MITRE ATT&CK® Module User Guide
This guide is meant to be used as a day-to-day reference for the MITRE ATT&CK content. All the content included in this module is listed here along with a detailed explanation, suggested response, and configuration and tuning notes.
Suppression Multiple: The Suppression Multiple in conjunction with the Suppression Period defines how much time must pass before the same AI Engine rule can be triggered again for the same set of criteria.
Environmental Dependence Factor: EDF is a high-level quantification of how much effort is required in configuration and tuning for an AI Engine rule to perform as expected. This setting has no impact on processing.
False Positive Probability: The False Positive Probability is used in Risk-Based Priority (RBP) calculation for AI Engine Rules. It estimates how likely the rule is to generate a false positive response. A value of low indicates the pattern the rule matches is almost always a true positive. However, a value of high indicates the pattern the rule matches is very likely to be a false positive.
Options range from 0 to 9 with:
- 0 indicating the pattern the rule matched is almost always a true positive
- 9 indicating the pattern the rule matched is very likely to be a false positive
T1003:OS Credential Dumping
AIE Rule ID: 1449
MITRE Tactic: Credential Access
Rule Description: T1003:OS Credential Dumping
Common Event: AIE:T1003:OS Credential Dumping
Classification: Security/Suspicious
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Credential Access
Technique: OS Credential Dumping
Rule Created: 2/8/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1003/
T1007:System Service Discovery
AIE Rule ID: 1452
MITRE Tactic: Discovery
Rule Description: T1007:System Service Discovery
Common Event: AIE:T1007:System Service Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: System Service Discovery
Rule Created: 2/4/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1007/
T1012:Query Registry
AIE Rule ID: 1453
MITRE Tactic: Discovery
Rule Description: T1012:Query Registry
Common Event: AIE:T1012:Query Registry
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: Query Registry
Rule Created: 2/4/2019
Rule Updated: 1/5/2021
Rule Updated: 3/30/2023
AIE Rule
https://attack.mitre.org/techniques/T1012/
T1016:System Network Configuration Discovery
AIE Rule ID: 1454
MITRE Tactic: Discovery
Rule Description: T1016:System Network Configuration Discovery
Common Event: AIE:T1016:System Network Configuration Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: System Network Configuration Discovery
Rule Created: 2/7/2019
Rule Updated: 1/5/2021
AIE Rule
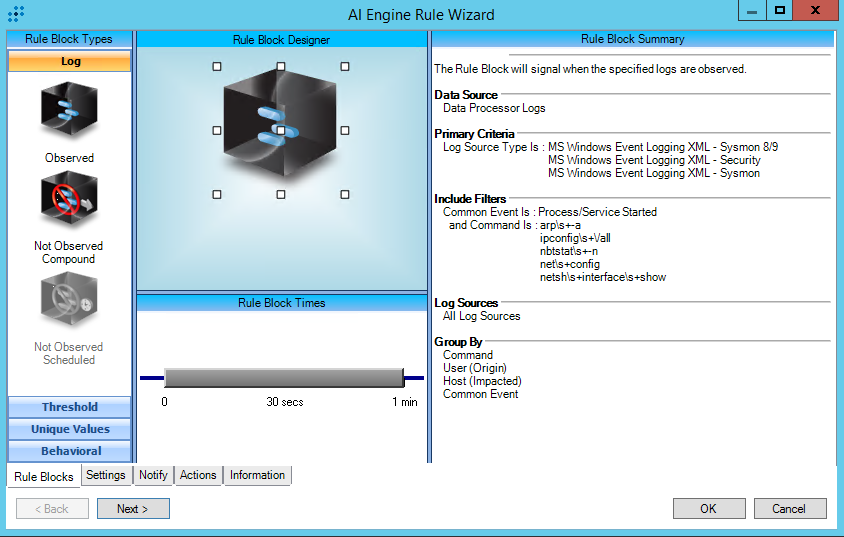
https://attack.mitre.org/techniques/T1016/
T1033:System Owner-User Discovery
AIE Rule ID: 1455
MITRE Tactic: Discovery
Rule Description: T1033:System Owner-User Discovery
Common Event: AIE:T1033:System Owner-User Discovery
Classification: Security/Reconnaissance
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic: Discovery
Technique: System Owner/User Discovery
Rule Created: 2/8/2019
Rule Updated: 1/5/2021
AIE Rule
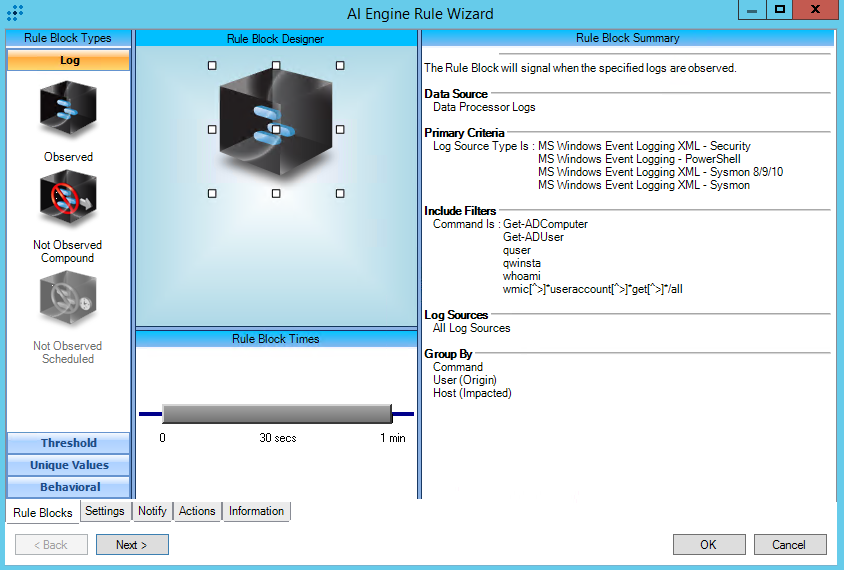
https://attack.mitre.org/techniques/T1033/
T1048:Exfiltration Over Alternative Protocol
AIE Rule ID: 1456
MITRE Tactic: Exfiltration
Rule Description: T1048:Exfiltration Over Alternative Protocol
Common Event: AIE:T1048:Exfiltration Over Alternative Protocol
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Exfiltration
Technique: Exfiltration Over Alternative Protocol
Rule Created:2/9/2019
Rule Updated: 1/5/2021
AIE Rule
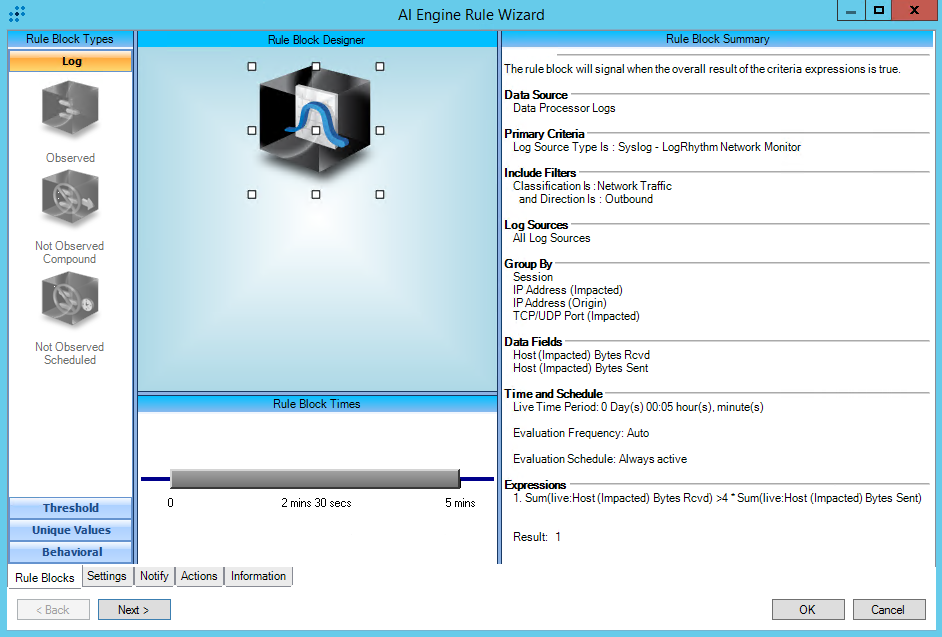
https://attack.mitre.org/techniques/T1048/
T1018:Remote System Discovery
AIE Rule ID: 1457
MITRE Tactic: Discovery
Rule Description: T1018:Remote System Discovery
Common Event: AIE:T1018:Remote System Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: Remote System Discovery
Rule Created: 2/27/2019
Rule Updated: 1/5/2021
AIE Rule
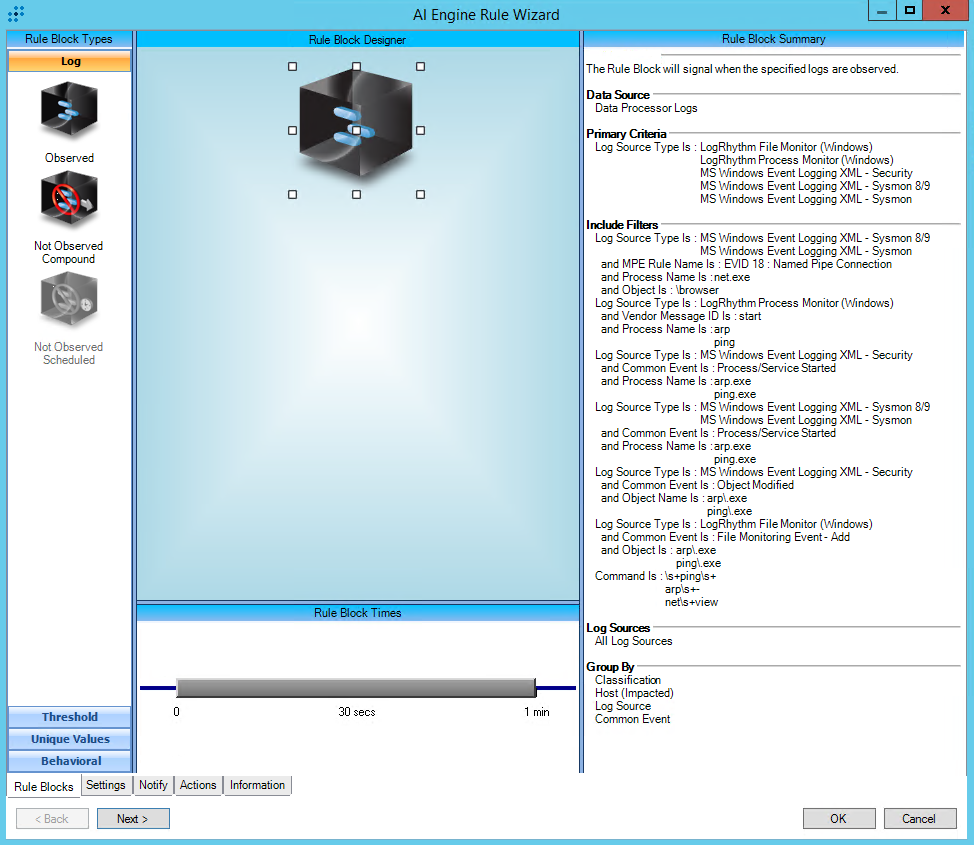
https://attack.mitre.org/techniques/T1018/
T1543.003:Windows Service
AIE Rule ID: 1459
MITRE Tactic: Persistence, Privilege Escalation
Rule Description: T1543.003:Windows Service
Common Event: AIE:T1543.003:Windows Service
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactics: Persistence, Privilege Escalation
Technique: Windows Service
Rule Created: 2/20/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1543/003/
T1547.001:Registry Run Keys/Startup Folder
AIE Rule ID: 1460
MITRE Tactic: Persistence
Rule Description: T1547.001:Registry Run Keys/Startup Folder
Common Event: AIE:T1547.001:Registry Run Keys/Startup Folder
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Persistence
Technique: Registry Run Keys/Startup Folder
Rule Created: 2/9/2019
Rule Updated: 1/5/2021
Rule Updated: 10/12/2023
AIE Rule
https://attack.mitre.org/techniques/T1547/001/
T1059:Command and Scripting Interpreter
AIE Rule ID: 1461
MITRE Tactic: Execution
Rule Description: T1059:Command and Scripting Interpreter
Common Event: AIE:T1059:Command and Scripting Interpreter
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Execution
Technique: Command and Scripting Interpreter
Rule Created: 2/11/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1059/
T1021.002:SMB/Windows Admin Shares
AIE Rule ID: 1462
MITRE Tactic: Lateral Movement
Rule Description: T1021.002:SMB/Windows Admin Shares
Common Event: AIE:T1021.002:SMB/Windows Admin Shares
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Lateral Movement
Technique: SMB/Windows Admin Shares
Rule Created: 2/15/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1021/002/
T1082:System Information Discovery
AIE Rule ID: 1463
MITRE Tactic: Discovery
Rule Description: T1082:System Information Discovery
Common Event: AIE:T1082:System Information Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: System Information Discovery
Rule Created: 2/25/2019
Rule Updated: 1/5/2021
AIE Rule
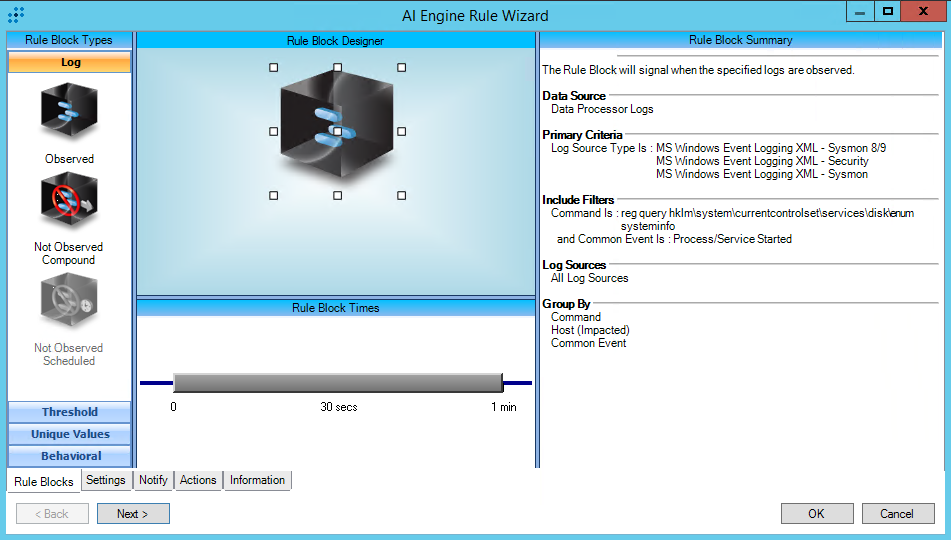
https://attack.mitre.org/techniques/T1082/
T1059.001:PowerShell
AIE Rule ID: 1464
MITRE Tactic: Execution
Rule Description: T1059.001:PowerShell
Common Event: AIE:T1059.001:PowerShell
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic(s): Execution
Technique: PowerShell
Rule Created: 2/25/2019
Rule Updated: 2/4/2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1059/001/
AIE Rule
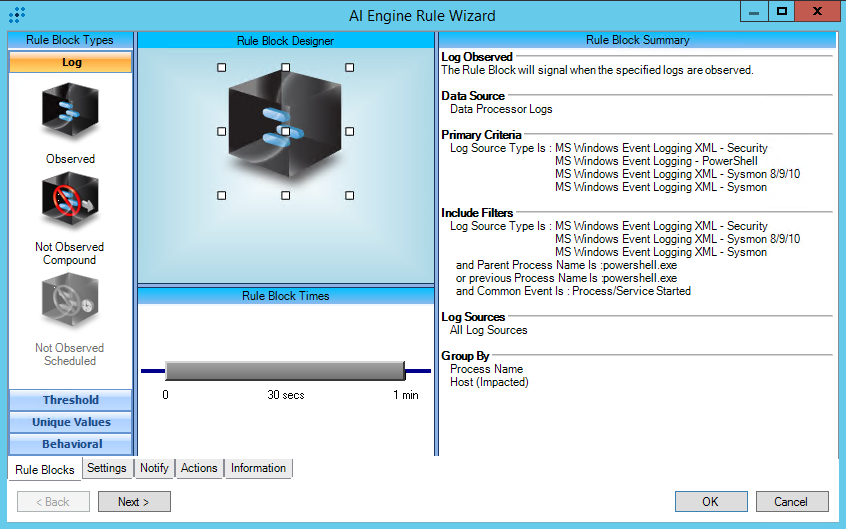
https://attack.mitre.org/techniques/T1059/001/
T1189:Drive-By Compromise
AIE Rule ID: 1466
MITRE Tactic: Initial Access
Rule Description: T1189:Drive-By Compromise
Common Event: AIE:T1189:Drive-By Compromise
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Initial Access
Technique: Drive-by Compromise
Rule Created: 2/14/2019
Rule Updated: 1/5/2021
AIE Rule
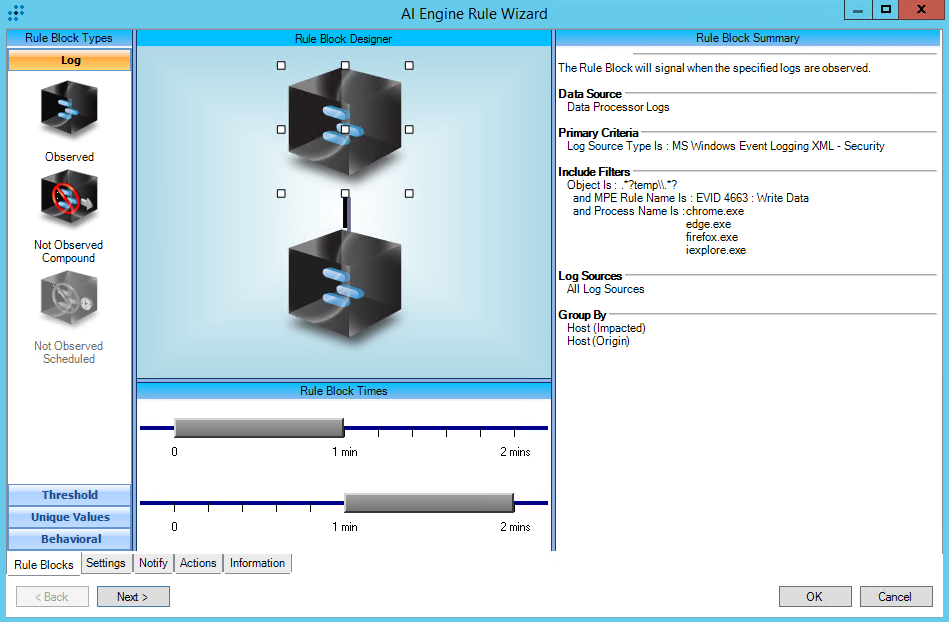
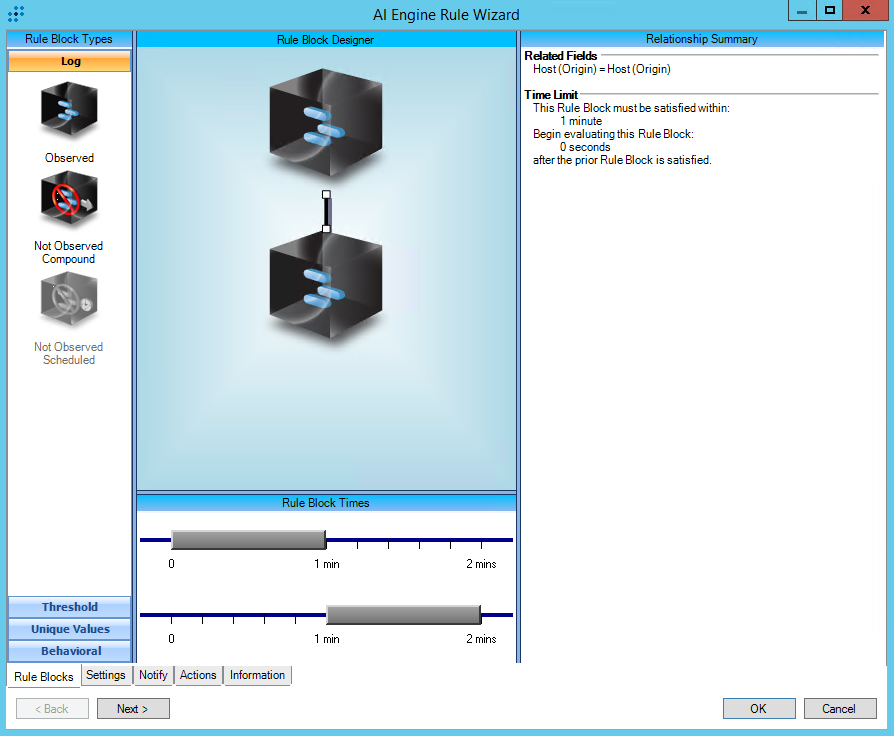
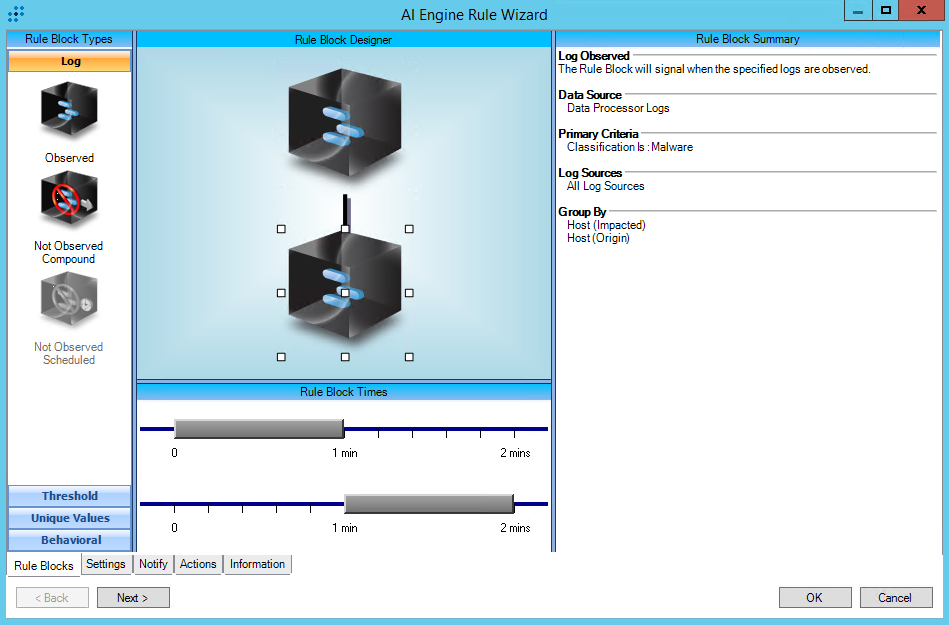
https://attack.mitre.org/techniques/T1189/
T1057:Process Discovery
AIE Rule ID: 1467
MITRE Tactic: Discovery
Rule Description: T1057:Process Discovery
Common Event: AIE:T1057:Process Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: Process Discovery
Rule Created: 3/4/2019
Rule Updated: 1/5/2021
AIE Rule
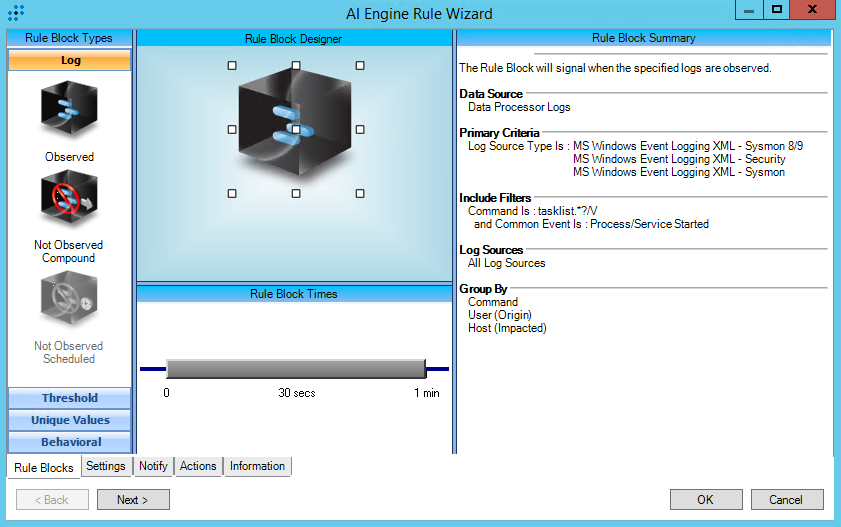
https://attack.mitre.org/techniques/T1057/
T1047:Windows Management Instrumentation
AIE Rule ID: 1468
MITRE Tactic: Execution
Rule Description: T1047:Windows Management Instrumentation
Common Event: AIE:T1047:Windows Management Instrumentation
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Execution
Technique: Windows Management Instrumentation
Rule Created: 3/6/2019
Rule Updated: 1/5/2021
AIE Rule
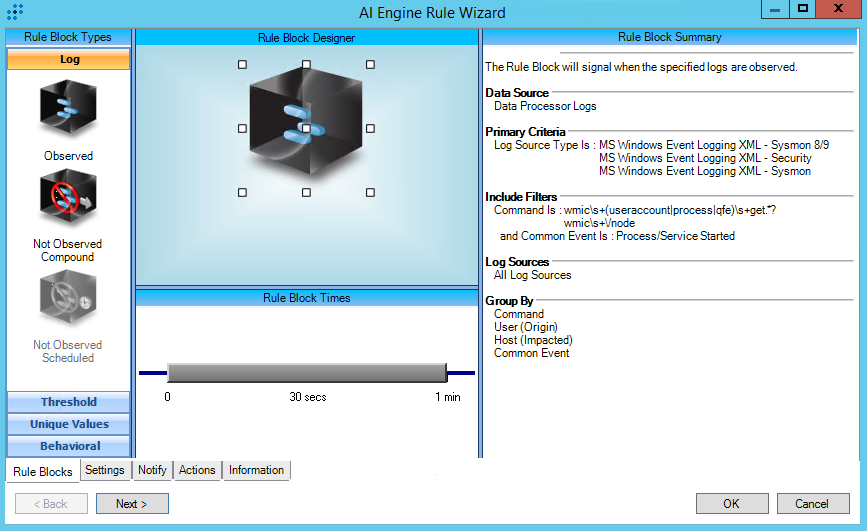
https://attack.mitre.org/techniques/T1047/
T1070.006:Timestomp
AIE Rule ID: 1469
MITRE Tactic: Defense Evasion
Rule Description: T1070.006:Timestomp
Common Event: AIE:T1070.006:Timestomp
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Defense Evasion
Technique: Timestomp
Rule Created: 3/8/2019
Rule Updated: 1/5/2021
AIE Rule
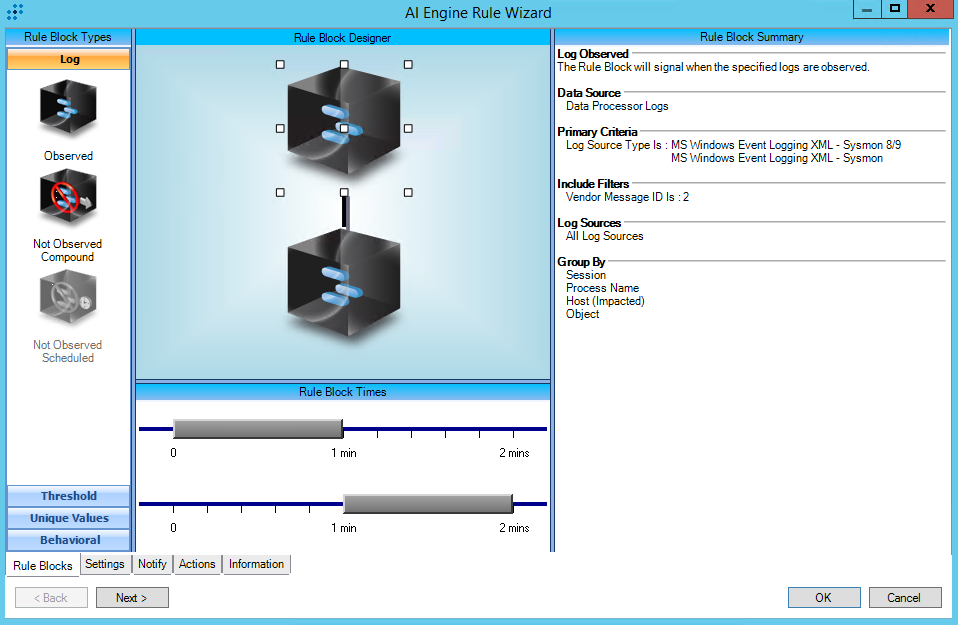
https://attack.mitre.org/techniques/T1070/006/
T1069:Permission Groups Discovery
AIE Rule ID: 1477
MITRE Tactic: Discovery
Rule Description: T1069:Permission Groups Discovery
Common Event: AIE:T1069:Permission Groups Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: Permission Groups Discovery
Rule Created: 4/8/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1069/
T1087:Account Discovery
AIE Rule ID: 1478
MITRE Tactic: Discovery
Rule Description: T1087:Account Discovery
Common Event: AIE:T1087:Account Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Discovery
Technique: Account Discovery
Rule Created: 4/12/2019
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1087/
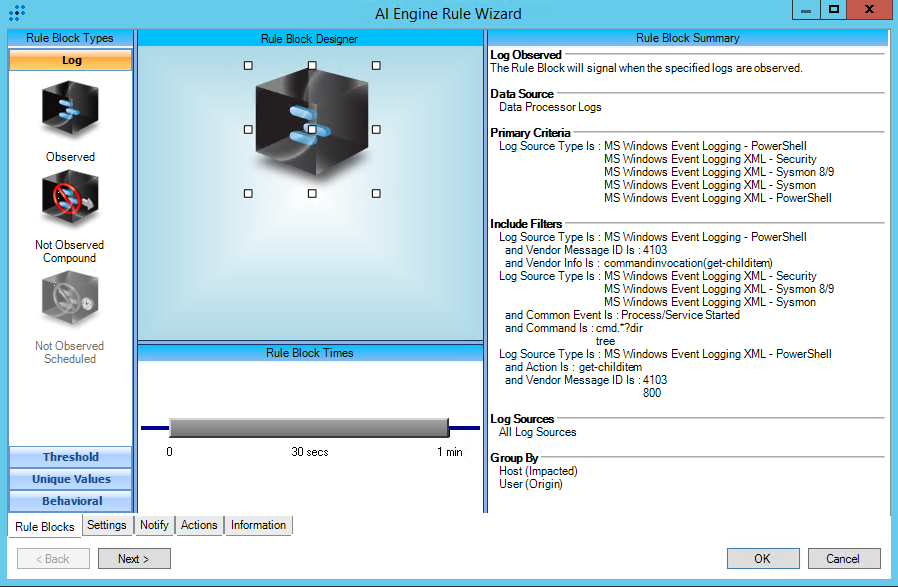
T1083:File and Directory Discovery
AIE Rule ID: 1479
MITRE Tactic: Discovery
Rule Description: T1083:File and Directory Discovery
Common Event: AIE:T1083:File and Directory Discovery
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Discovery
Technique: File and Directory Discovery
Rule Created: 4/9/2019
Rule Updated: 12/7/2021
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1083/
Notes:
Log Source Types:
MS Windows Event Logging - PowerShell
MS Windows Event Logging XML - PowerShell
MS Windows Event Logging XML - Security (v1 & v2)
MS Windows Event Logging XML - Sysmon (v1 & v2)
MS Windows Event Logging XML - Sysmon 8/9/10
Configuration:
PowerShell Module logging must be enabled
Windows process and common-line auditing must be enabled
Microsoft Sysmon's configuration for Event ID 1: Process creation must include (or not exclude) cmd.exe and tree.com
Please refer to Logging and Monitoring Configuration section of the MITRE ATT&CK Module Deployment Guide for more information: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module#MITREATT&CK%C2%AEDeploymentGuide%E2%80%93ImportandSynchronizetheModule-LoggingandMonitoringConfiguration
Tuning:
Exclude accounts from trusted backup/scanning utilities such as vulnerability scanners or backup software that frequently perform file and directory scanning.
