Axon: MITRE ATT&CK® Streaming Analytics User Guide
This user guide is meant to be used with the MITRE ATT&CK® Streaming Analytic rules and contains configuration and tuning notes.
T1003:OS Credential Dumping
Streaming Analytic Filter:
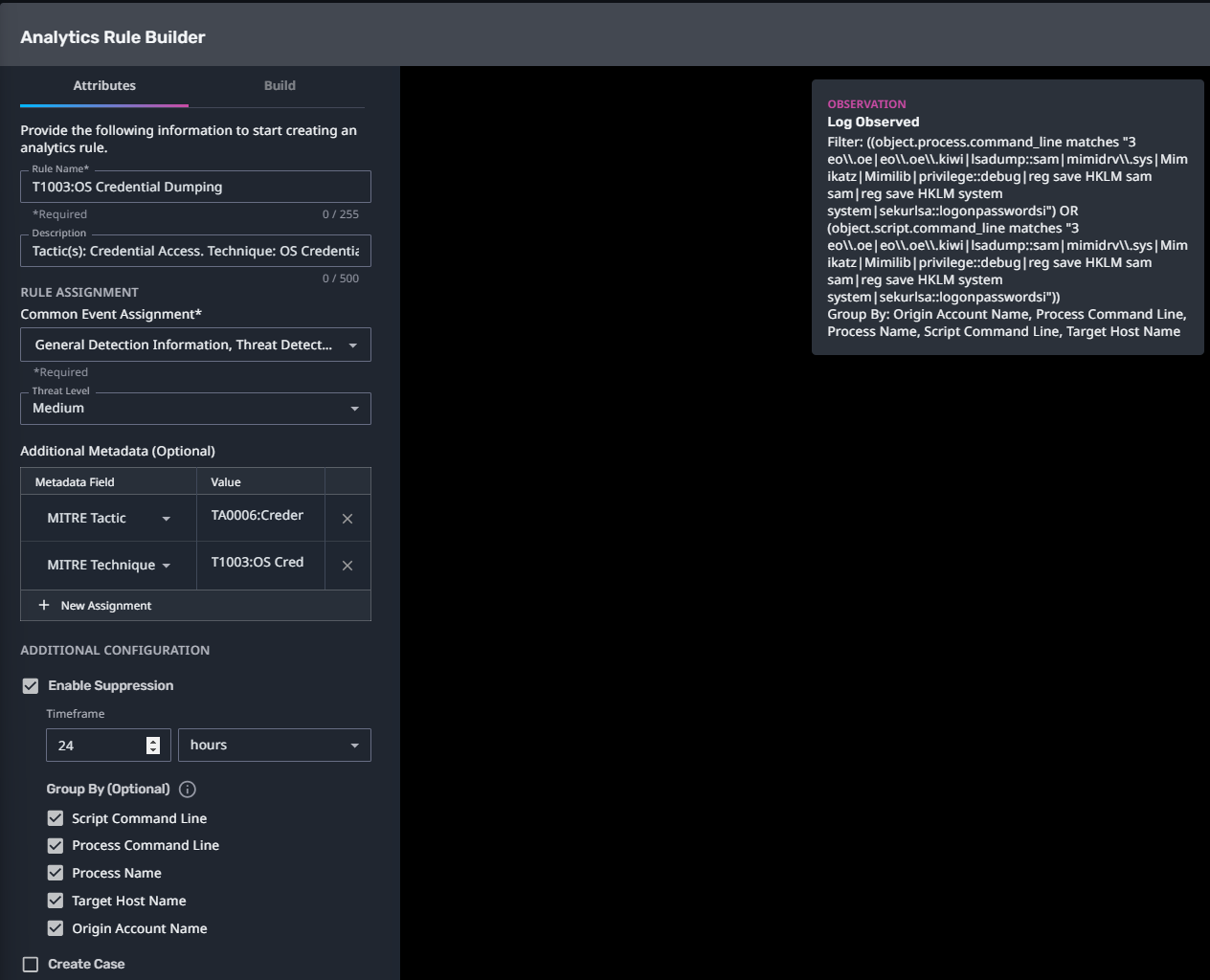
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1007:System Service Discovery
Streaming Analytic Filter:
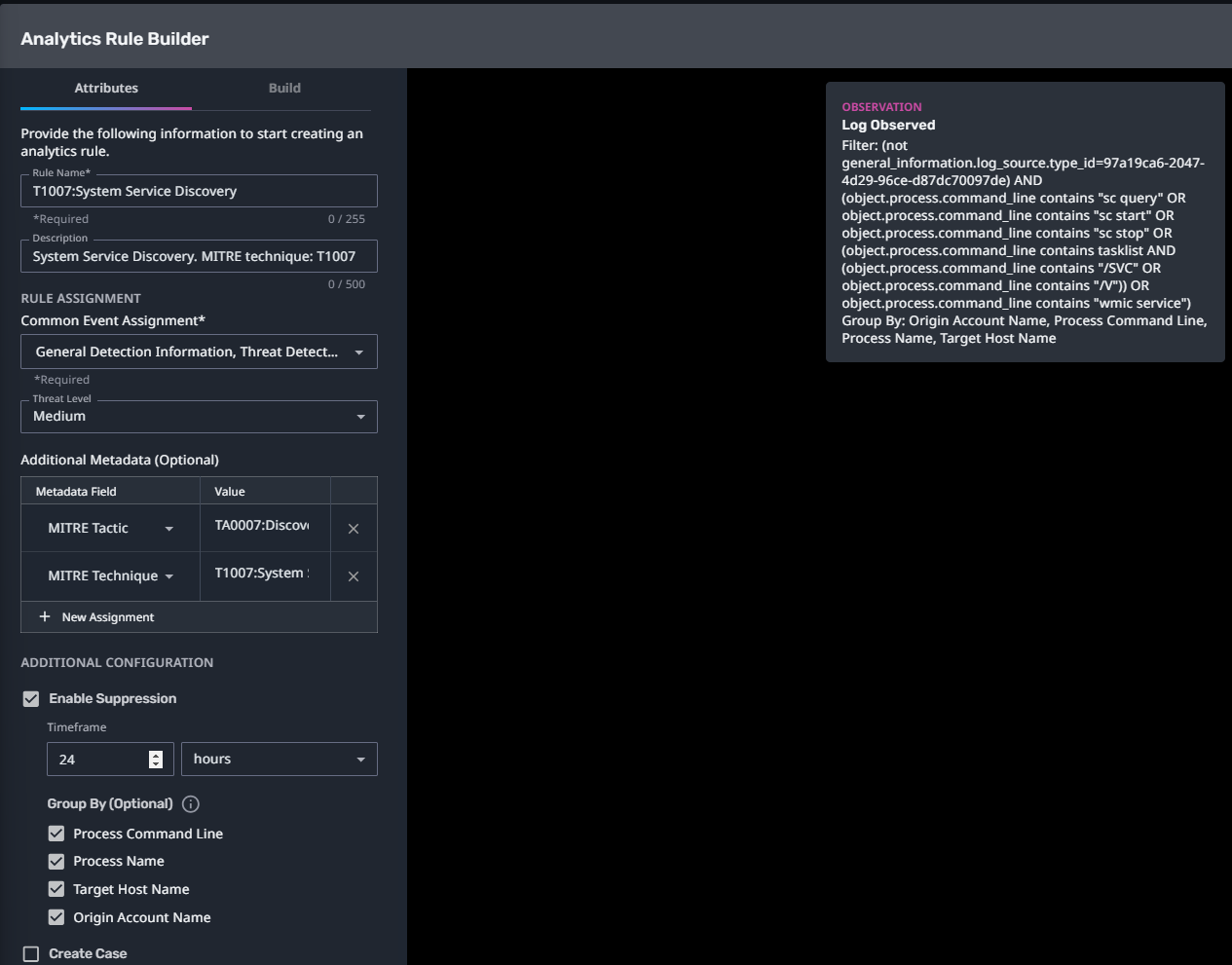
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1012:Query Registry
Streaming Analytic Filter:
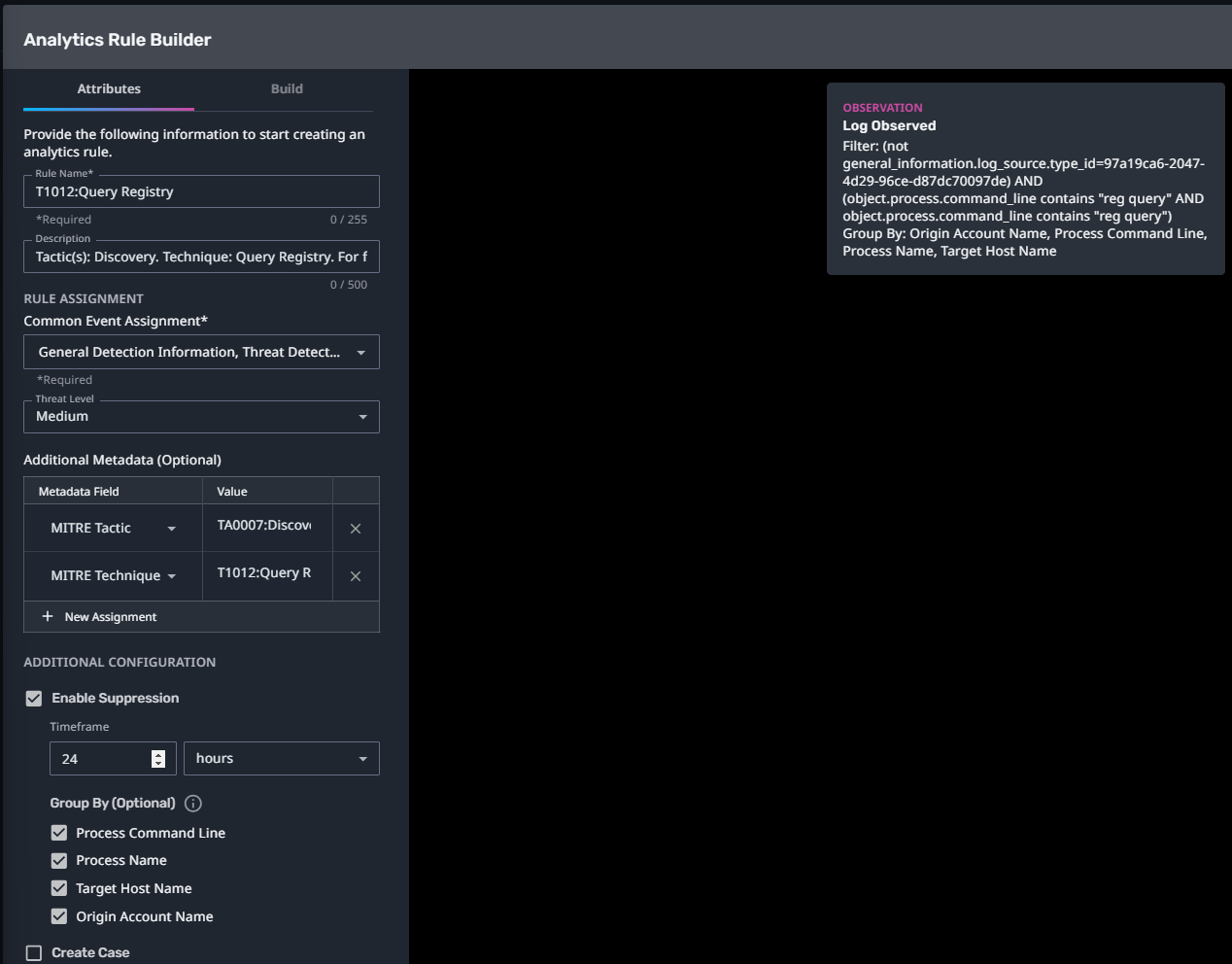
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1016:System Network Configuration Discovery
Streaming Analytic Filter:
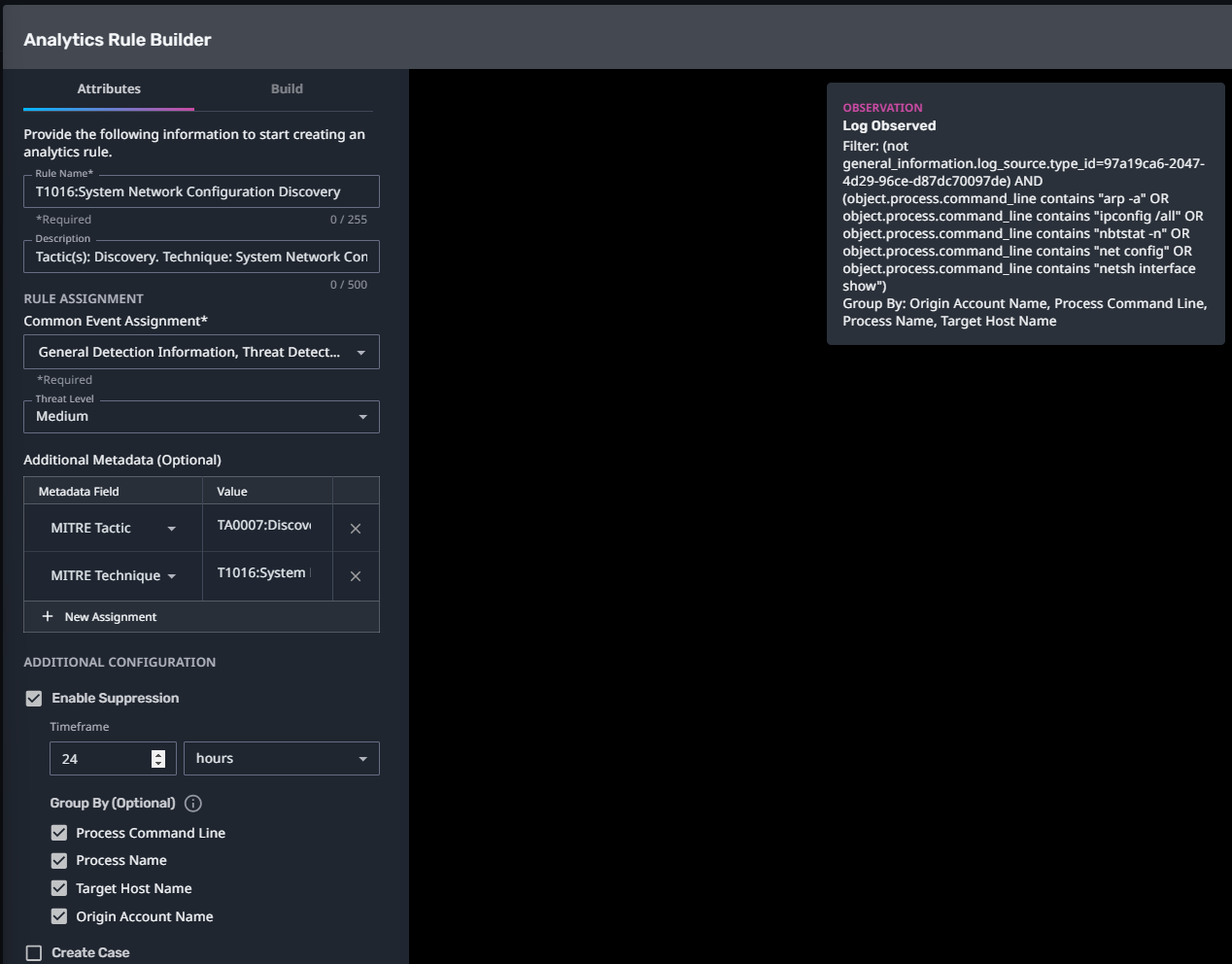
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1018:Remote System Discovery
Streaming Analytic Filter:
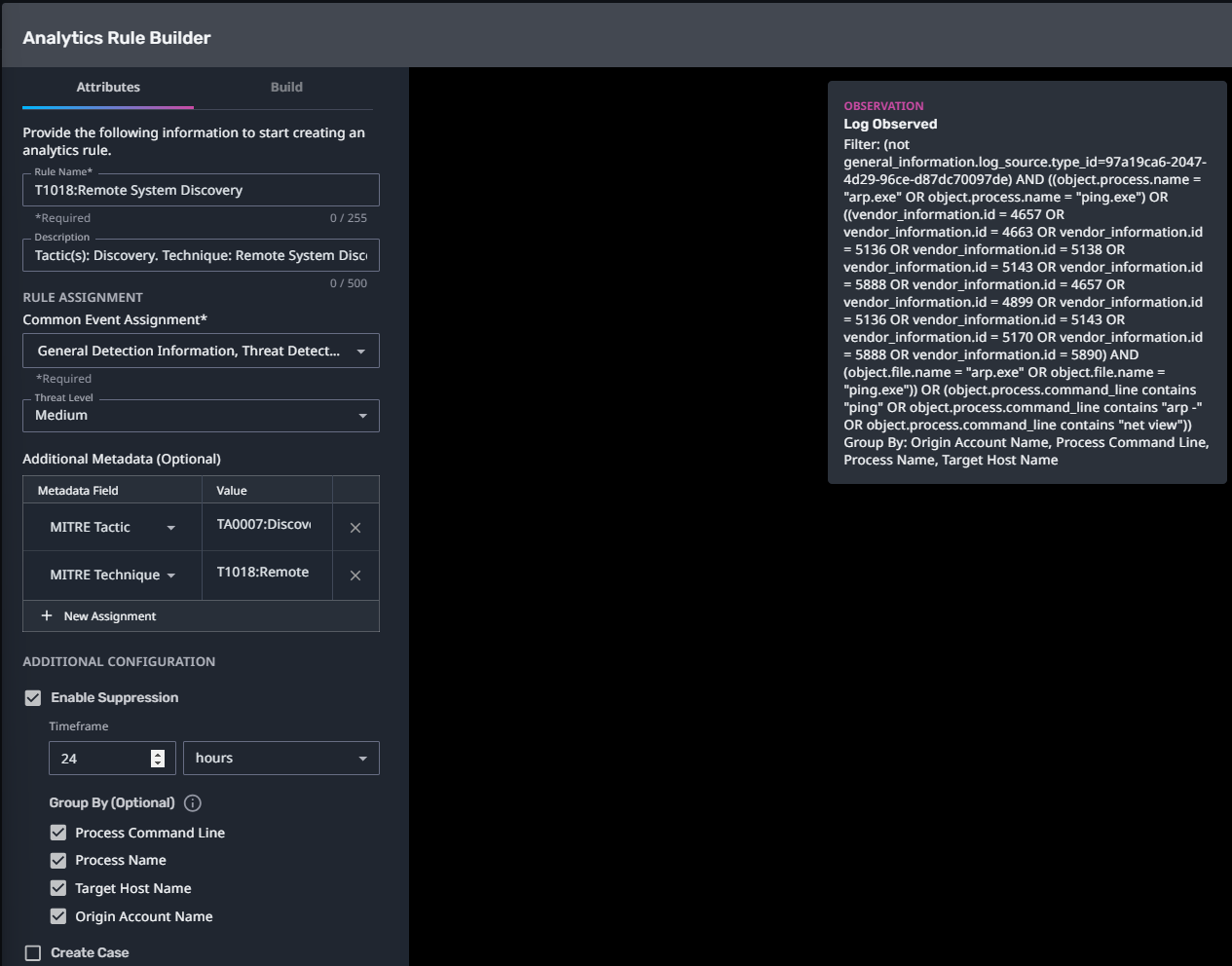
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1033:System Owner/User Discovery
Streaming Analytic Filter:
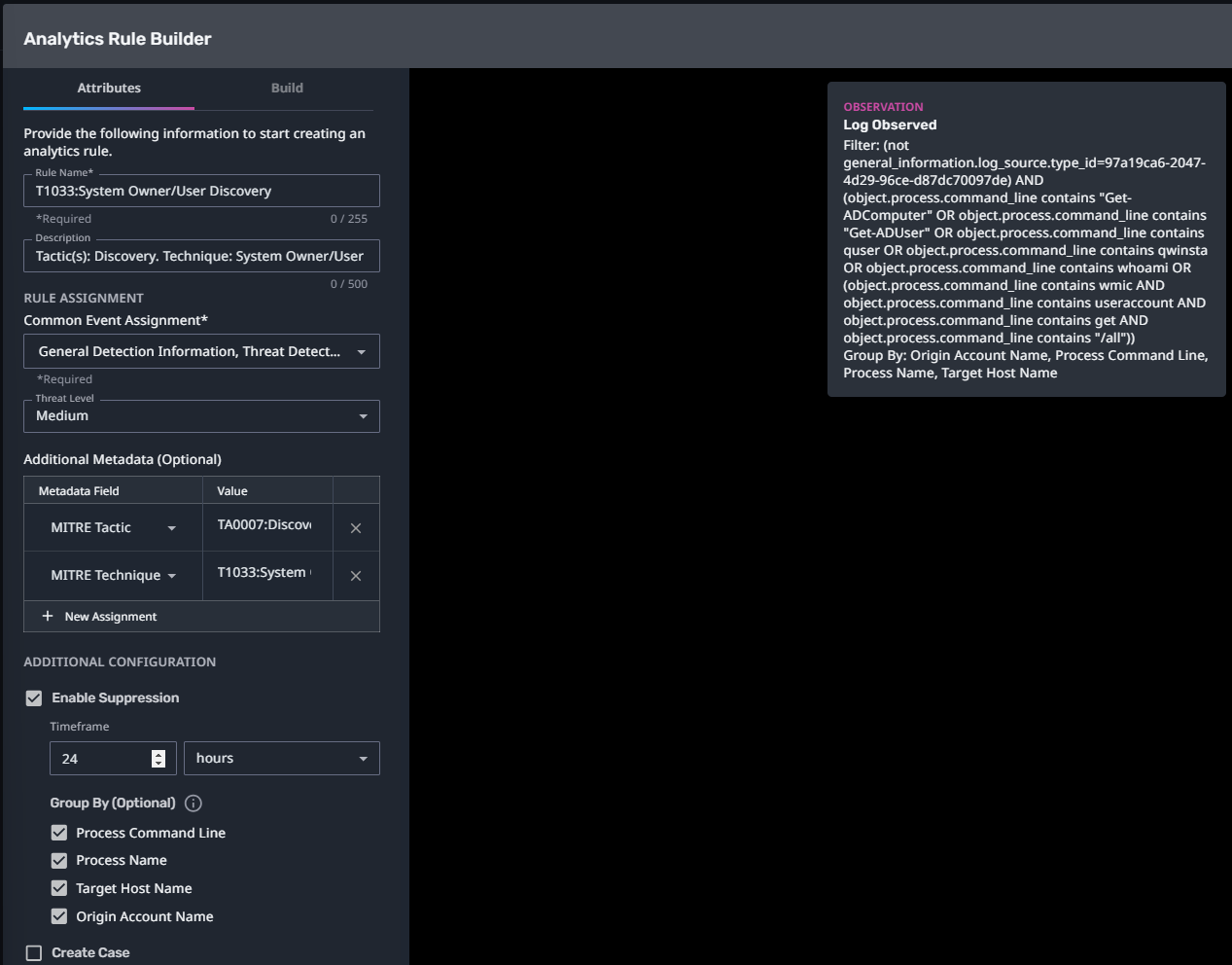
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1053:Scheduled Task
