NY DFS User Guide – Compliance Maturity Model: A Foundation and Road Map
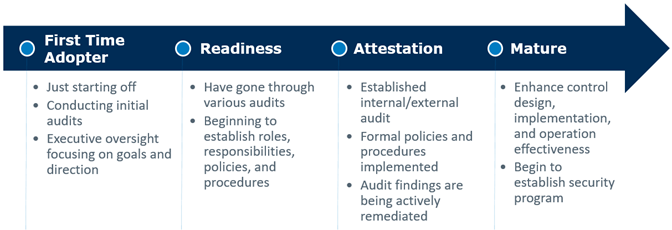
The Labs Compliance Research team within LogRhythm has established an understanding that our customers transition through a maturing process as they implement controls, policies, personnel, and system solutions according to the requirements of a given compliance or regulation. As compliance programs mature, the SIEM must be able to adapt and reflect changes within the organization’s environment. A compliance offering through SIEM that is out-of-the-box detracts value from the customer’s experience. With all the work put in towards establishing a compliance program, it is advantageous to integrate this gained insight into the SIEM to establish a strong foundation and structure for data.
When your organization hears it’s time for the annual audit or reference to compliance, the general outlook often is not overly positive. However, the opportunity exists to leverage these compliance frameworks to build a foundation and create competitive advantages. As an organization matures across the compliance maturity model (below), the groundwork of a foundation is established around policies, controls, systems, personnel, and understanding. The organization begins to establish key resources such as system classifications, account classifications, various risk assessments, scope definition, process & data flows, and audit results year-over-year, which are a key element to establishing this strong foundation.
All these factors are ingredients to establish what becomes a solid, yet adaptable foundation for which a mature, compliance organization can transition into a better security posture. This transition from the compliance foundation allows your security program to be built off a holistic and transparent understanding of the organization’s environment and risk profile.
Our goal through LogRhythm’s compliance approach is to provide a road map through which SIEM empowers the organization to grow and bridge the gap towards a security program. This allows organizations to start basic and transition into more enhanced facets of LogRhythm SIEM and other solutions. Data can now be utilized as a competitive advantage, a strong foundation to protect your organization.