AIE Rule
https://attack.mitre.org/techniques/T1083/
T1218.011:Rundll32
AIE Rule ID: 1480
MITRE Tactic: Defense Evasion
Rule Description: T1218.011:Rundll32
Common Event: AIE:T1218.011:Rundll32
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Defense Evasion
Technique: Rundll32
Rule Created: 4/15/2019
Rule Updated: 1/5/2021
AIE Rule
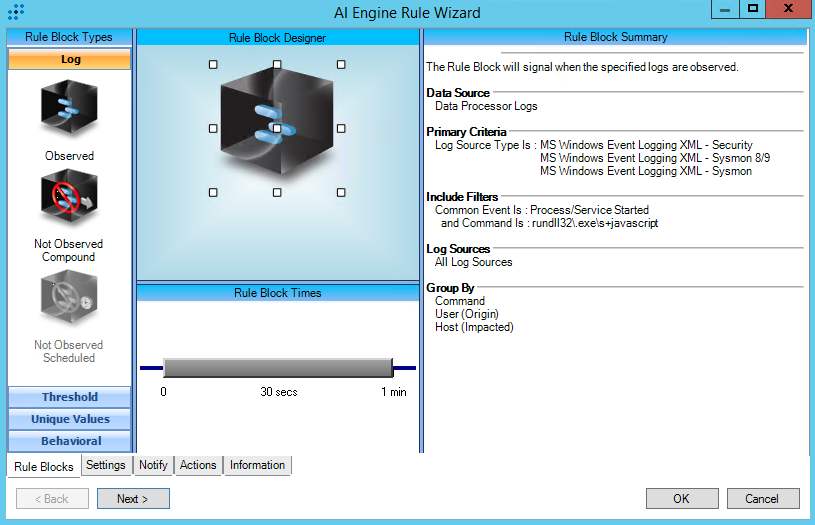
https://attack.mitre.org/techniques/T1218/011/
T1569.002:Service Execution
AIE Rule ID: 1481
MITRE Tactic: Execution
Rule Description: T1569.002:Service Execution
Common Event: AIE:T1569.002:Service Execution
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Execution
Technique: Service Execution
Rule Created: 12/10/2018
Rule Updated: 1/5/2021
AIE Rule
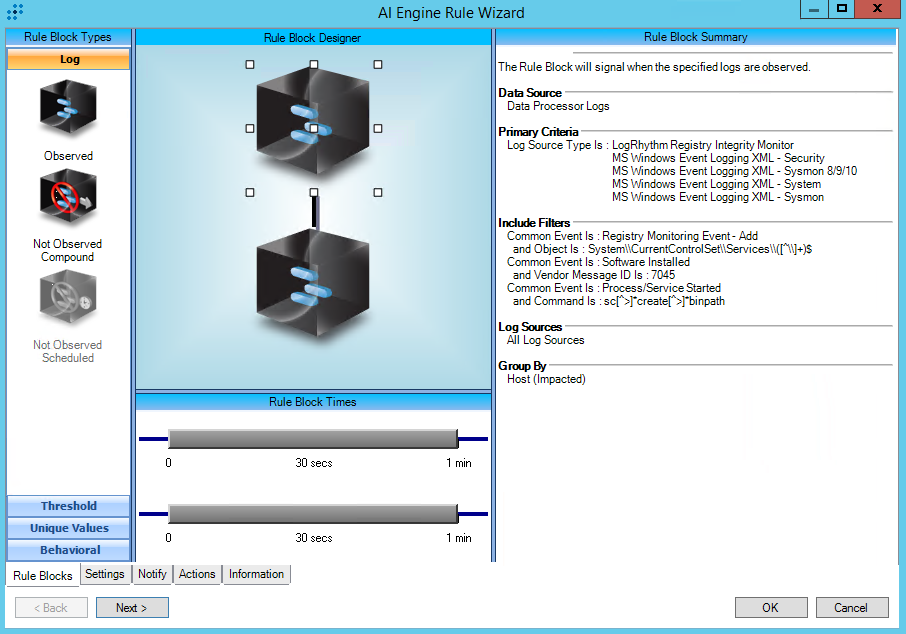
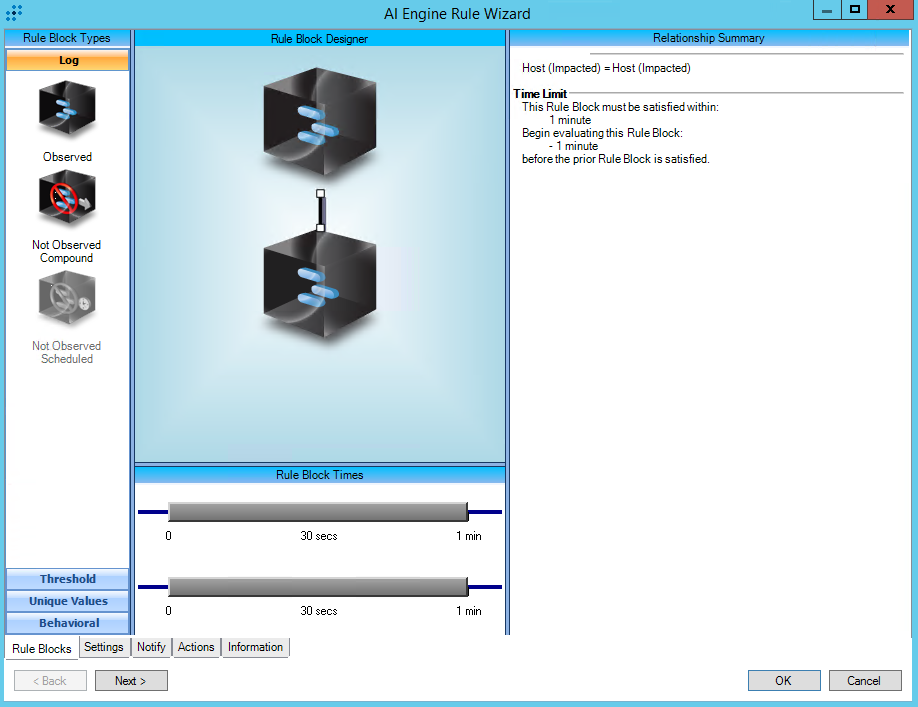
https://attack.mitre.org/techniques/T1569/002/
T1090.001:Proxy
AIE Rule ID: 1482
MITRE Tactic: C2
Rule Description: T1090.001:Proxy
Common Event: AIE:T1090.001:Proxy
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactics: Command and Control
Technique: Internal Proxy
Rule Created: 4/22/2019
Rule Updated:1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1090/001/
T1105:Ingress Tool Transfer
AIE Rule ID: 1483
MITRE Tactic: Multiple
Rule Description: T1105:Ingress Tool Transfer
Common Event: AIE:T1105:Ingress Tool Transfer
Classification: Security/Activity
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactics: Command and Control
Technique: Ingress Tool Transfer
Rule Created: 4/9/2019
Rule Updated: 1/5/2021
AIE Rule
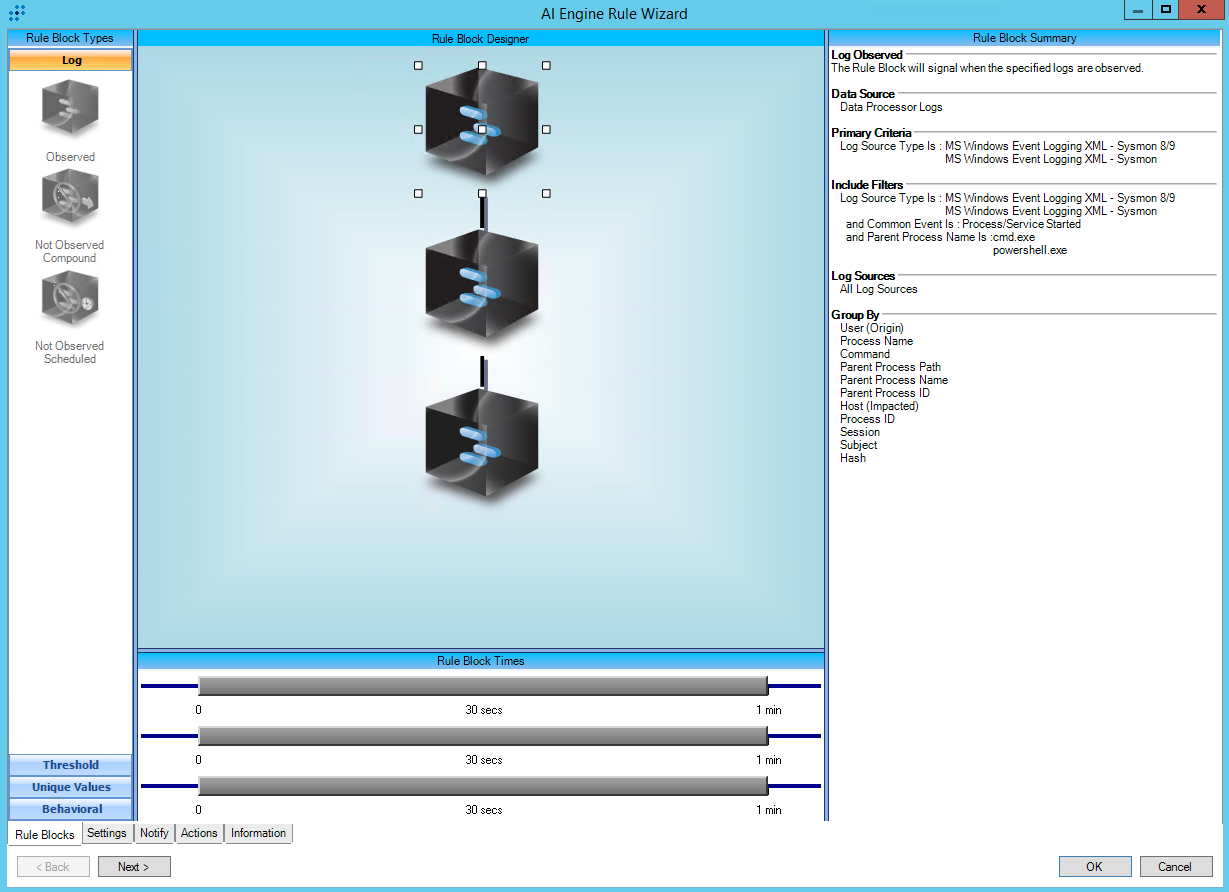
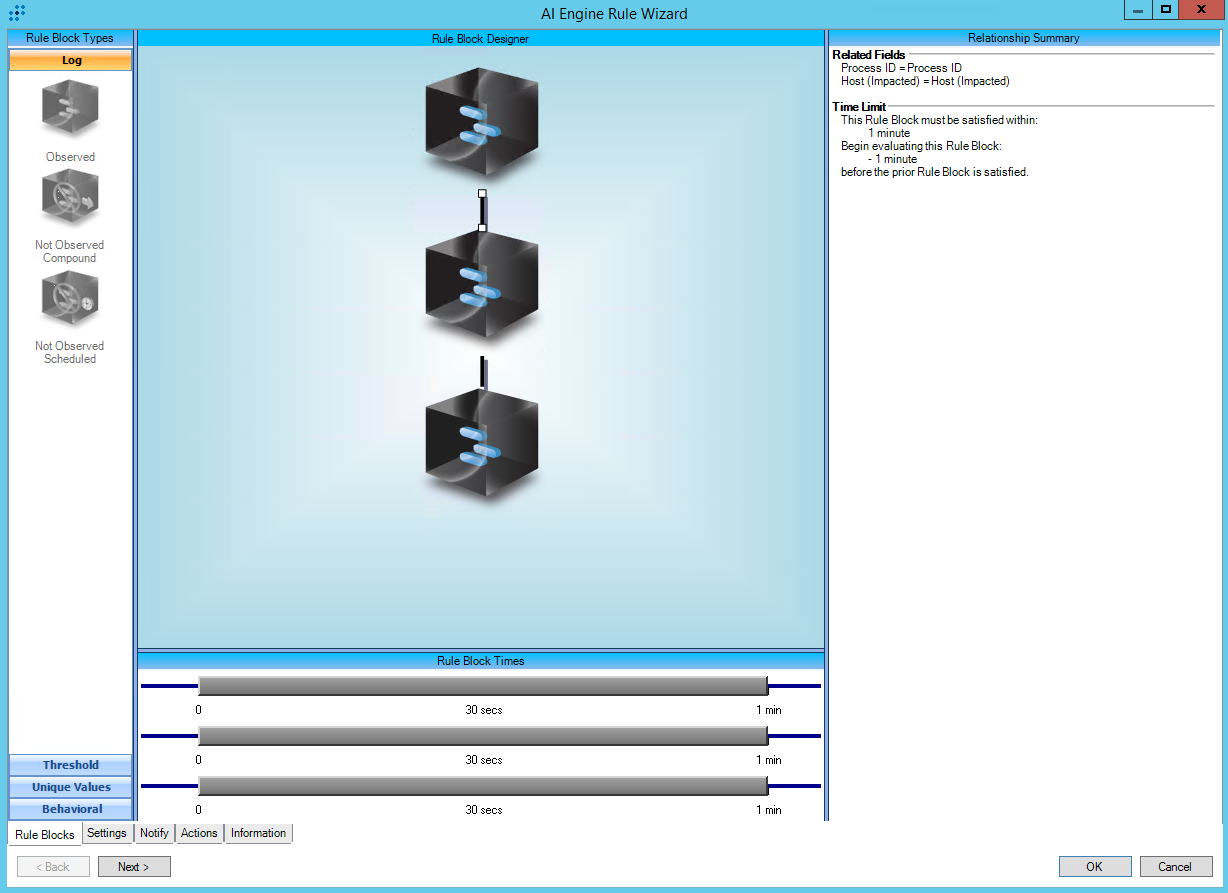
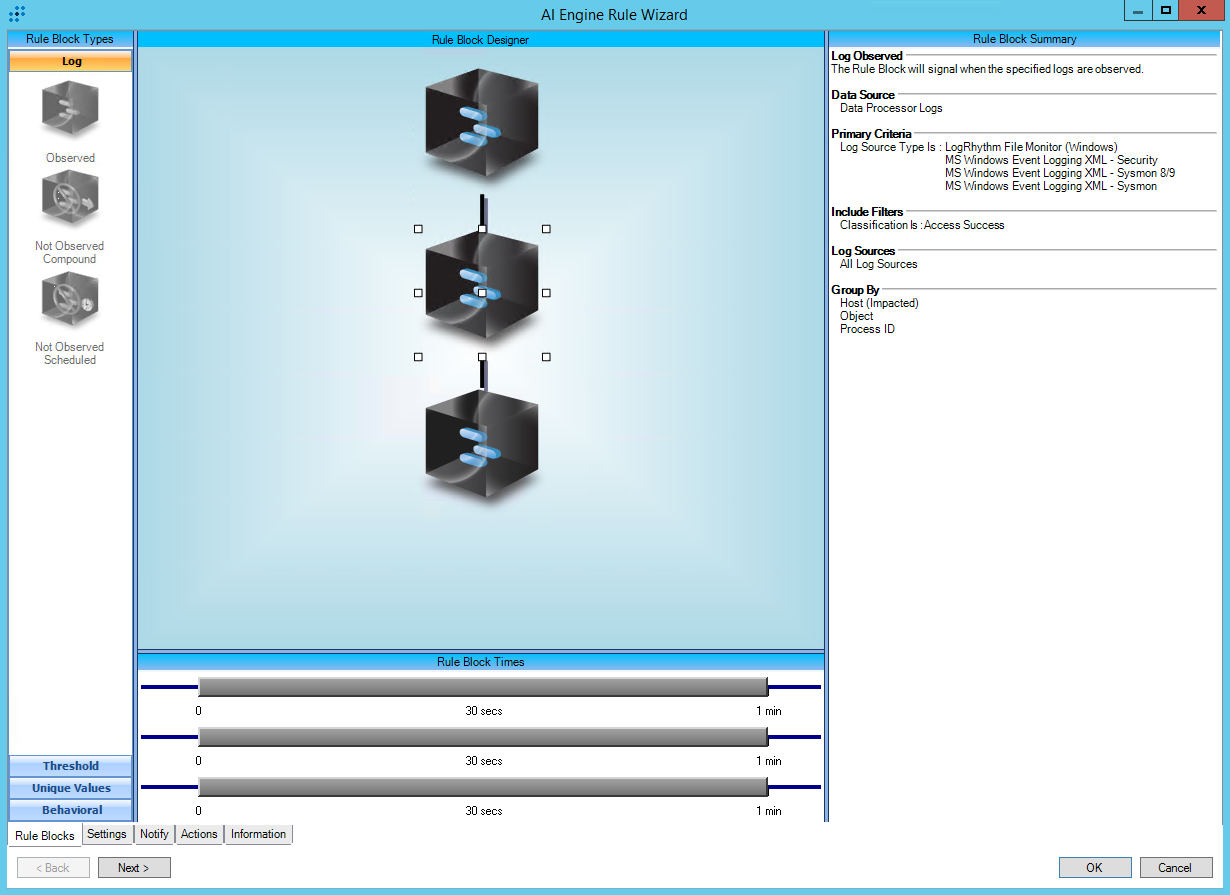
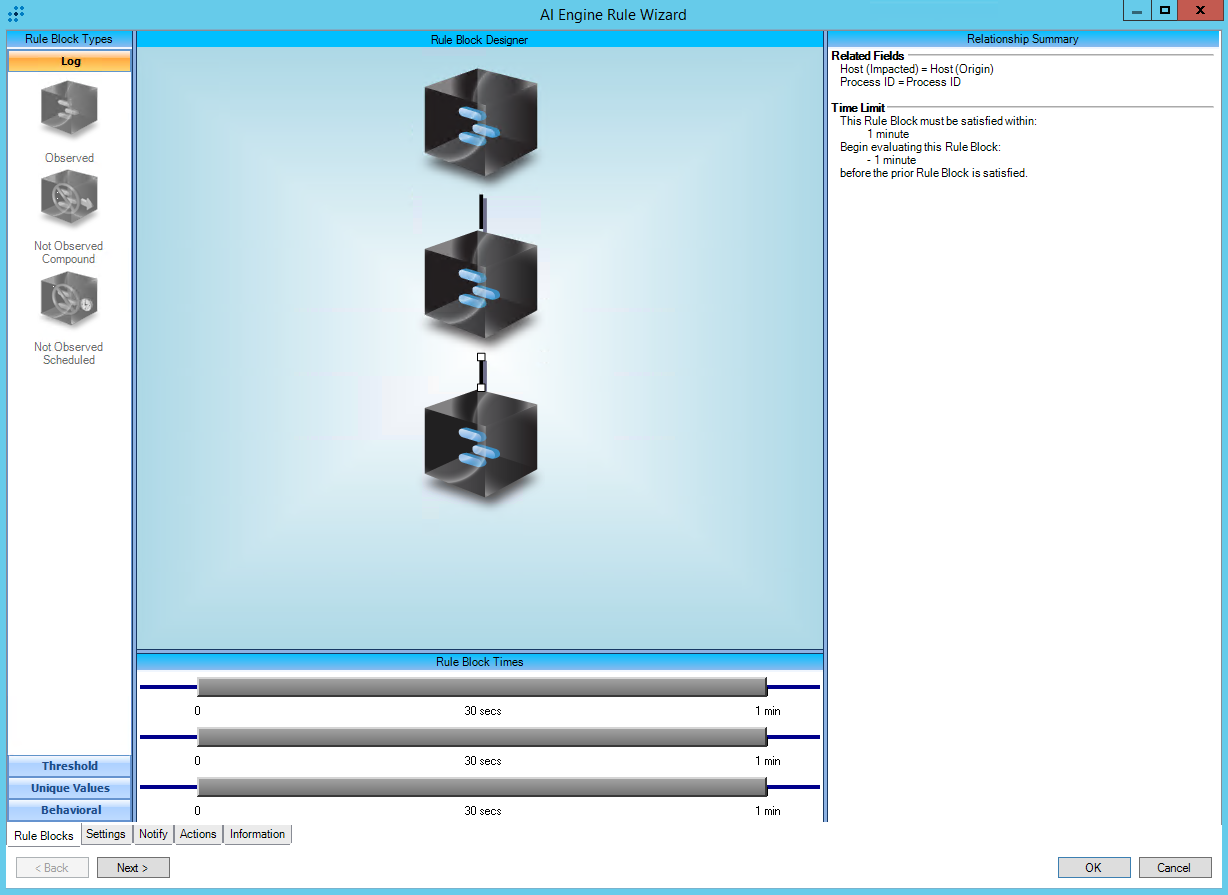
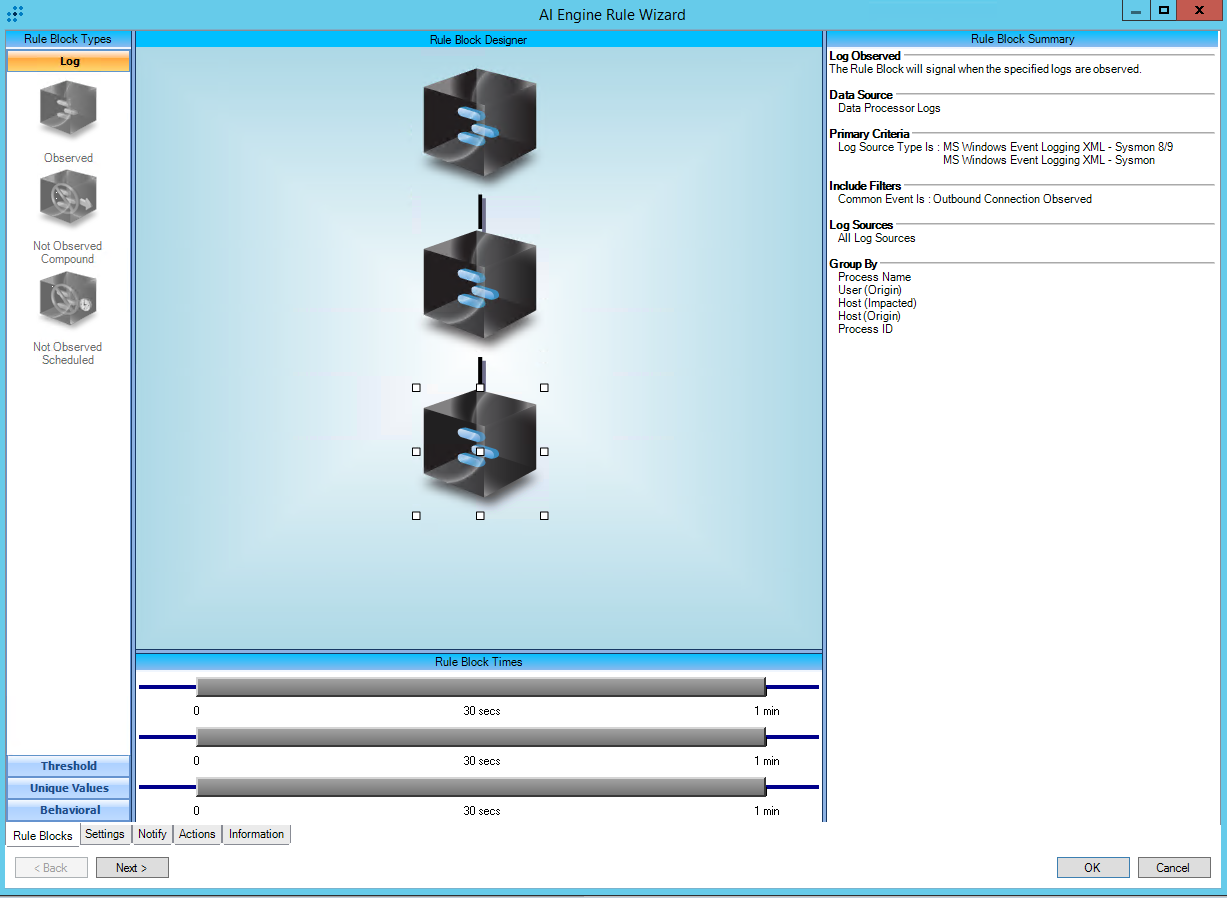
https://attack.mitre.org/techniques/T1105/
T1218.010:Regsvr32
AIE Rule ID: 1484
MITRE Tactic: Multiple
Rule Description: T1218.010:Regsvr32
Common Event: AIE:T1218.010:Regsvr32
Classification: Security/Activity
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Defense Evasion
Technique: Regsvr32
Rule Created: 4/18/2019
Rule Updated: 1/5/2021
AIE Rule
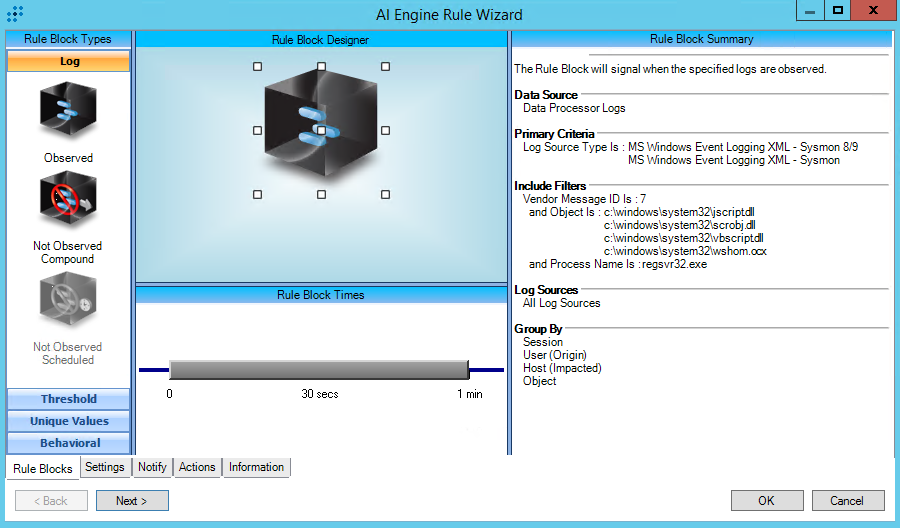
https://attack.mitre.org/techniques/T1218/010/
T1036.003:Rename System Utilities
AIE Rule ID: 1492
MITRE Tactic: Defense Evasion
Rule Description: T1036.003:Rename System Utilities
Common Event: AIE:T1036.003:Rename System Utilities
Classification: Security/Suspicious
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 2
AIE Rule Additional Details
Tactic: Defense Evasion
Technique: Rename System Utilities
Rule Created: 11/4/2019
Rule Updated: 1/5/2021
AIE Rule
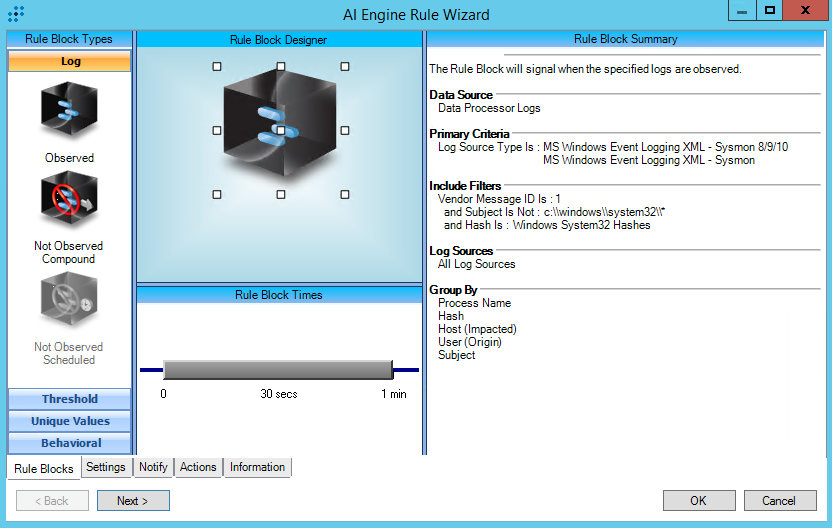
https://attack.mitre.org/techniques/T1036/003/
T1566.001:Spearphishing Attachment
AIE Rule ID: 1493
MITRE Tactic: Initial Access
Rule Description: T1566.001:Spearphishing Attachment
Common Event: AIE:T1566.001:Spearphishing Attachment
Classification: Security/Suspicious
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic: Initial Access
Technique: Spearphishing Attachment
Rule Created: 11/19/2019
Rule Updated: 1/5/2021
AIE Rule
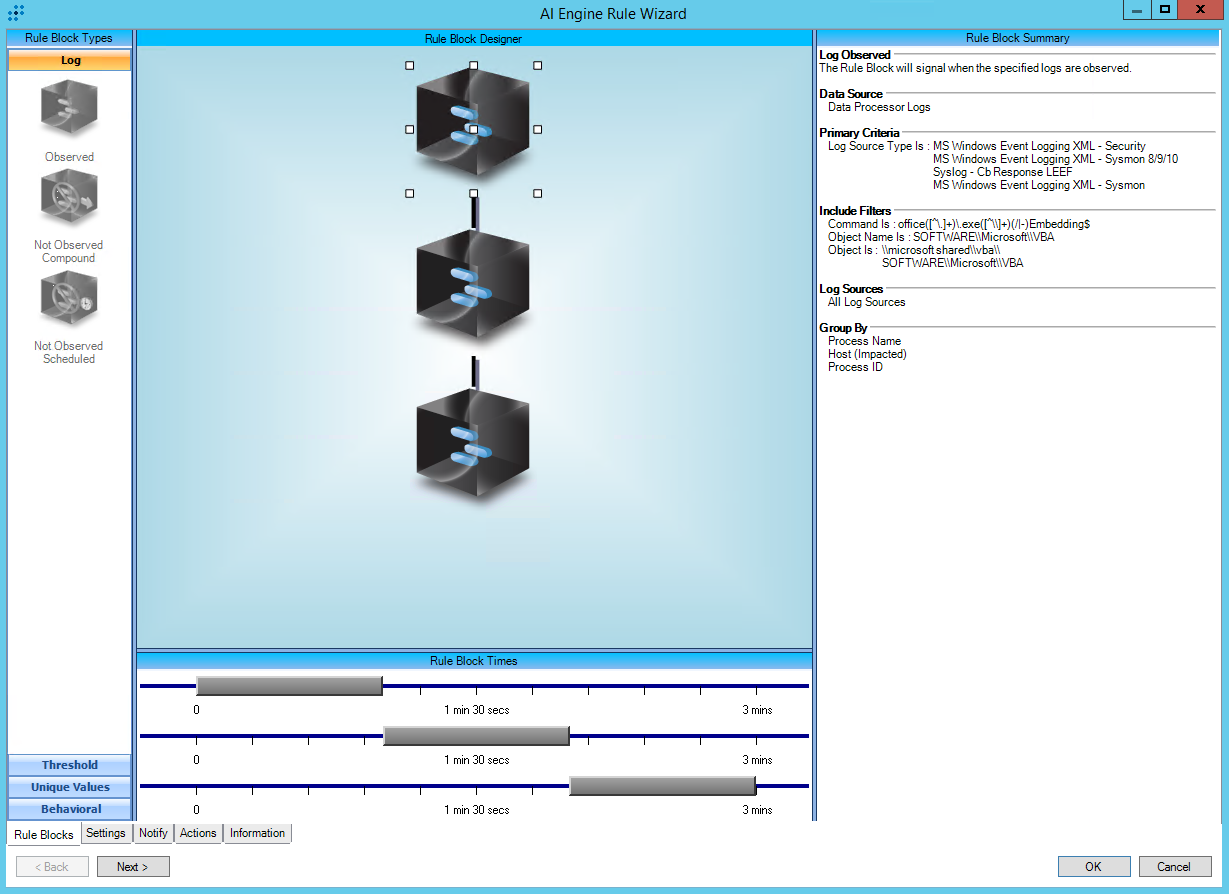
https://attack.mitre.org/techniques/T1566/001/
T1550.002:Pass the Hash
AIE Rule ID: 1494
MITRE Tactic: Lateral Movement
Rule Description: T1550.002:Pass the Hash
Common Event: AIE:T1550.002:Pass the Hash
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
AIE Rule Additional Details
Tactic: Lateral Movement
Technique: Pass the Hash
Rule Created: 12/24/2019
Rule Updated: 1/5/2021
Rule Updated: 10/12/2023
AIE Rule
https://attack.mitre.org/techniques/T1550/002/
T1550.003:Pass the Ticket
AIE Rule ID: 1495
MITRE Tactic: Lateral Movement
Rule Description: T1550.003:Pass the Ticket
Common Event: AIE:T1550.003:Pass the Ticket
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 3
AIE Rule Additional Details
Tactics: Defense Evasion, Lateral Movement
Technique: Pass the Ticket
Rule Created: 1/10/2020
Rule Updated: 1/5/2021
AIE Rule
For further guidance on the Tactic:Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1550/003/
T1053:Scheduled Task/Job
AIE Rule ID: 1497
MITRE Tactic: Execution, Persistence, Privilege Escalation
Rule Description: T1053:Scheduled Task/Job
Common Event: AIE:T1053:Scheduled Task/Job
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactics: Execution, Persistence, Privilege Escalation
Technique: Scheduled Task/Job
Rule Created: 1/30/2020
Rule Update: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1053/
This rule currently encompasses sub-techniques .002 and .005 and will be broken out into per sub-techniques in the future.
T1136.003:Cloud Account
AIE Rule ID: 1499
MITRE Tactic: Persistence
Rule Description: T1136.003:Cloud Account
Common Event: AIE:T1136.003:Cloud Account
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic: Persistence
Technique: Cloud Account
Rule Created: 4/20/2020
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1136/003/
T1098:Account Manipulation
AIE Rule ID: 1500
MITRE Tactic: Credential Access, Persistence
Rule Description: T1098:Account Manipulation
Common Event: AIE:T1098:Account Manipulation
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic: Persistence
Technique: Account Manipulation
Rule Created: 4/20/2020
Rule Updated: 1/5/2021
AIE Rule
https://attack.mitre.org/techniques/T1098/
T1566.002:Spearphishing Link
AIE Rule ID: 1501
MITRE Tactic: Initial Access
Rule Description: T1566.002:Spearphishing Link
Common Event: AIE:T1566.002:Spearphishing Link
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic: Initial Access
Technique: Phishing: Spearphishing Link
Rule Created: 4/15/2020
Rule Updated: 1/5/2021
AIE Rule
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1566/002/
T1534:Internal Spearphishing
AIE Rule ID: 1502
MITRE Tactic: Lateral Movement
Rule Description: T1534:Internal Spearphishing
Common Event: AIE:T1534:Internal Spearphishing
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 1
AIE Rule Additional Details
Tactic: Lateral Movement
Technique: Internal Spearphishing
Rule Created: 4/27/2020
Rule Updated: 3/25/2021
AIE Rule
For further guidance on this Tactic:Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1534/
T1114.003:Email Forwarding Rule
AIE Rule ID: 1503
MITRE Tactic: Collection
Rule Description: T1114.003:Email Forwarding Rule
Common Event: AIE:T1114.003:Email Forwarding Rule
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic: Collection
Technique: Email Forwarding Rule