Streaming Analytic Filter:
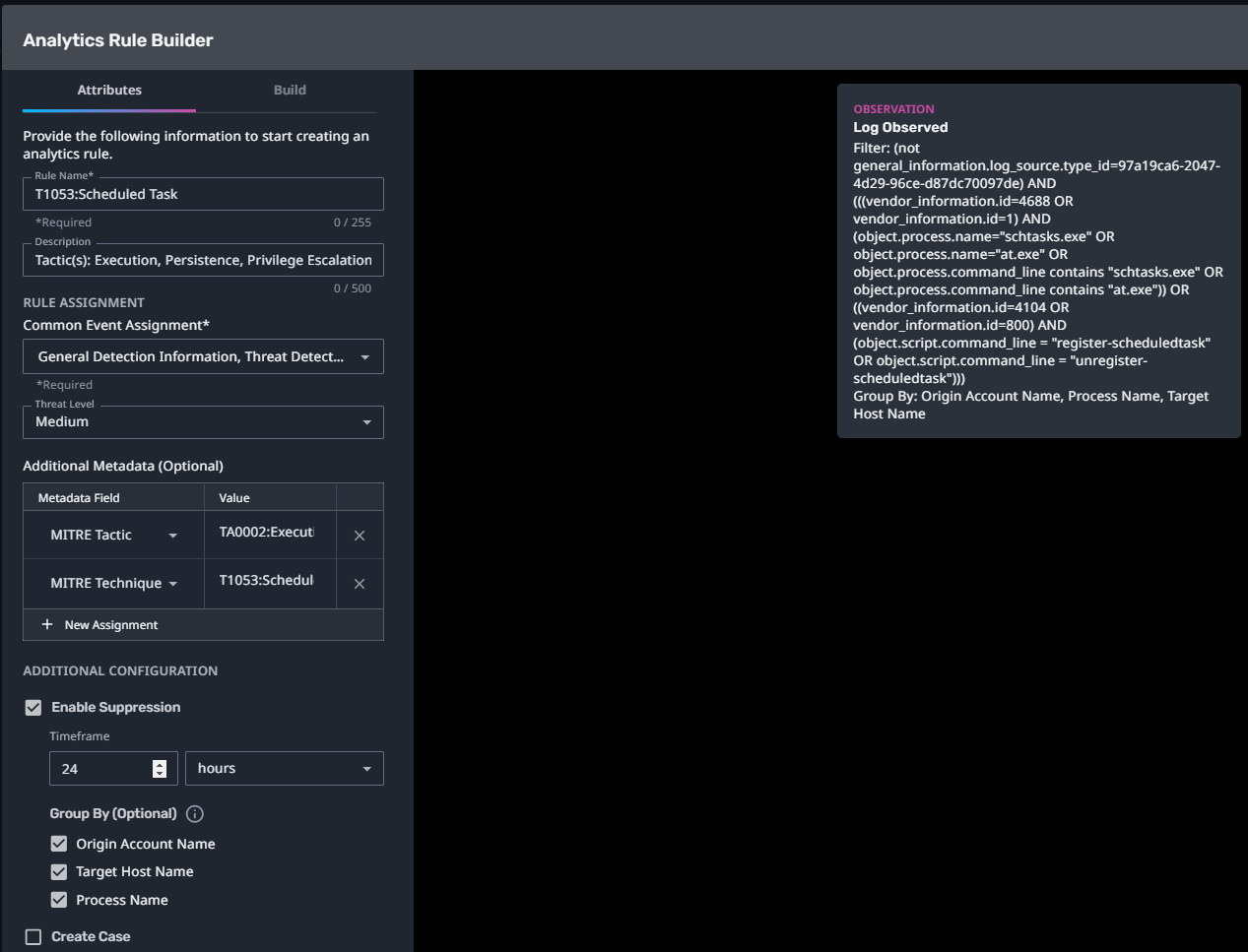
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1059:Command and Scripting Interpreter
Streaming Analytic Filter:
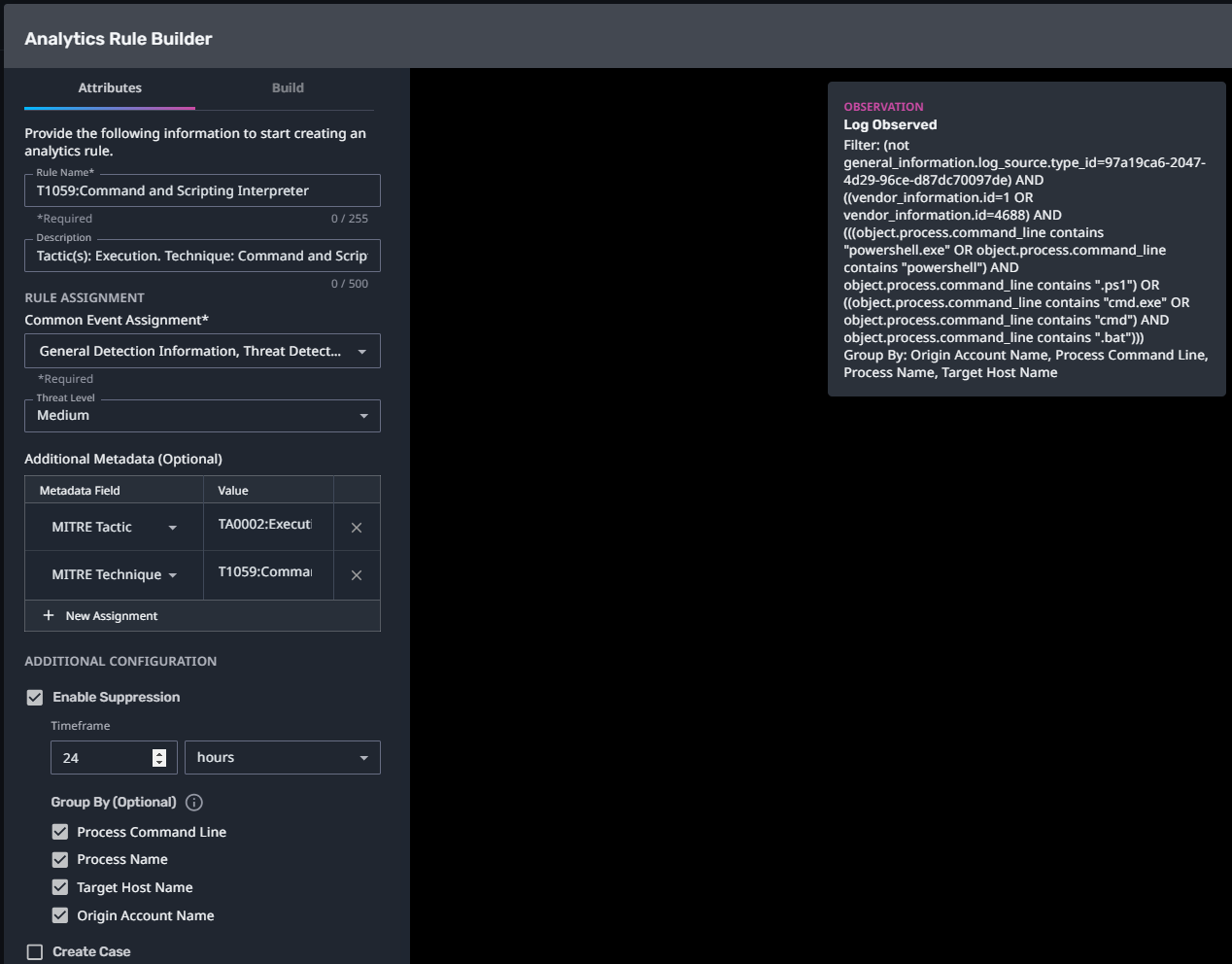
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1543.003:Windows Service
Streaming Analytic Filter:
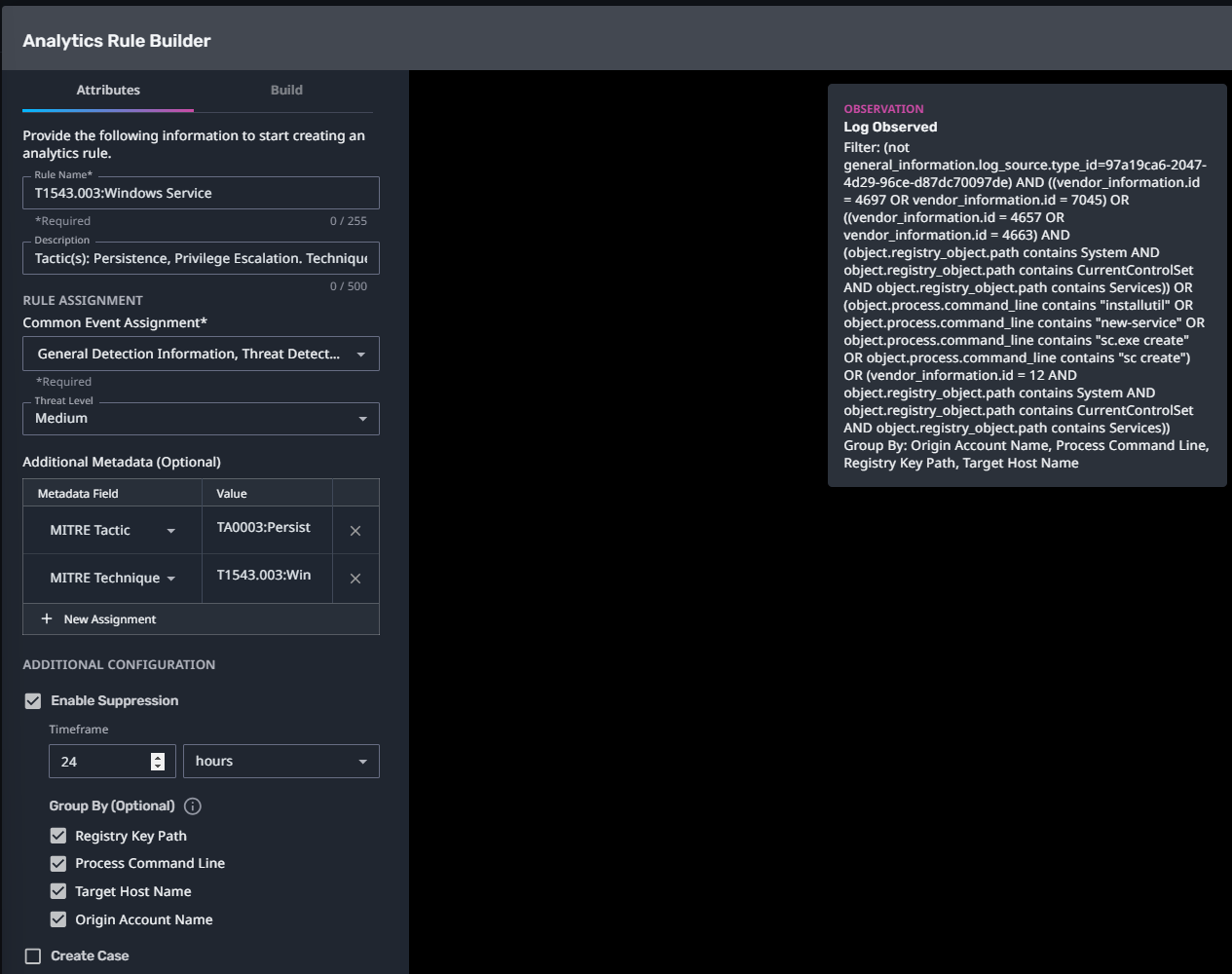
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1550.002:Pass the Hash
Streaming Analytic Filter:
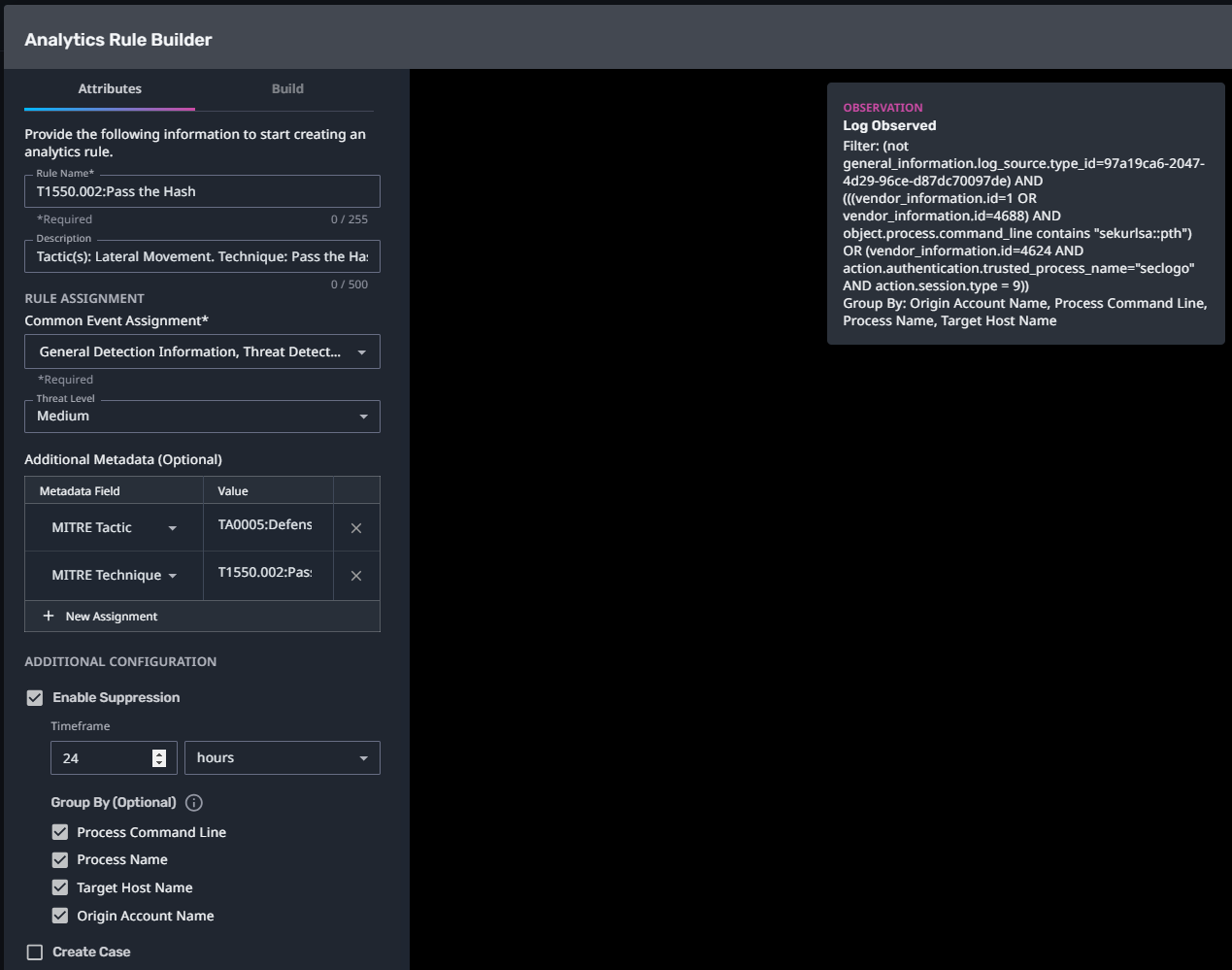
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1021.002:SMB/Windows Admin Shares
Streaming Analytic Filter:
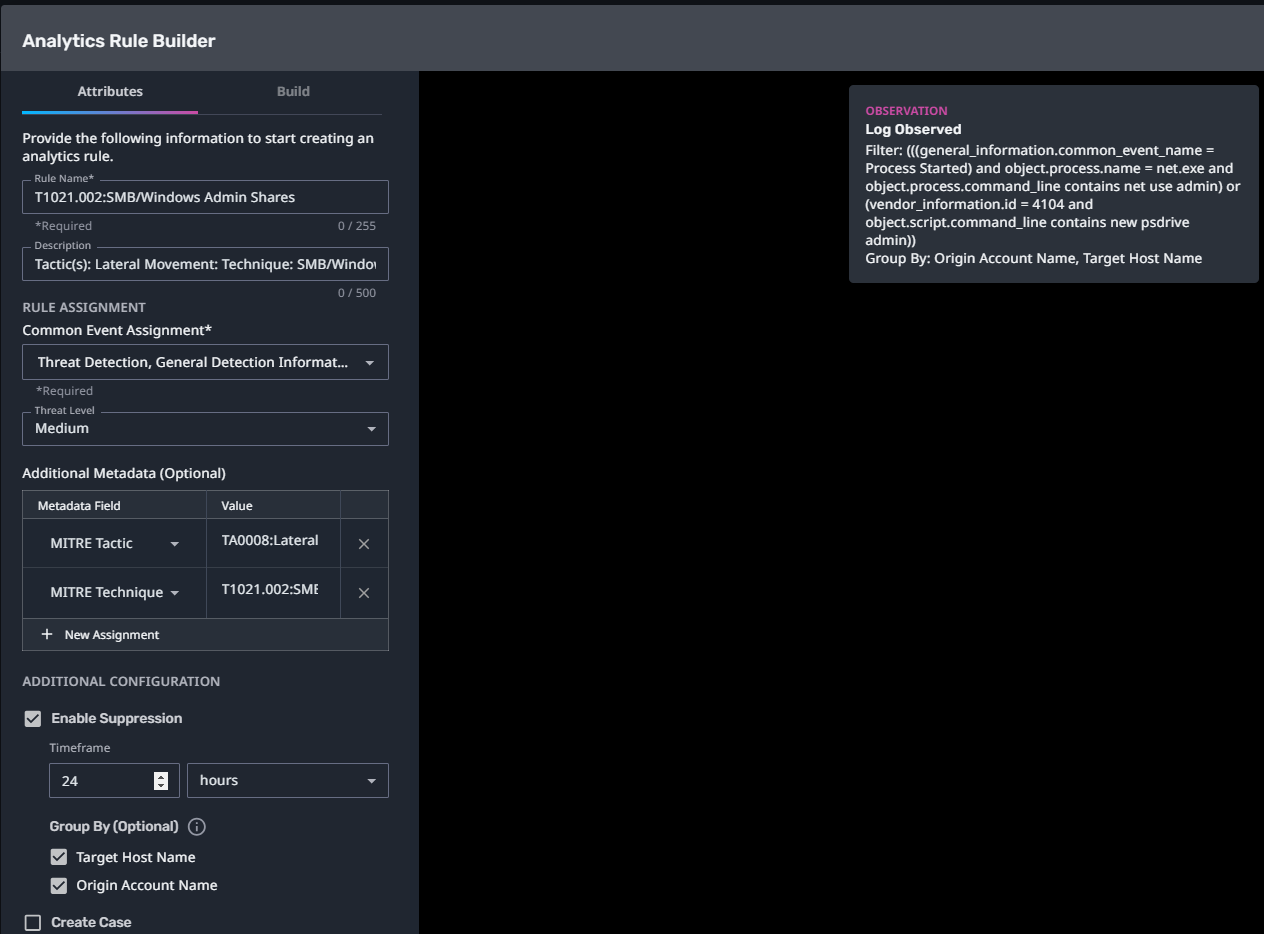
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1047:Windows Management Instrumentation
Streaming Analytic Filter:
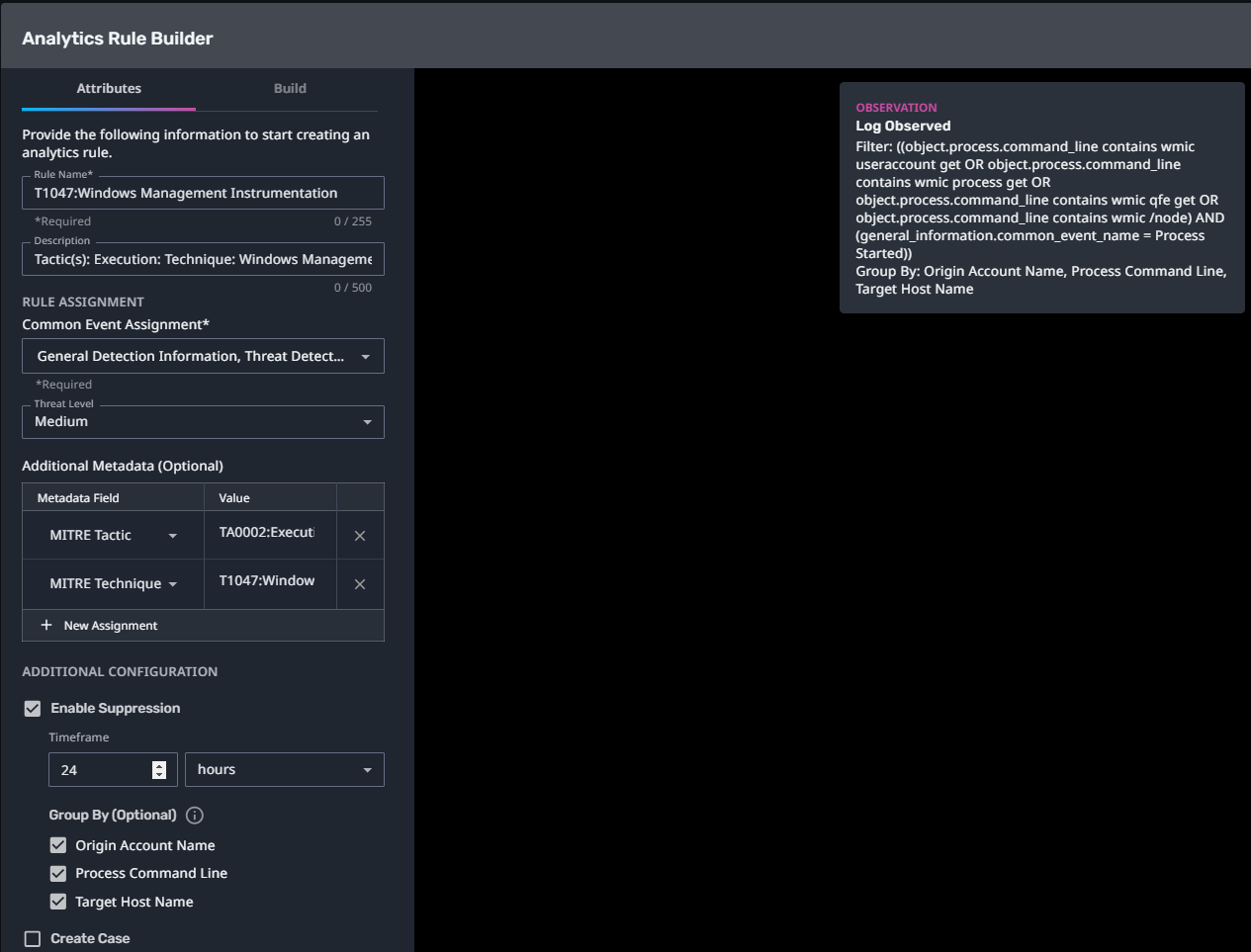
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1057:Process Discovery
Streaming Analytic Filter:
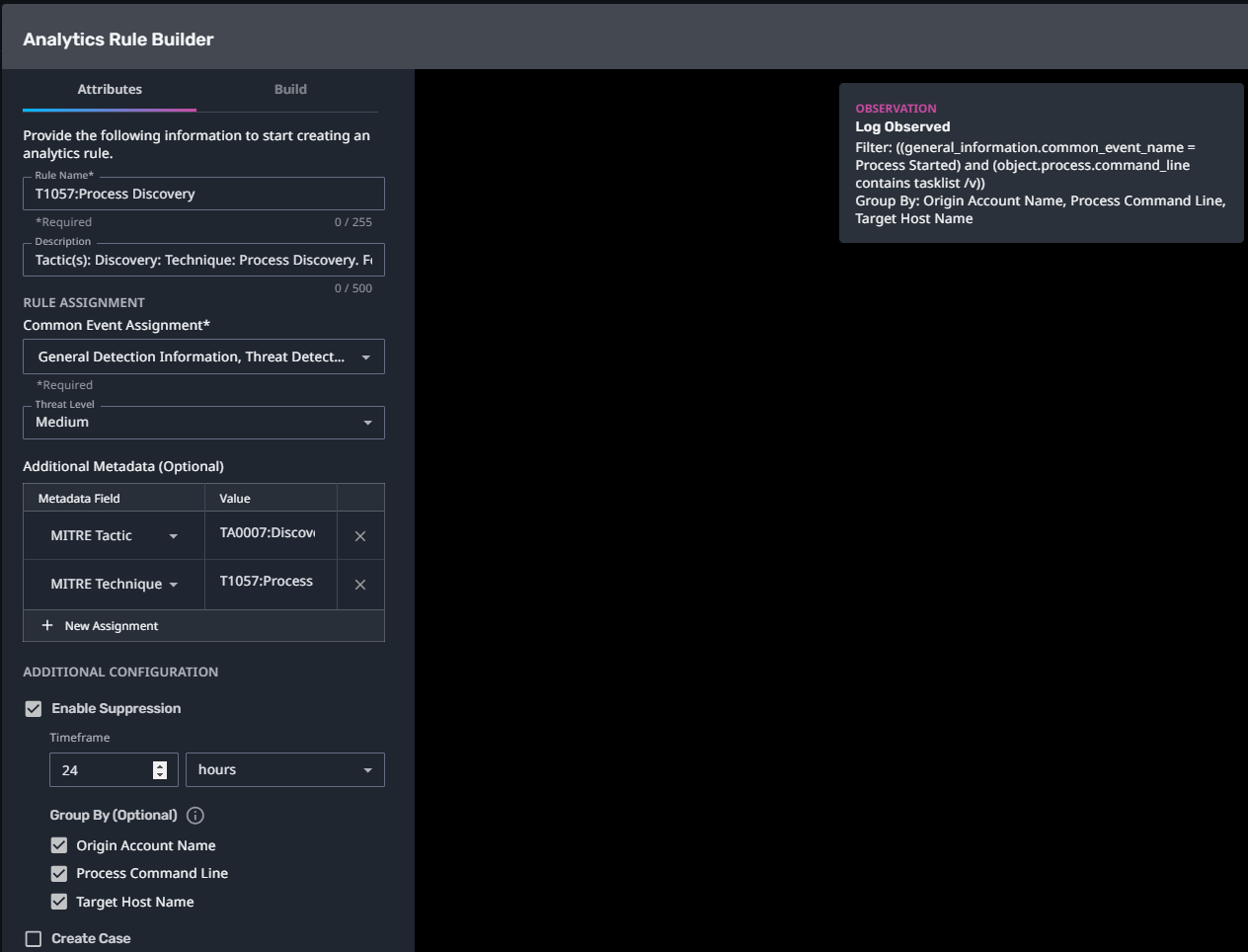
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1059.001:PowerShell
