CMMC User Guide – Compliance Maturity Model: A Foundation and Road Map
The Labs Compliance Research team within LogRhythm realizes our customers transition through a maturing process as they implement controls, policies, personnel, and system solutions to achieve compliance within regulatory frameworks. As their compliance programs mature, organizations need an SIEM solution that adapts to the changes they have implemented. A compliance offering through an SIEM that cannot be readily modified detracts value from a customer’s experience. While working to build their compliance programs, organizations need the ability to integrate their improvements into the SIEM to a robust cybersecurity infrastructure.
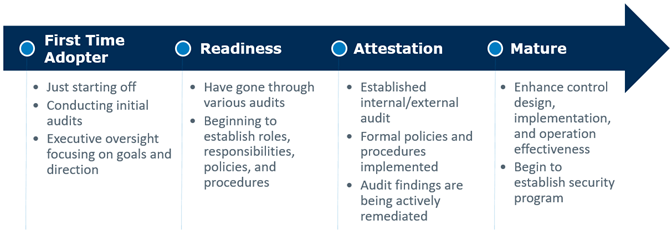
Audits and ongoing compliance programs might be viewed as compulsory, but organizations can actually leverage regulatory frameworks to create competitive advantages. As an organization progresses across the compliance maturity model (below), a security foundation emerges around policies, controls, systems, personnel, and understanding. The organization begins by developing key resources such as system and account classifications, risk assessments, scope definition, process and data flows, and audit results year-over-year. All these factors are ingredients to constructing a solid yet resilient compliance foundation that enables an organization to transition into a more mature security posture. This transition occurs as the organization builds its security program on a holistic and transparent understanding of its environment and risk profile.
LogRhythm aims to provide a road map through which SIEM empowers an organization to grow into a security program. Our approach allows organizations to start basic and transition into more enhanced facets of LogRhythm SIEM and other solutions where data protection not only achieves regulatory compliance but it also becomes a competitive advantage.
Key Resources
As your organization works to achieve compliance with the CMMC, begin by developing the following key resources that you can leverage within the deployment of this compliance automation suite and LogRhythm SIEM as a whole.
- Data Inventory and Privacy Classification
- Asset Inventory and System Classification
- Definition of Key Management Responsibilities
- Security Policies and Procedures
- Information Security and Business Continuity Plans
Key Audiences
Examples of key audiences involved in the CMMC life cycle are listed below. You can use reporting packages, reports, and Case Management to deliver critical information to your key audiences. You can also modify these reporting tools to accommodate specific requests.
- Executive Management
- System Owners
- Control Owners
- Information Security
- IT Operations