Rule Created:4/19/2020
Rule Updated: 8/24/2021
Notes:
The API - Office 365 Management Activity log that triggers this rule can be generated by several different user actions. Search the API - Office 365 Management Activity log for command = set-mailbox, new-inboxrule, updateinboxrule, or set-inboxrule to find the offending rule name and information.
Log Source Types:
API - Office 365 Management Activity
Configuration:
In the Microsoft 365 compliance center, the default policy "Creation of forwarding/redirect rule" must be enabled. For more information, see Managing Alerts in the Alert Policies in Microsoft 365 topic for more information.
AIE Rule
https://attack.mitre.org/techniques/T1114/003/
T1566.002:Spearphishing Link:O365
AIE Rule ID: 1504
MITRE Tactic: Initial Access
Rule Description: T1566.002:Spearphishing Link:O365
Common Event: AIE:T1566.002:Spearphishing Link:O365
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 1
AIE Rule Additional Details
Tactic: Initial Access
Technique: Phishing: Spearphishing Link
Rule Created: 4/15/2020
Rule Updated: 1/5/2021
AIE Rule
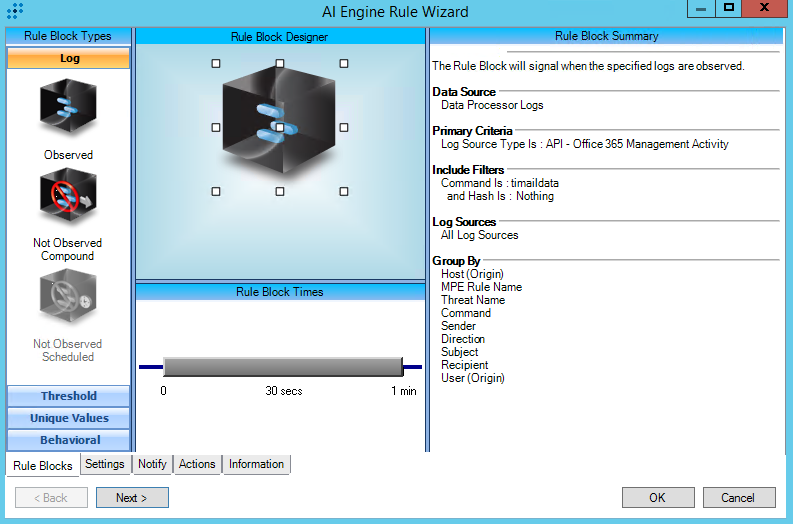
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1566/002/
T1190:Exploit Public-Facing Application:SQL Injection
AIE Rule ID: 1505
MITRE Tactic: Initial Access
Rule Description: T1190:Exploit Public-Facing Application:SQL Injection
Common Event: AIE:T1190:Exploit Public-Facing Application:SQL Injection
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Initial Access
Technique: Exploit Public-Facing Application
Rule Created: 3/31/2021
Rule Updated: N/A
For further guidance on this Tactic:Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1190/
Notes:
Log Source Types:
API - Cisco IDS/IPS
API - Sourcefire eStreamer
Flat File - McAfee Foundstone
Flat File - Snort Fast Alert File
OPSEC LEA - Checkpoint Firewall
OPSEC LEA - Checkpoint Log Server
Syslog - Apcon Network Monitor
Syslog - Cisco FirePOWER
Syslog - Cisco FireSIGHT
Syslog - Citrix Netscaler
Syslog - Dell SecureWorks iSensor IPS
Syslog - Enterasys Dragon IDS
Syslog - F5 BIG-IP ASM v12
Syslog - F5 Big-IP LTM
Syslog - Fortinet FortiAnalyzer
Syslog - Fortinet FortiGate v4.0
Syslog - IBM WebSphere DataPower Integration
Syslog - Imperva Incapsula CEF
Syslog - Imperva SecureSphere
Syslog - Juniper Firewall
Syslog - Juniper IDP
Syslog - Juniper NSM
Syslog - NetScreen Firewall
Syslog - OSSEC Alerts
Syslog - Sguil
Syslog - Snort IDS
Syslog - Sourcefire IDS 3D
Syslog - Symantec Endpoint Server
Syslog - Tipping Point IPS
Syslog - Trend Micro Deep Security CEF
Syslog - Trustwave Web Application Firewall
UDLA - ISS Proventia SiteProtector - IPS
Configuration:
This rule must be tuned before enabling. Configure rule with expected log source types by adding to the Log Source Criteria tab in the rule block. This rule should only evaluate logs associated with web applications, and that are public facing. Log source types that would be applicable to this rule include, and are not limited to those listed above in "Log Source Types".
Tuning:
This rule is specifically looking for logs that would be applicable to the detection of "SQL Injection". If false positives occur, consider tuning the log source logic.
AIE Rule
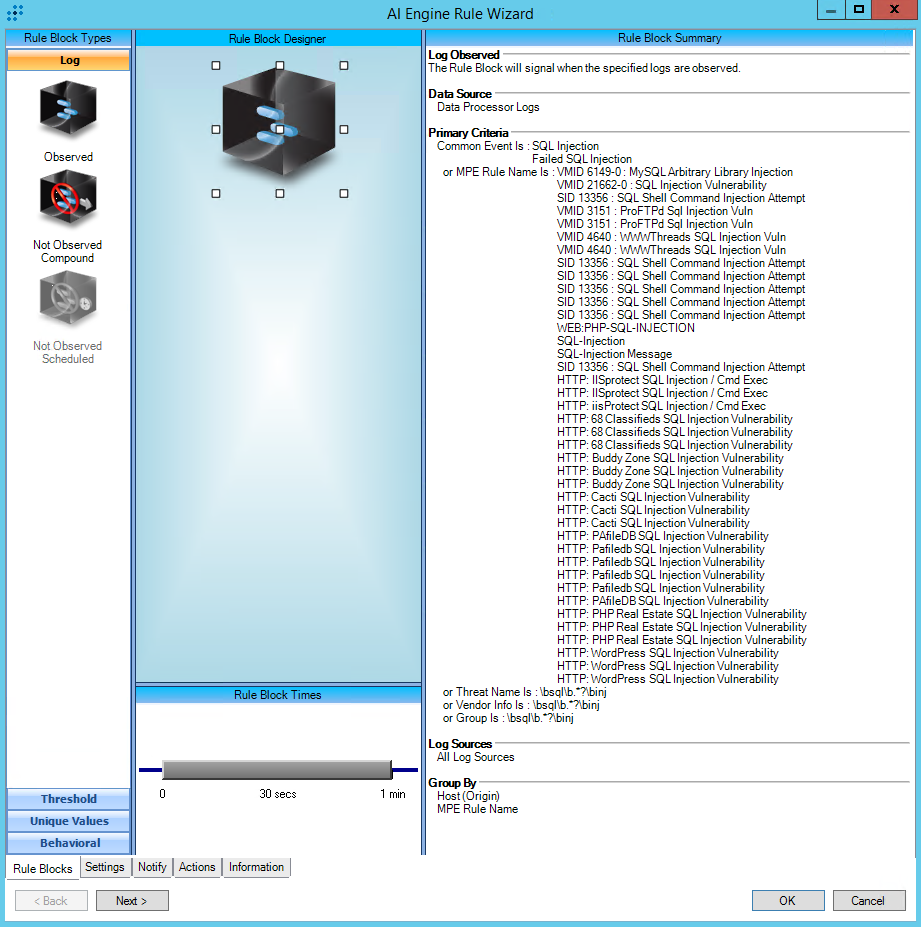
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1190/
T1199:Trusted Relationship
AIE Rule ID: 1513
MITRE Tactic: Initial Access
Rule Description: T1199:Trusted Relationship
Common Event: AIE:T1199:Trusted Relationship
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Initial Access
Technique: Trusted Relationship
Rule Created: 6/15/2021
Rule Updated: N/A
For further guidance on this Tactic:Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1199/
Notes:
Log Source Types:
LogRhythm AI Engine
Configuration:
This rule must be tuned before enabling. Populate the “MA: Third Party Accounts” list with a list of user or service accounts used by 3rd parties to access your company’s network, applications, services, etc.
Tuning:
This rule is specifically looking for matches between AI Engine (AIE) Events and users or service accounts in the “MA: Third Party Accounts” list. This rule is considered a “Feedback” rule, meaning that another AIE rule evented containing the user listed in “MA: Third Party Accounts” list. The AIE rule that evented causing this feedback rule to event should be the focus area for tuning.
You may also tune this rule by creating an exception. If a number of exceptions are needed involving the same 3rd party company, you may create two additional lists for user, and Host, then adding to the exceptions tab a rule to exclude the user list and the host list you created.
You may also leverage the “CCF: Third Party Accounts” list by adding the list to the include filter.
AIE Rule
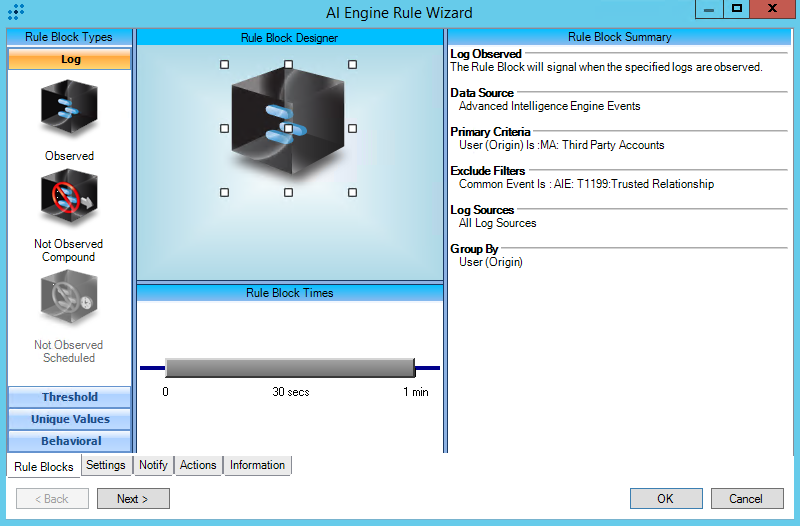
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1199/
T1078.001:Default Accounts
AIE Rule ID: 1522
MITRE Tactic: Defense Evasion, Persistence, Privilege Escalation, Initial Access
Rule Description: T1078.001:Default Accounts
Common Event: AIE:T1078.001:Default Accounts
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 0
AIE Rule Additional Details
Tactic(s): Defense Evasion, Persistence, Privilege Escalation, Initial Access
Technique: Default Accounts
Rule Created: 7/19/2021
Rule Updated: N/A
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/001/
Notes:
Log Source Types:
LogRhythm AI Engine
Configuration:
This rule must be tuned before enabling. Populate the “MA: Default Accounts” list with a list of default accounts applicable to your company’s network, applications, services, etc.
Tuning:
This rule specifically looks for matches between AI Engine (AIE) Events and users or service accounts in the “MA: Default Accounts” list. This rule is considered a “Feedback” rule, meaning that another AIE rule evented containing the user listed in “MA: Default Accounts” list. The AIE rule that evented causing this feedback rule to event should be the focus area for tuning.
You may also tune this rule by creating an exception. If a number of exceptions are needed involving the same account, you may create two additional lists for user and host, then adding to the exceptions tab a rule to exclude the user list and the host list you created.
You may also leverage other similar lists already in your LogRhythm deployment. First, identify if the existing list is a good fit, and if so, add the list to the "MA: Default Accounts" list as a nested list.