Streaming Analytic Filter:
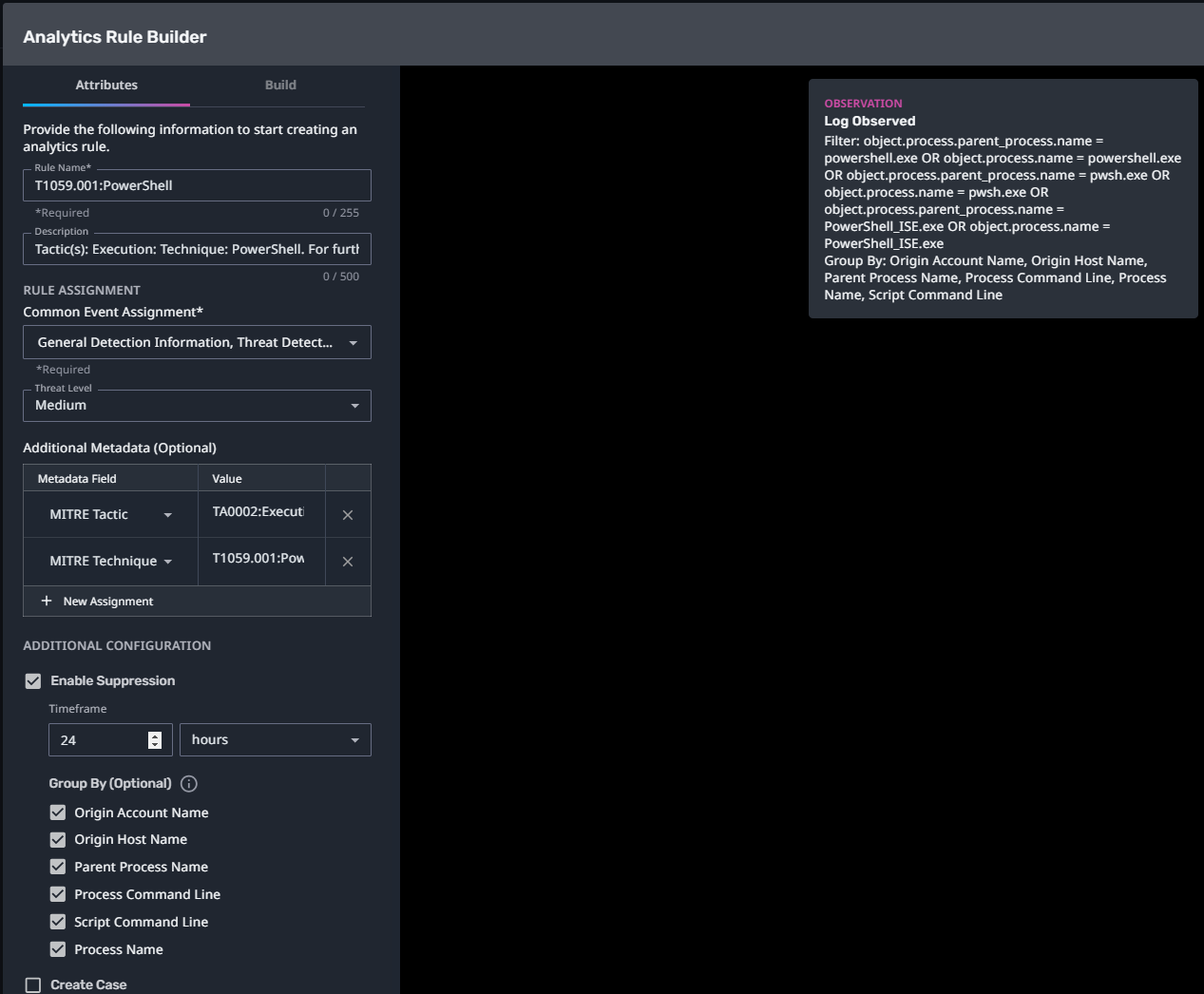
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1069:Permission Groups Discovery
Streaming Analytic Filter:
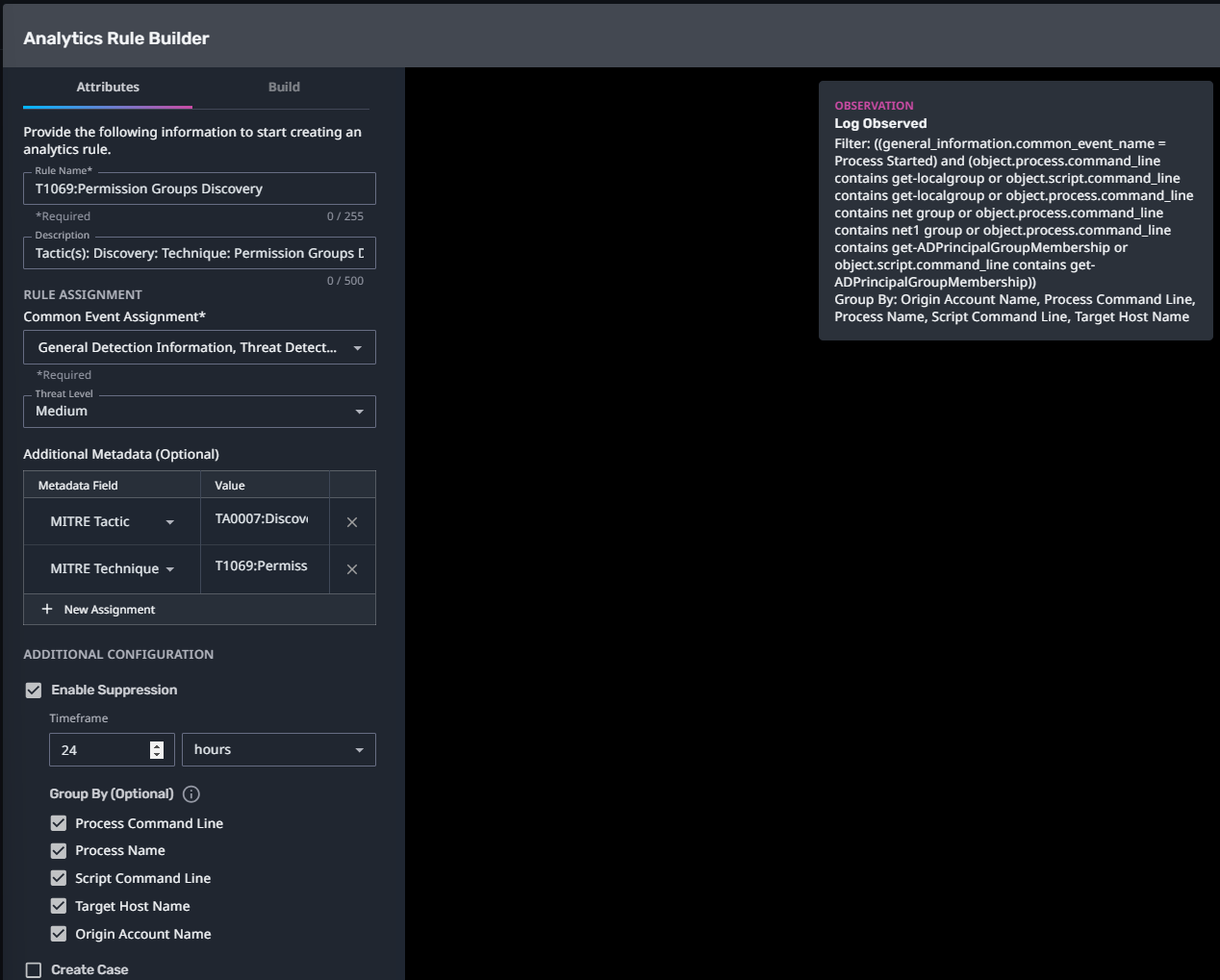
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1070.006:Timestomp
Streaming Analytic Filter:
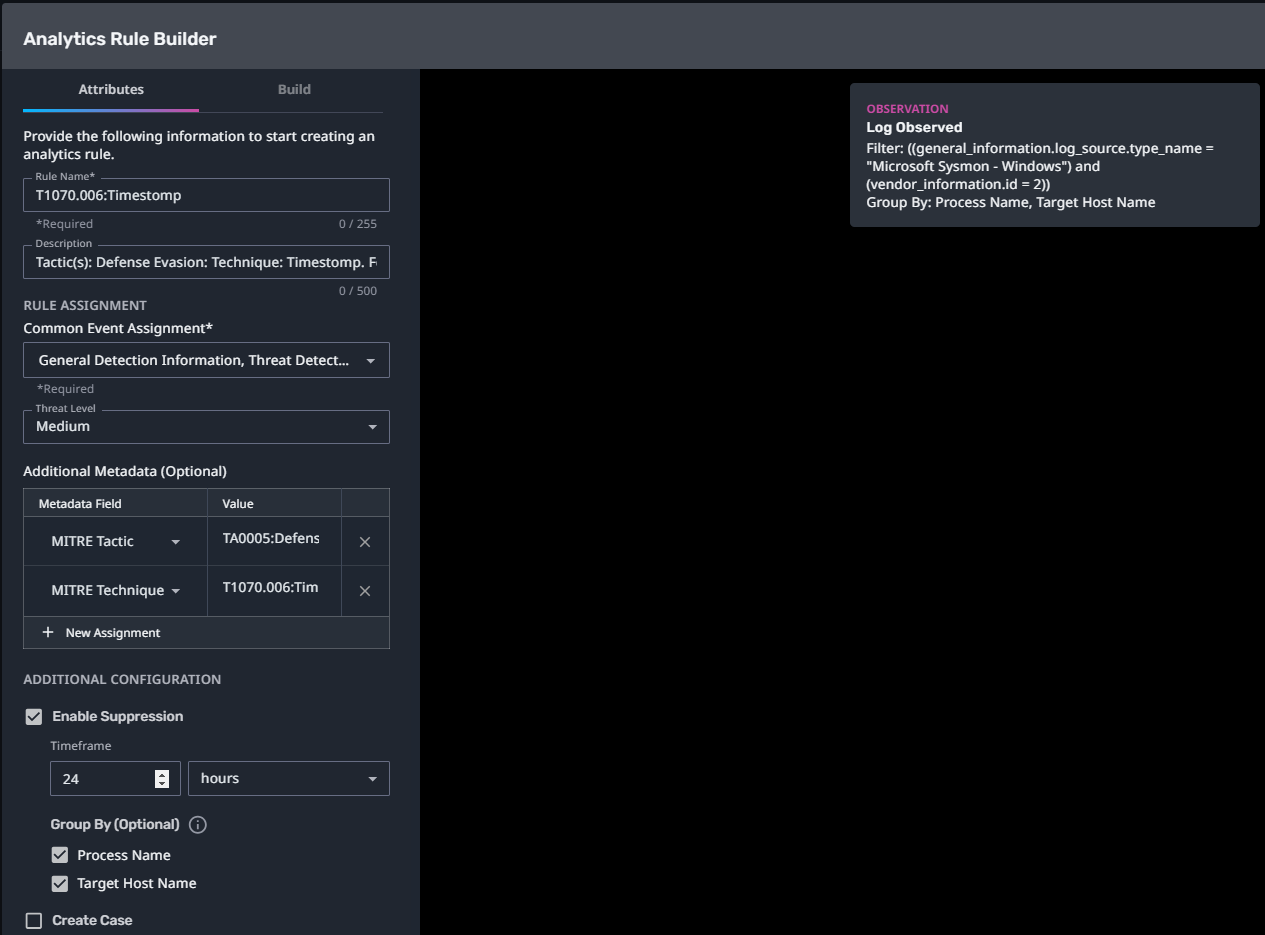
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1082:System Information Discovery
Streaming Analytic Filter:
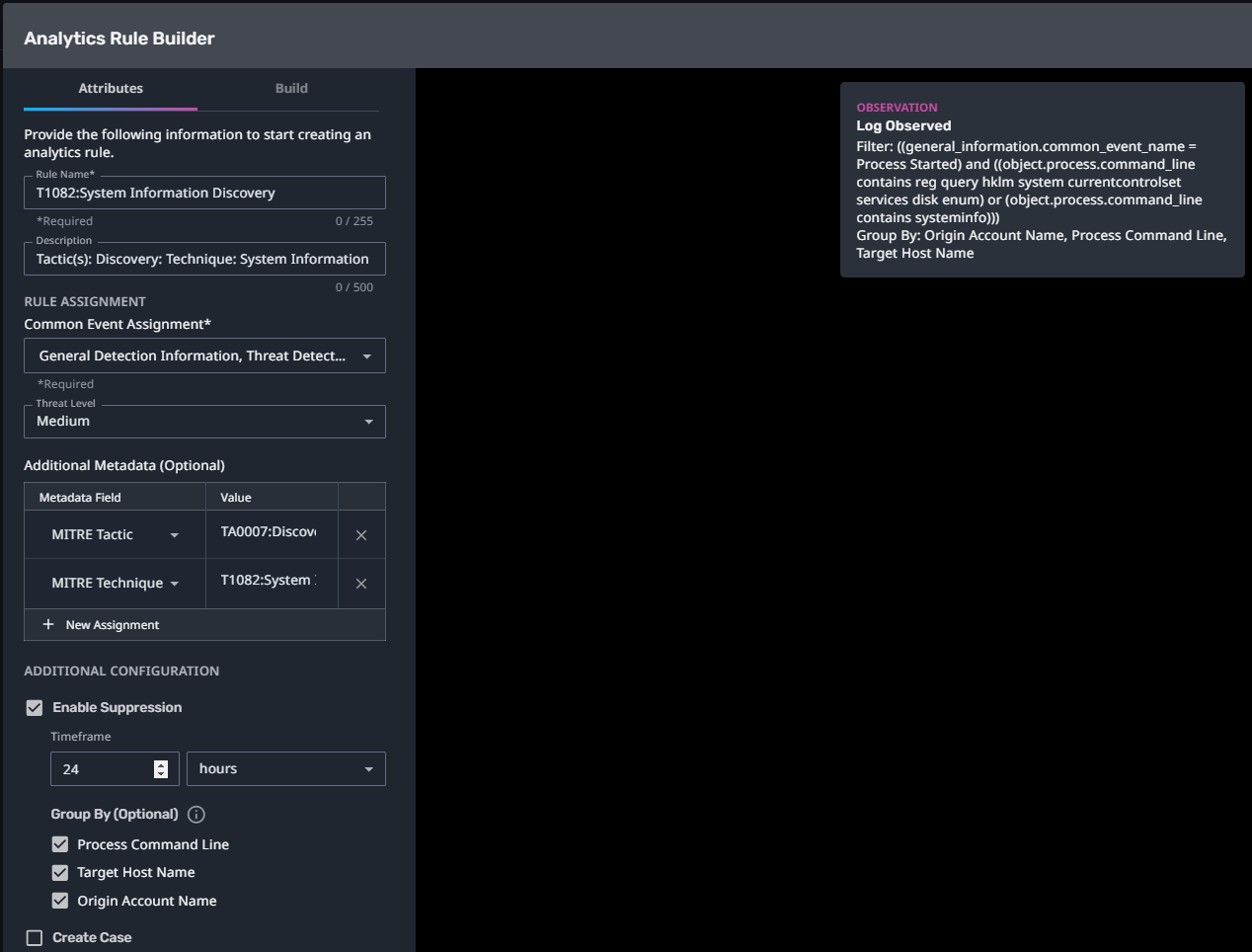
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1087:Account Discovery
Streaming Analytic Filter:
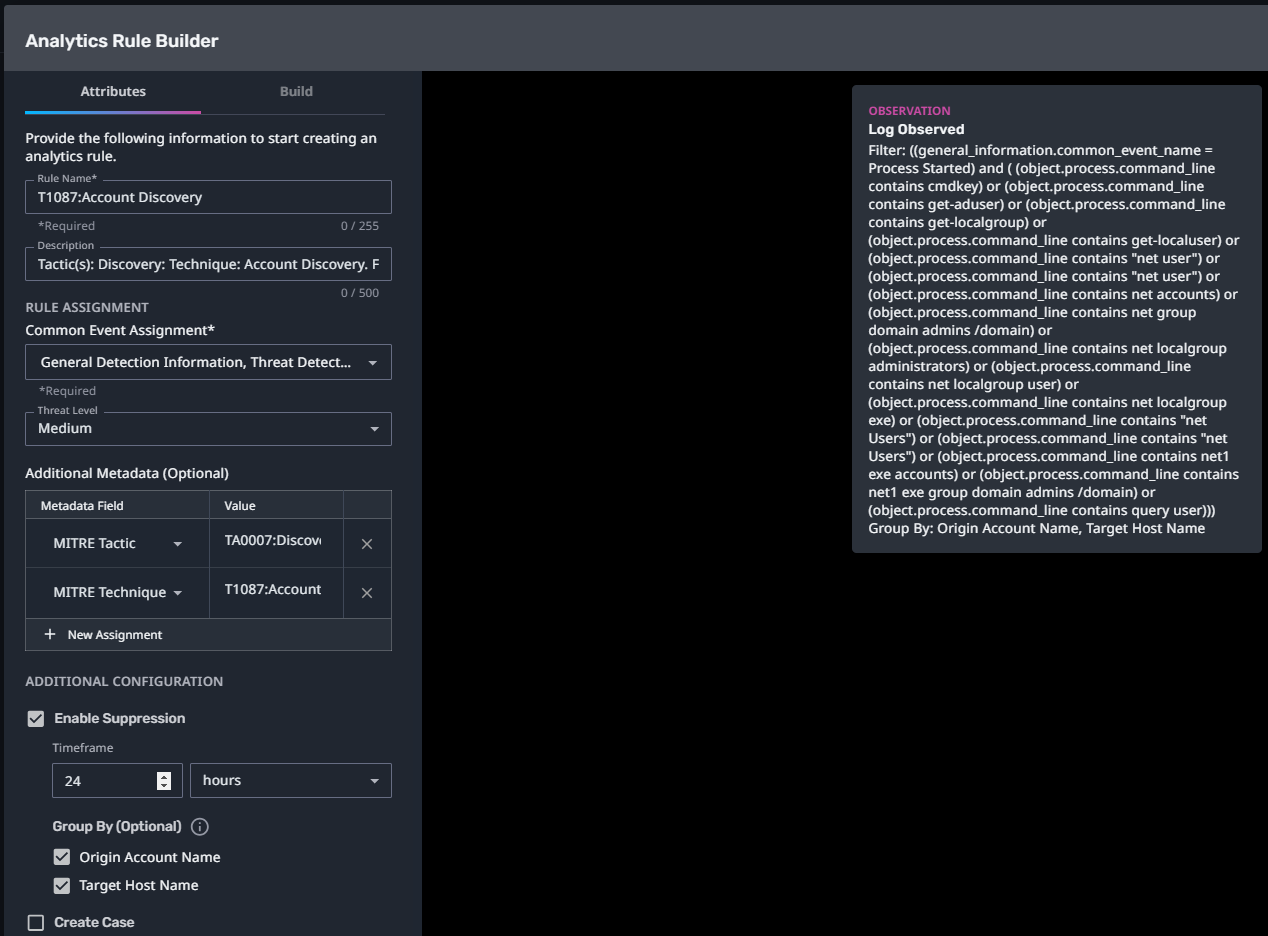
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1218.011:Rundll32
Streaming Analytic Filter:
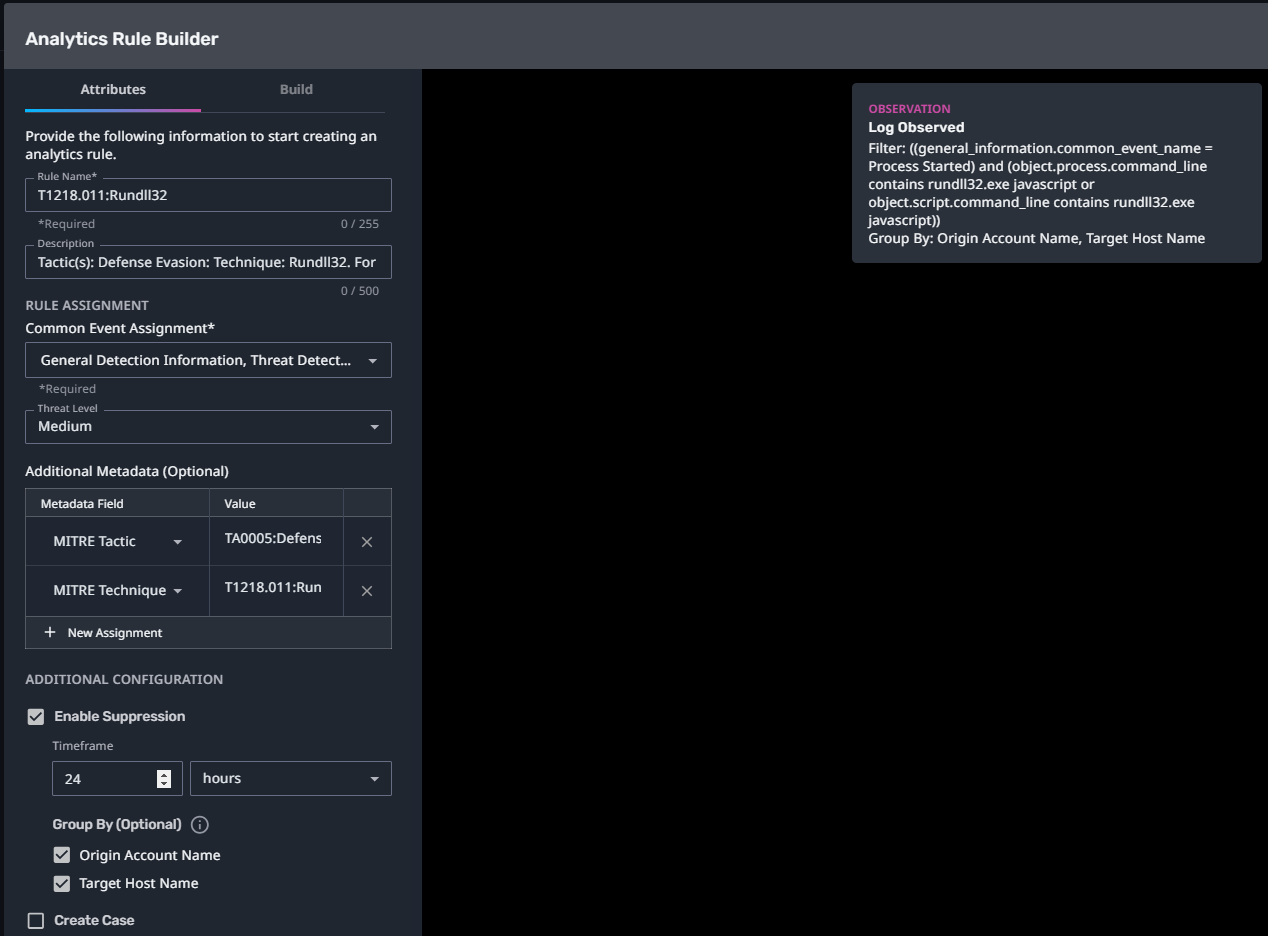
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1490:Inhibit System Recovery
Streaming Analytic Filter:
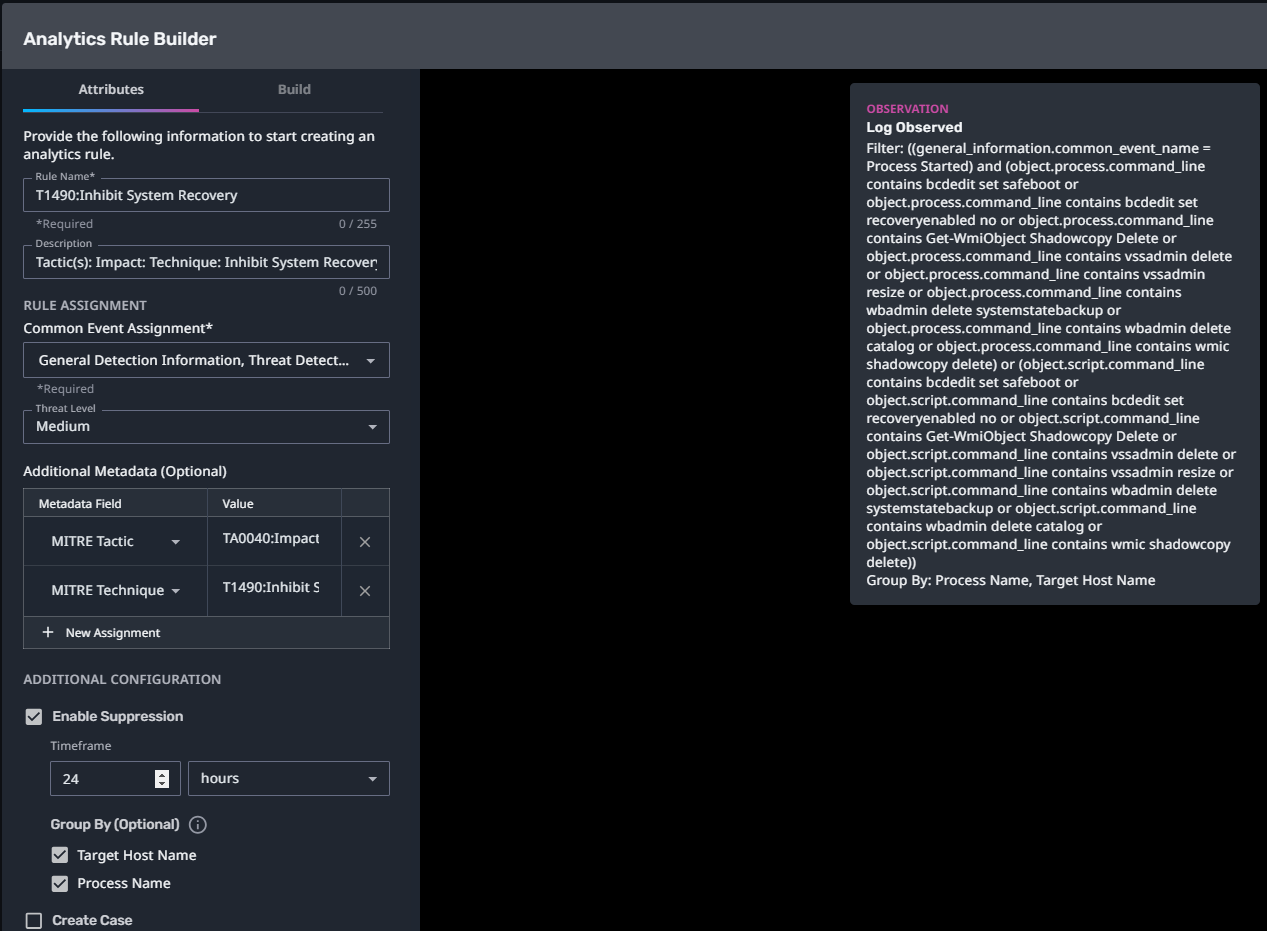
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1547.001:Registry Run Keys/Startup Folder
Streaming Analytic Filter:
