (AI) Engine is configured in the LogRhythm SIEM deployment, the Data Processor can also send copies of logs to the AI Engine for additional analysis. The AI Engine evaluates the logs against its AIE Correlation Rules. If a log triggers an AIE Rule, the AI Engine sends an AIE event to the Platform Manager (with Alarm rules already applied).
- As events move into the Platform Manager, the integrated Alarming and Response Manager (ARM) applies Alarm rules to the live stream of events data. If an Alarm rule matches an event, an alarm is created.
Alarms can trigger one or both of the following actions:
Notification. An alert is sent to administrators via SNMP traps, email (SMTP), or text files.
Remediation (SmartResponse). An automated script responds with an action to resolve the issue.
SmartResponse Actions
SmartResponse actions are automated defensive or operational responses to triggered alarm rules. The following examples describe some of the different functions that SmartResponse actions can perform:
- When compromised systems are detected, SmartResponse actions can perform vulnerability scans or packet captures on the target hosts.
- SmartResponse actions can kill inappropriate processes (such as BitTorrent or a Peer2Peer application) detected on a server.
- When LogRhythm SIEM observes concurrent successful logins to the same account from two different countries, SmartResponse actions can disable the account.
- SmartResponse actions can automatically set network devices to debug-level logging when LogRhythm SIEM observes critical operations issues on them.
An alarm rule can be configured to start up to 10 SmartResponse actions when triggered. Actions can be run immediately or after a quorum-approval process. In a quorum process, individuals or groups are required to approve the action before it runs (up to three levels of approval may be configured). When multiple individuals are assigned to the same level, only one person needs to provide approval or denial.
From the Web Console, you can use the Inspector panel to view the details of SmartResponse actions and manage their approval statuses. For more information, see View Additional Alarm Information and Approve or Deny SmartResponse Actions.
You cannot create, configure, or remove SmartResponse actions with the Web Console. These tasks can only be performed in the Client Console.