AIE Rule
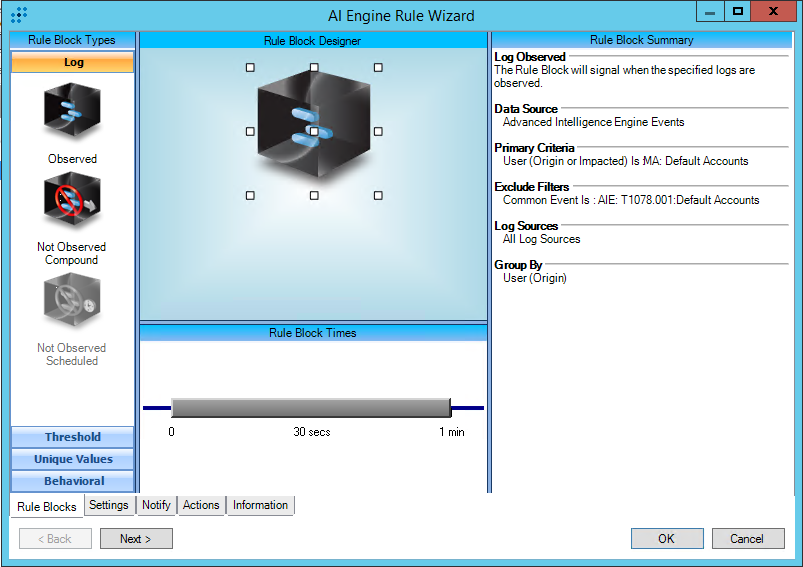
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/001/
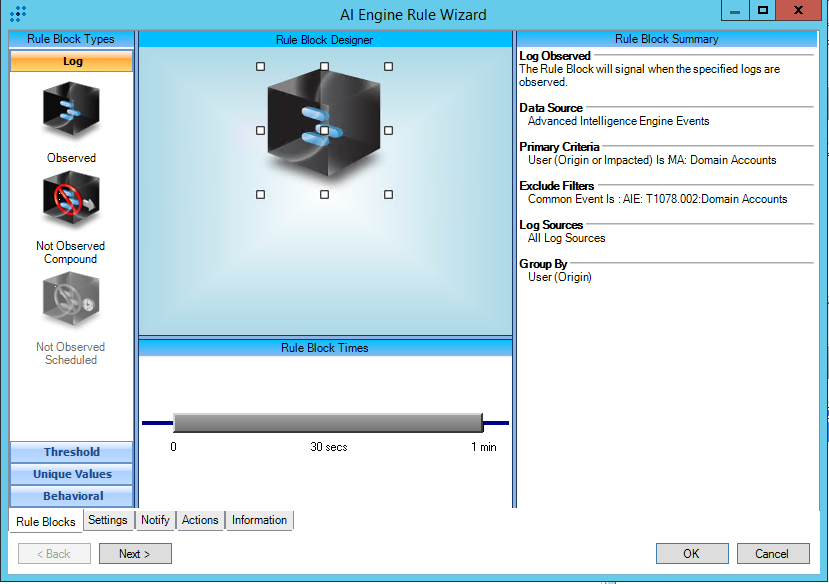
T1078.002:Domain Accounts
AIE Rule ID: 1523
MITRE Tactic: Defense Evasion, Persistence, Privilege Escalation, Initial Access
Rule Description: T1078.002:Domain Accounts
Common Event: AIE:T1078.002:Domain Accounts
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 0
AIE Rule Additional Details
Tactic(s): Defense Evasion, Persistence, Privilege Escalation, Initial Access
Technique: Local Accounts
Rule Created: 7/19/2021
Rule Updated: N/A
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/002/
Notes:
Log Source Types:
LogRhythm AI Engine
Configuration:
This rule must be tuned before enabling. Populate the “MA: Domain Accounts” list with a list of domain accounts applicable to your company’s network, applications, services, etc.
Tuning:
This rule specifically looks for matches between AI Engine (AIE) Events and users or service accounts in the “MA: Domain Accounts” list. This rule is considered a “Feedback” rule, meaning that another AIE rule evented containing the user listed in “MA: Domain Accounts” list. The AIE rule that evented causing this feedback rule to event should be the focus area for tuning.
You may also tune this rule by creating an exception. If a number of exceptions are needed involving the same account, you may create two additional lists for user and host, then adding to the exceptions tab a rule to exclude the user list and the host list you created.
You may also leverage other similar lists already in your LogRhythm deployment. First, identify if the existing list is a good fit, and if so, add the list to the "MA: Domain Accounts" list as a nested list. For example, if you have already populated "CCF: Default Account List", then you may want to add this list as a nested list to the "MA: Default Accounts" by opening the "MA: Default Accounts", clicking on the "List Items" tab, then clicking on "Add List...", and selecting the "CCF: Default Account List".
AIE Rule
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/002/
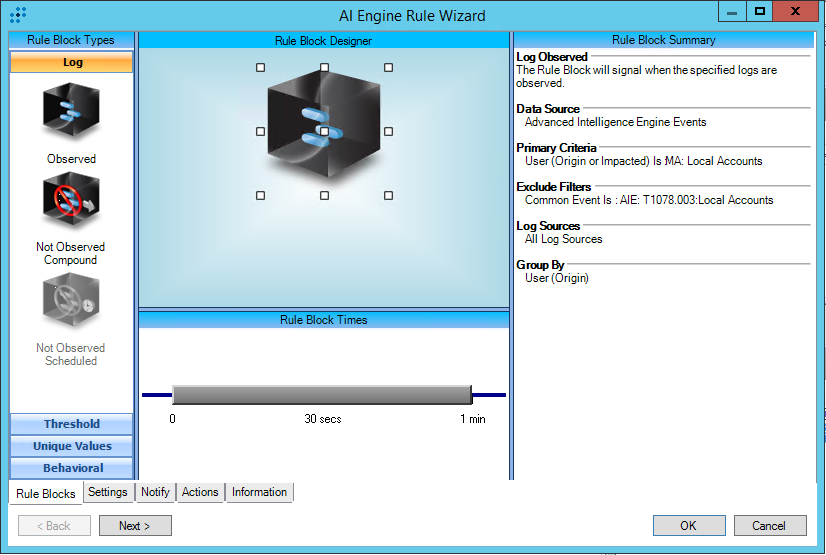
T1078.003:Local Accounts
AIE Rule ID: 1524
MITRE Tactic: Defense Evasion, Persistence, Privilege Escalation, Initial Access
Rule Description: T1078.003:Local Accounts
Common Event: AIE:T1078.003:Local Accounts
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 0
AIE Rule Additional Details
Tactic(s): Defense Evasion, Persistence, Privilege Escalation, Initial Access
Technique: Local Accounts
Rule Created: 7/19/2021
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/003/
Notes:
Log Source Types:
LogRhythm AI Engine
Configuration:
This rule must be tuned before enabling. Populate the “MA: Local Accounts” list with a list of local accounts applicable to your company’s network, applications, services, etc.
Tuning:
This rule specifically looks for matches between AI Engine (AIE) Events and users or service accounts in the “MA: Local Accounts” list. This rule is considered a “Feedback” rule, meaning that another AIE rule evented containing the user listed in “MA: Local Accounts” list. The AIE rule that evented causing this feedback rule to event should be the focus area for tuning.
You may also tune this rule by creating an exception. If a number of exceptions are needed involving the same account, you may create two additional lists for user and host, then adding to the exceptions tab a rule to exclude the user list and the host list you created.
You may also leverage other similar lists already in your LogRhythm deployment. First, identify if the existing list is a good fit, and if so, add the list to the "MA: Local Accounts" list as a nested list. For example, if you have already populated "CCF: Default Account List", then you may want to add this list as a nested list to the "MA: Default Accounts" by opening the "MA: Default Accounts", clicking on the "List Items" tab, then clicking on "Add List...", and selecting the "CCF: Default Account List".
AIE Rule
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/003/
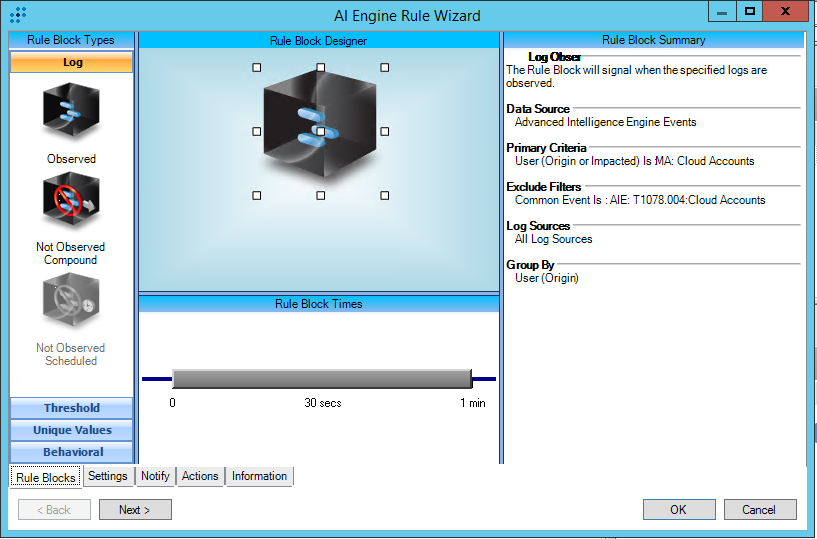
T1078.004:Cloud Accounts
AIE Rule ID: 1525
MITRE Tactic: Defense Evasion, Persistence, Privilege Escalation, Initial Access
Rule Description: T1078.004:Cloud Accounts
Common Event: AIE:T1078.004:Cloud Accounts
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 0
AIE Rule Additional Details
Tactic(s): Defense Evasion, Persistence, Privilege Escalation, Initial Access
Technique: Cloud Accounts
Rule Created: 7/19/2021
Rule Updated: N/A
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/004/
Notes:
Log Source Types:
LogRhythm AI Engine
Configuration:
This rule must be tuned before enabling. Populate the “MA: Cloud Accounts” list with a list of cloud accounts applicable to your company’s network, applications, services, etc.
Tuning:
This rule specifically looks for matches between AI Engine (AIE) Events and users or service accounts in the “MA: Cloud Accounts” list. This rule is considered a “Feedback” rule, meaning that another AIE rule evented containing the user listed in “MA: Cloud Accounts” list. The AIE rule that evented causing this feedback rule to event should be the focus area for tuning.
You may also tune this rule by creating an exception. If a number of exceptions are needed involving the same account, you may create two additional lists for user and host, then adding to the exceptions tab a rule to exclude the user list and the host list you created.
You may also leverage similar other lists already in your LogRhythm deployment. First, identify if the existing list is a good fit, and if so, add the list to the "MA: Cloud Accounts" list as a nested list. For example, if you have already populated "CCF: Default Account List", then you may want to add this list as a nested list to the "MA: Default Accounts" by opening the "MA: Default Accounts", clicking on the "List Items" tab, then clicking on "Add List...", and selecting the "CCF: Default Account List".
AIE Rule
For further guidance on this Tactic: Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1078/004/
T1606.002:SAML Tokens:O365 and ADFS
AIE Rule ID: 1526
MITRE Tactic: Credential Access
Rule Description: T1606.002:SAML Tokens:O365 and ADFS
Common Event: AIE:T1606.002:SAML Tokens:O365 and ADFS
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Credential Access
Technique: SAML Tokens
Rule Created: 2/24/2021
Rule Updated: N/A
For further guidance on this Tactic: Technique, visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1606/002/
Notes:
Log Source Types:
API - Office 365 Management Activity or Syslog - Open Collector - Azure Event Hub
Microsoft Windows Event Logging XML - Security
Configuration:
LogRhythm TrueIdentity must be configured and the users monitored must have identities defined, including their User Principal Name (user@domain.com) and their AD logon (user).
For more information about LogRhythm TrueIdentity, see TrueIdentity.
ADFS auditing must be enabled: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-logging
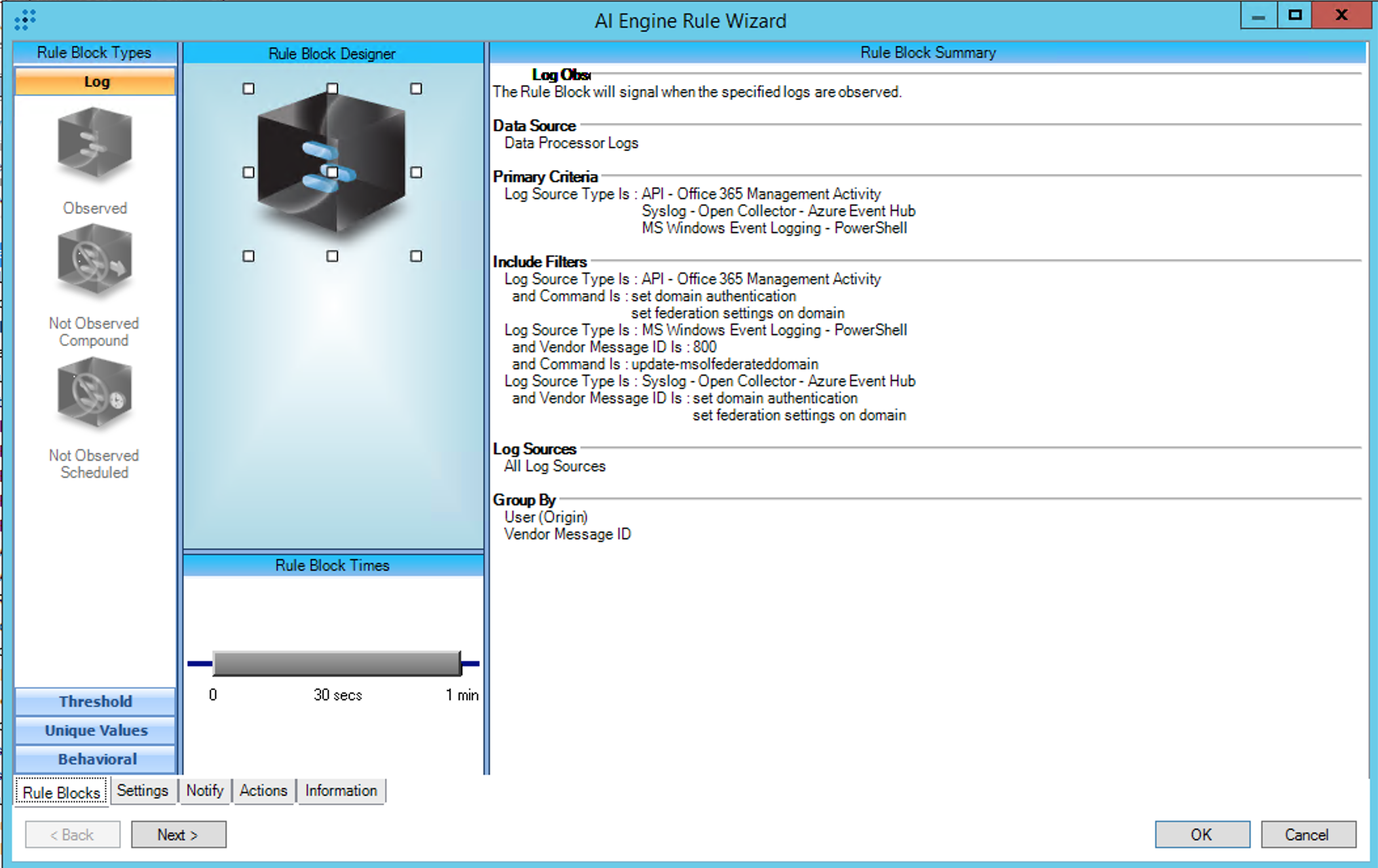
AIE Rule
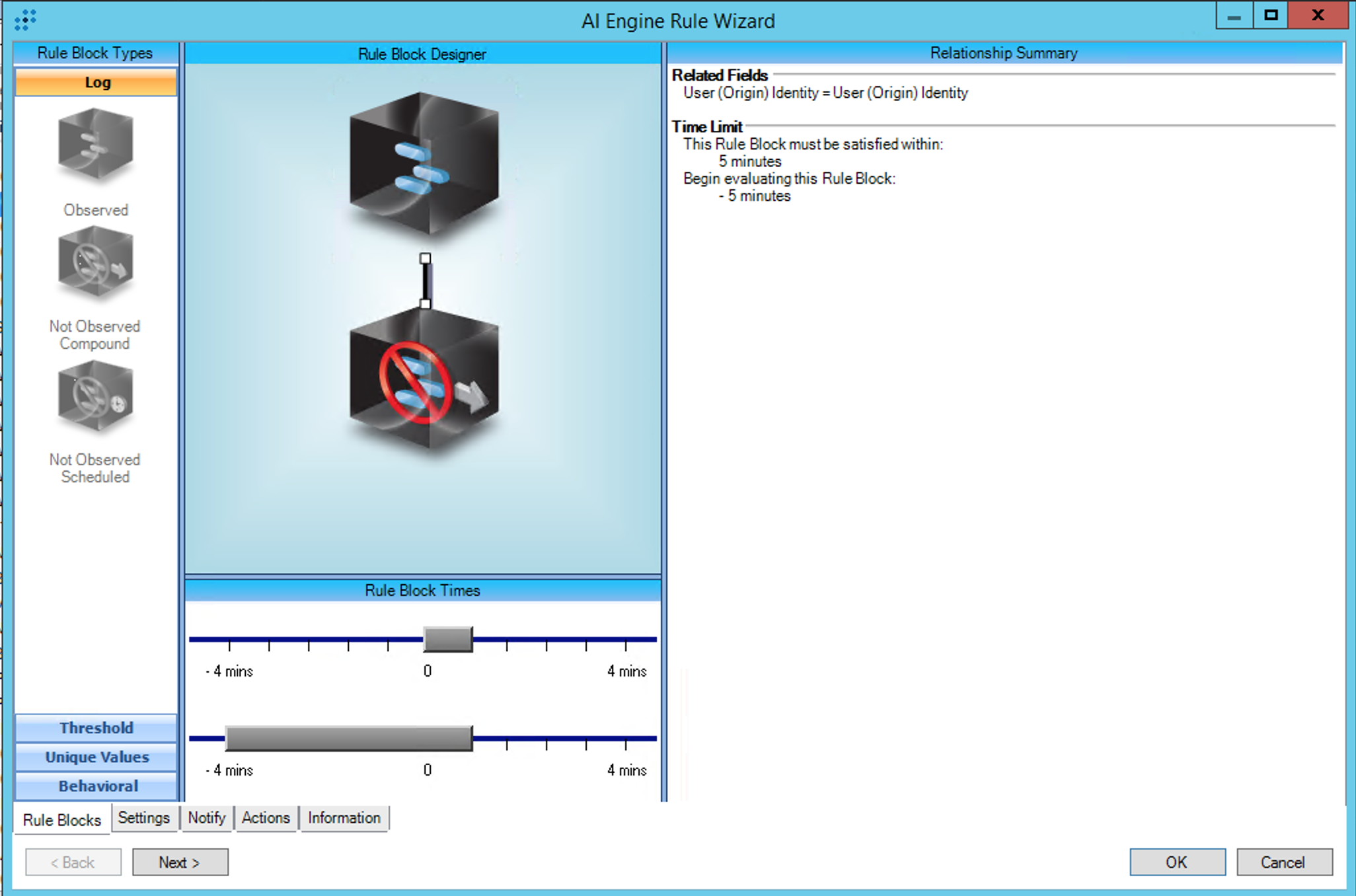
For further guidance on this Tactic: Technique, visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1606/002/
T1606.002:SAML Tokens:O365 and ADFS
AIE Rule ID: 1527
MITRE Tactic: Defense Evasion, Privilege Escalation
Rule Description: T1484.002:Domain Trust Modification
Common Event: AIE:T1484.002:Domain Trust Modification
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 2
AIE Rule Additional Details
Tactic(s): Defense Evasion, Privilege Escalation
Technique: Domain Trust Modification
Rule Created: 3/11/2021
For further guidance on this Tactic: Technique, visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1484/002/
Notes:
Log Source Types:
API - Office 365 Management Activity
Syslog - Open Collector - Azure Event Hub
MS Windows Event Logging - PowerShell
Configuration:
PowerShell Module Logging must be enabled in order for the PowerShell criteria to be met: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_group_policy_settings
Collect Azure AD logs either through the API - Office 365 Management Activity log source type (https://docs.logrhythm.com/docs/devices/api-log-sources/api-office-365-management-activity-microsoft) or the Syslog - Open Collector - Azure Event Hub log source type (https://docs.logrhythm.com/docs/OCbeats/azure-event-hubs-beat-6-0-2).
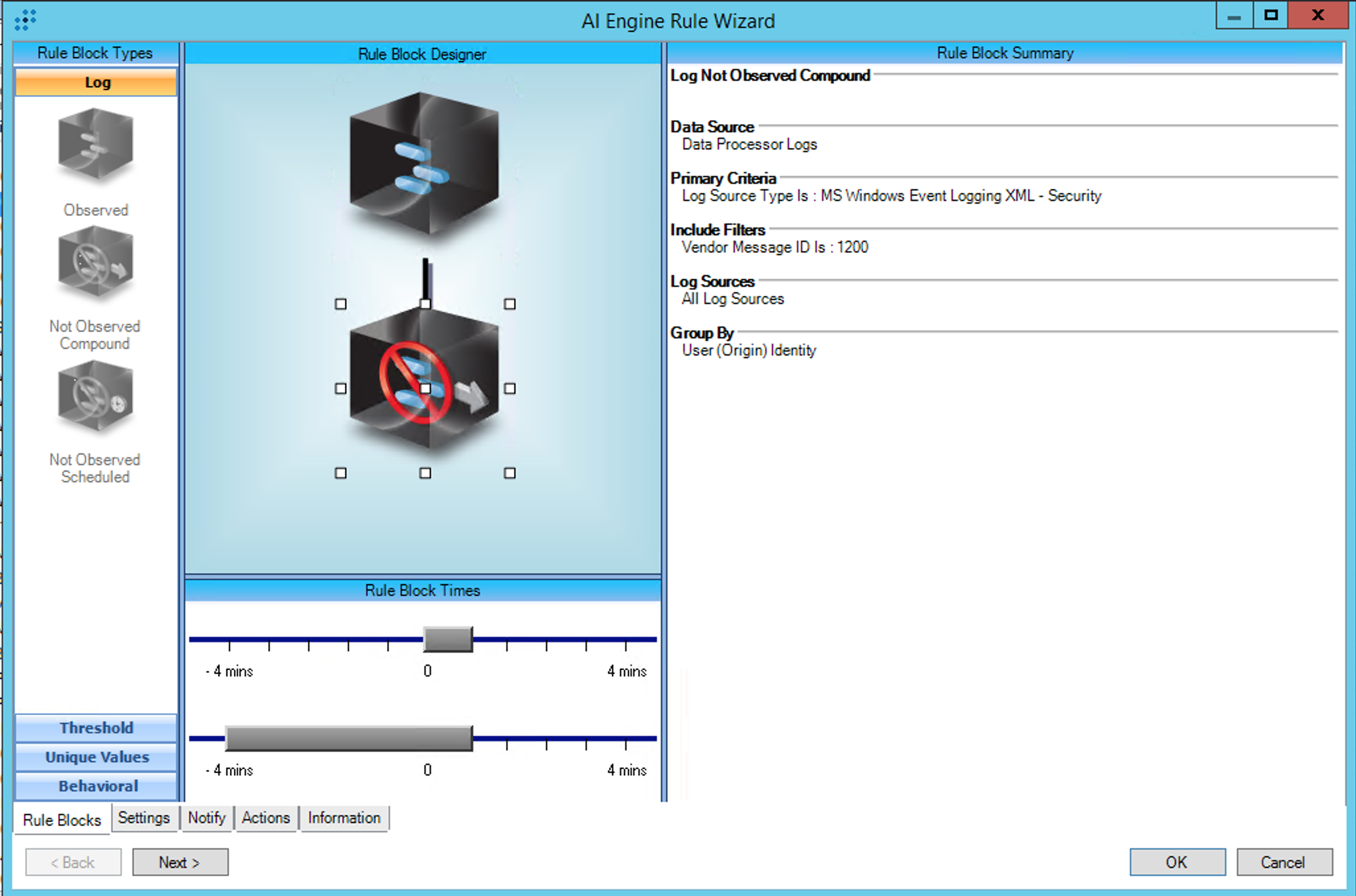
AIE Rule
For further guidance on this Tactic: Technique, visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1484/002/
T1552.004:Private Keys
AIE Rule ID: 1540
MITRE Tactic: Credential Access
Rule Description: T1552.004:Private Keys
Common Event: AIE:T1552.004:Private Keys
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 3
AIE Rule Additional Details
Tactic(s): Credential Access
Technique: Unsecured Credentials: Private Keys
Rule Created: 03/18/2021
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1552/004/
Note: Additional exclusions may need to be made for processes that legitimately use the "\microsoft##wid\tsql\query" named pipe .