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1218.010:Regsvr32
Streaming Analytic Filter:
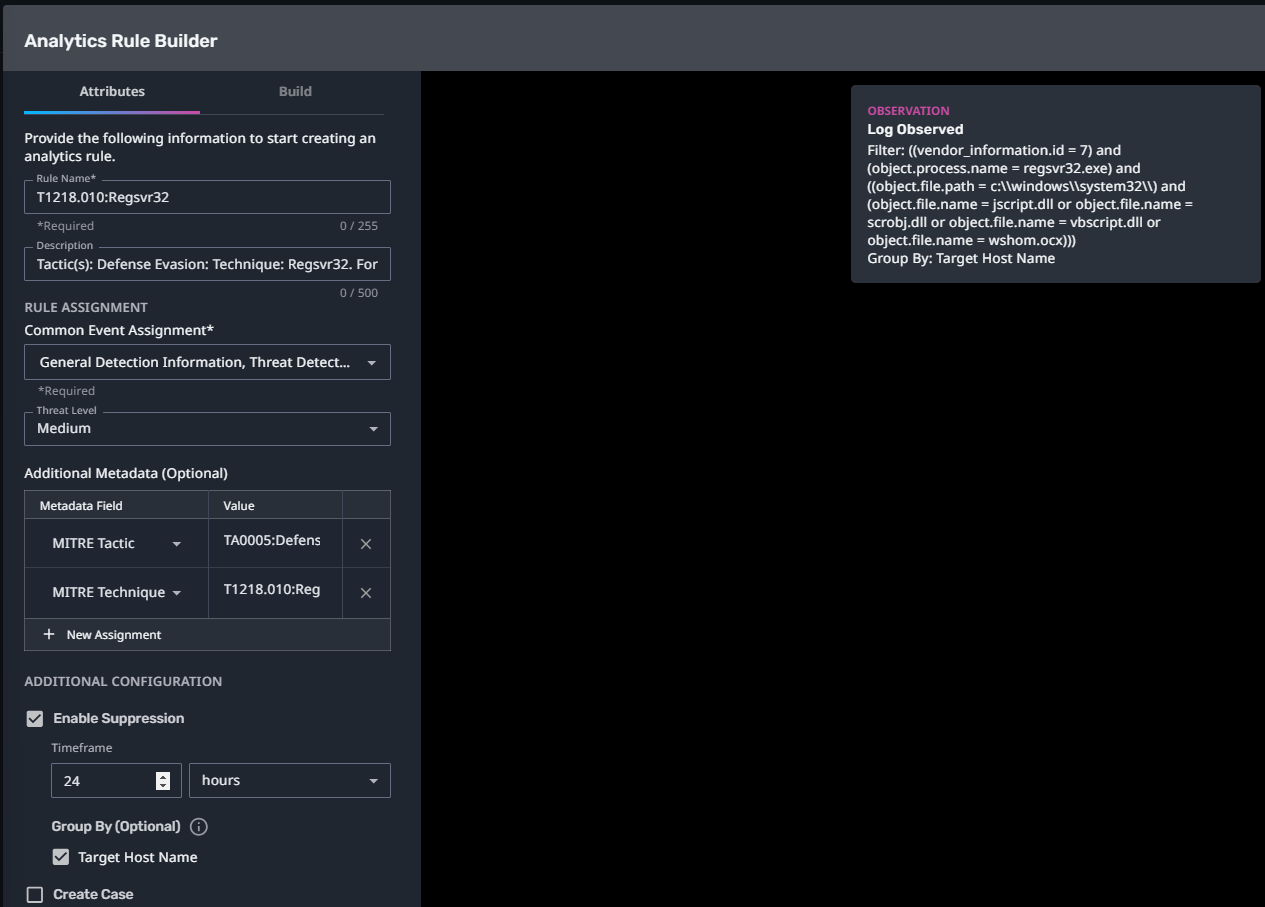
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1558.003:Kerberoasting:Invoke-Kerberoast
Streaming Analytic Filter:
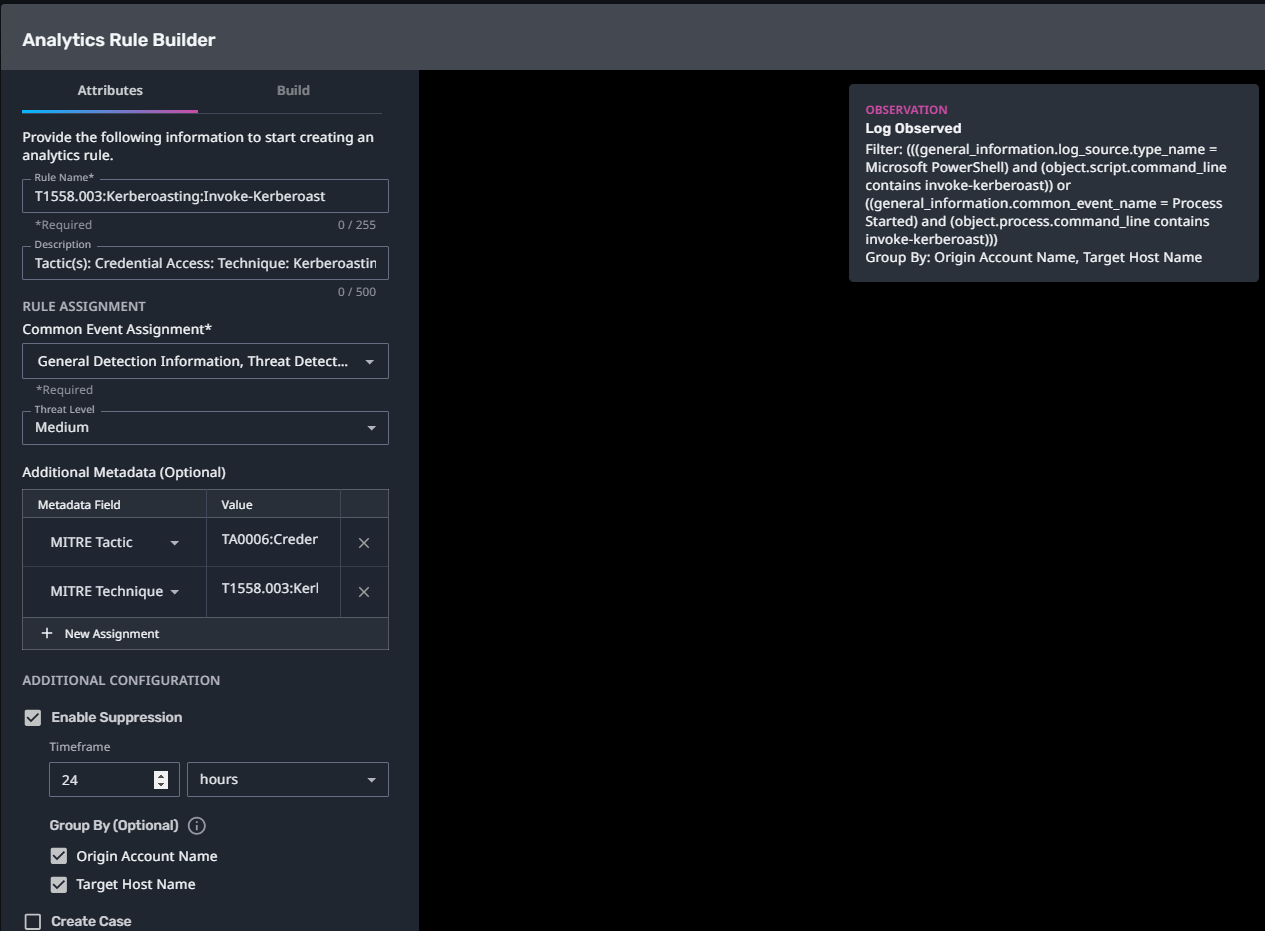
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1569.002:Service Execution
Streaming Analytic Filter:
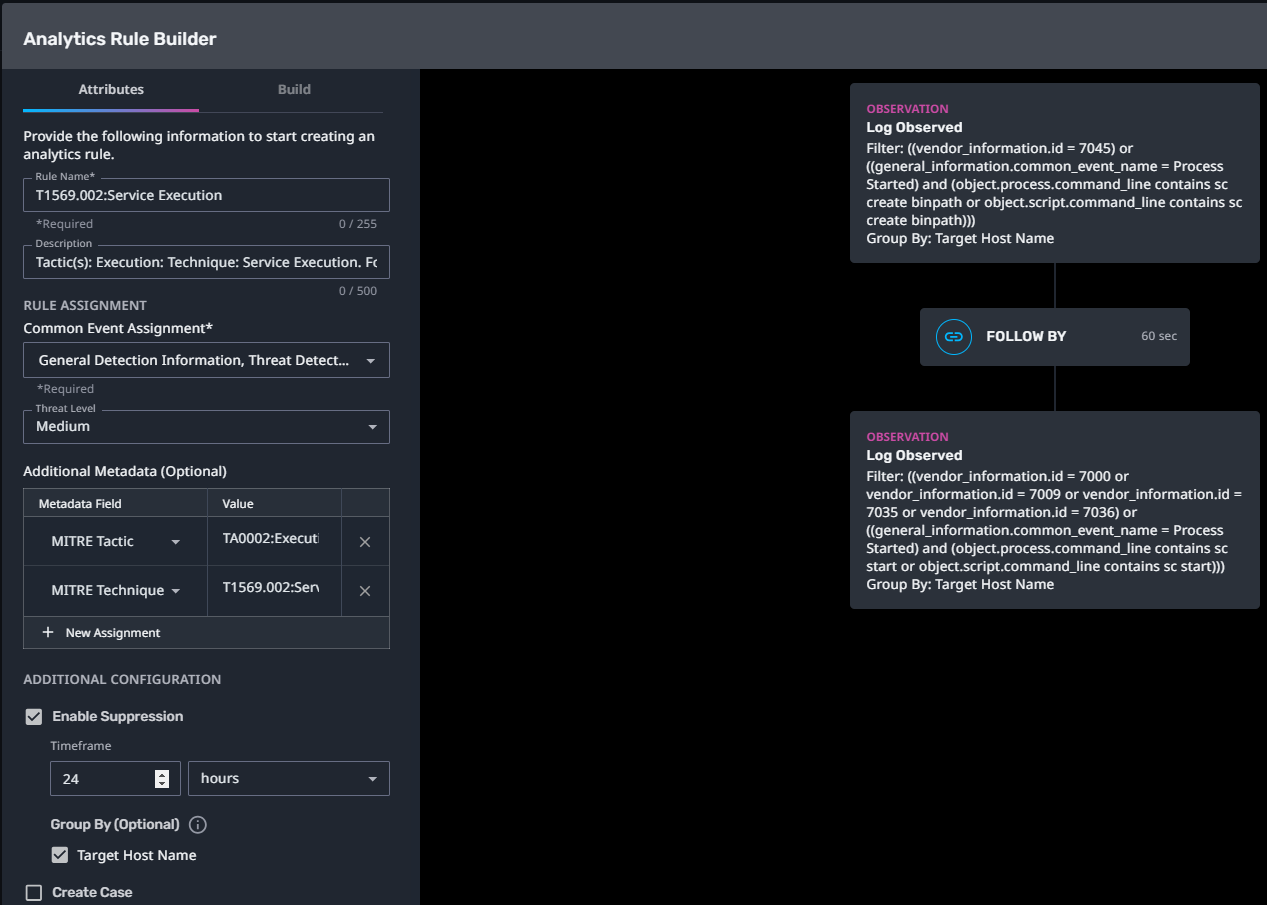
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1550.003:Pass the Ticket
Streaming Analytic Filter:
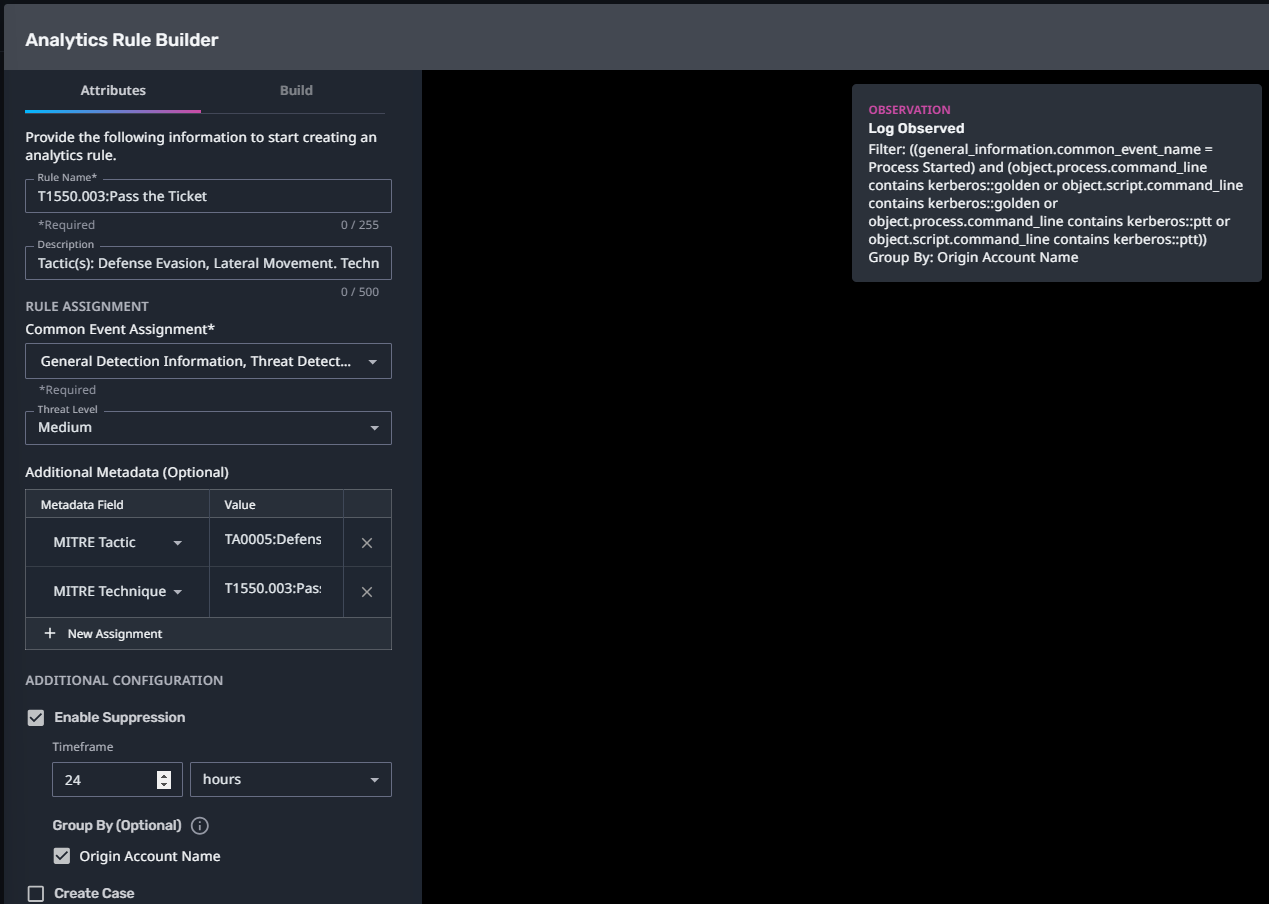
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1562.002:Impair Defenses: Disable Windows Event Logging
Streaming Analytic Filter:
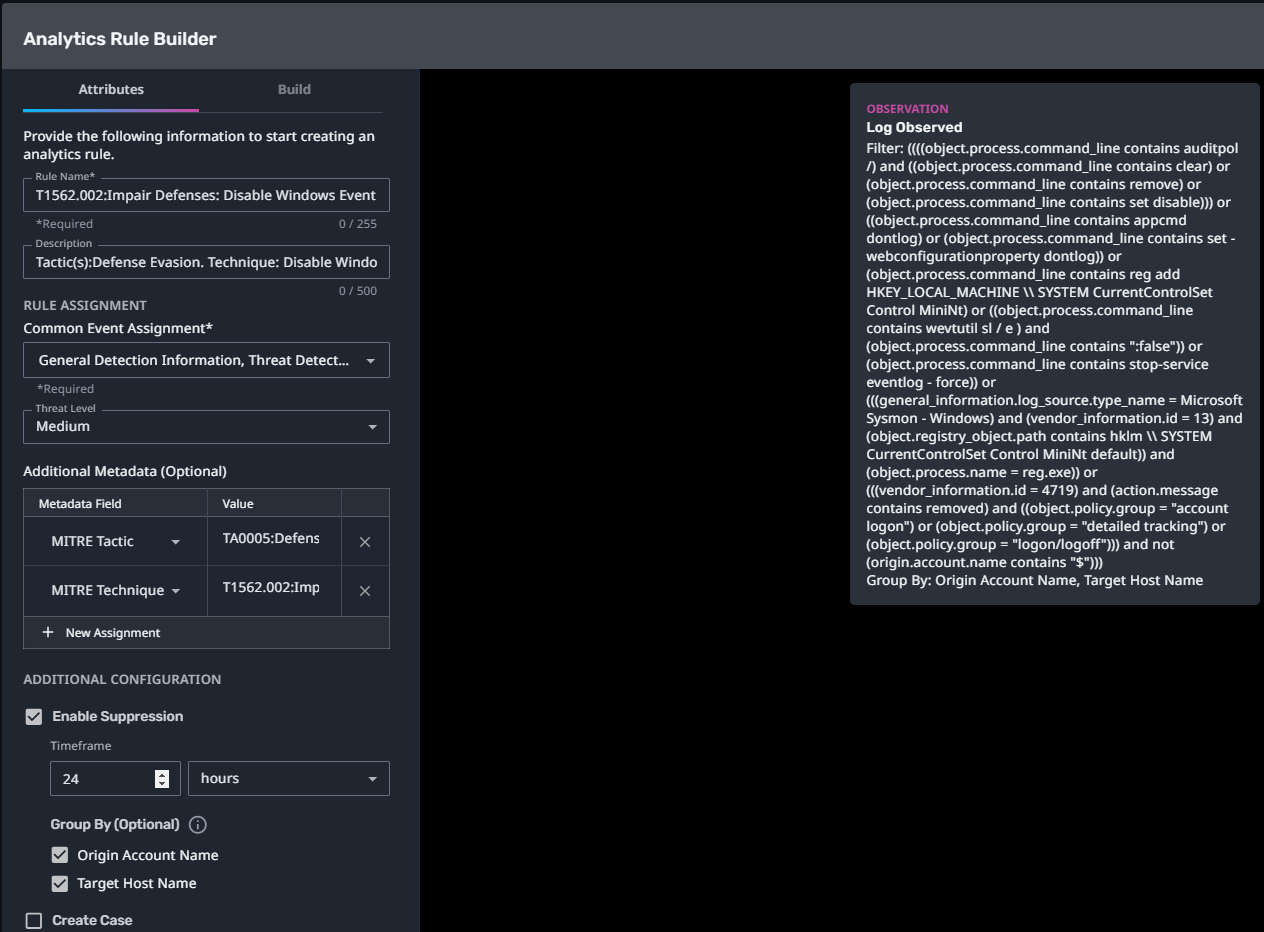
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1106:Native API
Streaming Analytic Filter:
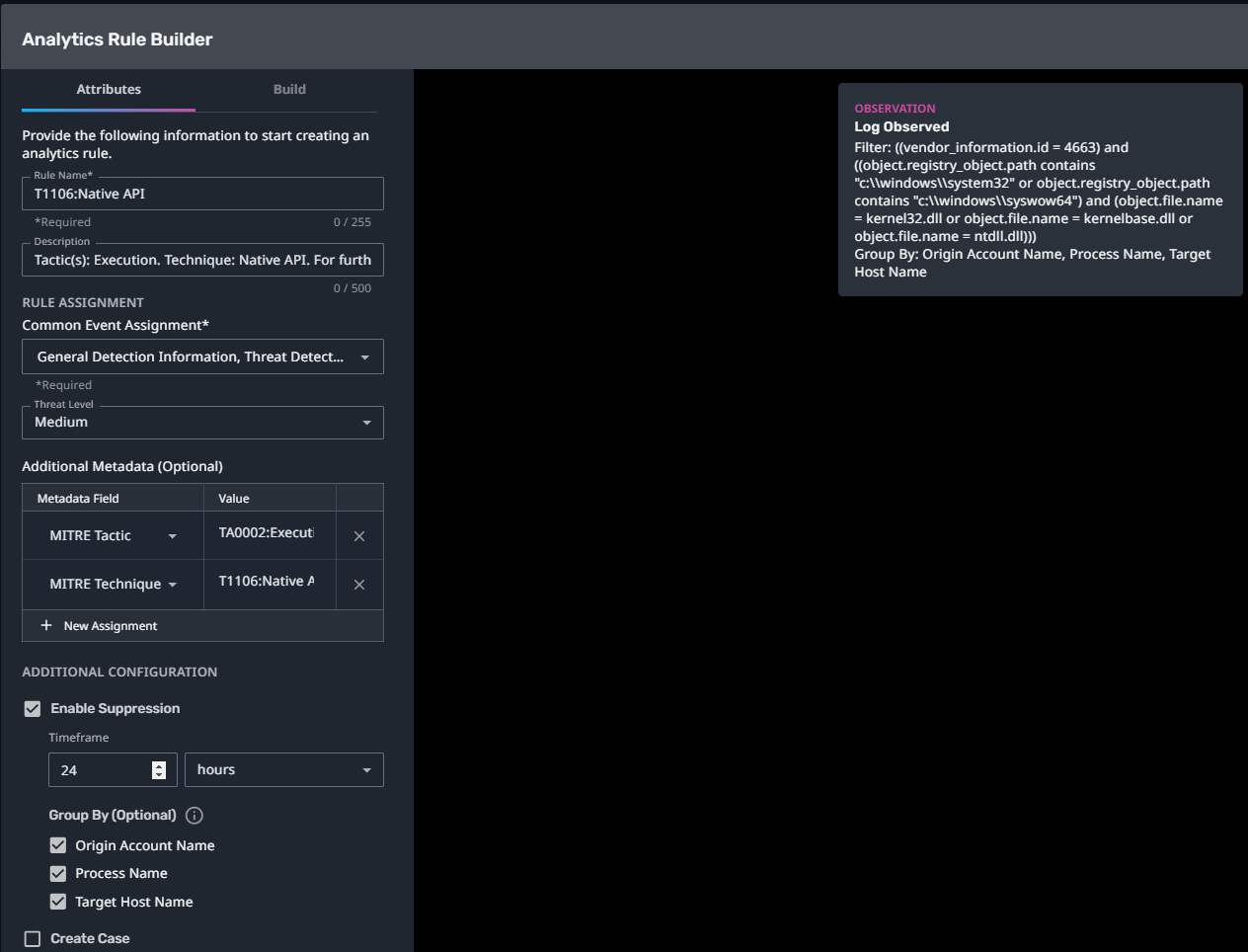
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1134.002:Access Token Manipulation:Create Process with Token
Streaming Analytic Filter:
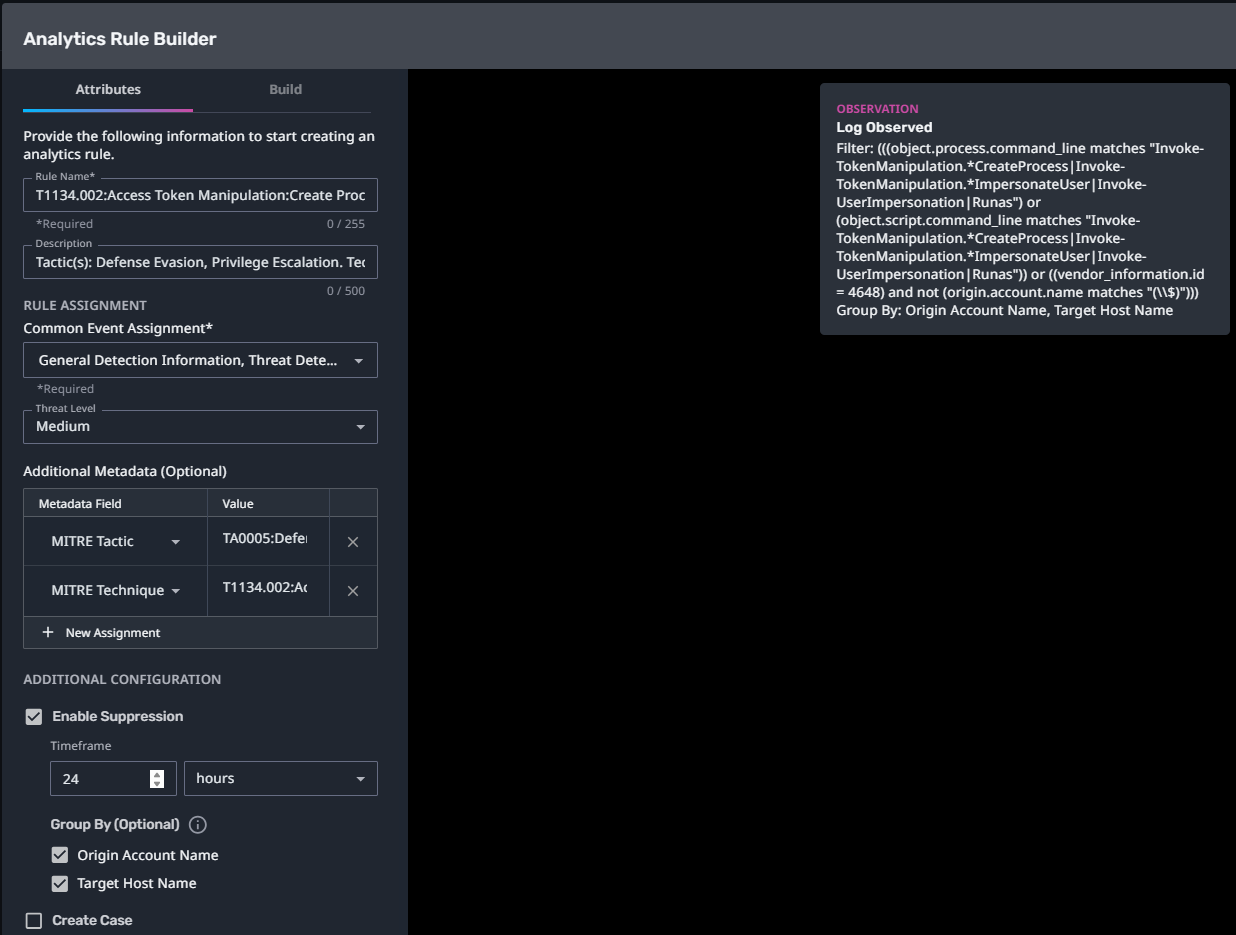
