Configure MS Graph API
Microsoft Graph is a RESTful web API that enables you to access Microsoft Cloud service resources. After you register your app and get authentication tokens for a user or service, you can make requests to the Microsoft Graph API. This includes getting log data for Directory Audits, Sign Ins, and Security Alerts for the registered application.
Configure Microsoft Azure for Log Collection
The following steps must be completed prior to setting up a new "MSGraph API" collector in Axon.
Administrator permissions are required to perform some of these steps.
Create a New Azure Active Directory Application
Navigate to https://portal.azure.com and log in to the Azure portal.
- From the Azure portal dashboard, click Azure Active Directory in the left-hand menu.
- Click App registrations in the left-hand menu.
- Click + New registration.
The Register an application pop-up appears. - Enter a unique Name for the application.
- For Supported account types, click the Accounts in any organizational directory option.
- (Optional.) Enter the Redirect URI.
- Click Register.
The new application is added to the App registrations window. Click the newly created application to open its configuration page.
Copy the Application (client) ID and Directory (tenant) ID into a text document for later use.
Create a New Client Secret
- On the landing page for your newly created app (opened during step 9 of the previous section), click Certificates & secrets in the left-hand panel.
- Click the Client Secrets tab.
- Click the + New client secret button.
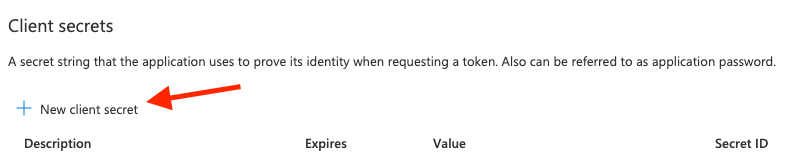
- Enter a unique Description for this client secret.
- Select the desired expiry period from the Expires drop-list.
- Click Add.
Copy the Value and Secret ID into a text document for later use.
These values are not accessible once the window is closed. Be sure to copy them now for later use.
Grant Permissions to the Azure Active Directory Application
- From the application's overview page, click API permissions in the left-hand panel.
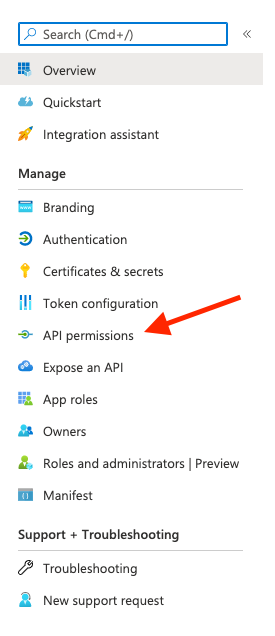
- Click + Add a permission.
- Click on Microsoft Graph.
- Click on Application permissions.
The following permissions need to be granted for the Azure Active Directory Application to communicate properly with Axon.
In the Select permissions search bar, enter these two permissions and check the box for each to include it.AuditLog.Read.All
- SecurityEvents.Read.All
- Directory.Read.All
- SecurityAlert.Read.All
- SecurityAlert.ReadWrite.All
- Click the Add permissions button.
The permissions are granted to the application.
(Optional) Assign a User to the Application with an Appropriate License
This step is only required to collect SignIn logs.
- On the landing page for the newly created application, click Owners in the left-hand menu.
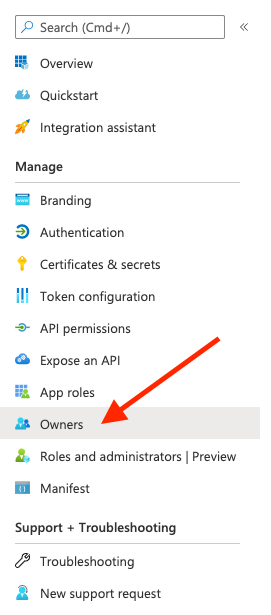
- Click the + Add owners button.
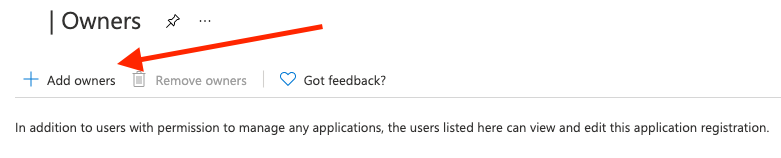
Add a user with either a P1, P2, or E1 license.
Click Select to add the owner.
For information on how to add a license to a user in Azure Active Directory, see https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/license-users-groups