AIE Rule
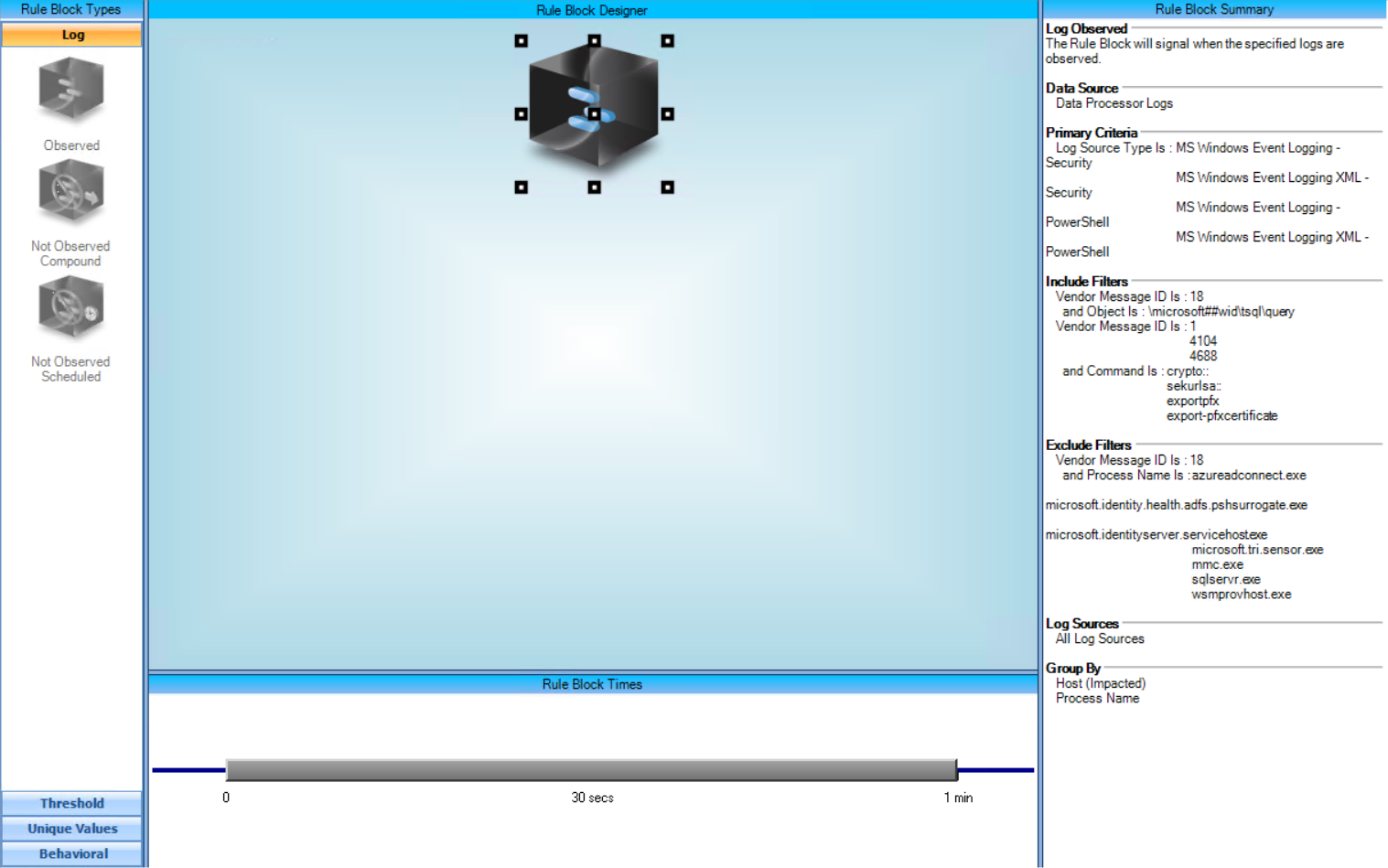
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1552/004/
T1489:Service Stop
AIE Rule ID: 1541
MITRE Tactic: Impact
Rule Description: T1489:Service Stop
Common Event: AIE:T1489:Service Stop
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic(s): Impact
Technique: Service Stop
Rule Created: 09/13/2021
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1489/
AIE Rule
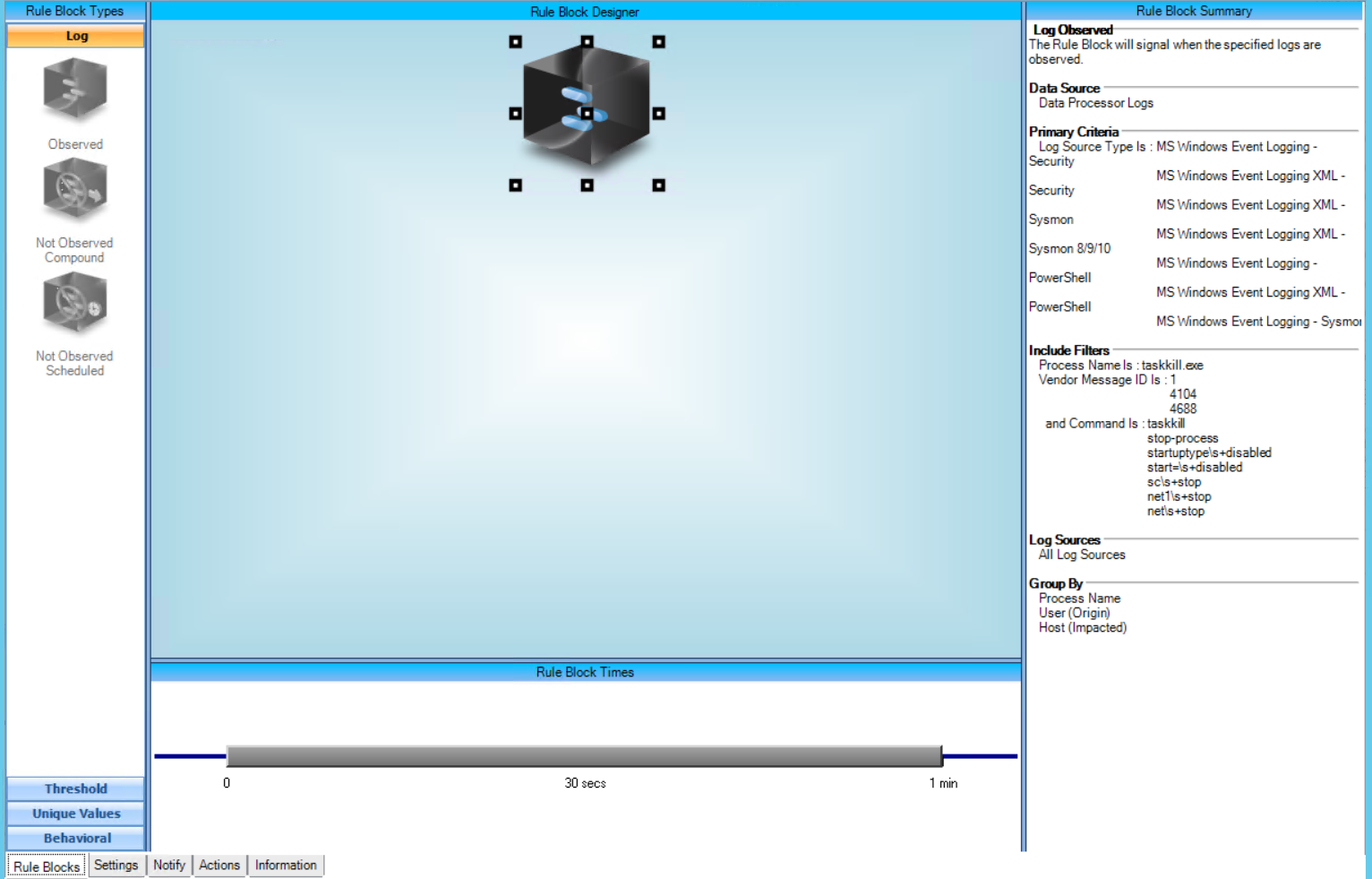
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1489/
T1059.003:Windows Command Shell
AIE Rule ID: 1542
MITRE Tactic: Execution
Rule Description: T1059.003:Windows Command Shell
Common Event: AIE:T1059.003:Windows Command Shell
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details
Tactic(s): Execution
Technique: Windows Command Shell
Rule Created: 08/02/2021
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1059/003/
AIE Rule
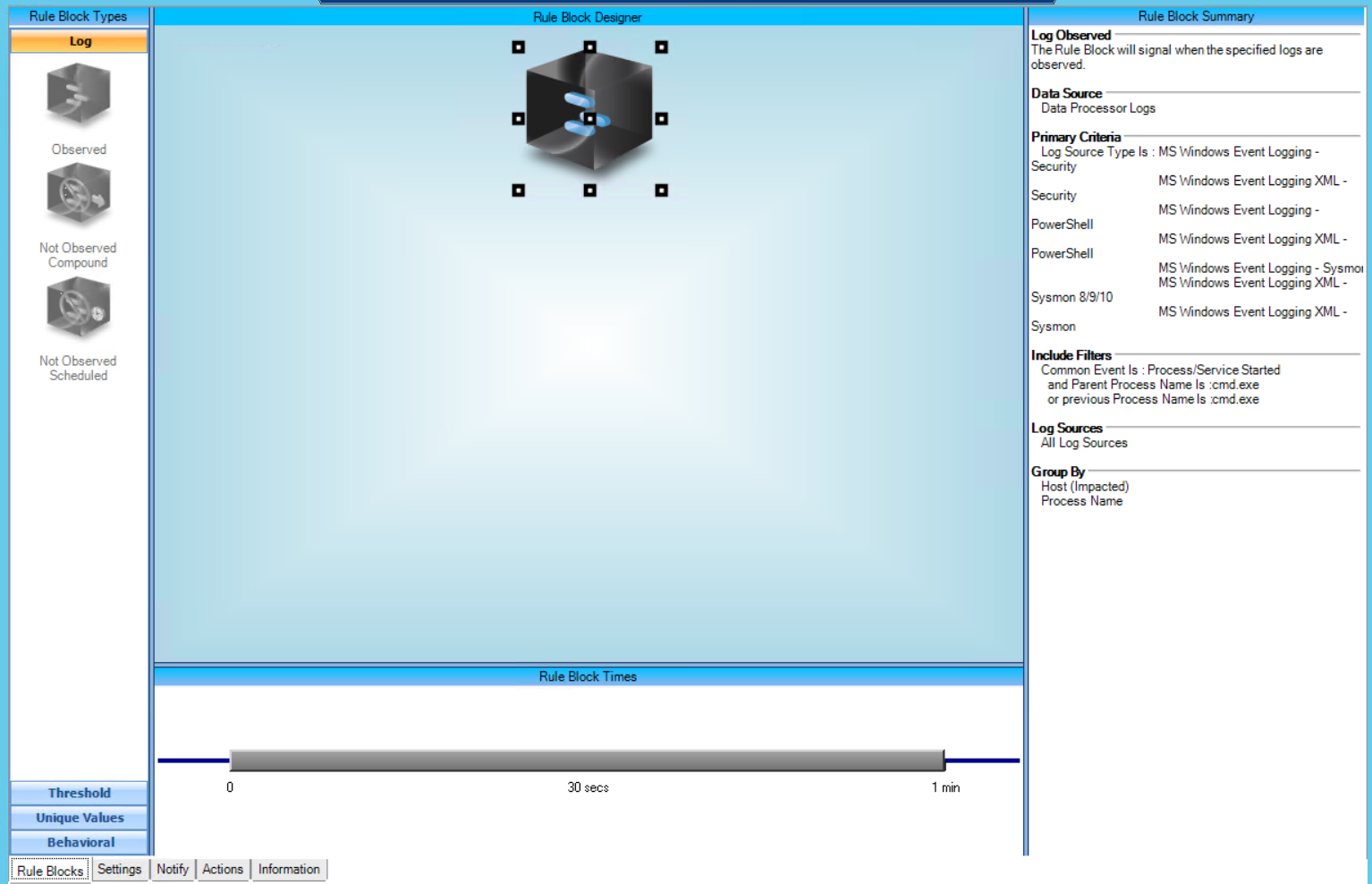
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1059/003/
T1490:Inhibit System Recovery
AIE Rule ID: 1544
MITRE Tactic: Impact
Rule Description: T1490:Inhibit System Recovery
Common Event: AIE:T1490:Inhibit System Recovery
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 1
AIE Rule Additional Details
Tactic(s): Impact
Technique: Inhibit System Recovery
Rule Created: 2/4/2019
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1490/
AIE Rule
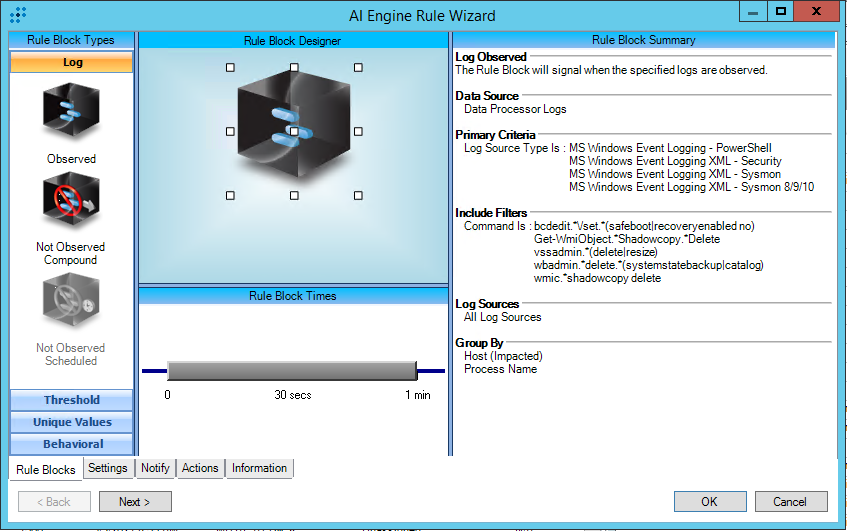
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1490/
T1562.001:Disable or Modify Tools:Windows Defender
AIE Rule ID: 1545
MITRE Tactic: Defense Evasion
Rule Description: T1562.001:Disable or Modify Tools:Windows Defender
Common Event: AIE:T1562.001:Disable or Modify Tools:Windows Defender
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Defense Evasion
Technique:Disable or Modify Tools
Rule Created: 11/15/2021
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1562/001
Notes:
Log Source Types:
Microsoft Windows Event Logging XML - Security
Microsoft Windows Event Logging - PowerShell
Microsoft Windows Event Logging XML - Sysmon
Microsoft Windows Event Logging XML - Windows Defender
Configuration:
This rule detects attempts to stop, disable or reconfigure Windows Defender in order to evade detection.
PowerShell module and script block logging must be enabled. Configuration steps can be found in the Logging and Monitoring Configuration section of the MITRE ATT&CK® Module Deployment Guide at https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Process and command line monitoring logs can be gathered via the Microsoft Windows Event Logging XML - Security or Microsoft Windows Event Logging XML - Sysmon. Configuration steps can be found in the Logging and Monitoring Configuration section of the MITRE ATT&CK® Module Deployment Guide at https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Tuning:
If alarming will be turned on for this rule it is recommended to enable the following AIE Summary Fields in the rule block so that more context is provided with the alarm:
Command
Common Event
Host(Impacted)
Host(Origin)
MPE Rule Name
Reason
Subject
Threat Name
User (Origin)
AIE Rule
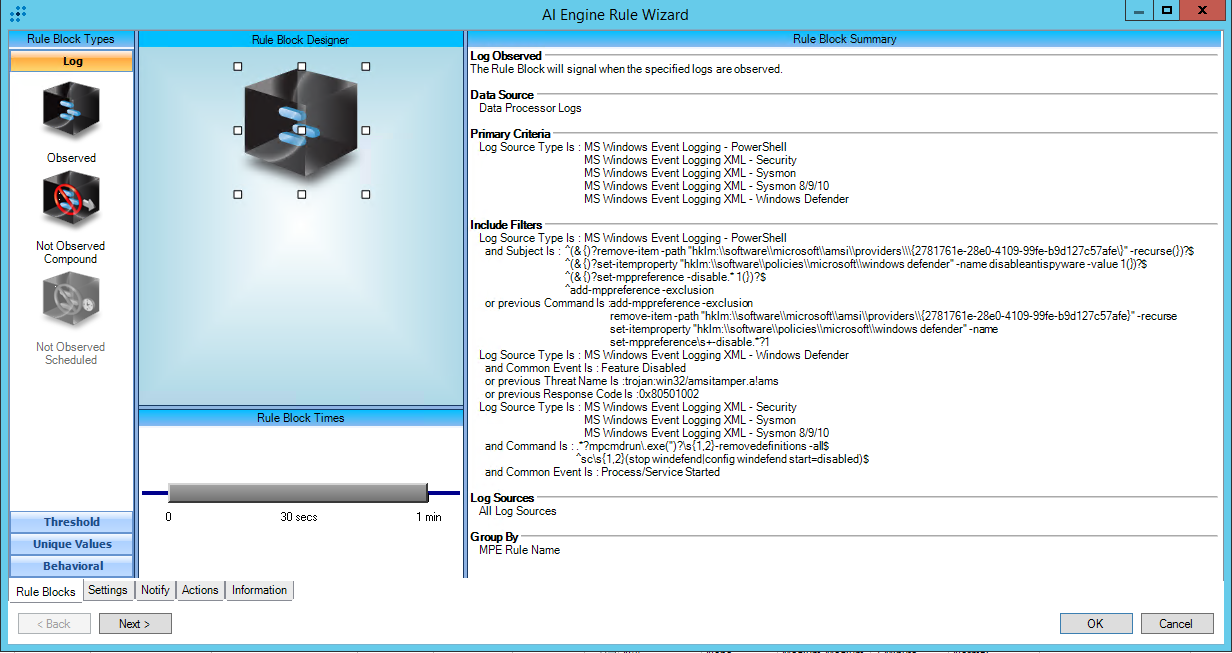
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1562/001
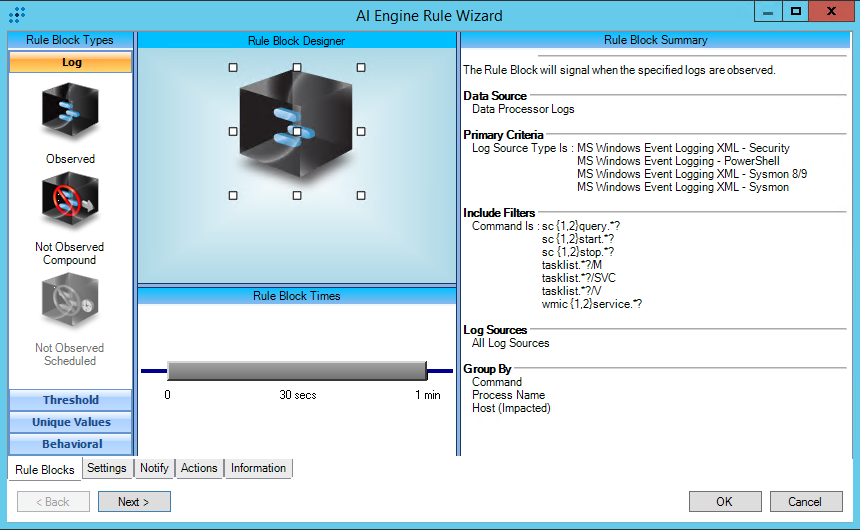
T1106:Native API
AIE Rule ID: 1546
MITRE Tactic: Execution
Rule Description: T1106:Native API
Common Event: AIE:T1106:Native API
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 6
AIE Rule Additional Details
Tactic(s): Execution
Technique: Native API
Rule Created: 12/07/2021
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1106/
Notes:
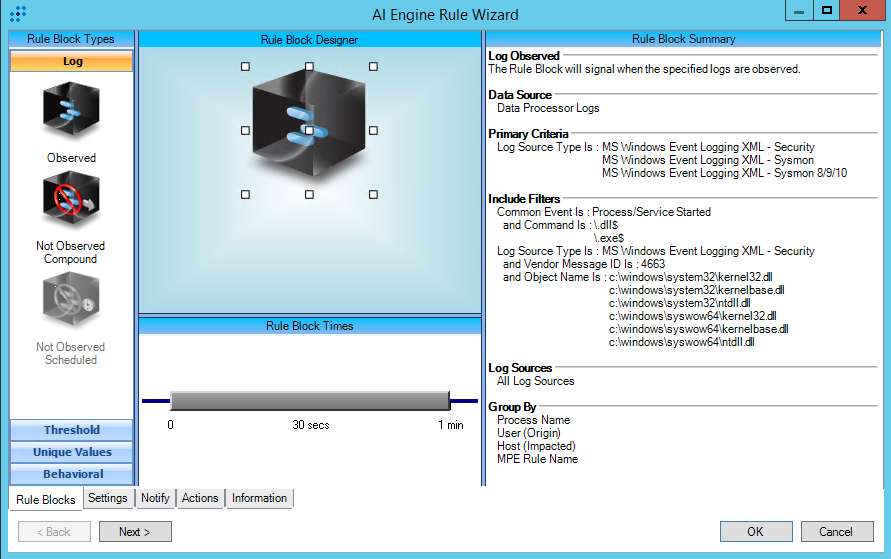
This rule contains two different observations. One is primarily looking for processes started (Common Event: Process/Service Started) with command line auditing enabled, and an indicator that the process was started by an API call by evidence of the Command field being populated with the process name without quotes, and without arguments. The other is primarily looking for files being accessed (Common Event: Object Accessed) when “Read data/traverse directory” file auditing is enabled and where Kernel32, Kernelbase, or NTDll are involved indicating that an API call was made to the file.
Log Source Types:
MS Windows Event Logging XML - Security
MS Windows Event Logging XML - Sysmon
MS Windows Event Logging XML - Sysmon 8/9/10
Configuration:
Please refer to the configuration guidance section in the “MITRE ATT&CK® Deployment Guide – Import and Synchronize the Module”.
Tuning:
To reduce the frequency of events of known Windows API calls that are part of normal operations, you may do one or more of the following:
• Common Event: Process/Service Started: Determine if the process involved is “Known good” by verifying the hash against a popular known malware database. If known good, you may wish to exclude the following from the rule: User Origin, Process Name, and Host Impacted.
• Common Event: Object Accessed: First, determine if the process involved is “Known good” by verifying the hash against a popular known malware database. Next, verify the User Origin involved is “System” (either “System” or computer name ending in “$”). If both are known good, you may wish to exclude the following from the rule: User Origin, Process Name, and Object Name.
AIE Rule
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1106/
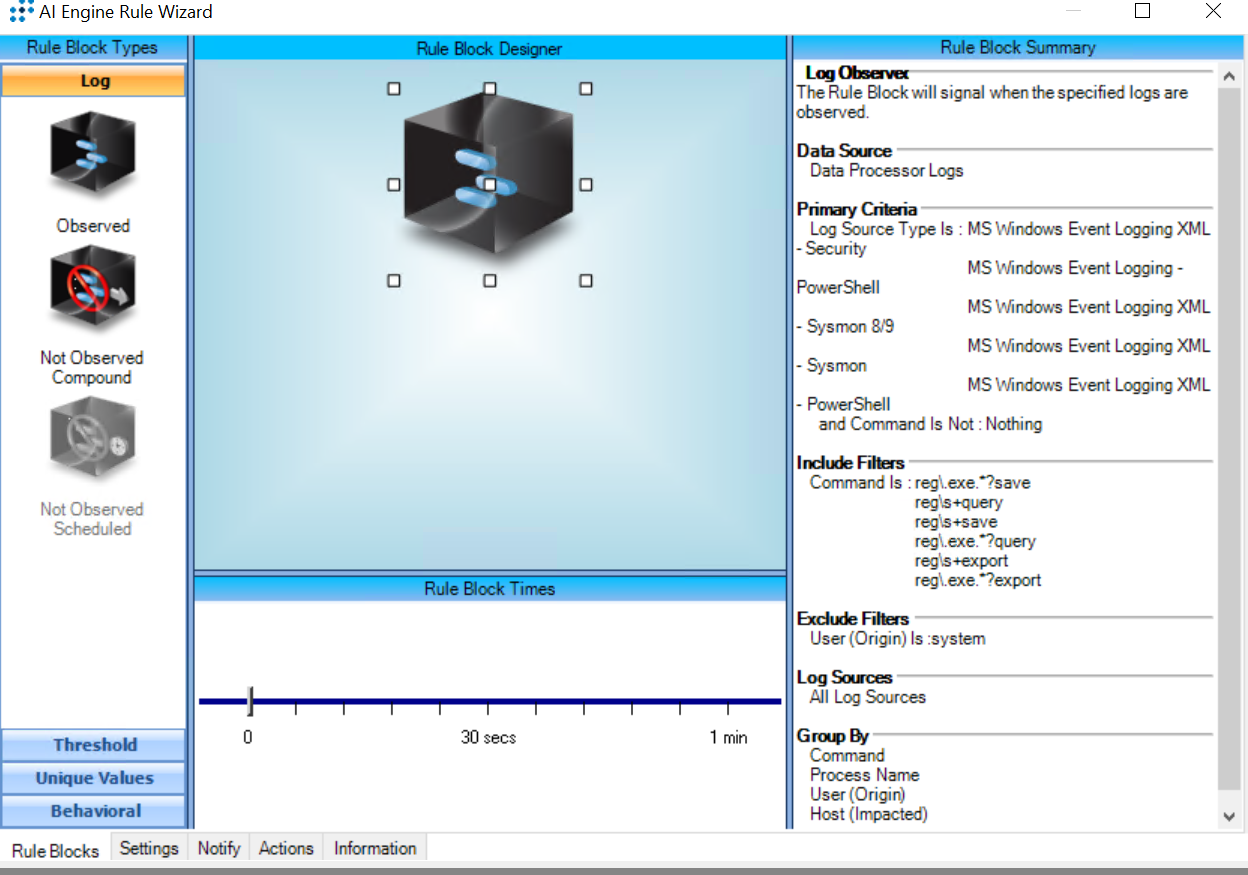
T1027:Obfuscated Files or Information
AIE Rule ID: 1547
MITRE Tactic: Defense Evasion
Rule Description: T1027:Obfuscated Files or Information
Common Event: AIE:T1027:Obfuscated Files or Information
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Defense Evasion
Technique: Obfuscated Files or Information
Rule Created: 1/21/2021
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1027/
Notes:
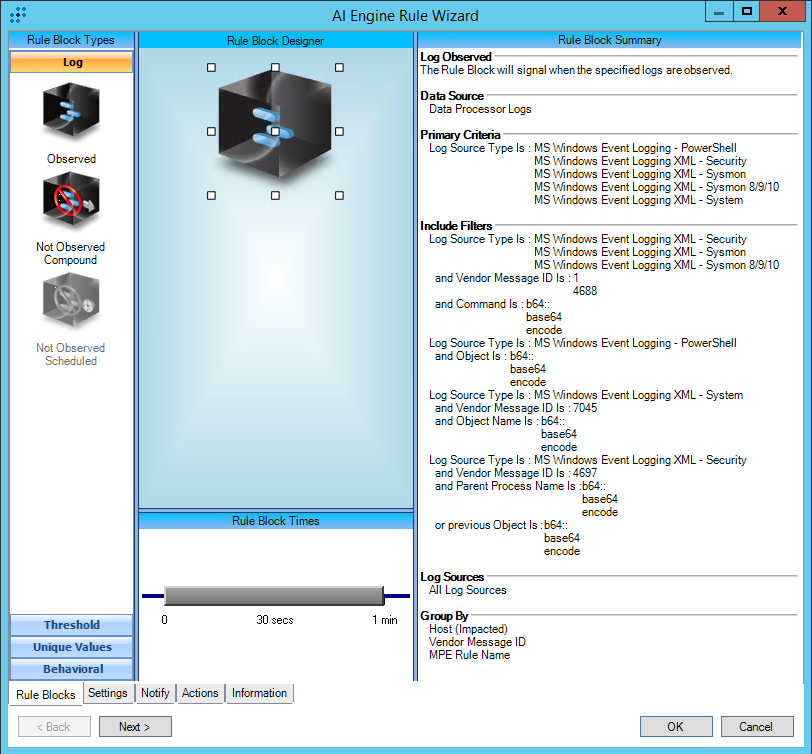
This rule is primarily evaluating the presence of base64 encoding.