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1190:Exploit Public-Facing Application:SQL Injection4.002:Access Token Manipulation:Create Process with Token
Streaming Analytic Filter:
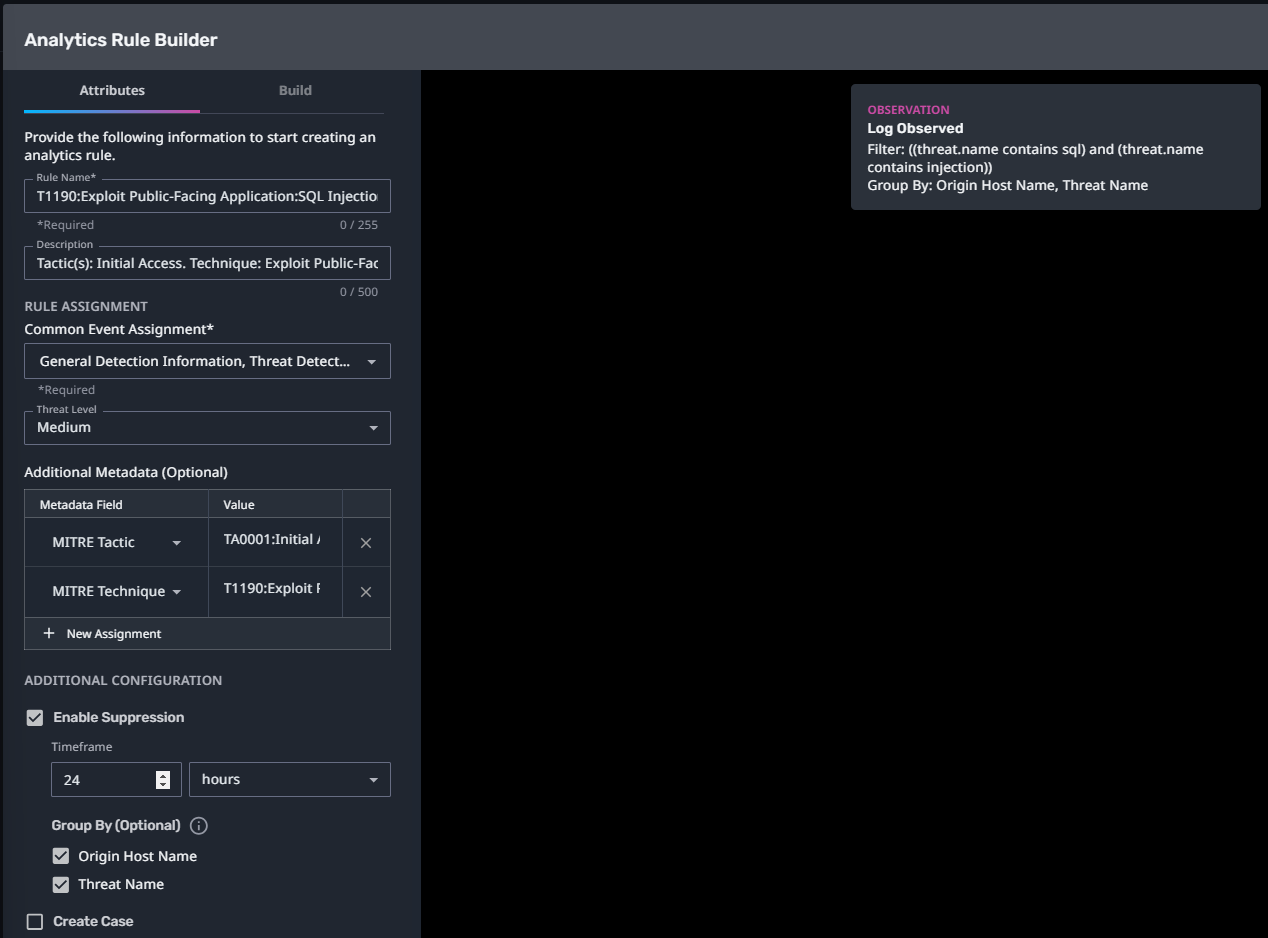
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1484.002:Domain Trust Modification
Streaming Analytic Filter:
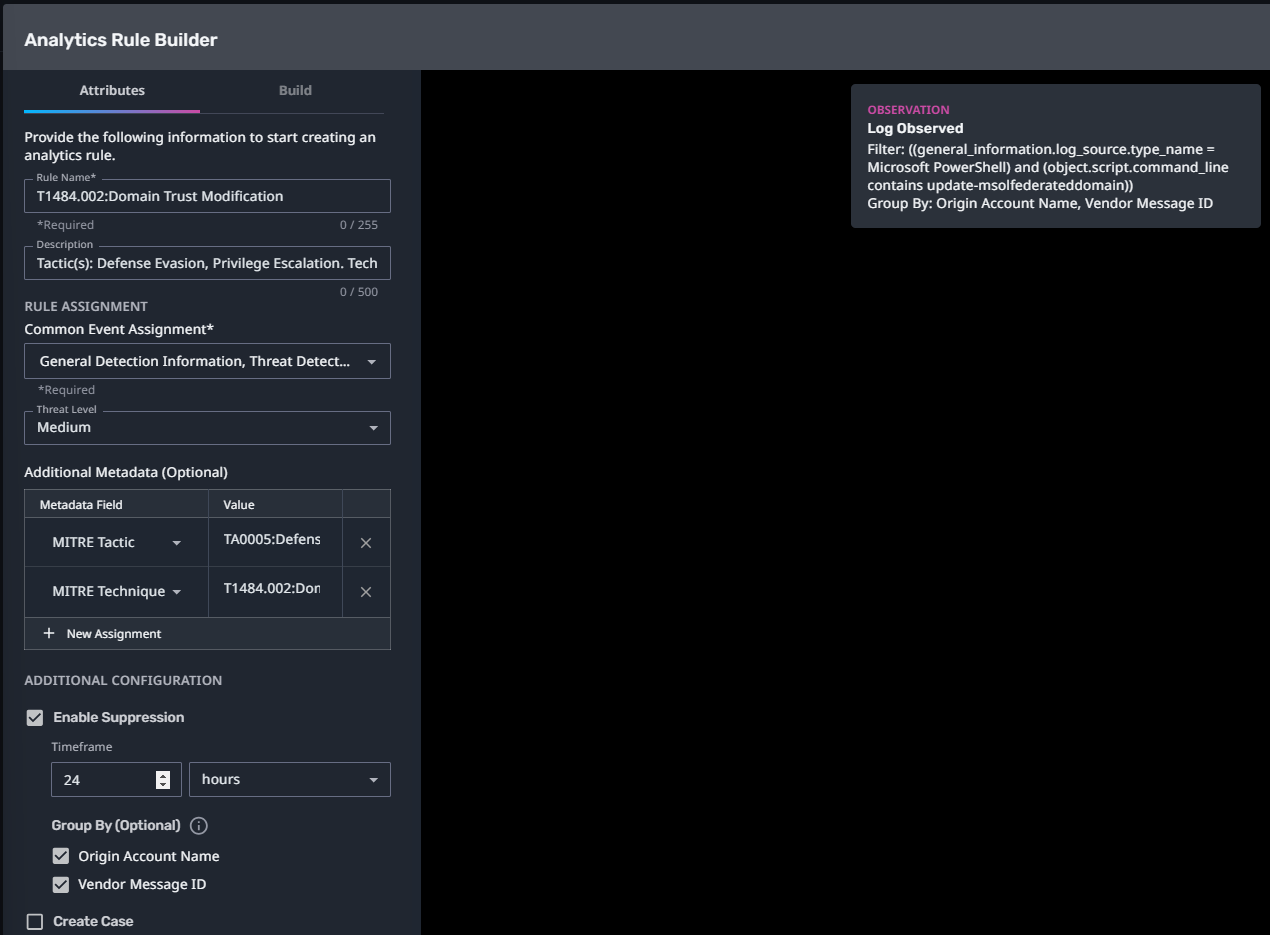
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1489:Service Stop
Streaming Analytic Filter:
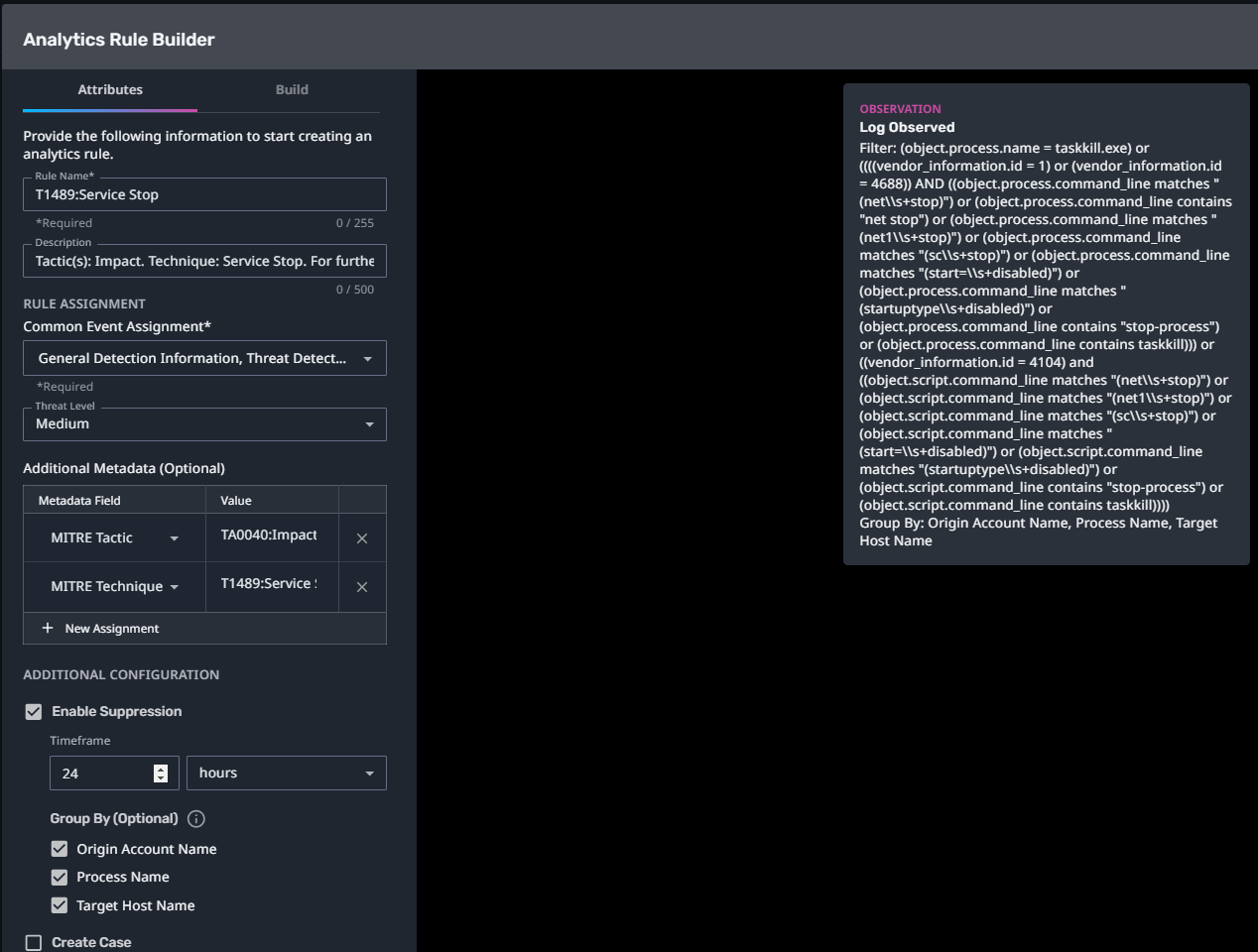
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1539:Steal Web Session Cookie
Streaming Analytic Filter:
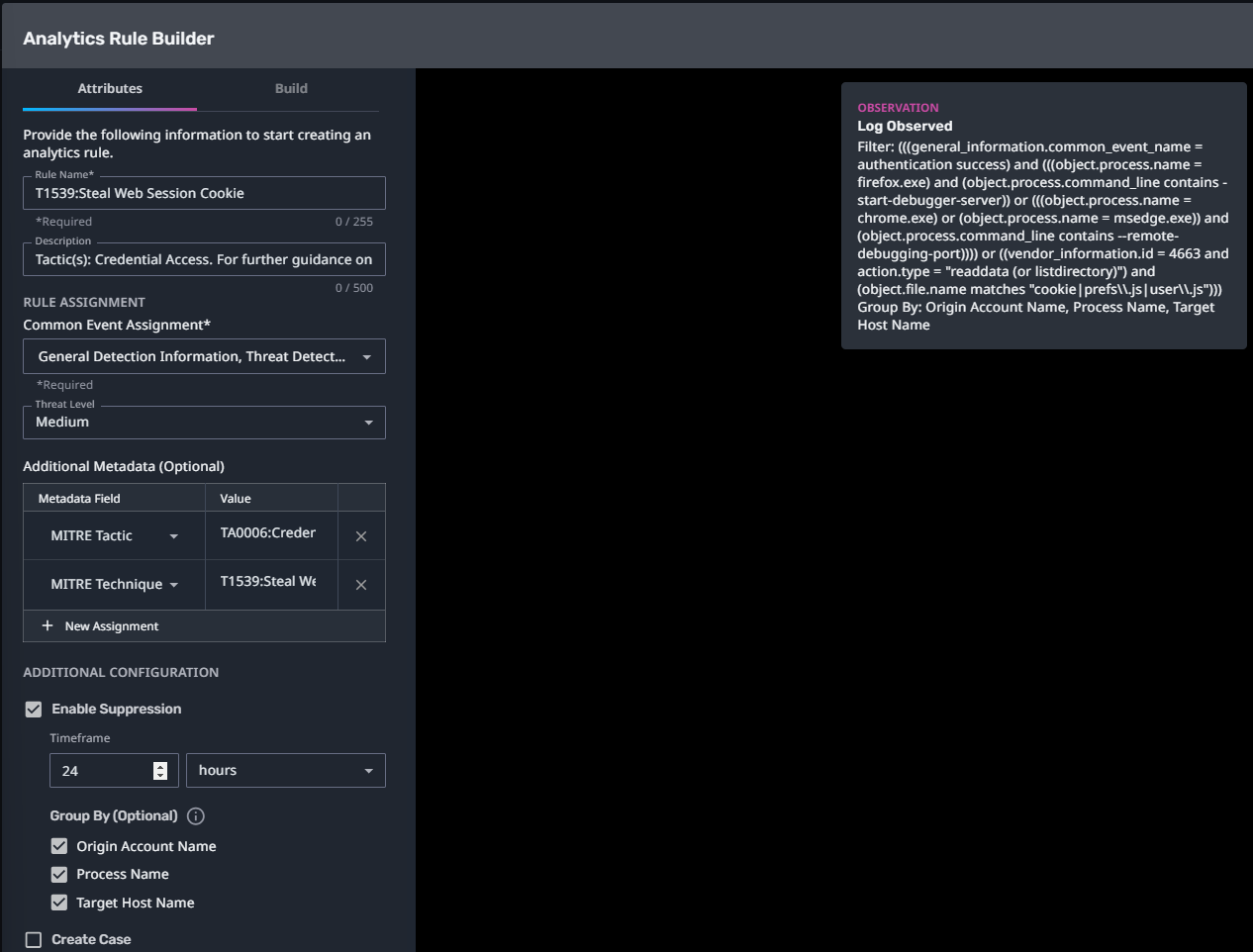
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1621:MFA Request Generation:Rapid Okta AD Authentication Success
Streaming Analytic Filter:
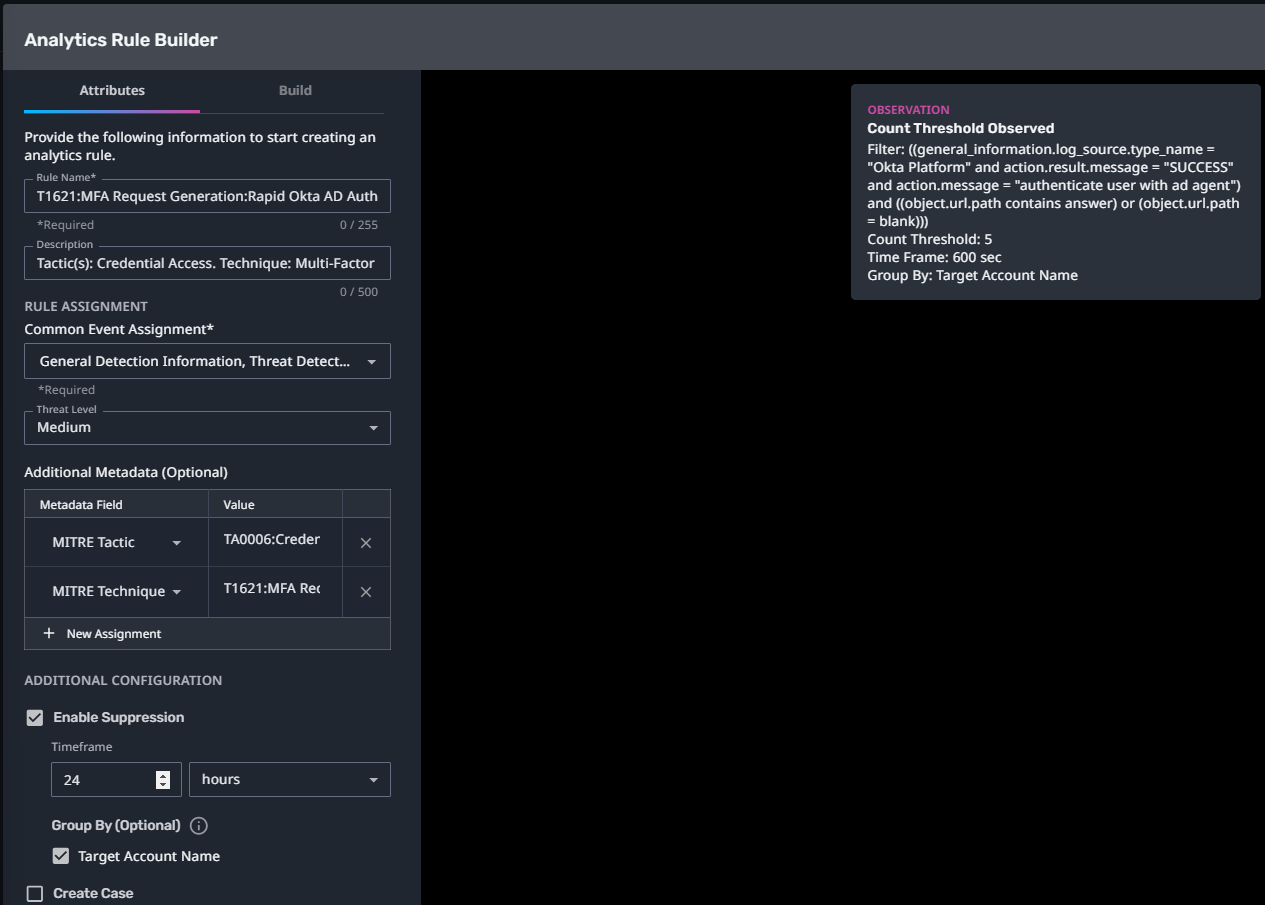
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1114.003:Email Forwarding
Streaming Analytic Filter:
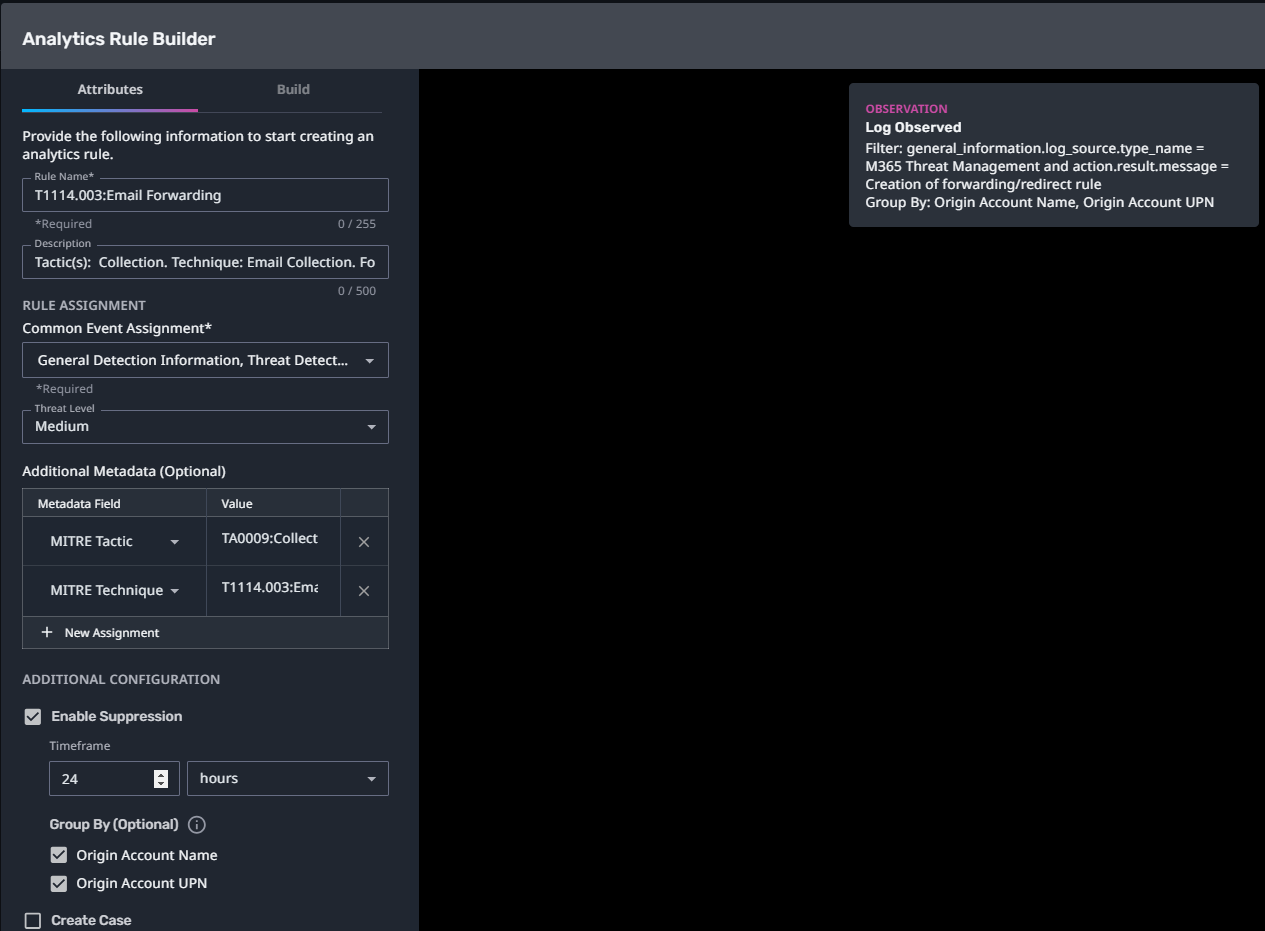
Configuration Notes:
Enable “Create Case” to automatically create a case upon detection.