Log Source Types:
MS Windows Event Logging - PowerShell
MS Windows Event Logging XML - Security
MS Windows Event Logging XML - Sysmon
MS Windows Event Logging XML - Sysmon 8/9/10
MS Windows Event Logging XML – System
Configuration:
Please refer to the configuration guidance section in the “MITRE ATT&CK® Deployment Guide – Import and Synchronize the Module”.
Tuning:
To reduce the frequency of events of known obfuscation (base64) that are part of normal operations, you may exclude based on:
• Common Event: Process/Service Started: Determine if the process involved is “Known good” by verifying the hash against a popular known malware database. If known good, you may wish to exclude the following from the rule: User Origin, Process Name, Parent Process Name, and Host Impacted.
AIE Rule
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1027/
T1059.001:PowerShell:ProviderLifeCycle
AIE Rule ID: 1548
MITRE Tactic: Execution
Rule Description: T1059.001:PowerShell:ProviderLifeCycle
Common Event: AIE:T1059.001:PowerShell:ProviderLifeCycle
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details
Tactic(s): Execution
Technique: PowerShell
Rule Created: 1/26/2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1059/001/
Log Source Types:
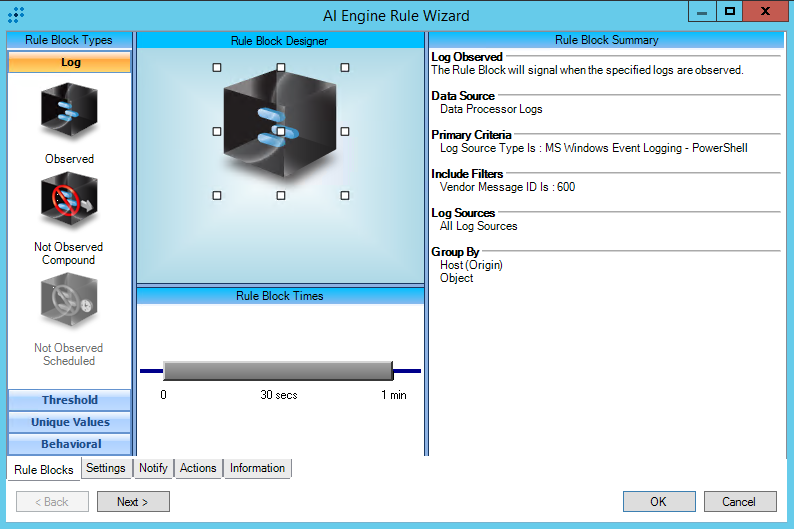
MS Windows Event Logging - PowerShell
Configuration:
PowerShell Audit logging must be enabled and the Windows PowerShell channel in the Windows Event Log must be collected. Please see the section titled "Configure PowerShell Logging" in the MITRE ATT&CK Deployment Guide for more information: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Tuning:
It is not recommended to set this rule to alarm as it is triggered by the use of PowerShell on an endpoint. Potential tuning approaches include creating an include filter containing a list of endpoints that should rarely, if ever, run PowerShell.
AIE Rule
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1059/001/
T1621:MFA Request Generation:Okta Push from Non-Whitelisted Location
AIE Rule ID: 1550
MITRE Tactic: Credential Access
Rule Description: T1621:MFA Request Generation:Okta Push from Non-Whitelisted Location
Common Event: AIE:T1621:MFARequest:OktaPushBadLocation
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 2
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Multi-Factor Authentication Request Generation:Okta Push from Non-Whitelisted Location
Rule Created: 8 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
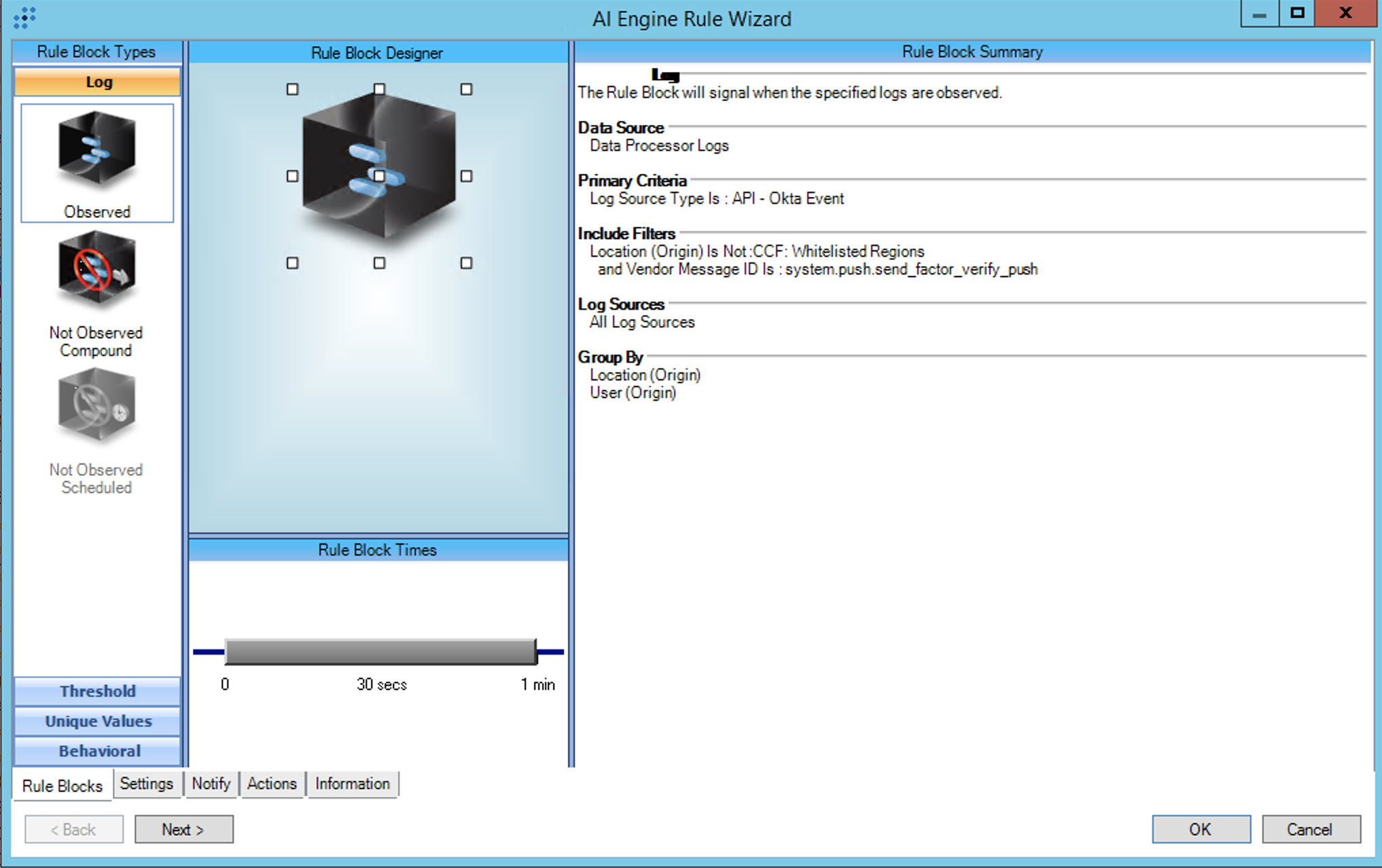
Log Source Types:
API - Okta Event. Note that this rule is speciifc to logs from the Okta Classic Engine product. If your deployment includes other Okta MFA products such as Okta Indentity Engine you may need to adjust the criteria accordingly.
Configuration:
This rule depends on the CCF: Whitelisted Regions list included with the Consolidated Compliance Framework (CCF) Module (https://docs.logrhythm.com/docs/kb/compliance/consolidated-compliance-framework-ccf-module). If necessary, enable this module in your LogRhythm deployment and populate the list with approved regions. If it is not desired to use the CCF Module, clone the rule and create a custom list for approved regions.
Tuning:
No tuning required.
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
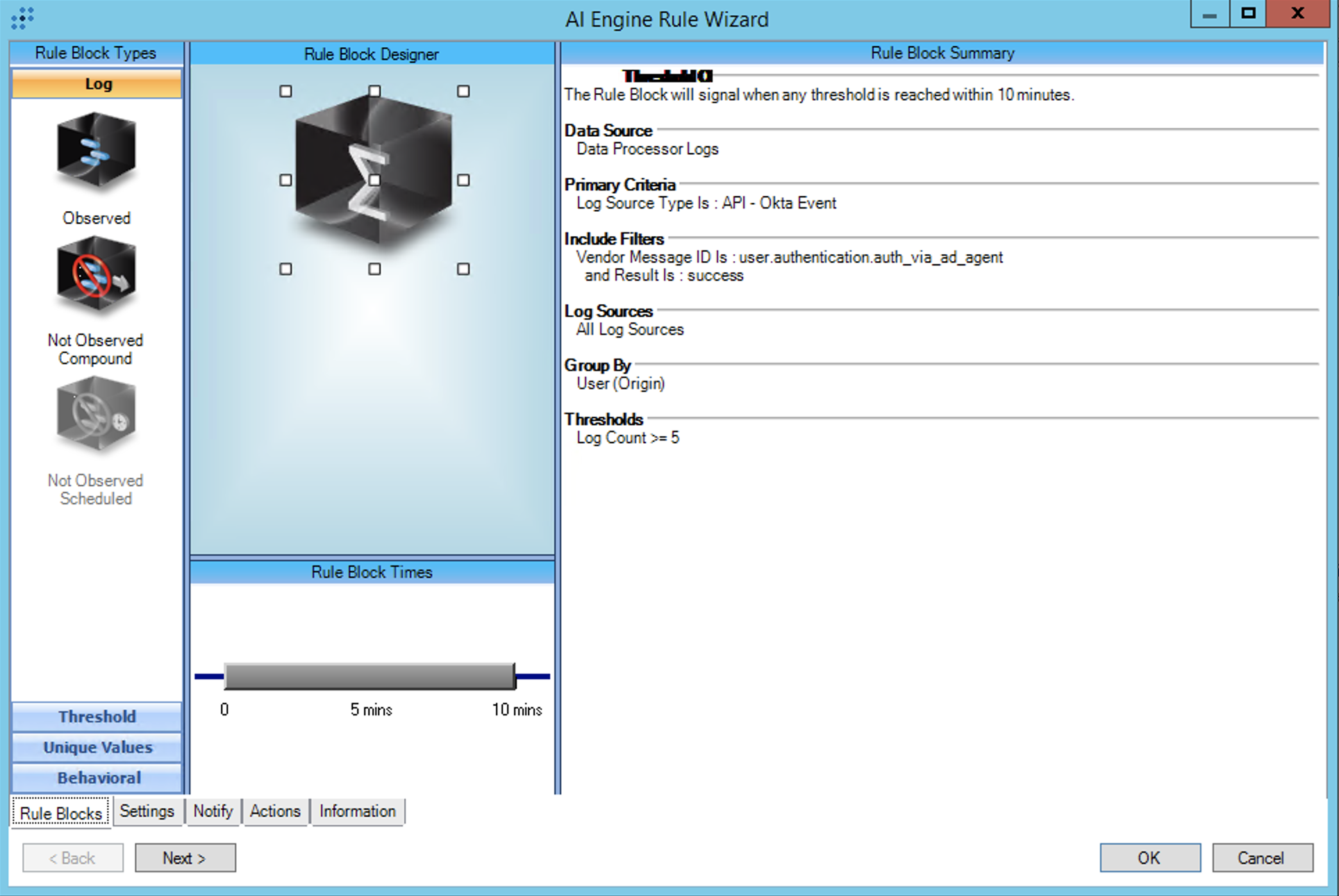
T1621:MFA Request Generation:Rapid Okta AD Authentication Success
AIE Rule ID: 1551
MITRE Tactic: Credential Access
Rule Description: T1621:MFA Request Generation:Rapid Okta AD Authentication Success
Common Event: AIE:T1621:MFARequest:RapidOktaADAuthSuccess
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 2
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Multi-Factor Authentication Request Generation:Rapid Okta AD Authentication Success
Rule Created: 8 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
Log Source Types:
API - Okta Event
Configuration:
Note that threshold adjustments may be overwritten depending on your KB advanced synchronization setting. This rule can be cloned to avoid having the threshold overwritten.
Tuning:
Investigate your environment to determine the normal authentication success rate per-user and adjust the threshold if it exceeds 5 per 10 minutes.
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
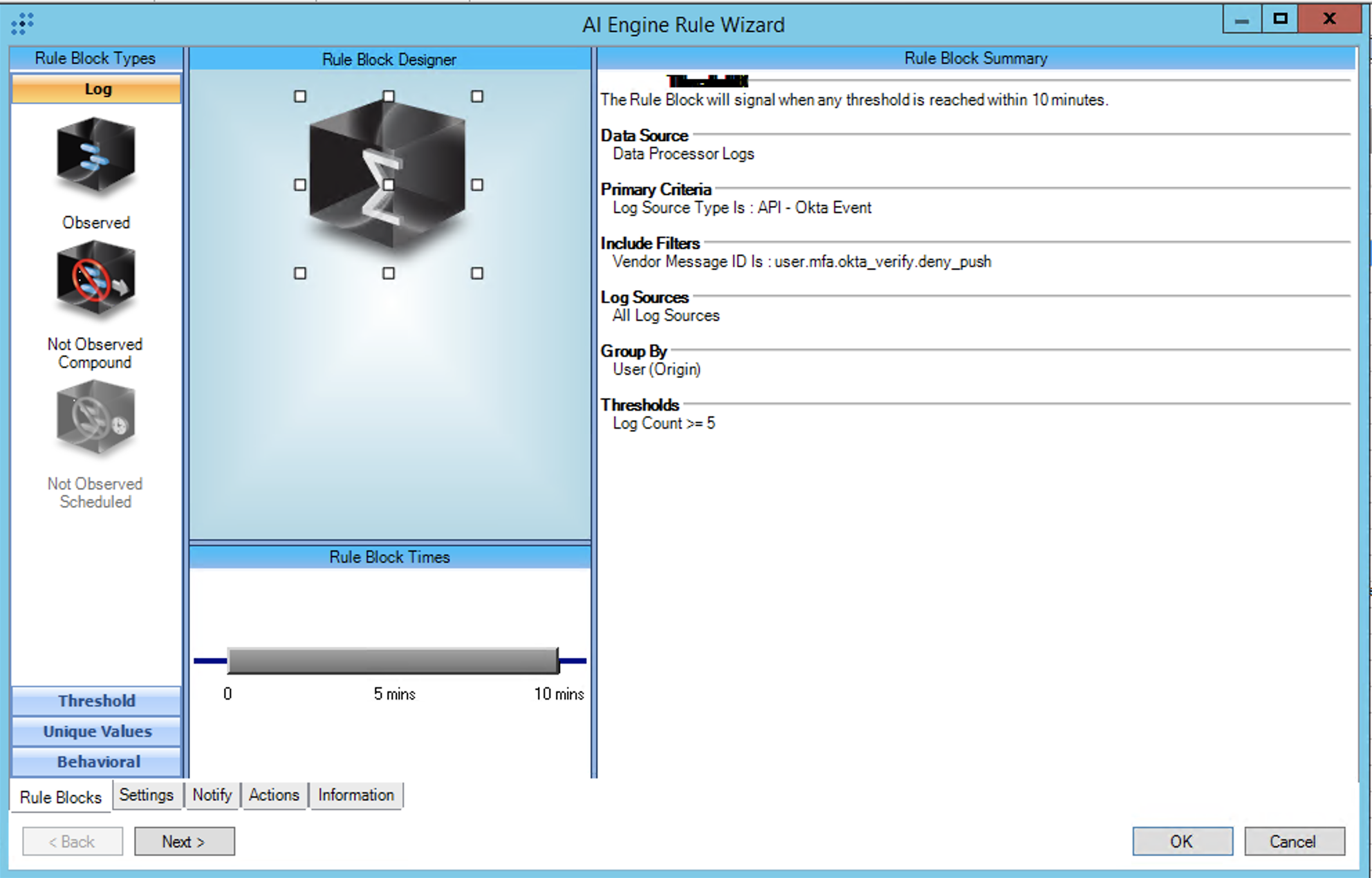
T1621:MFA Request Generation:Repeated OKTA Push Denies
AIE Rule ID: 1552
MITRE Tactic: Credential Access
Rule Description: T1621:MFA Request Generation:Repeated OKTA Push Denies
Common Event: AIE:T1621:MFARequest:RepeatOKTAPushDeny
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 1
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Multi-Factor Authentication Request Generation:Repeated OKTA Push Denies
Rule Created: 8 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
Log Source Types:
API - Okta Event
Configuration:
Note that threshold adjustments may be overwritten depending on your KB advanced synchronization setting. This rule can be cloned to avoid having the threshold overwritten.
Tuning:
Investigate your environment to determine the normal push deny rate per-user and adjust the threshold if it exceeds 5 per 10 minutes.
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
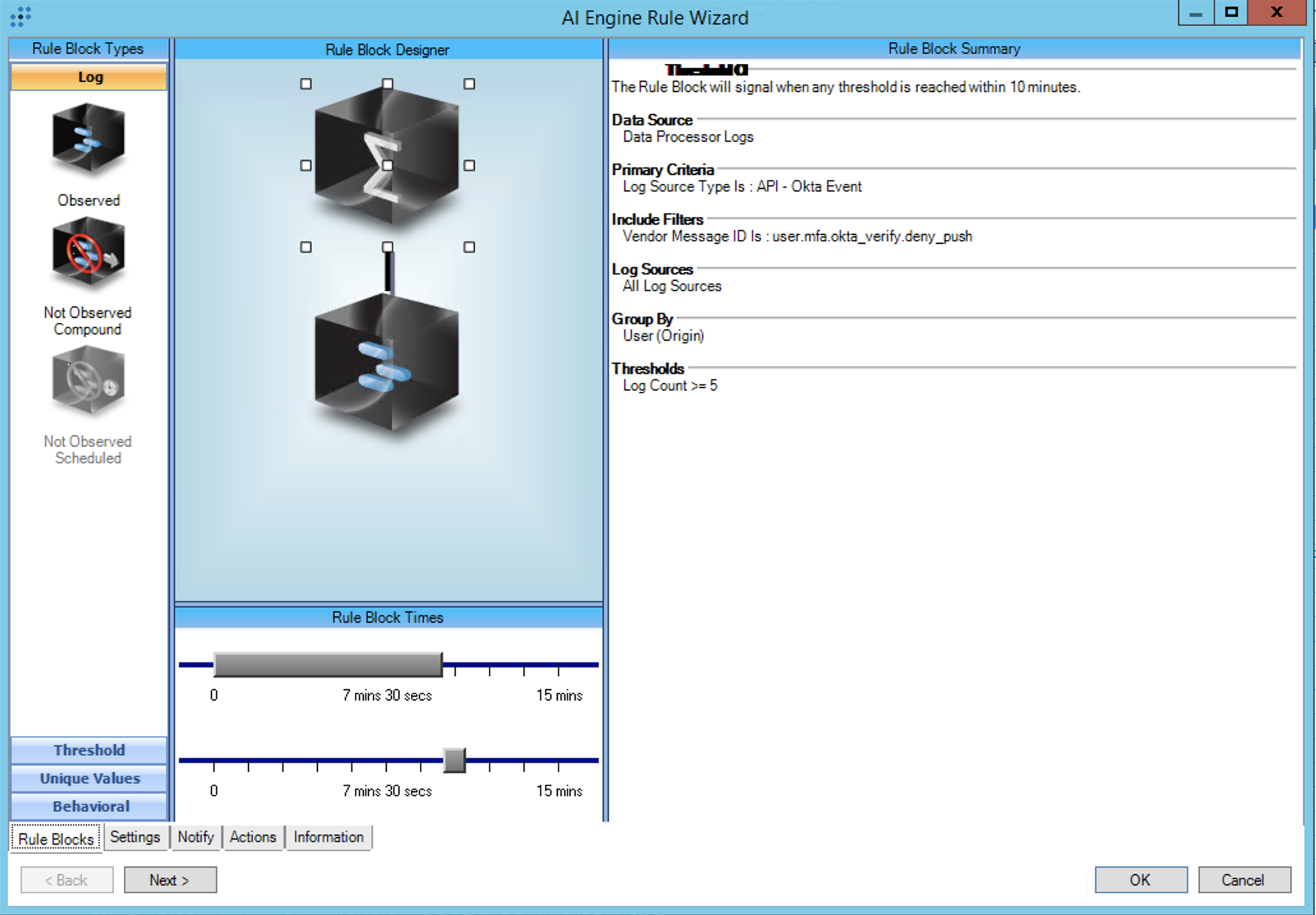
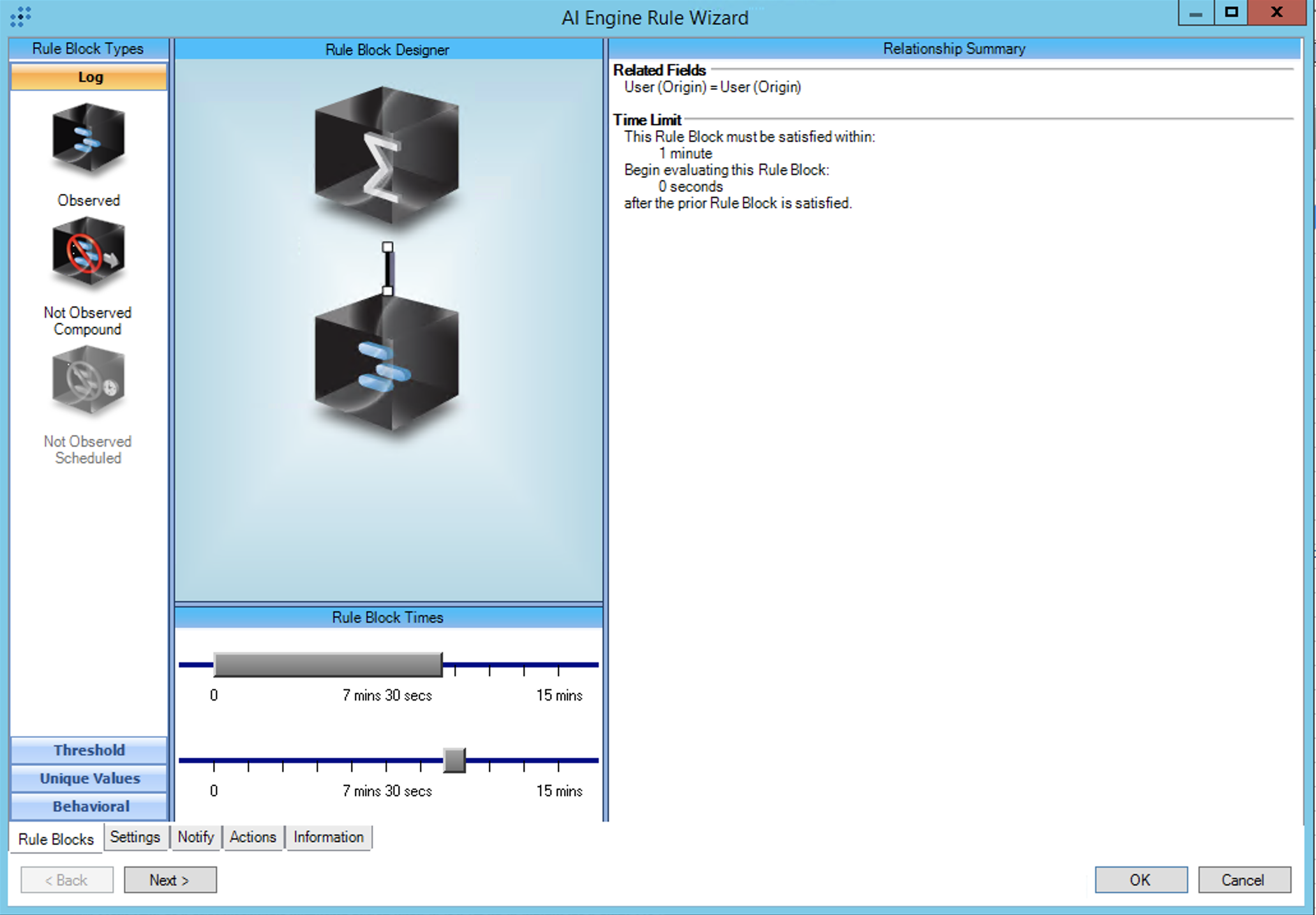
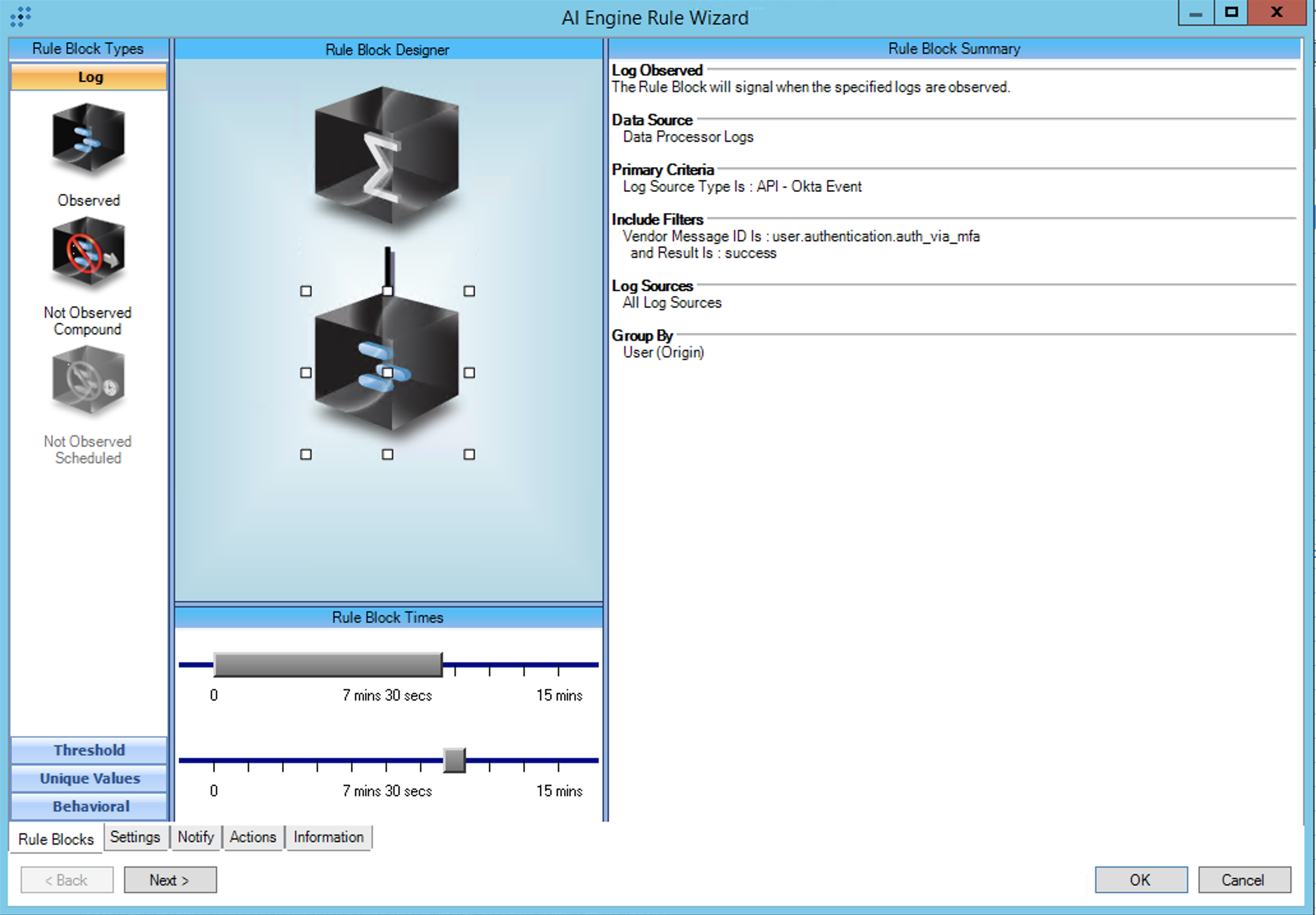
T1621:MFA Request Generation:Repeated OKTA Push Denies then Allow
AIE Rule ID: 1553
MITRE Tactic: Credential Access
Rule Description: T1621:MFA Request Generation:Repeated OKTA Push Denies then Allow
Common Event: AIE:T1621:MFARequest:RepeatOKTAPushDenyAndAllow
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 2
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Multi-Factor Authentication Request Generation:Repeated OKTA Push Denies
Rule Created: 8 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
Log Source Types:
API - Okta Event
Configuration:
Note that threshold adjustments may be overwritten depending on your KB advanced synchronization setting. This rule can be cloned to avoid having the threshold overwritten.