This rule requires the M365 Threat Management log source.
T1083:File and Directory Discovery
Streaming Analytic Filter:
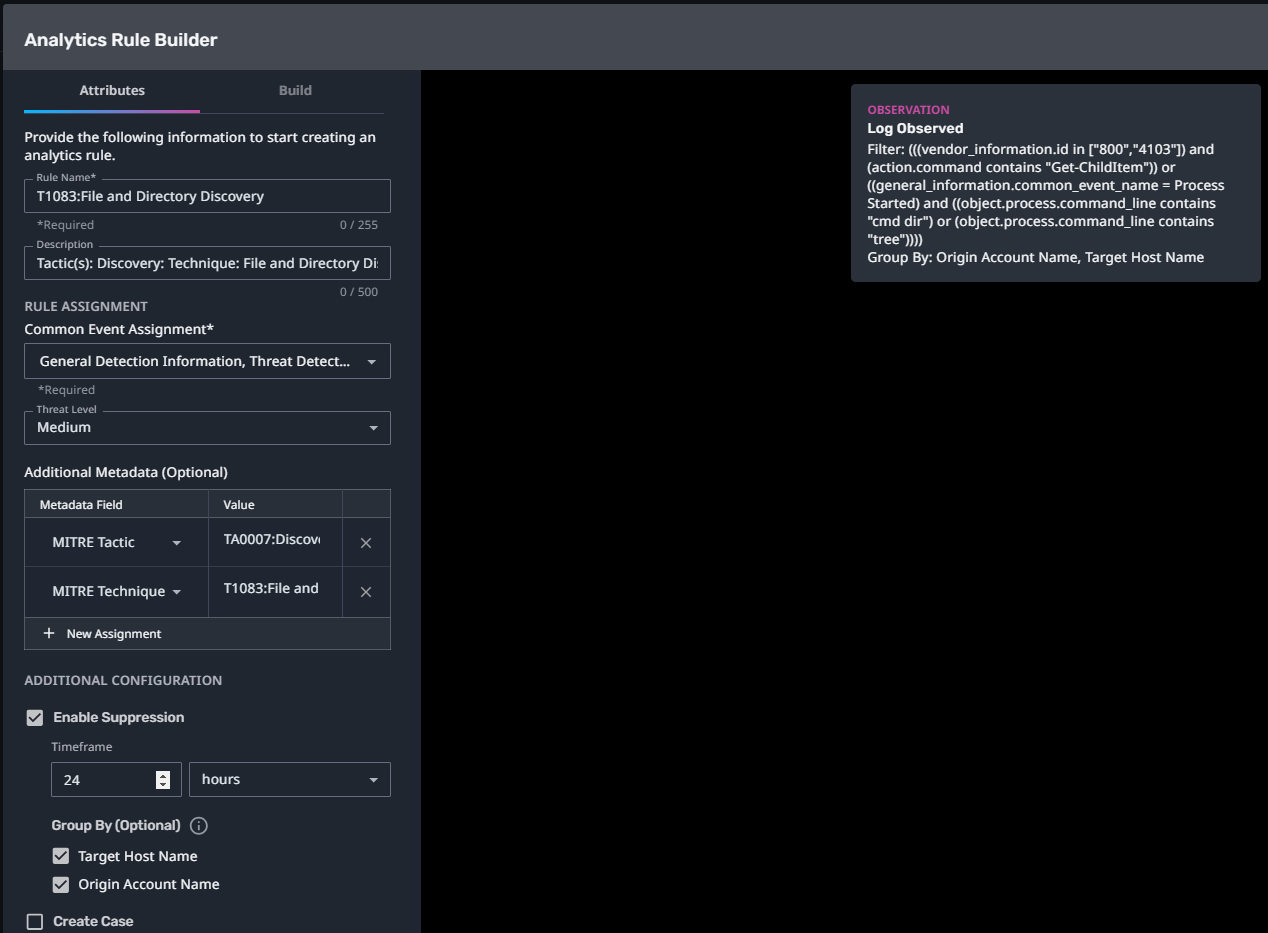
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1566.001:Spearphishing Attachment
Streaming Analytic Filter:
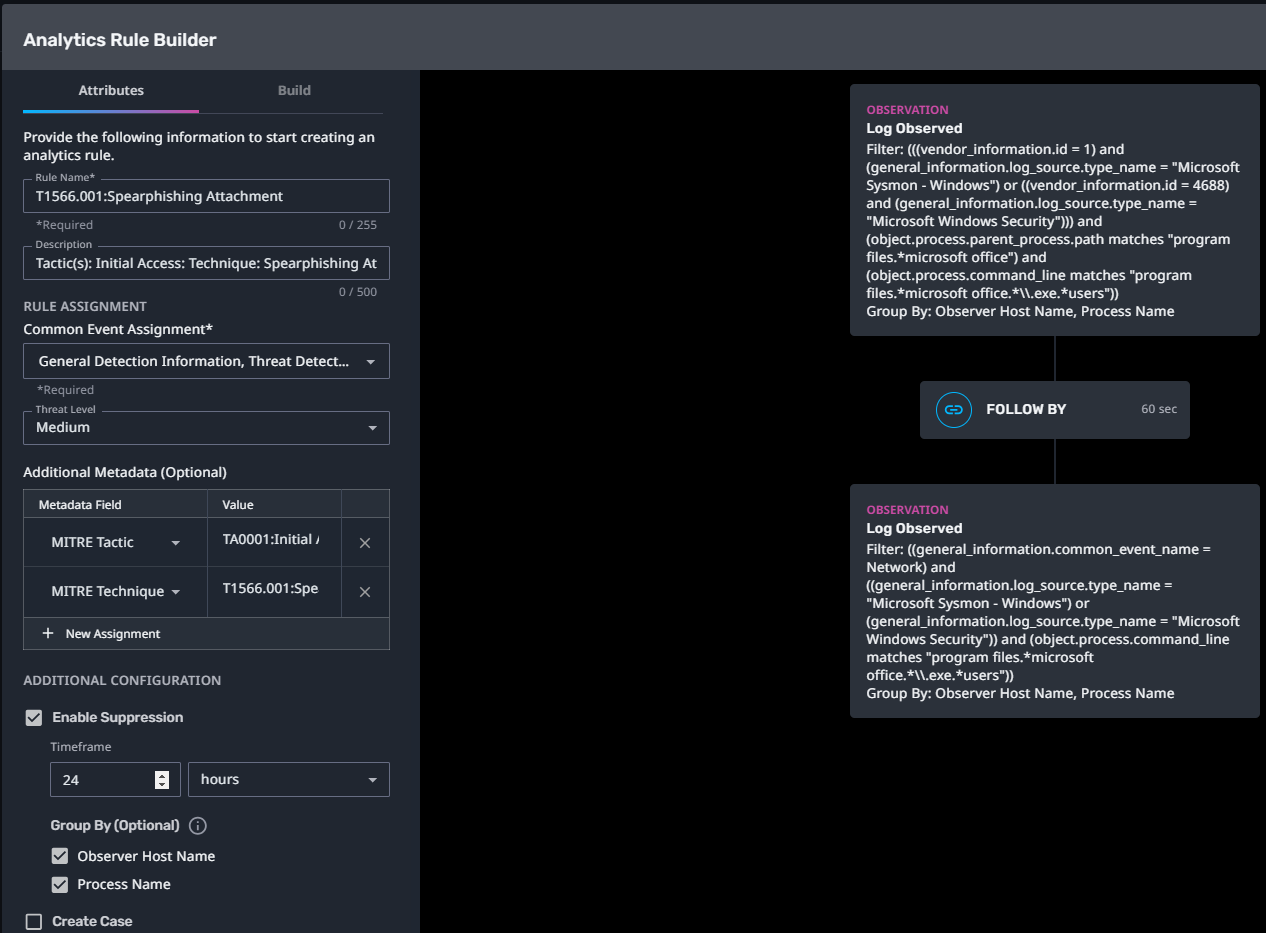
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1566.002:Spearphishing Link
Streaming Analytic Filter:
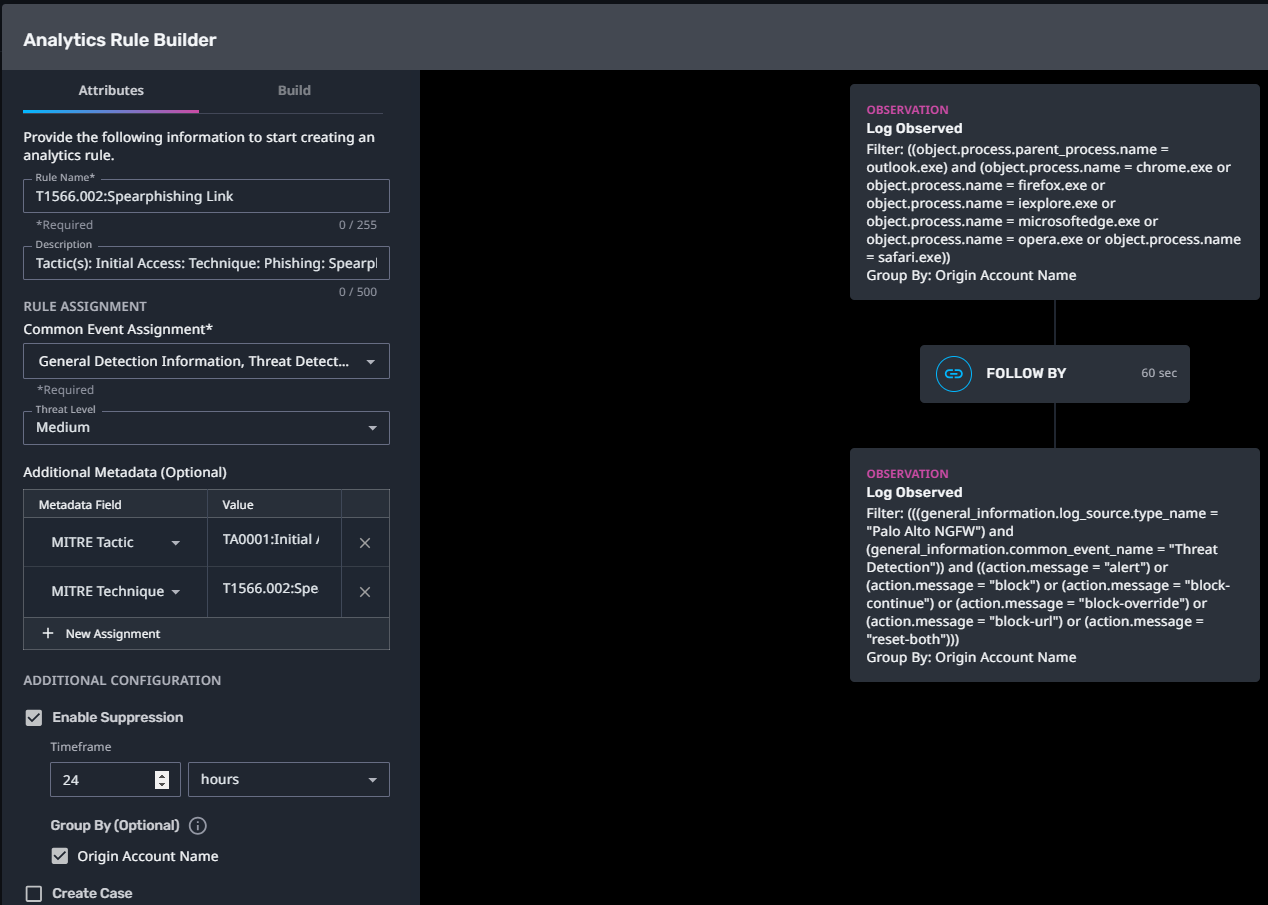
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1558.003:Kerberoasting:TGS Requests for Multiple Services
Streaming Analytic Filter:
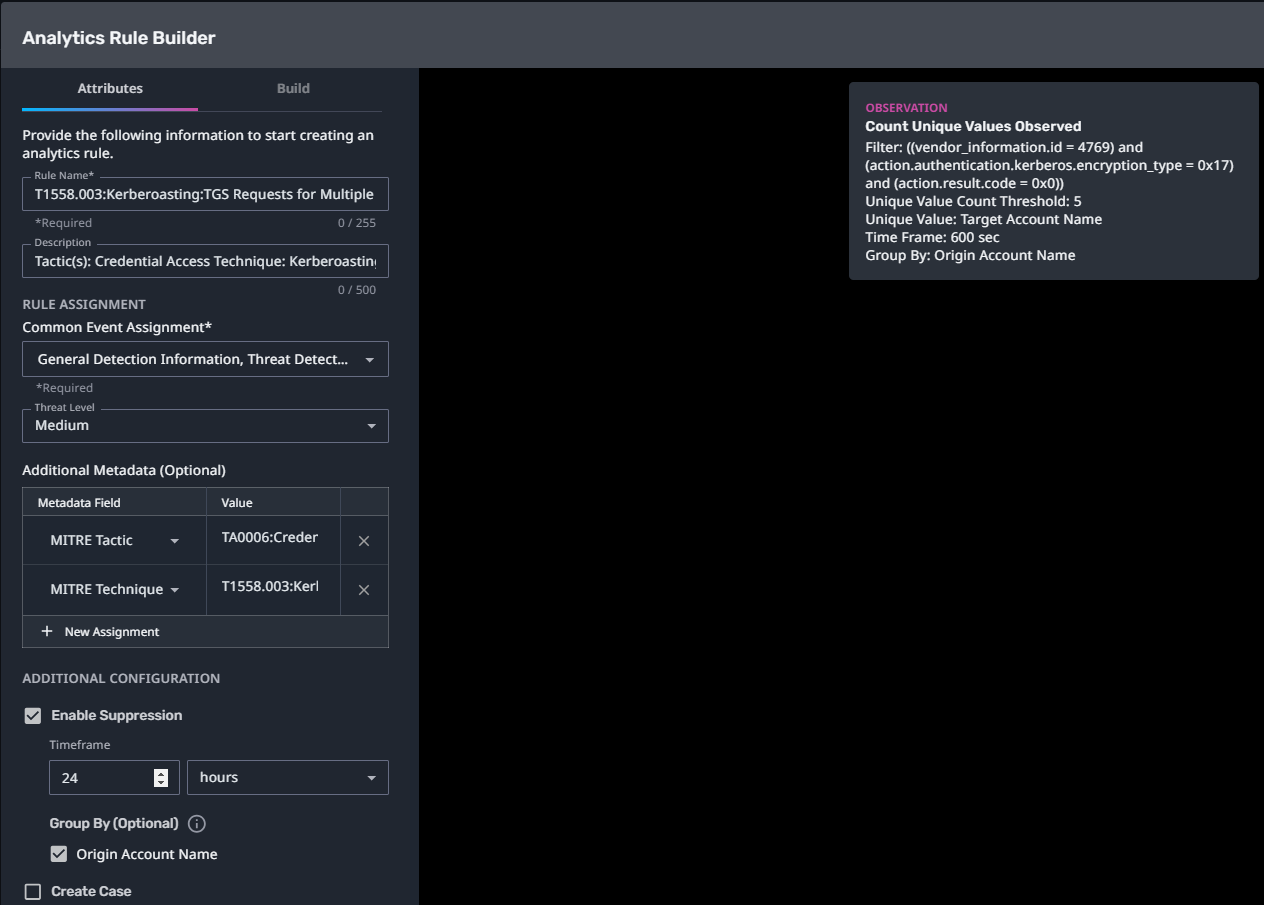
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1090.001:Proxy
Streaming Analytic Filter:
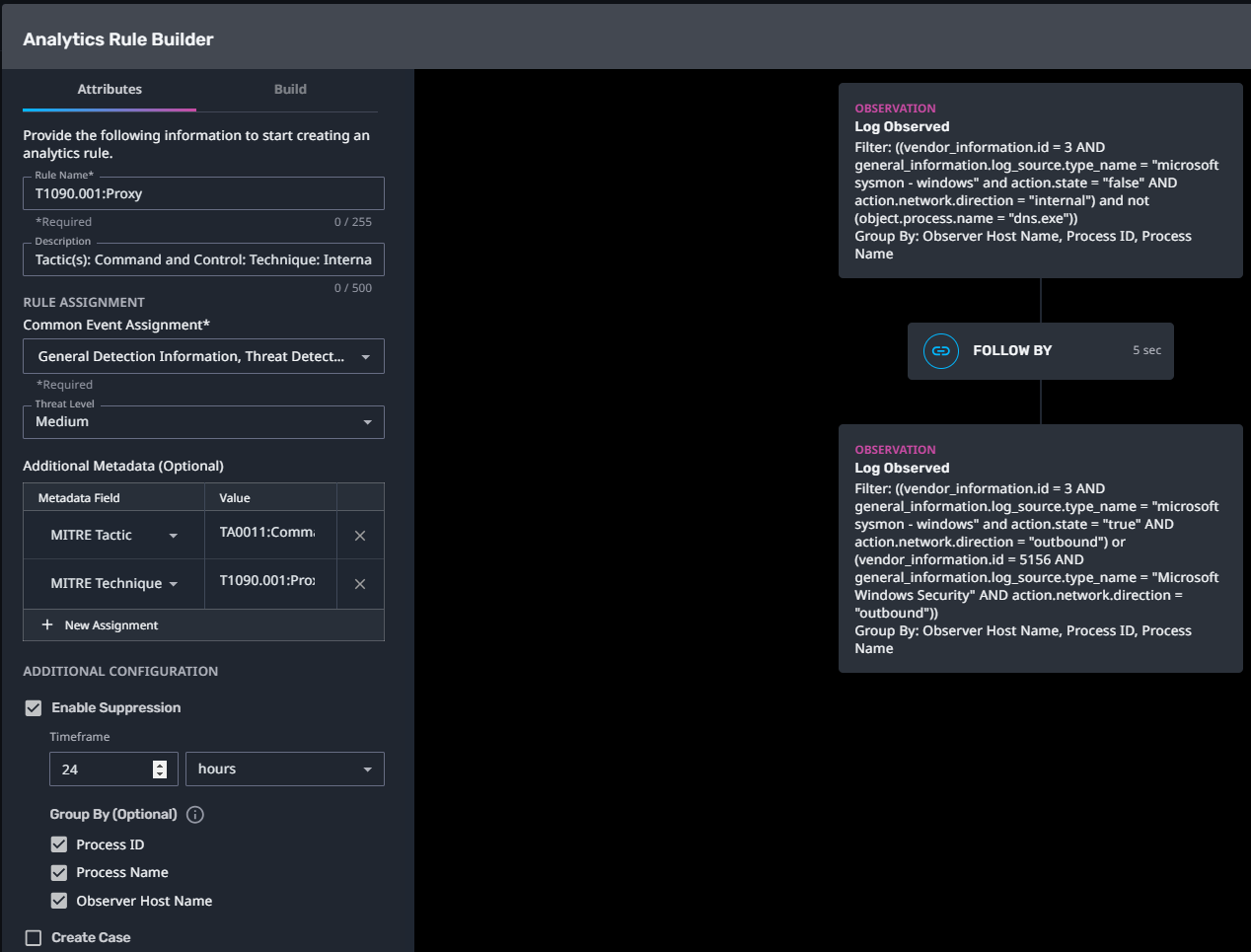
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1078.004:Cloud Accounts
Streaming Analytic Filter:
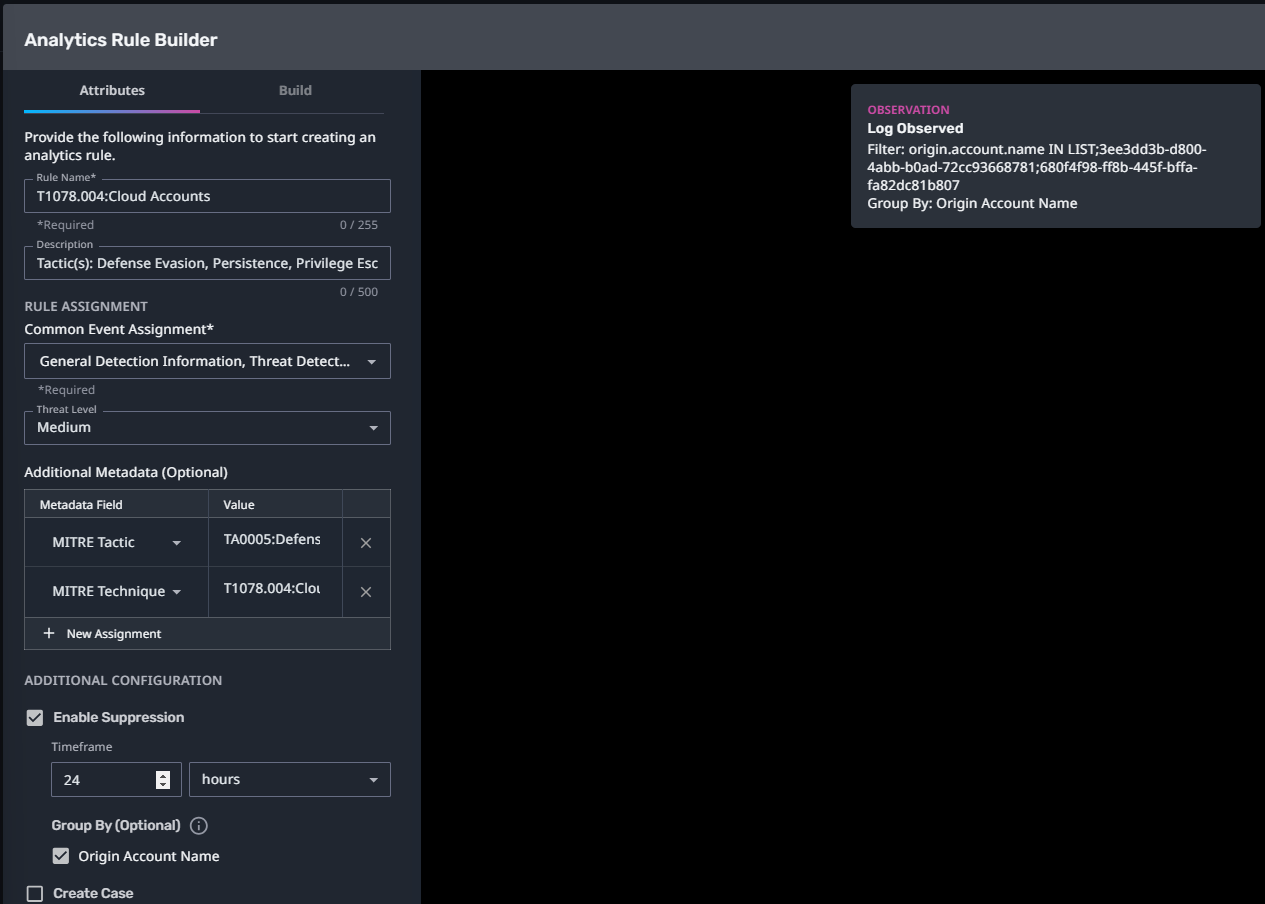
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
This rule requires a List to be populated before enabling. Populate the “MA:Cloud Accounts” list with a list of cloud administrative accounts applicable to your company’s network, applications, services, etc.