Tuning:
Investigate your environment to determine the normal push deny rate per-user and adjust the threshold if it exceeds 5 per 10 minutes.
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1621/
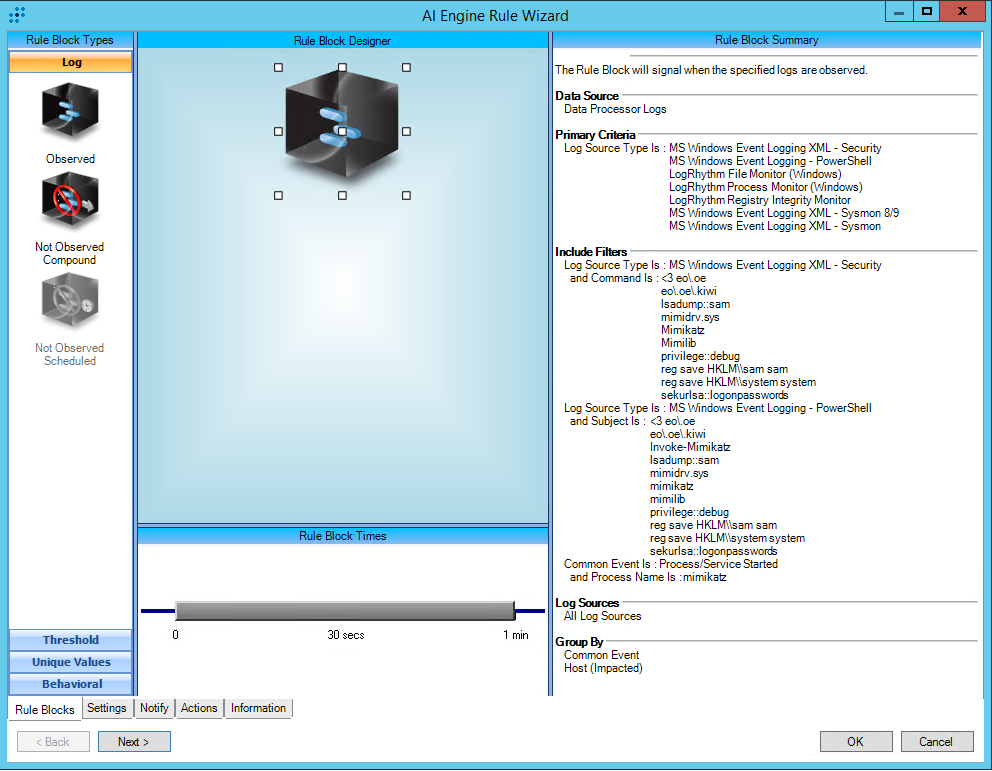
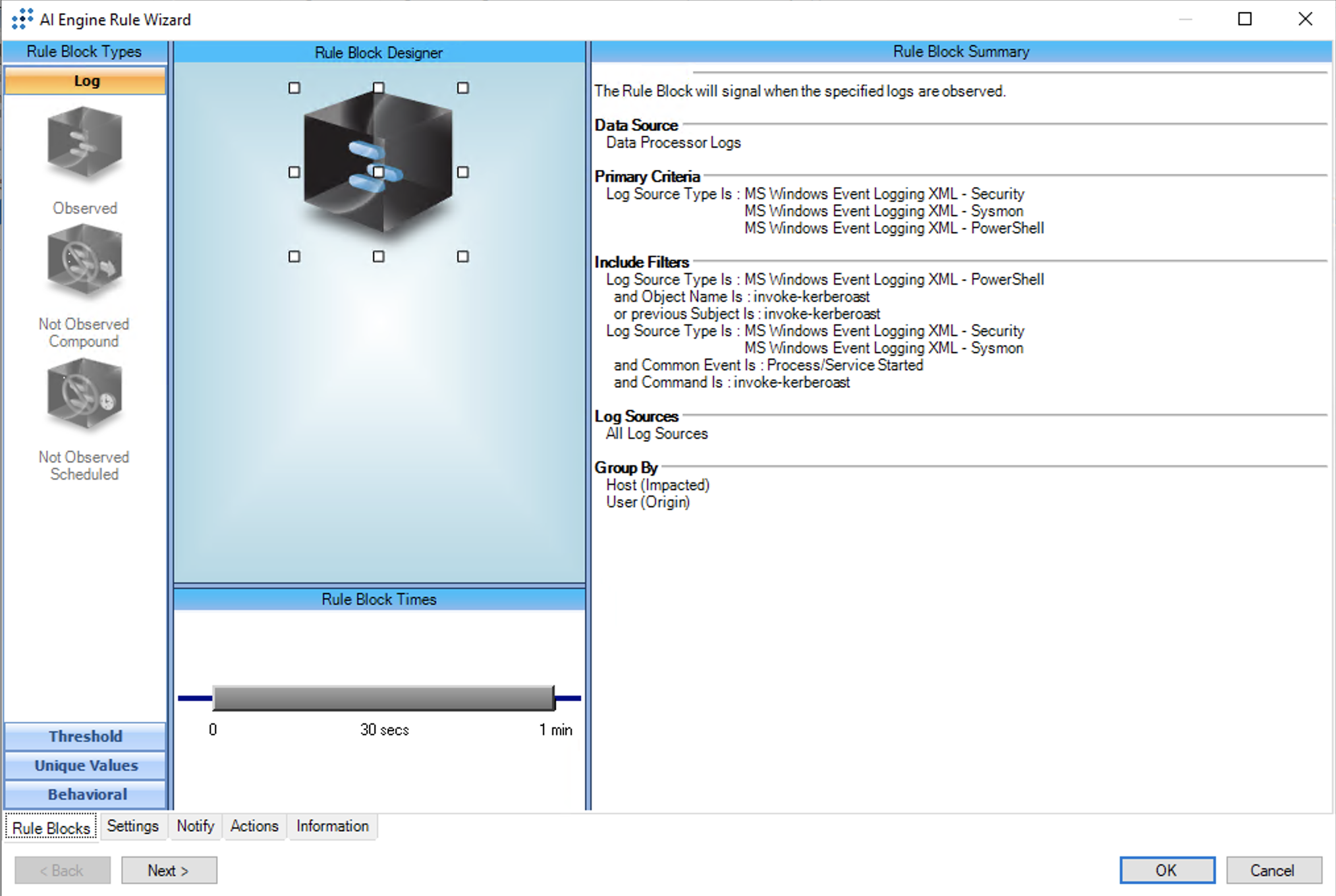
T1558.003:Kerberoasting:Invoke-Kerberoast
AIE Rule ID: 1554
MITRE Tactic: Credential Access
Rule Description: T1558.003:Kerberoasting:Invoke-Kerberoast
Common Event: AIE:T1558.003:Kerberoasting:Invoke-Kerberoast
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 3
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Kerberoasting
Rule Created: 20 Nov 2020
Rule Updated: 18 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1558/003/
Notes:
Log Source Types:
Microsoft Windows Event Logging XML - Security
Microsoft Windows Event Logging - PowerShell
Microsoft Windows Event Logging XML - Sysmon
Configuration:
PowerShell Module Logging must be enabled in order for the PowerShell criteria to be met: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_group_policy_settings
Process Monitoring must be enabled for the process criteria with Microsoft Windows Event Logging XML - Security and Microsoft Windows Event Logging XML - Sysmon to be met: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Tuning:
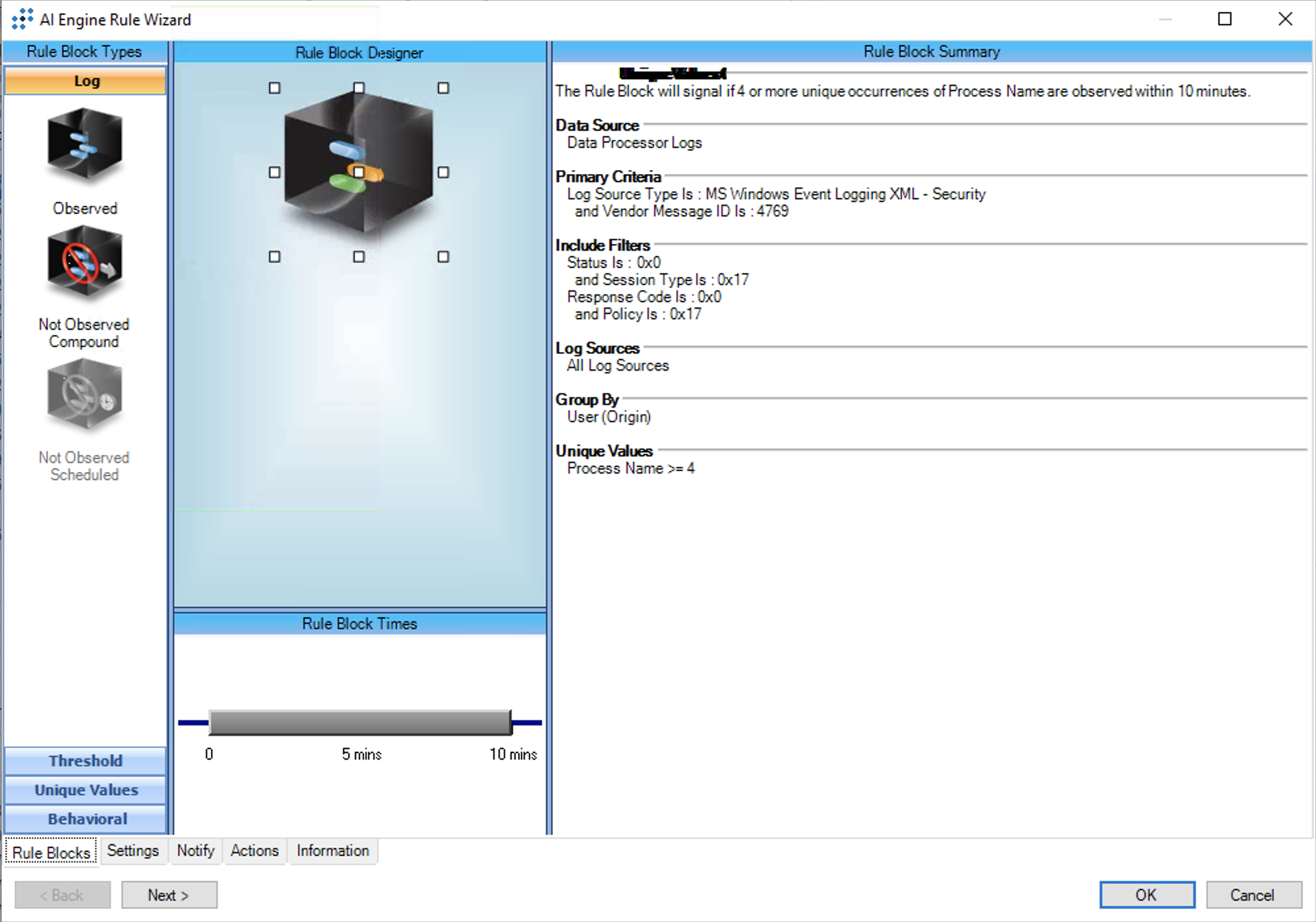
T1558.003:Kerberoasting:TGS Requests for Multiple Services
AIE Rule ID: 1555
MITRE Tactic: Credential Access
Rule Description: T1558.003:Kerberoasting:TGS Requests for Multiple Services
Common Event: AIE:T1558.003:Kerberoasting:TGSReqMultServices
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 3
AIE Rule Additional Details:
Tactic(s): Credential Access
Technique: Kerberoasting
Rule Created: 20 Nov 2022
Rule Updated: 18 Nov 2022
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1558/003/
Notes:
Log Source Types:
Microsoft Windows Event Logging XML - Security
Microsoft Windows Event Logging - PowerShell
Microsoft Windows Event Logging XML - Sysmon
Configuration:
Kerberos Service Ticket Operations must be audited in order for Windows Security Logs with Event ID 4769 to be generated: https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/audit-kerberos-service-ticket-operations
Tuning:
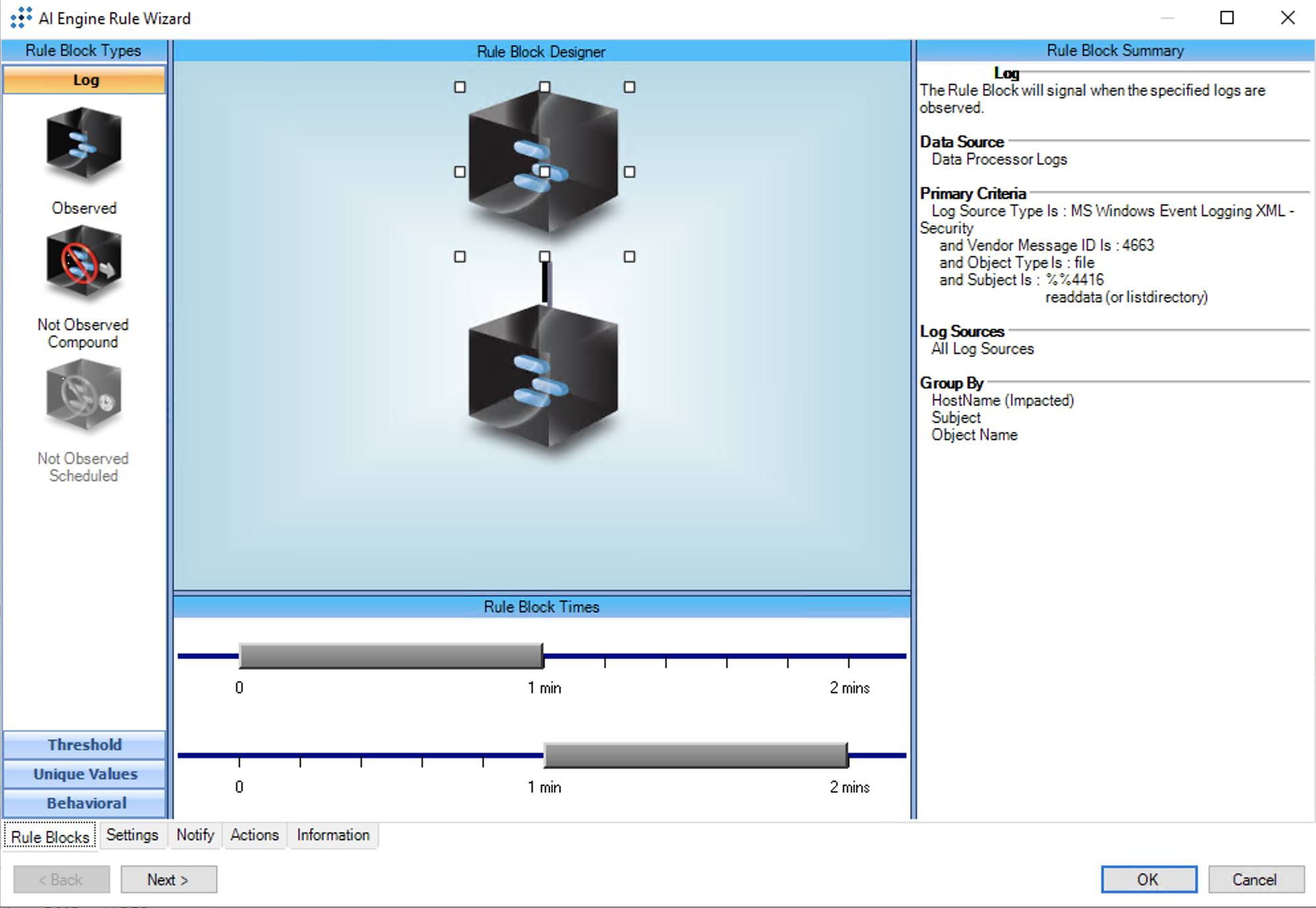
T1486: Data Encrypted for Impact: Feedback Source: File Read and Delete
AIE Rule ID: 1556
MITRE Tactic: Impact
Rule Description: T1486: Data Encrypted for Impact: Feedback Source: File Read and Delete
Common Event: T1486: DataEncrypted:FeedbackSource
Suppression Multiple: 1
Alarm on Event Occurrence: No
Forward AIE Event to Platform Manager: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details:
Tactic(s): Impact
Rule Created:2023 Jan 31
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1486
Notes:
Log Source Types:
MS Windows Event Logging XML - Security
Configuration:
***Use on LogRhythm version 7.9.0 and later***
This rule provides observations for two AIE feeback rules: "T1486: Data Encrypted for Impact: Rate" (Rule ID 1557) and "T1486:Data Encrypted for Impact:Threshold" (Rule ID 1558). Please enable one or both of the feedback rules along with this rule. When this rule triggers it will not produce an event in the LogRhythm Events database and thus will not be searchable or viewable in the LogRhythm Web Console. It is simply used to feed observations into the feedback rules.
File monitoring, especially when file reads are audited, can be an extremely high-volume log source. Before configuring and enabling this rule, consider which directories on your file servers and workstations contain mission-critical data that should be monitored for encryption activity.
Once the in-scope directories have been identified:
1) Enable Windows Object Access auditing in Group Policy under Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> System Audit Policies -> Object Access. Enable auditing of Success events for the Audit FileSytem subcategory.
2) Go to the Advanced Security Settings of the in-scope directories, choose the Auditing item and add an Auditing item (for Everyone) which includes the Read and Delete permissions.
3) Add the in-scope directory paths as an Include Filter to this rule. The Include Filter will be for the field Object Name and contain the path(s) you would like to monitor.
For more detailed instructions please search in LogRhythm Community (https://community.logrhythm.com) for the post titled "Configuration and Use of the T1486:Data Encrypted for Impact Rules"
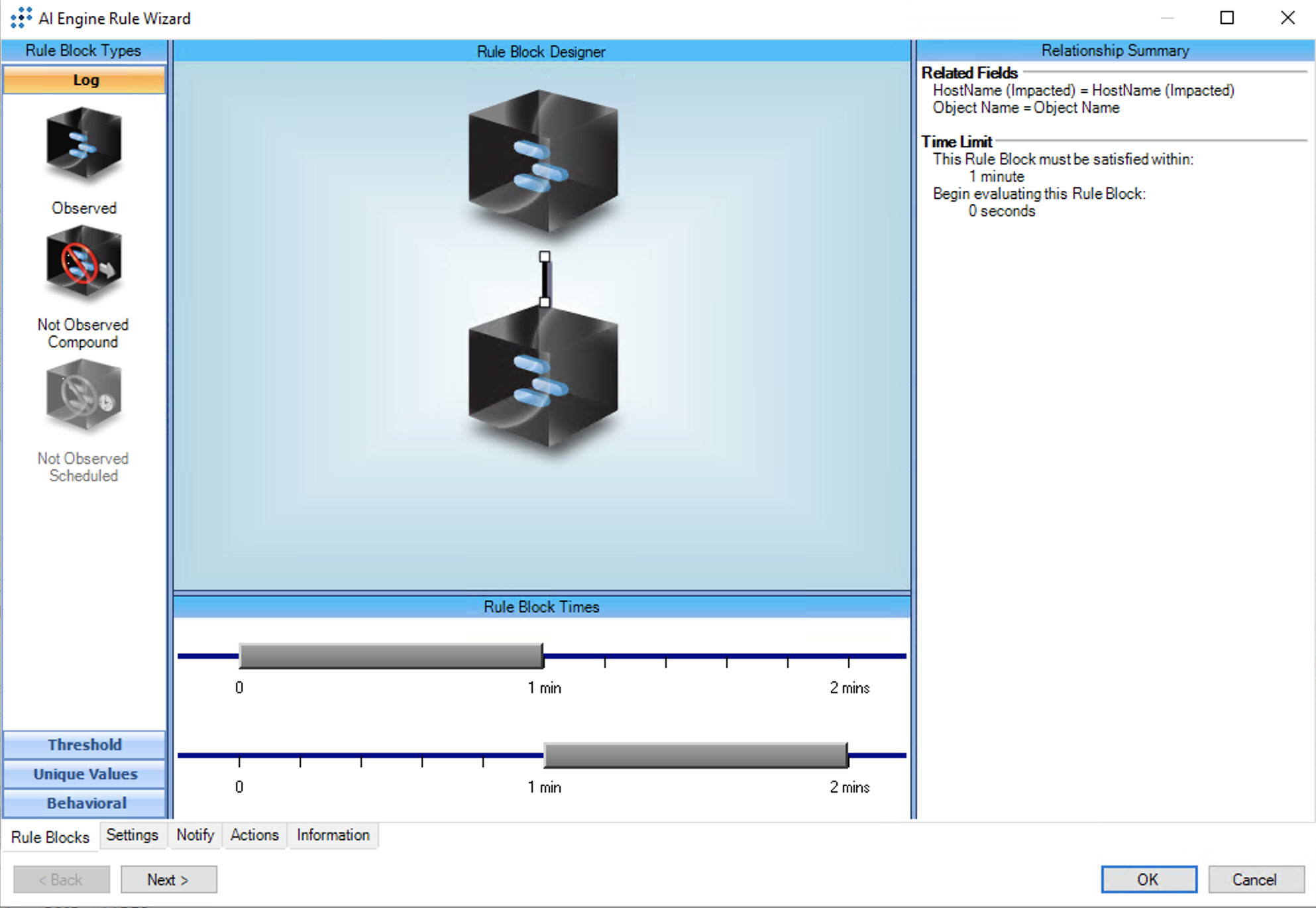
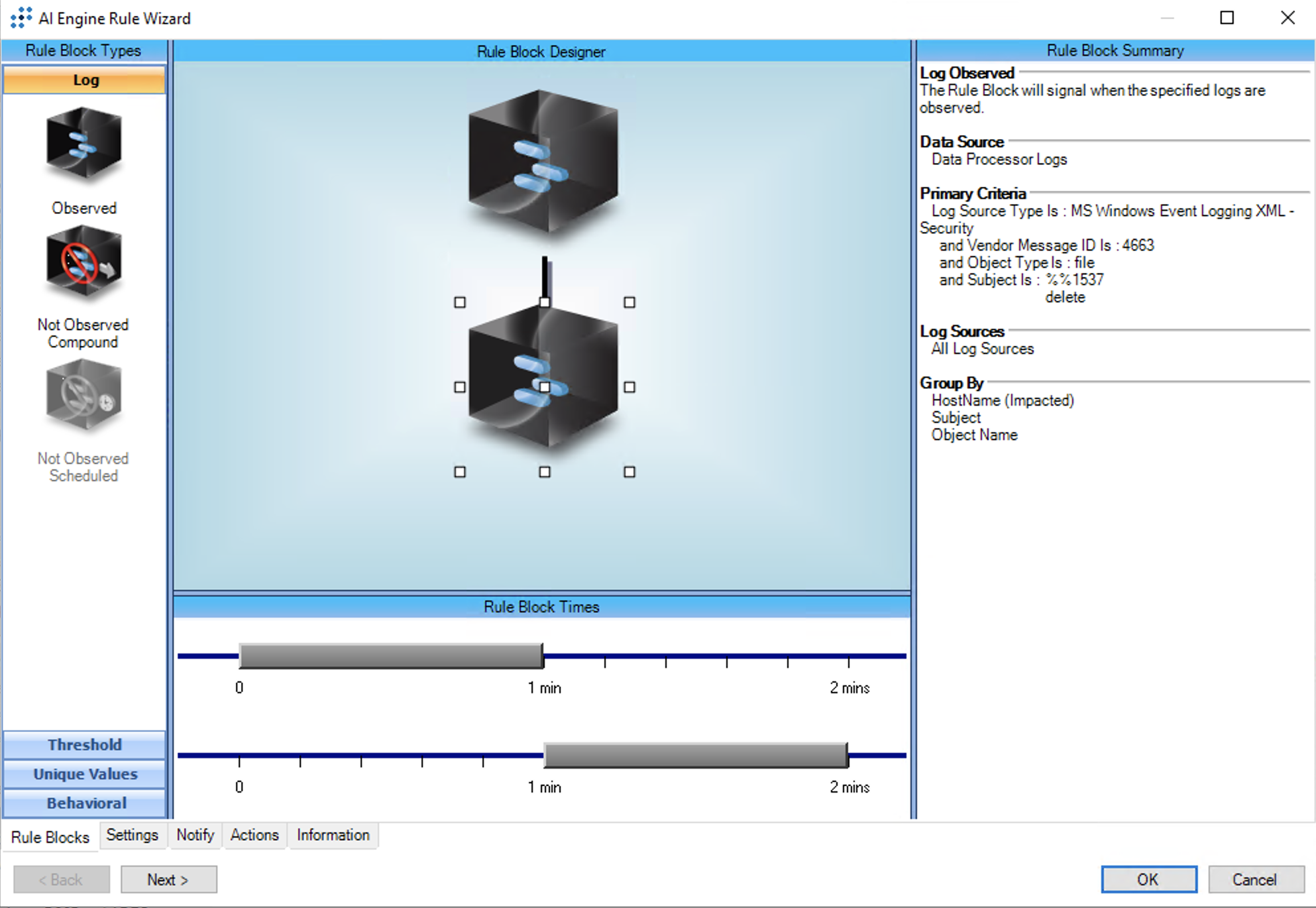
T1486:Data Encrypted for Impact: Rate
AIE Rule ID: 1557
MITRE Tactic: Impact
Rule Description: T1486:Data Encrypted for Impact: Rate
Common Event: T1486:Data Encrypted for Impact: Rate
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details:
Tactic(s): Impact
Rule Created:2023 Jan 31
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1486
Notes:
Use Case:
Ransomware is encrypting the user directories of a workstation or data-bearing directories on a file server.