T1059.001:PowerShell:ProviderLifeCycle
Streaming Analytic Filter:
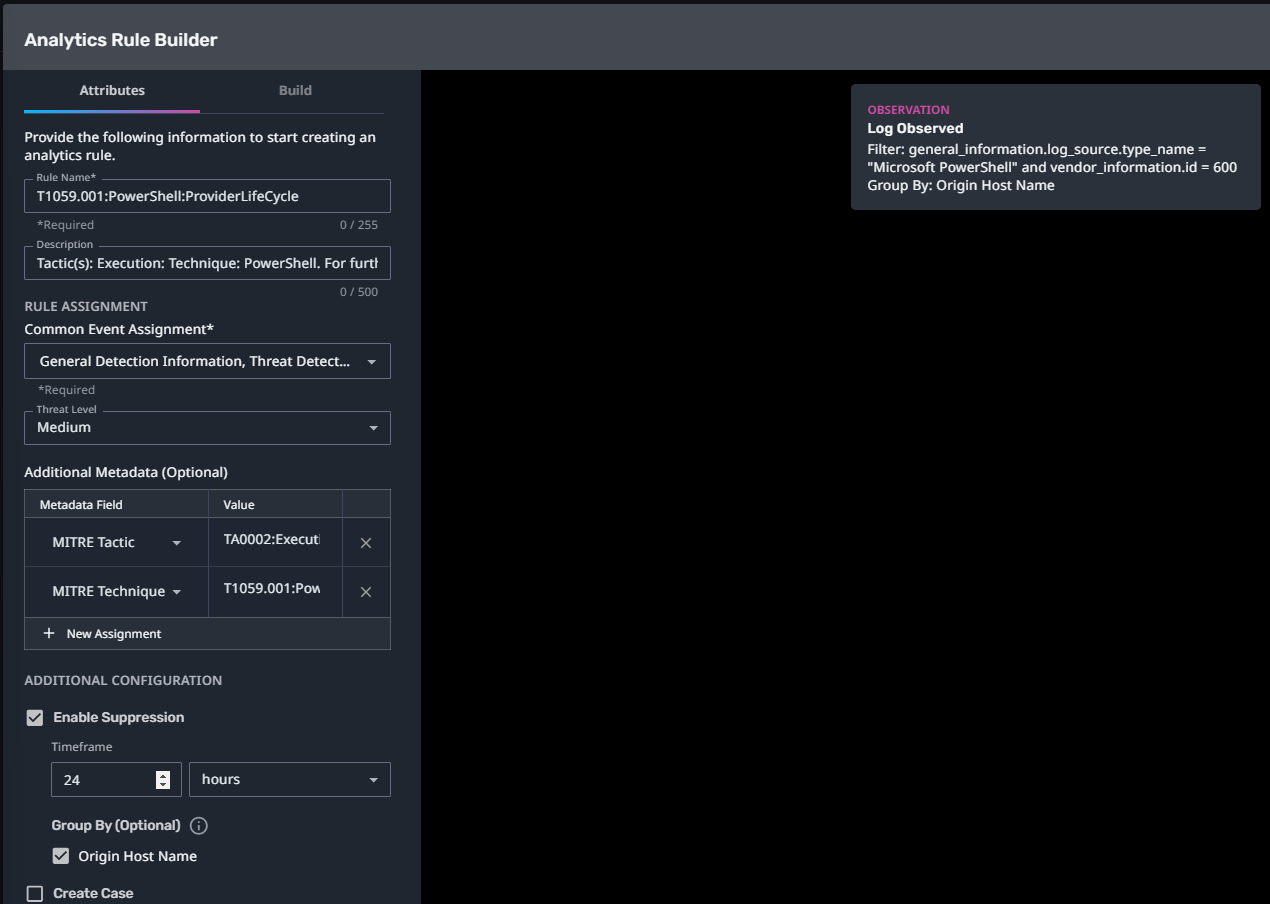
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1136.003:Cloud Account
Streaming Analytic Filter:
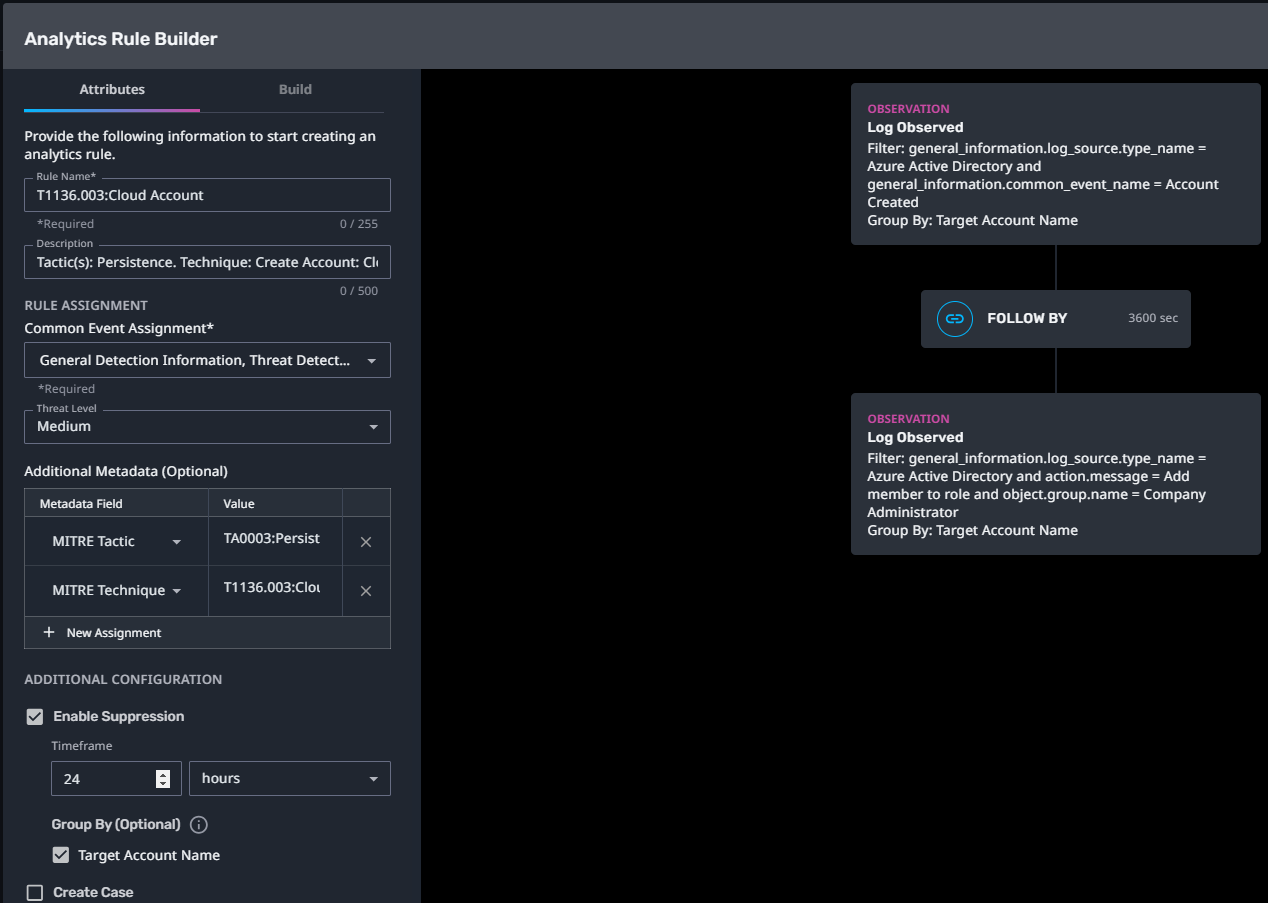
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
Requires the Azure Active Directory log source.
T1199:Trusted Relationship
Streaming Analytic Filter:
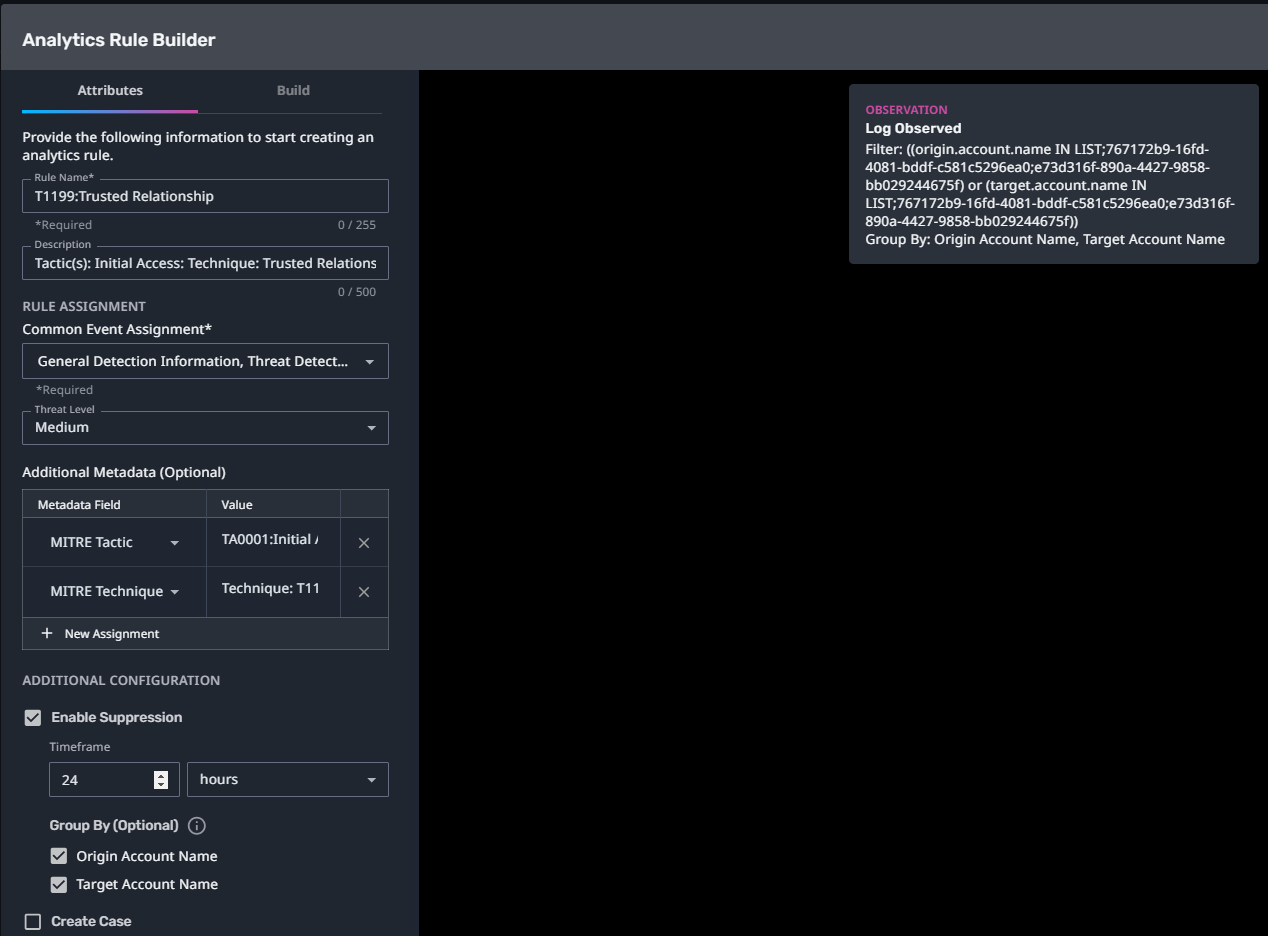
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
This rule requires a List to be populated before enabling. This analytic monitors for activity from third party accounts. Add the names of the accounts you would like to monitor to the list named "MA:Third Party Accounts". Refer to the Origin Account Name field of existing logs to ensure the account name format is correct.
T1078.001:Default Accounts
Streaming Analytic Filter:
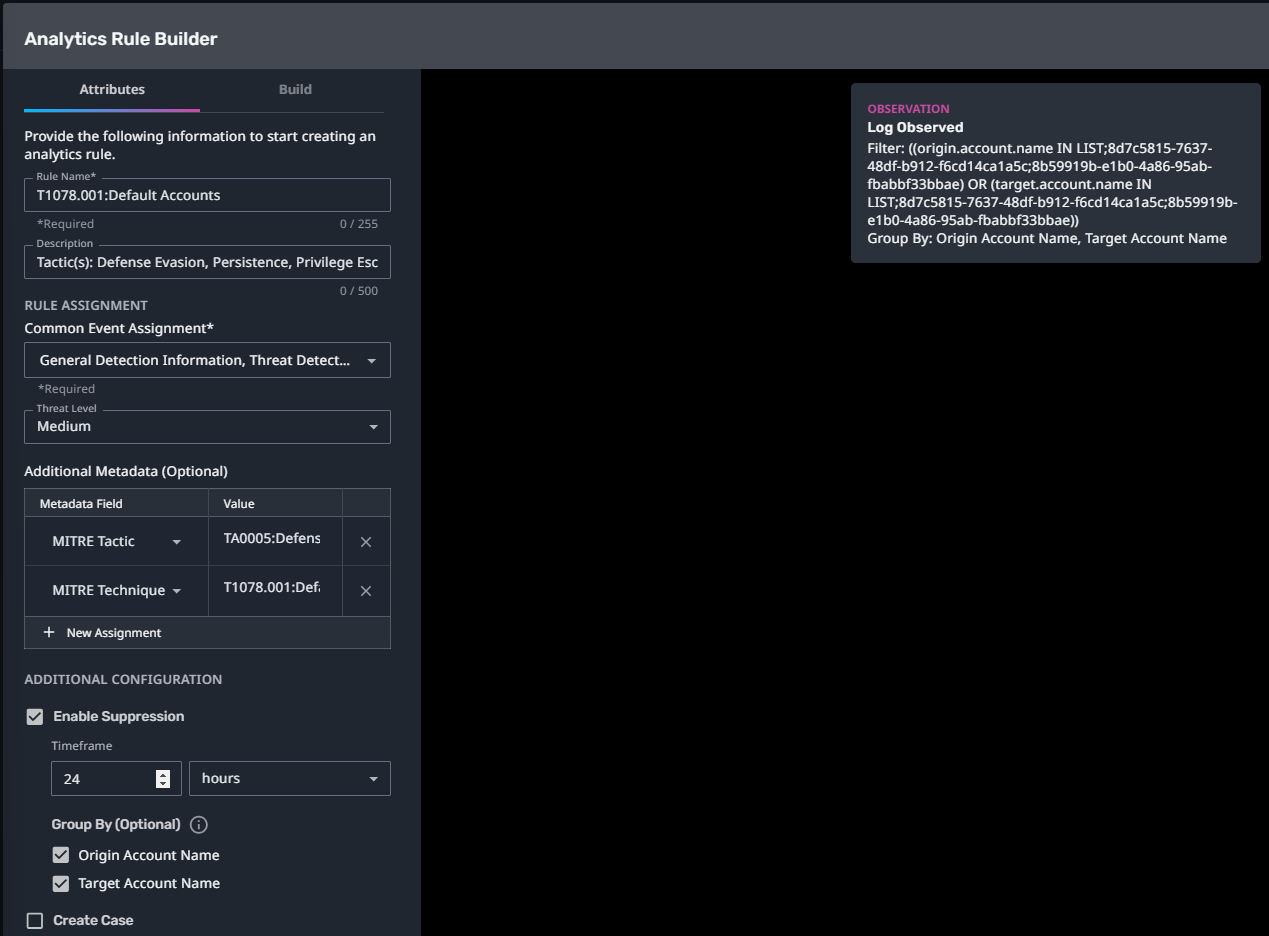
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
This rule requires a List to be populated before enabling. This analytic monitors for activity from default accounts. Add the names of the default accounts you would like to monitor to the list named "MA:Default Accounts". Refer to the Origin Account Name field of existing logs to ensure the account name format is correct.
T1621:MFA Request Generation:Okta Push from Non-Safelisted Location
Streaming Analytic Filter:

Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
This rule requires a List to be populated before enabling. This analytic monitors for activity from Safelisted Regions. Add the names of the safelisted regions you would like to monitor to the list named " Safelisted Regions".
T1078.003:Local Accounts
Streaming Analytic Filter:
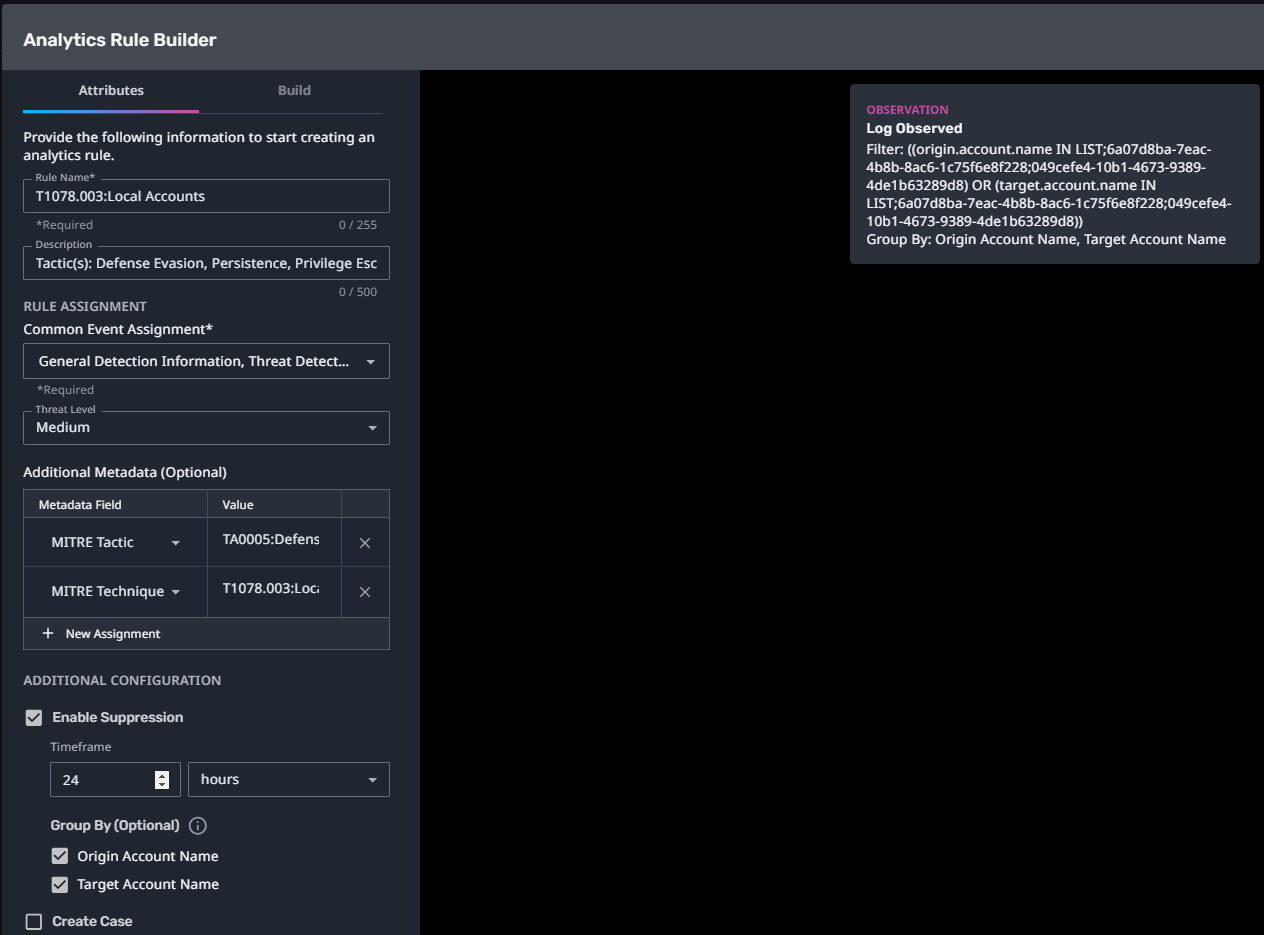
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
This rule requires a List to be populated before enabling. This analytic monitors for activity from local accounts. Populate the “MA:Local Accounts” list with a list of local accounts applicable to your company’s network, applications, services, etc. Refer to the Origin Account Name field of existing logs to ensure the account name format is correct.