Log Source Types:
LogRhythm AI Engine
Configuration:
***Use on LogRhythm version 7.9.0 and later***
The AIE Engine rule "T1486: Data Encrypted for Impact: Feedback Source: File Read and Delete" must be configured and enabled for this rule to function. This rule triggers based on the rate and volume of events generated per-host by the T1486: Data Encrypted for Impact: Feedback Source: File Read and Delete AIE rule.
For more detailed instructions please search in LogRhythm Community (https://community.logrhythm.com) for the post titled "Configuration and Use of the T1486:Data Encrypted for Impact Rules"
Tuning:
The volume and rate of events required to trigger this rule can be adjusted to reflect modern ransomware encryption speeds. It is recommended to test rate assumptions against ransomware simulators.
False Positive Considerations:
Other activities could produce a high volume of file reads and deletes, such as archive backups or a high volume of file moves. Consider tuning the feeder rule (T1486: Data Encrypted for Impact: Feedback Source: File Read and Delete) to exclude known processes that exhibit such behaviors.
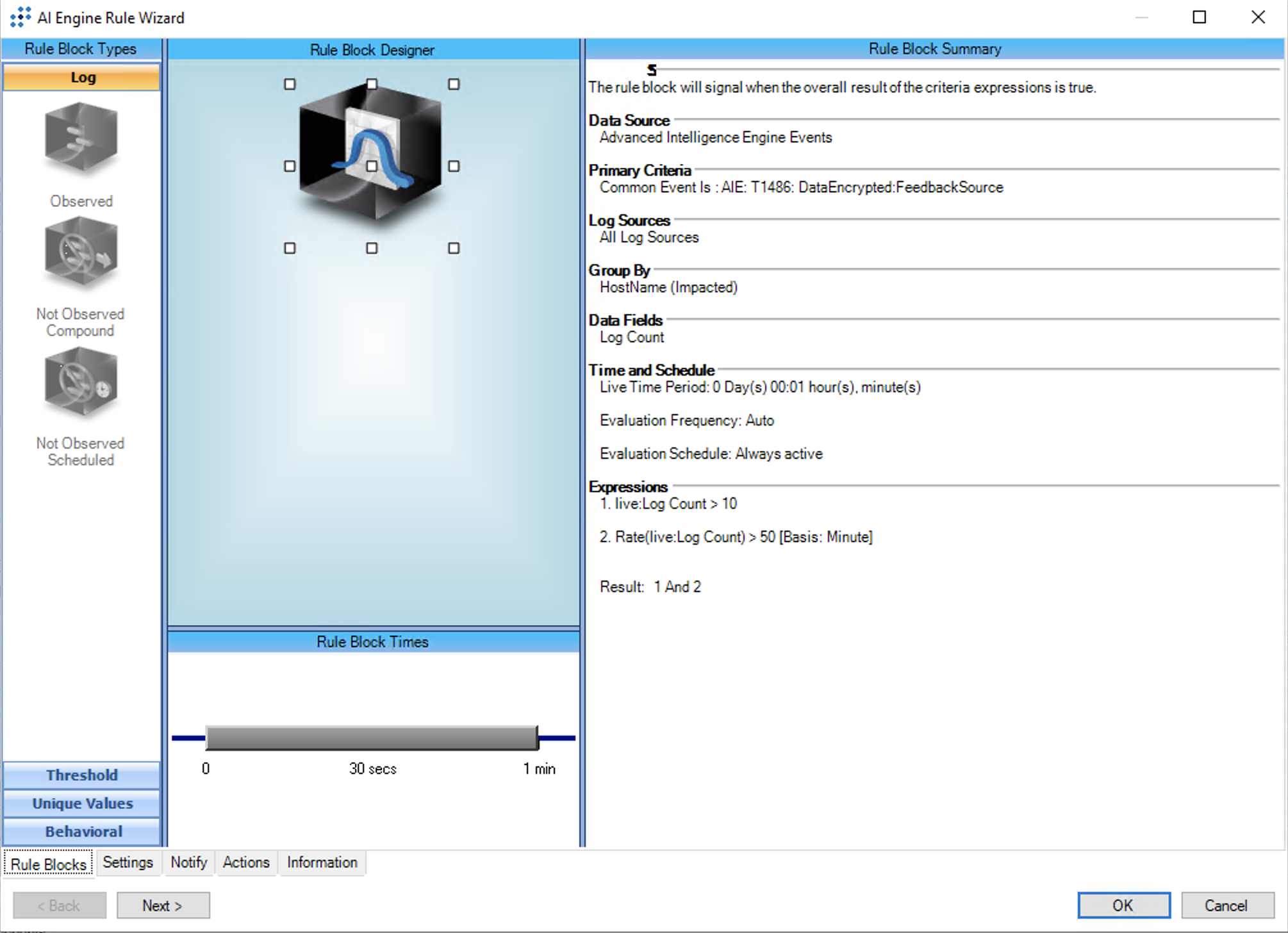
T1486:Data Encrypted for Impact:Threshold
AIE Rule ID: 1558
MITRE Tactic: Impact
Rule Description: T1486:Data Encrypted for Impact:Threshold
Common Event: T1486:Data Encrypted for Impact:Threshold
Suppression Multiple: 1
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details:
Tactic(s): Impact
Rule Created: 25 Jan 2023
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1486
Notes:
Use Case:
Ransomware is encrypting the user directories of a workstation or data-bearing directories on a file server.
Log Source Types:
LogRhythm AI Engine
Configuration:
***Use on LogRhythm version 7.9.0 and later***
The AIE Engine rule "T1486: Data Encrypted for Impact: feedback source:file read and delete" must be configured and enabled for this rule to function. This rule triggers based on the rate and volume of events generated per-host by the T1486: Data Encrypted for Impact: feedback source: file read and delete AIE rule.
For more detailed instructions please search in LogRhythm Community (https://community.logrhythm.com) for the post titled "Configuration and Use of the T1486:Data Encrypted for Impact Rules"
Tuning:
The volume and rate of events required to trigger this rule can be adjusted to reflect modern ransomware encryption speeds. It is recommended to test rate assumptions against ransomware simulators.
False Positive Considerations:
Other activities could produce a high volume of file reads and deletes, such as archive backups or a high volume of file moves. Consider tuning the feeder rule (T1486: Data Encrypted for Impact: file read and delete) to exclude known processes that exhibit such behaviors.
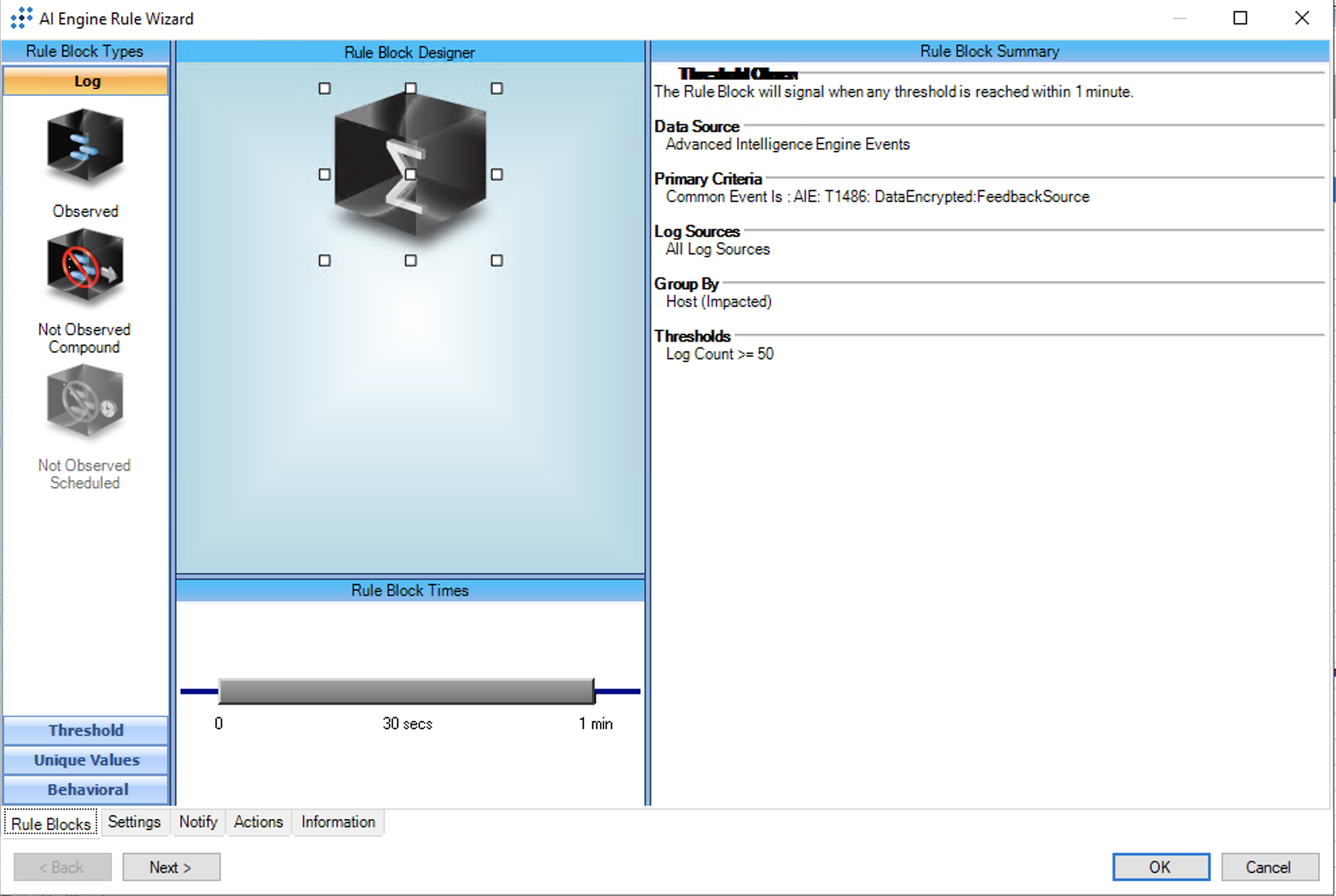
1562.002: Impair Defenses: Disable Windows Event Logging
AIE Rule ID: 1559
MITRE Tactic: Defense Evasion
Rule Description: 1562.002: Impair Defenses: Disable Windows Event Logging
Common Event: AIE: 1562.002:ImpairDefenses:DisableWinEvtLog
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details:
Tactic(s):Defense Evasion
Technique: Disable Windows Event Logging
Rule Created:10 Jan 2023
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1562/002
Notes:
Log Source Types:
Microsoft Windows Event Logging XML - Security
Microsoft Windows Event Logging - PowerShell
Microsoft Windows Event Logging XML - Sysmon
Configuration:
Command line logging and PowerShell logging must be enabled. Please see the sections titled "Configure Command Line Parameter Logging" and "Configure PowerShell Logging" in the MITRE ATT&CK Deployment Guide for more information: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
The Microsoft Sysmon configuration for Event ID 13 should include HKLM\System\CurrentControlSet\Control. Please see https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon for more information.
It is recommeded to enable Alarming for this rule and to enable the following AIE Summary Fields in the rule block so that the AIE Event contains more contextual information:
Policy
Process
Command
Object Name
Subject
Tuning:
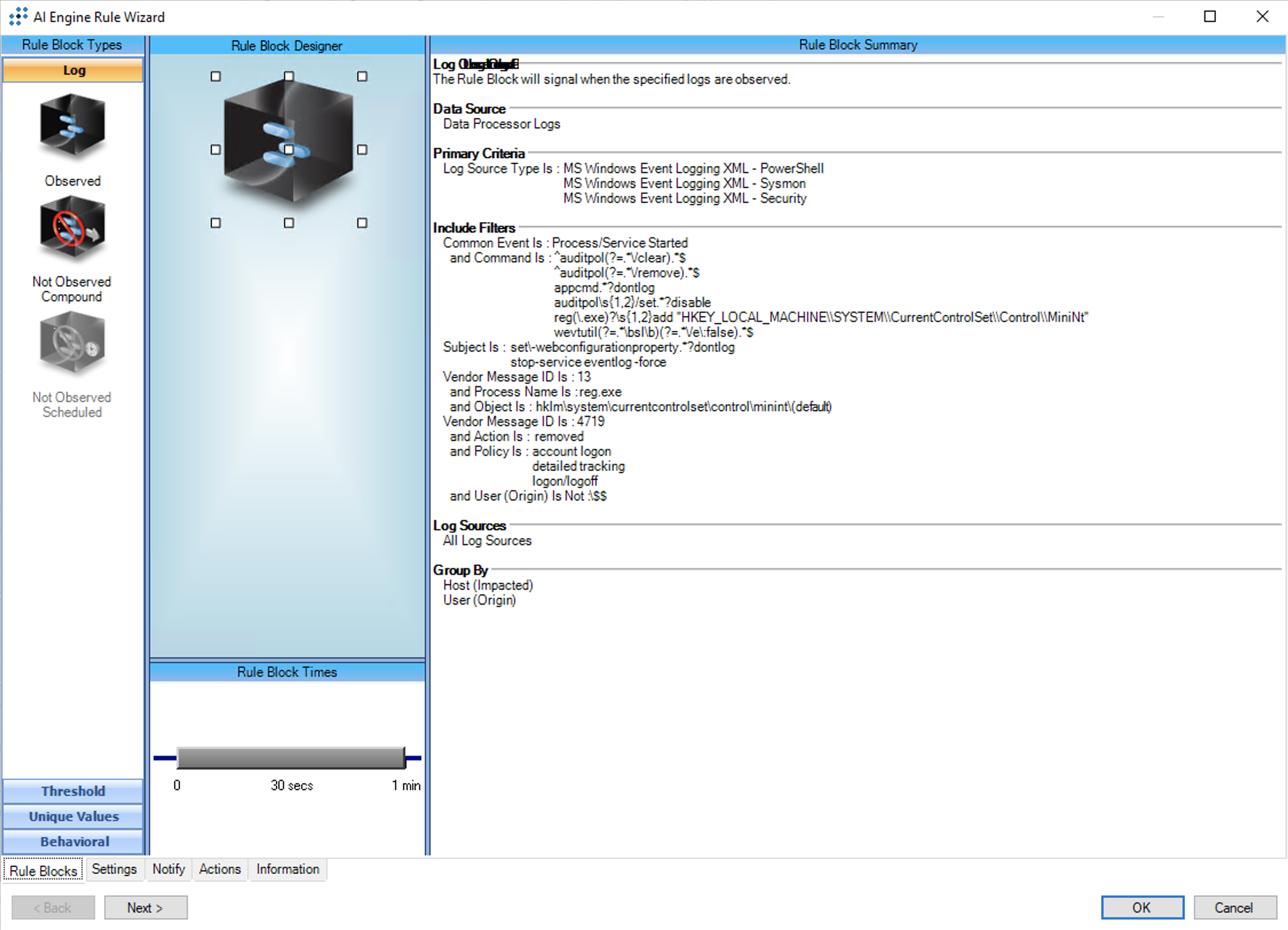
T1539: Steal Web Session Cookie
AIE Rule ID: 1565
MITRE Tactic: Defense Evasion
Rule Description: T1539: Steal Web Session Cookie
Common Event: AIE: T1539: Steal Web Session Cookie
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 5
AIE Rule Additional Details:
Tactic(s): Credential Access
Rule Created:20 March 2023
Rule Updated: N/A
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1539
Notes:
This rule detects the potential theft of Web Session Cookies via two different means:
- direct access of the cookies files of Firefox (in %appdata%\Mozilla\Firefox\Profiles\*\cookies.sqlite), Chrome (in %LOCALAPPDATA%\Google\Chrome\User Data\Default\Network\Cookies) or MSEdge (in %LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Network\Cookies) by either powershell.exe or sqlite3.exe
- starting Chrome or Firefox in remote debugging mode
Logging requirements:
To take full advantage of this detection, you need to have the following logging configured:
- File monitoring, either via MS Windows Event Logging XML - Security or LogRhythm File Monitor logs, of the cookies files listed above
- Process and command-line logging, either via MS Windows Event Logging XML - Security or MS Windows Event Logging XML - Sysmon
Please refer to the MITRE ATT&CK Module Deployment Guide for more information about configuring file and process monitoring: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Tuning:
If this rule is set to have Alarming enabled, it is recommended to enable the following AIE Summary Fields:
- Command
- Object Name
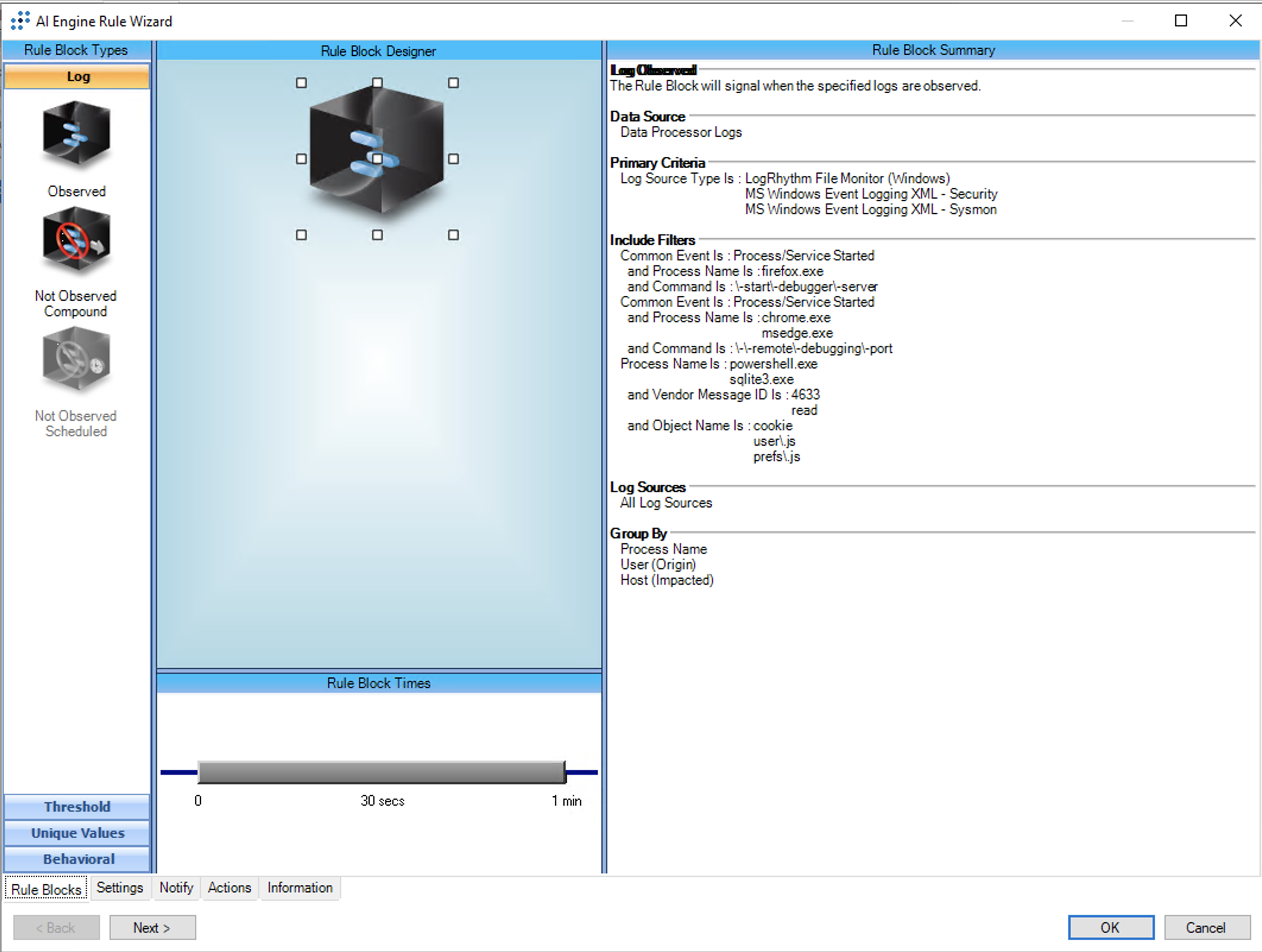
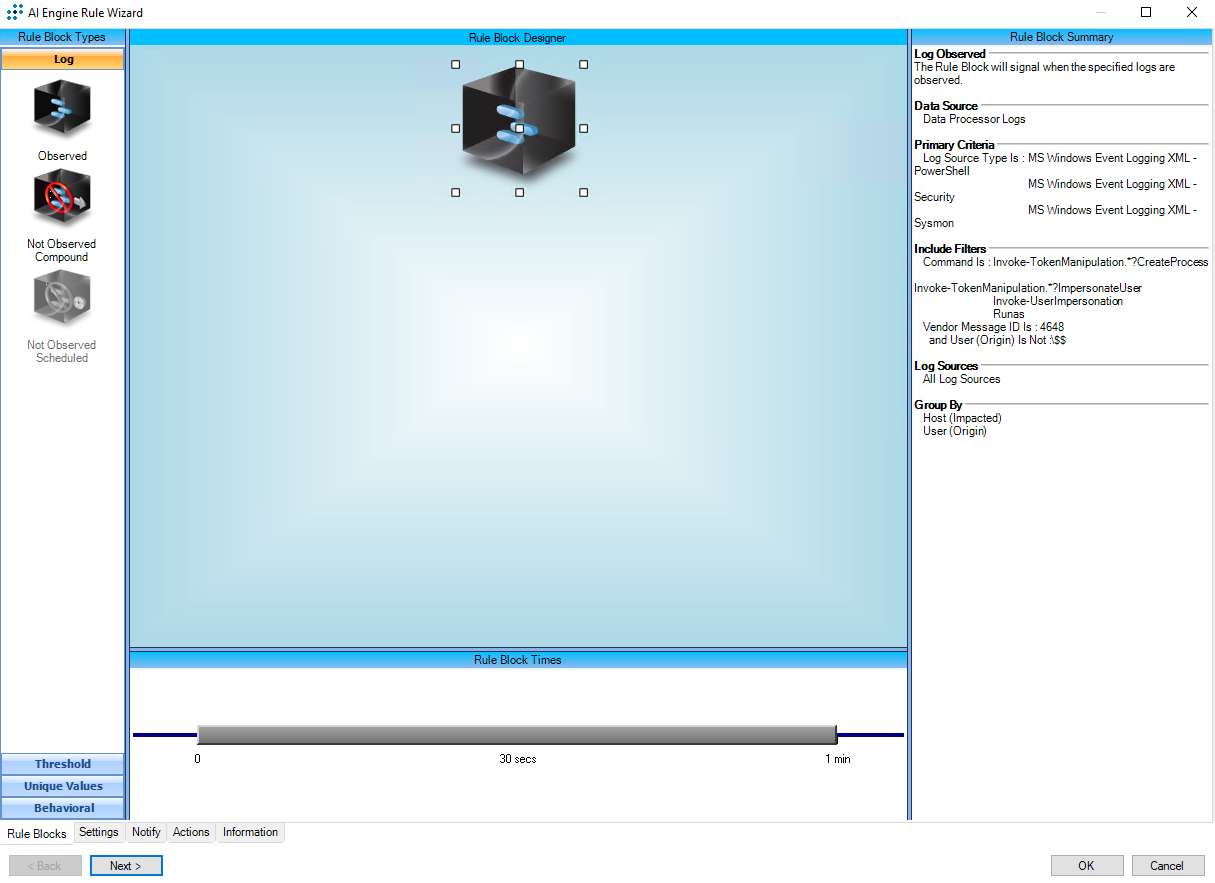
T1134.002:Access Token Manipulation:Create Process with Token
AIE Rule ID: 1566
MITRE Tactics: Defense Evasion, Privilege Escalation
Rule Description: T1134.002:Access Token Manipulation:Create Process with Token
Common Event: T1134.002:Manipulation:CreateProcesswithToken
Suppression Multiple: 60
Alarm on Event Occurrence: No
Environmental Dependence Factor: None
False Positive Probability: 7
AIE Rule Additional Details:
Tactic(s): Defense Evasion, Privilege Escalation
Technique: Access Token Manipulation
Rule Created: 04/14/2023
For further guidance on this Tactic : Technique, please visit the MITRE ATT&CK website:
https://attack.mitre.org/techniques/T1134/002/
Notes:
Log Source Types:
Microsoft Windows Event Logging XML - Security
Microsoft Windows Event Logging XML - PowerShell
Microsoft Windows Event Logging XML - Sysmon
Configuration:
PowerShell Module Logging must be enabled in order for the PowerShell criteria to be met: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_group_policy_settings
Process Monitoring must be enabled for the process criteria with Microsoft Windows Event Logging XML - Security and Microsoft Windows Event Logging XML - Sysmon to be met: https://docs.logrhythm.com/docs/kb/threat-detection/mitre-att-ck-module/mitre-att-ck-module-deployment-guide/mitre-att-ck-deployment-guide-import-and-synchronize-the-module
Tuning:
Some services (e.g. Microsoft SCCM, LogRhythm SCSM, Microsoft SQL) may run as different users depending on how they are configured and will generate 4648 logs. If the behavior is expected, you may add exclude filters to remove them from this rule.