T1621:MFA Request Generation:Repeated OKTA Push Denies then Allow
Streaming Analytic Filter:
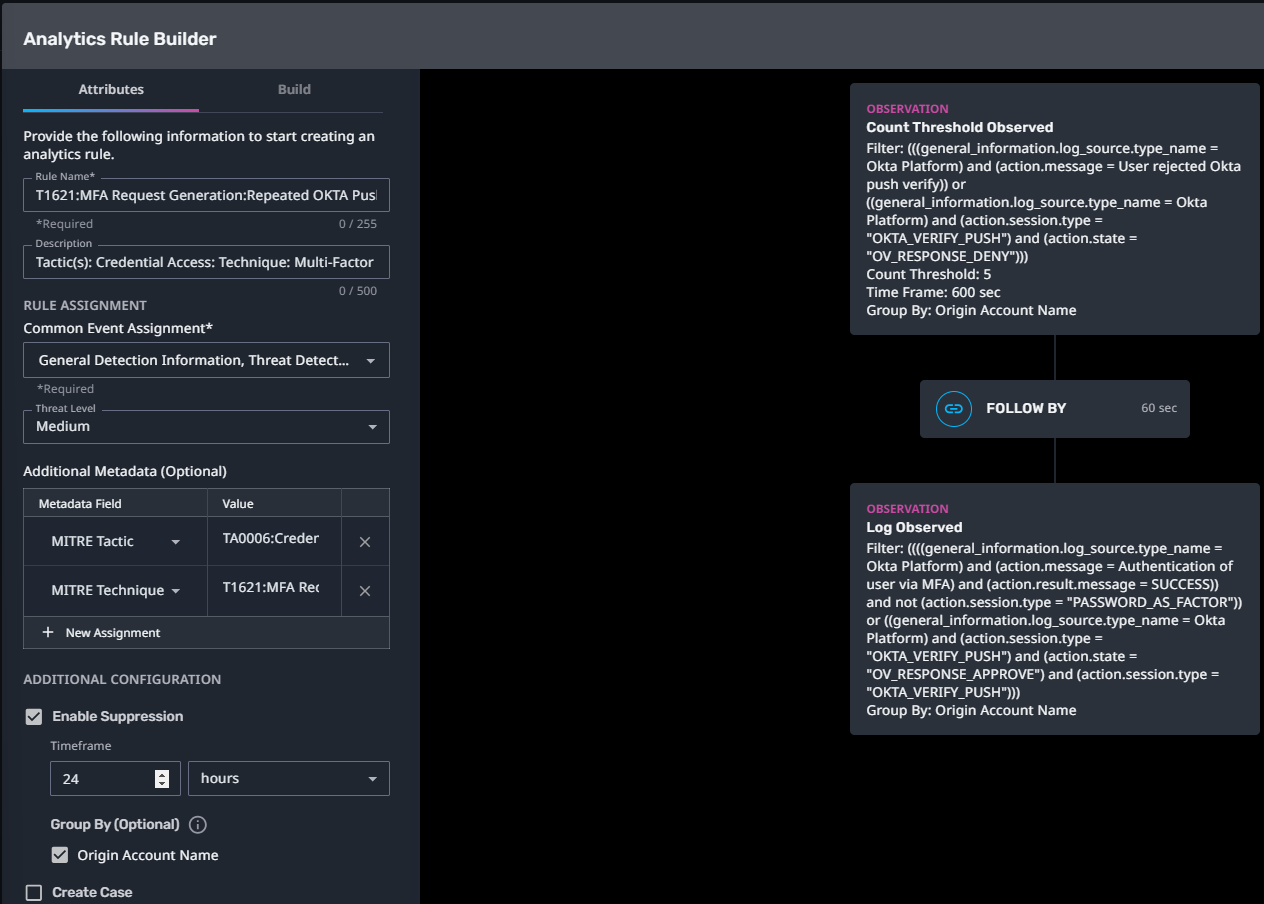
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1562.001:Disable or Modify Tools:Windows Defender
Streaming Analytic Filter:
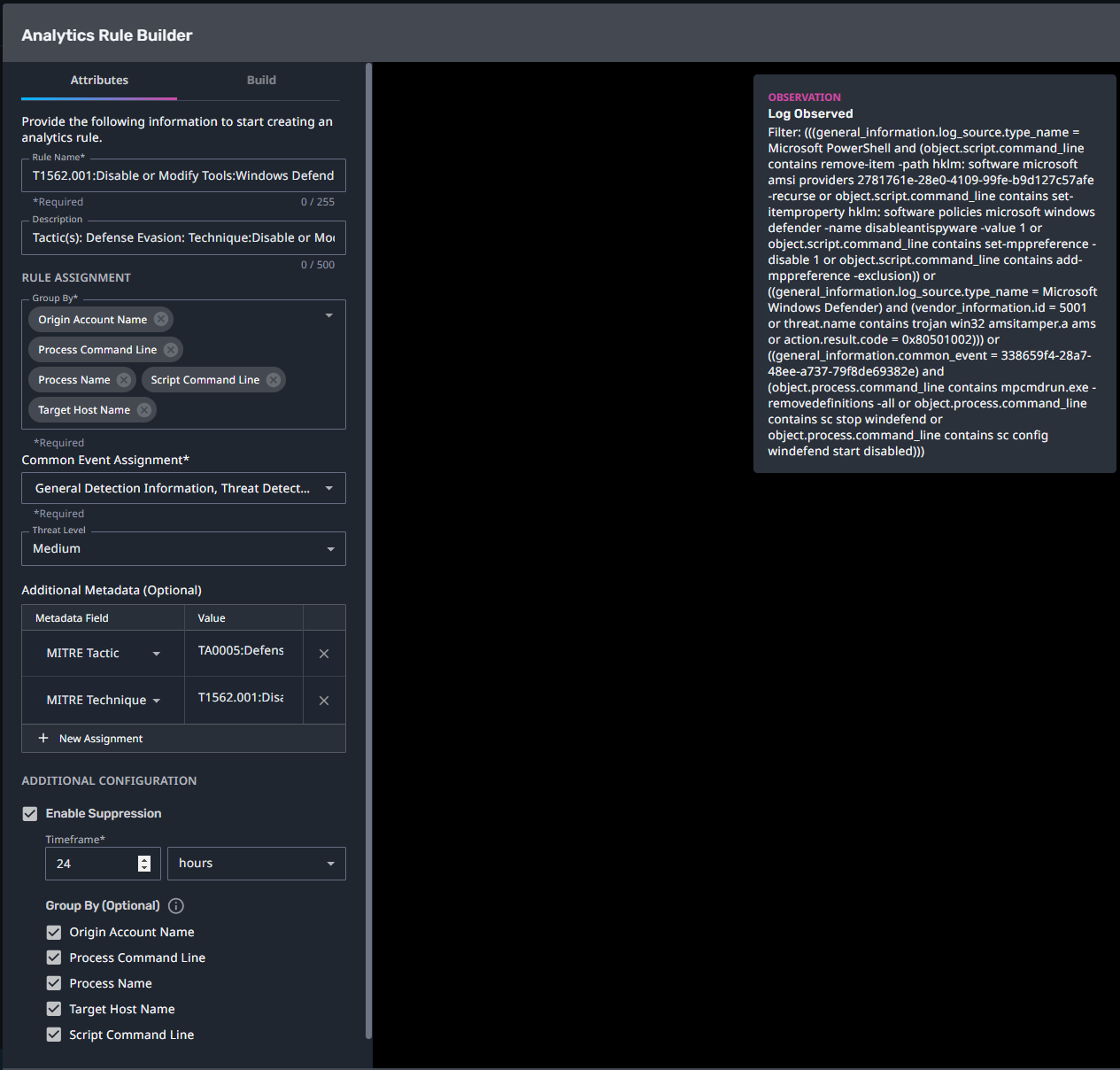
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1098:Account Manipulation
Streaming Analytic Filter:
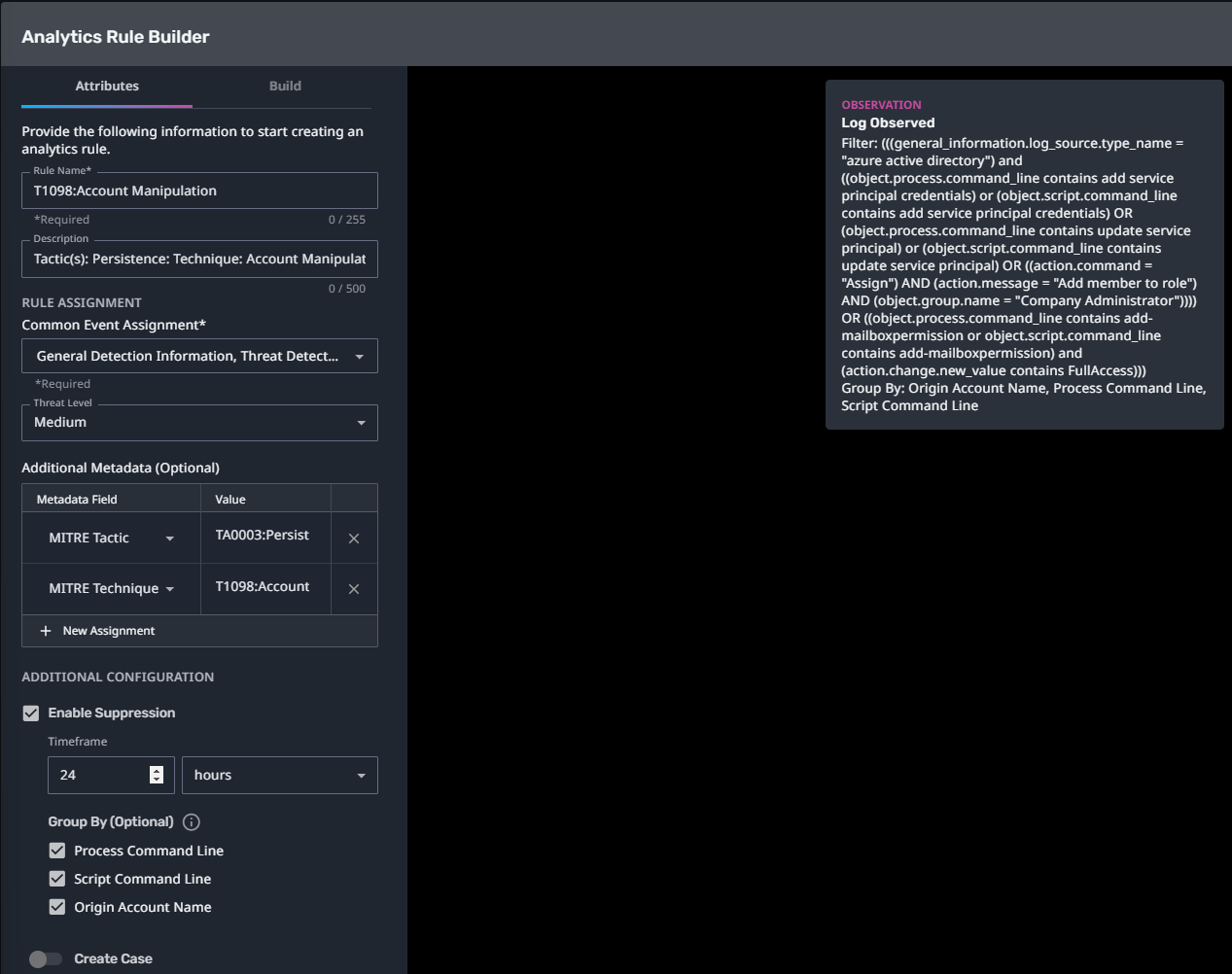
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1552.004:Private Keys
Streaming Analytic Filter:
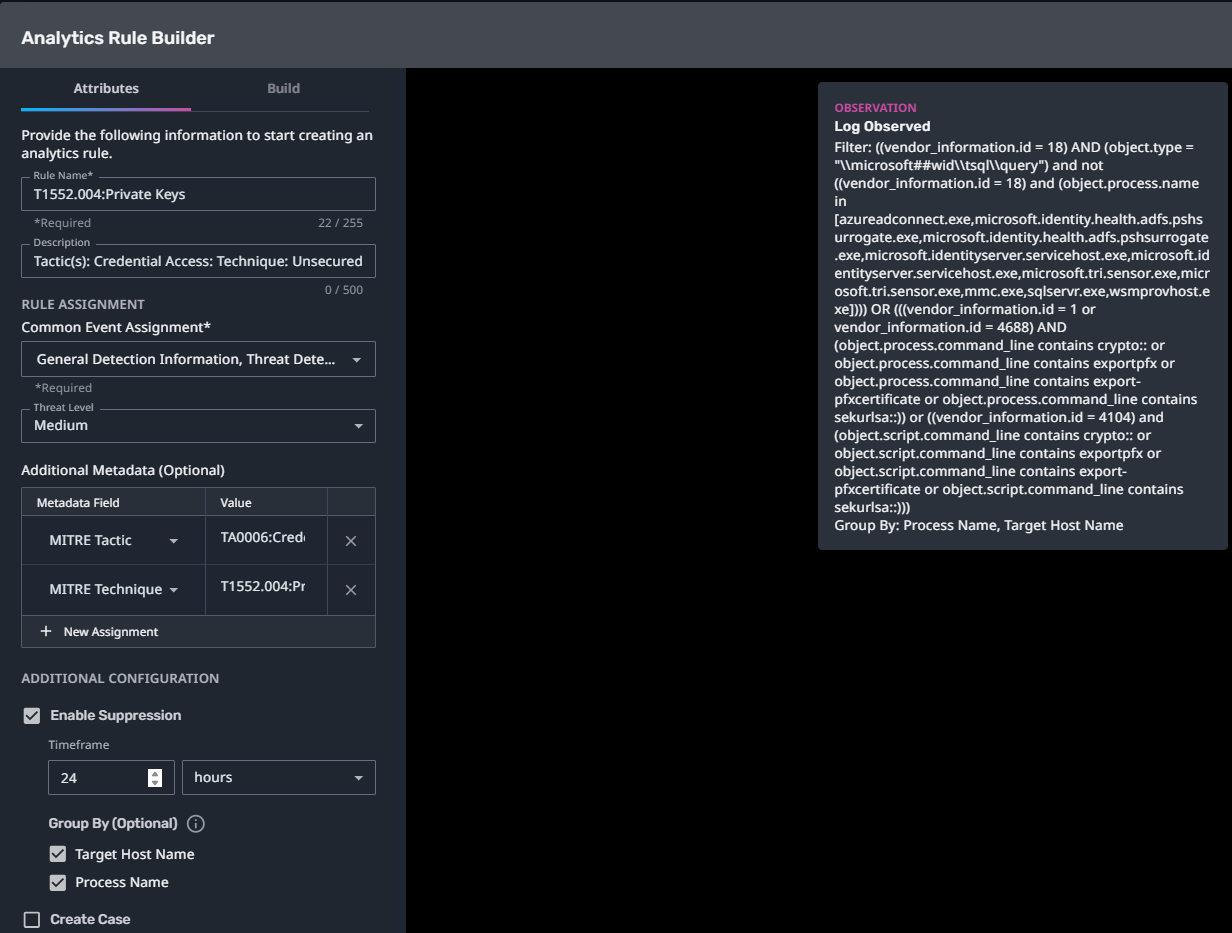
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1621:MFA Request Generation:Repeated OKTA Push Denies
Streaming Analytic Filter:
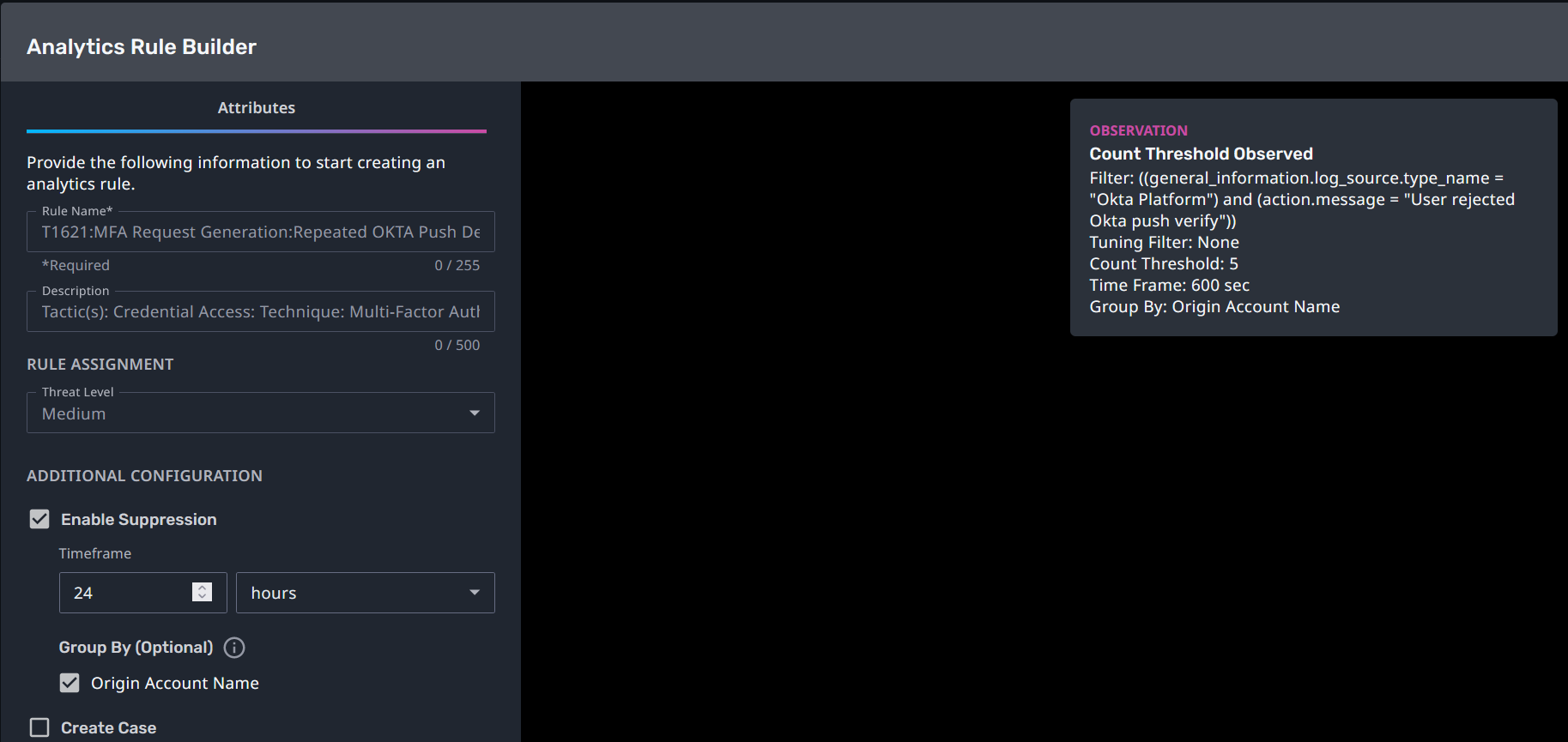
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
Tuning: Investigate your environment to determine the normal push deny rate per-user and adjust the threshold if it exceeds 5 per 10 minutes.
T1059.003:Windows Command Shell
Streaming Analytic Filter:
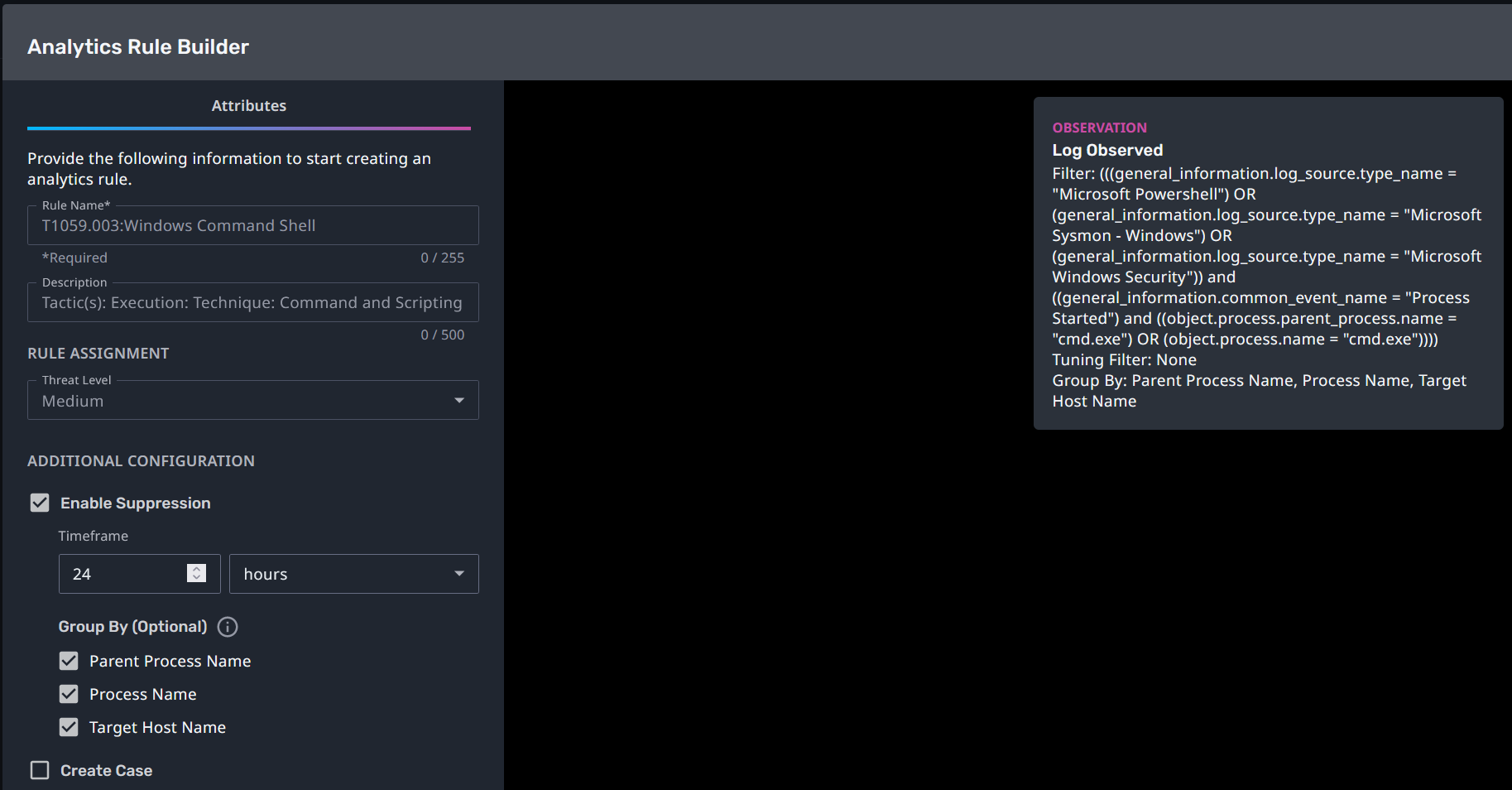
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
T1021.001:Remote Services: Remote Desktop Protocol
Streaming Analytic Filter:
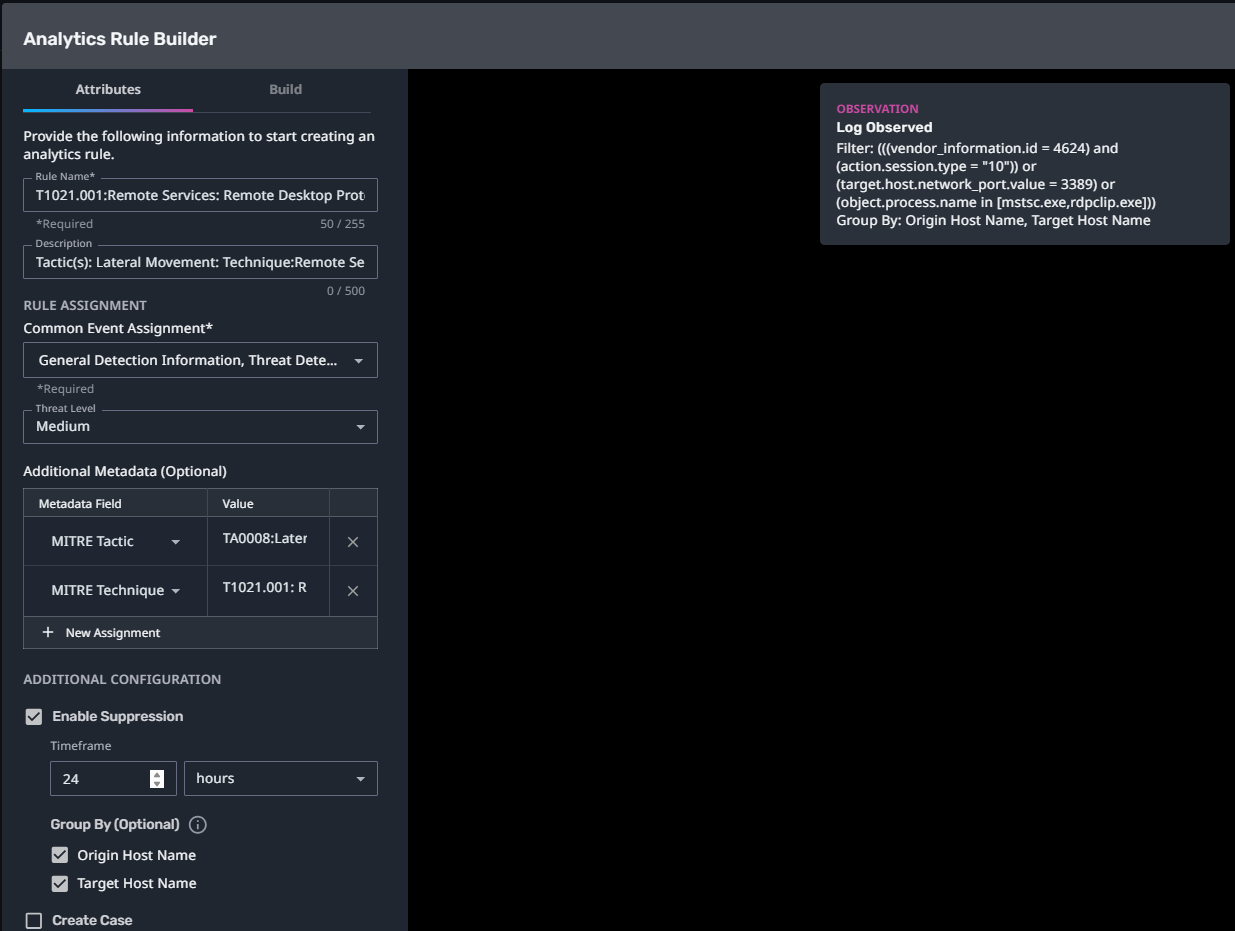
Configuration Note:
Enable “Create Case” to automatically create a case upon detection.
